Notebooks
Table of Contents
- Overview
- Feature Benefits
- Getting Started with Notebooks
- Creating and Managing Notebooks
- Notebook Templates
- Command Menu and Formatting
- Sharing Notebooks
- Notebook Management
- Notebook Practices
Overview
Notebooks is a powerful incident response feature that allows SOC analysts to centralize their investigation queries, automation actions, and reporting in a single document. With support for markdown syntax and rich media, Notebooks streamlines the incident response process and facilitates team collaboration.
Feature Benefits
- Centralized incident response
- Embedded queries and automations
- Customizable templates for different threat types
- Rich text formatting with markdown support
- Standardized response processes
- PDF export
- Multi-tenant sharing capabilities
Getting Started with Notebooks
Types of Notebooks
Standalone Notebooks
- Independent notebooks for general use (threat hunting, custom reporting)
- Accessible from the
Notebooks menu
Context-linked Notebooks
- Attached to specific
casesoralertsfor incident response - Directly accessible from the
Notebooks tabwithin cases or alerts - Provides centralized investigation context
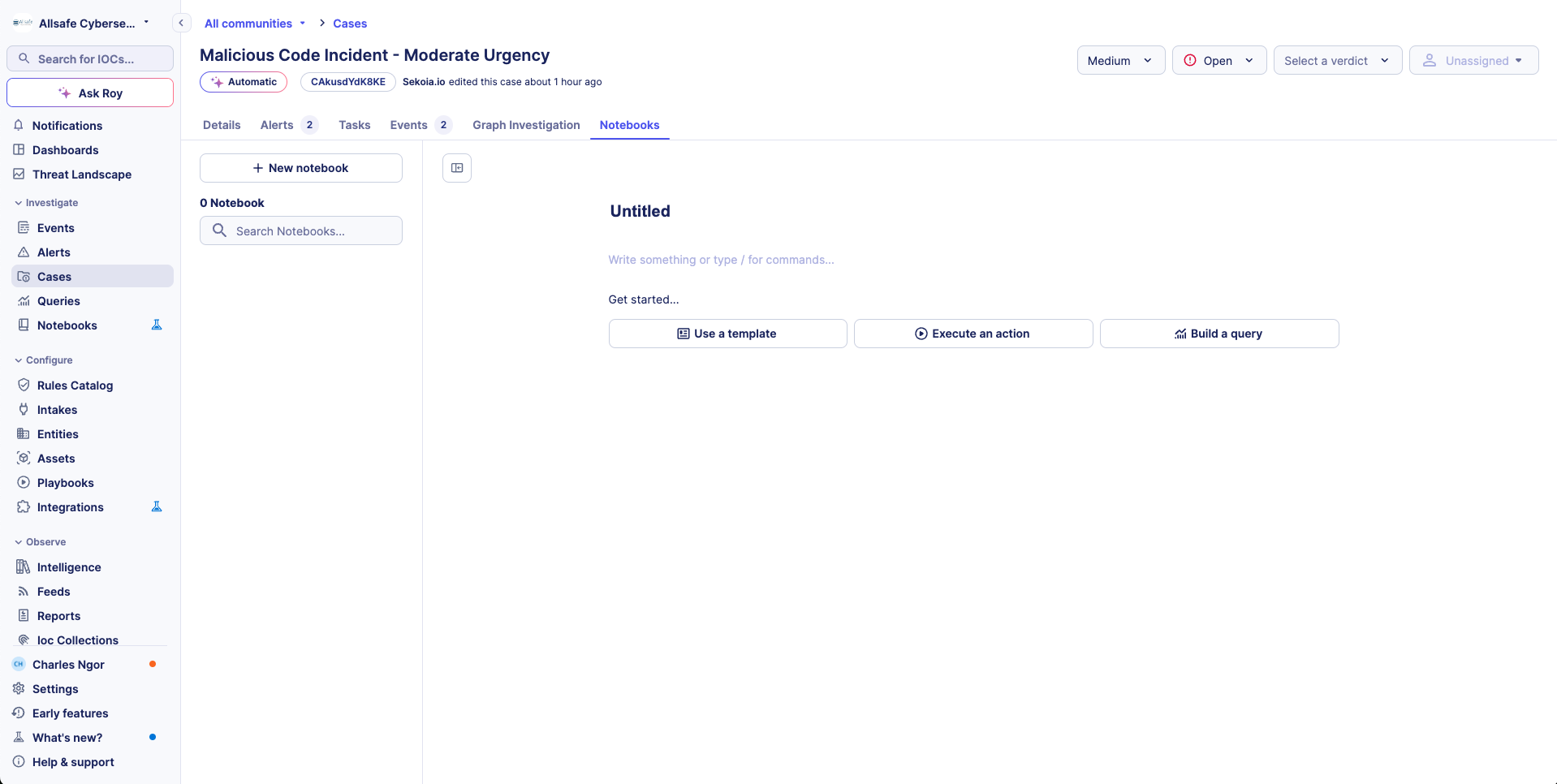
Creating and Managing Notebooks
Creating a New Notebook
- Navigate to the
Notebooks tabwithin a case or an alert - Click
New Notebook - Edit blank notebook or use an existing template
Warning
In a multi-tenant environment, notebooks are created in the parent workspace by default. They are not visible to child tenants unless you explicitly share the notebook with them.
Basic Features
- Markdown syntax support
- Image attachment for evidence collection
- Multi datasources querying
- Investigation findings documentation
- Automations execution
- Real-time modifications saving
Info
Currently, Markdown table syntax is not supported.
Tracking Changes
- Last modification date
- Last modification author
Notebook Templates
Template Management
Enhance incident response capabilities by creating template notebooks tailored to different threat types:
- Phishing investigations
- Malware analysis
- Intrusion containment
- Any custom threat responses
Template Features
- Pre-defined investigation steps
- Threat tailored query templates
- Suggested remediation actions
- Guidance for analysts
Setting Default Notebook Template For Cases/Alerts
- Navigate to Notebook templates
- Select desired template
- Set as
defaultfor cases and alerts
The default notebook template will be suggested for use in cases and alerts, enabling the SOC team to standardize their response processes.

Template Creation Methods
- Create notebook template from scratch
- Convert existing notebook to template
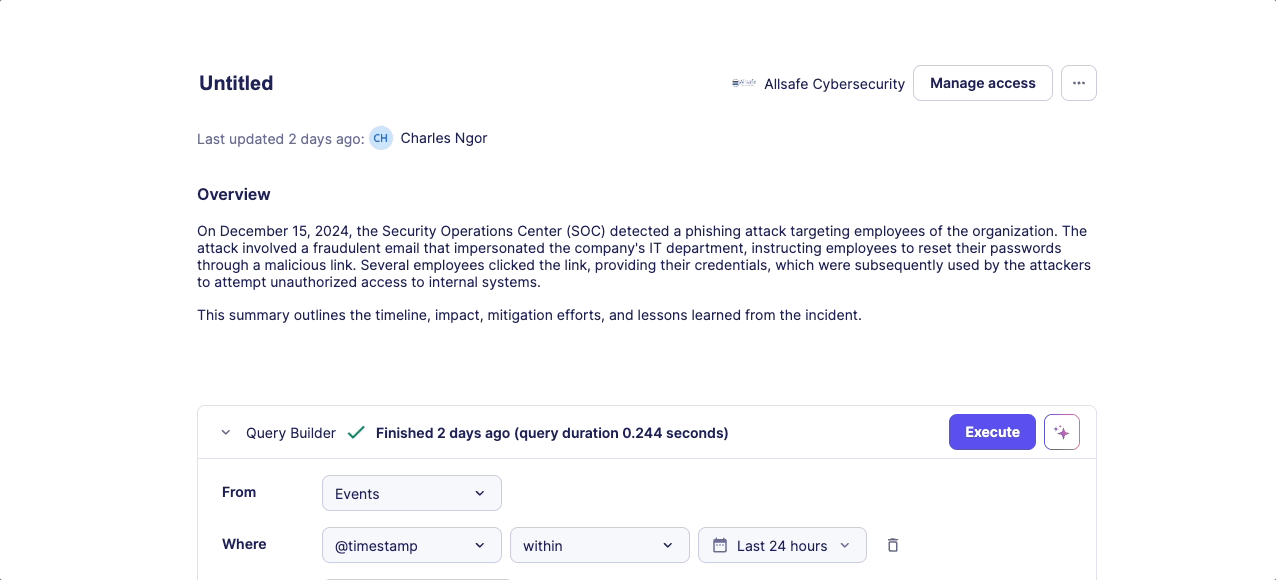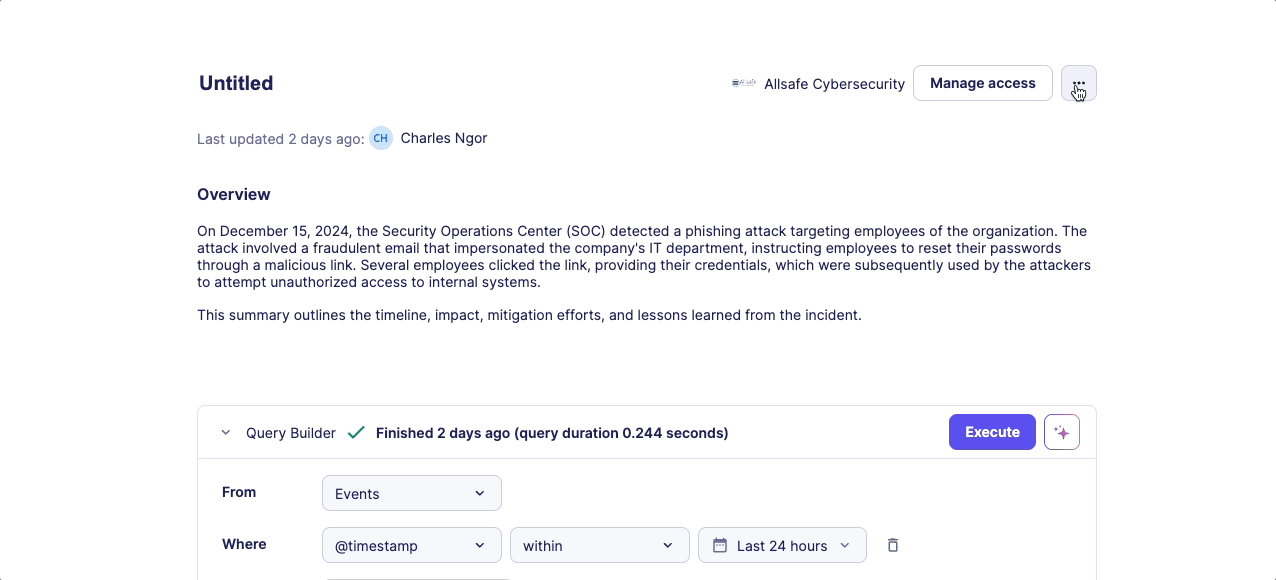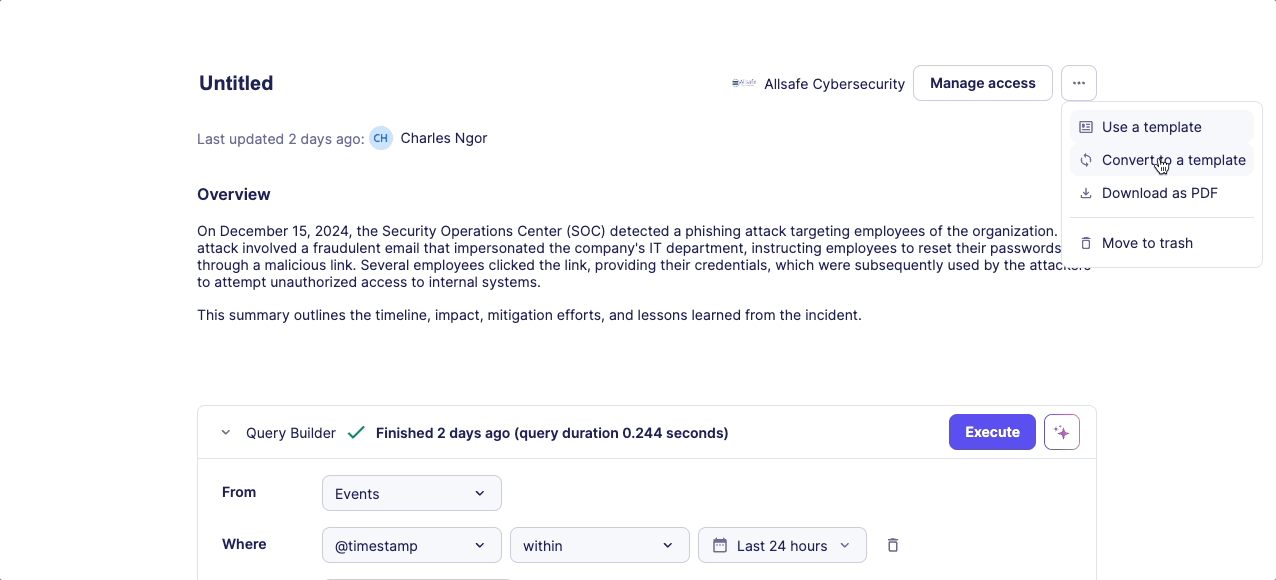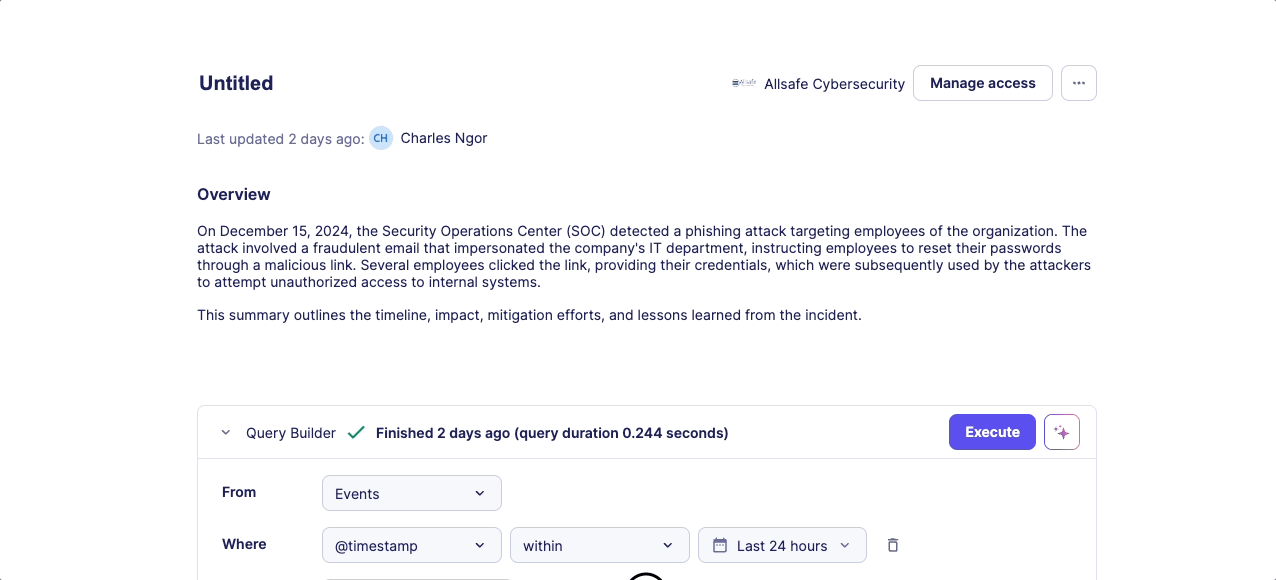
Command Menu and Formatting
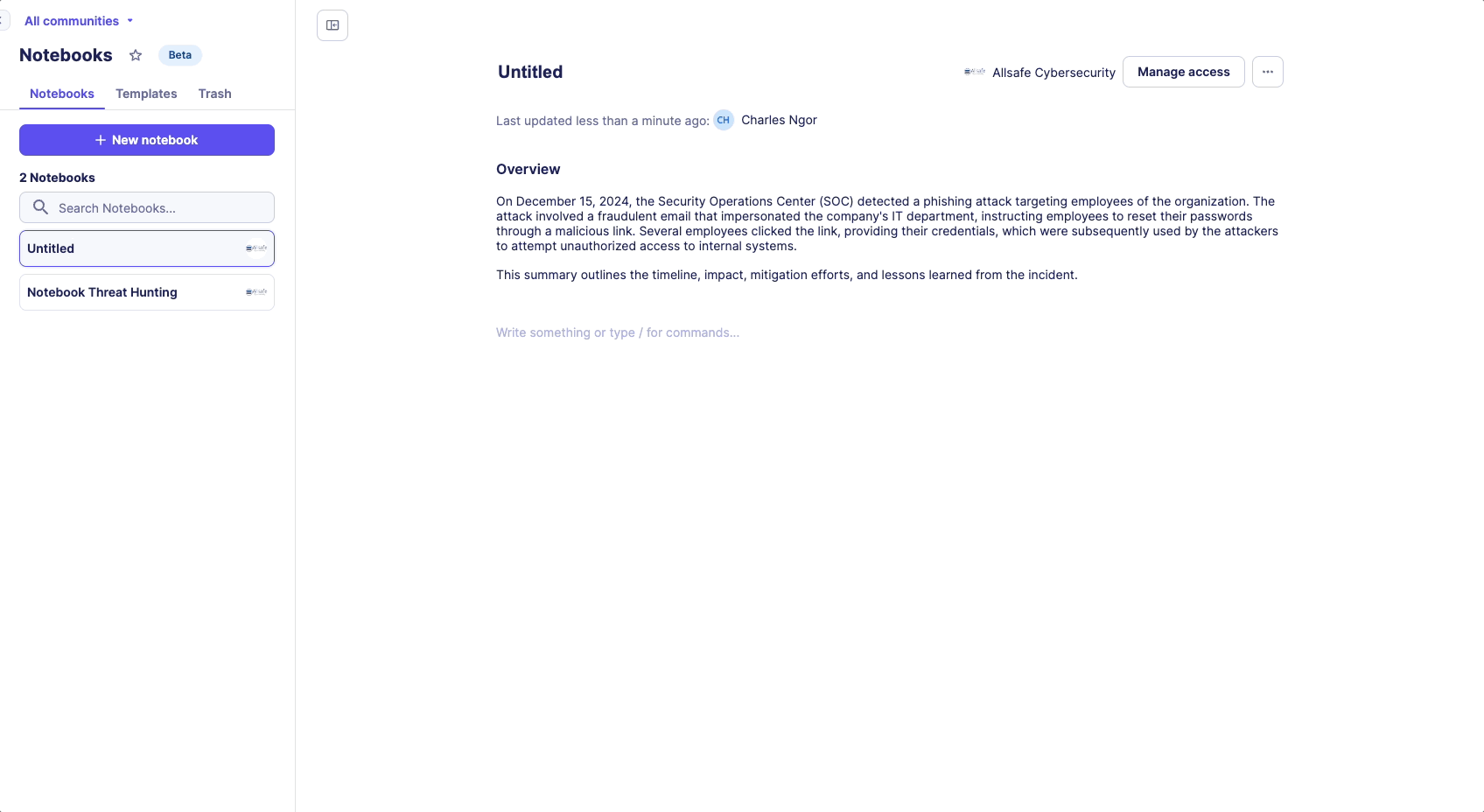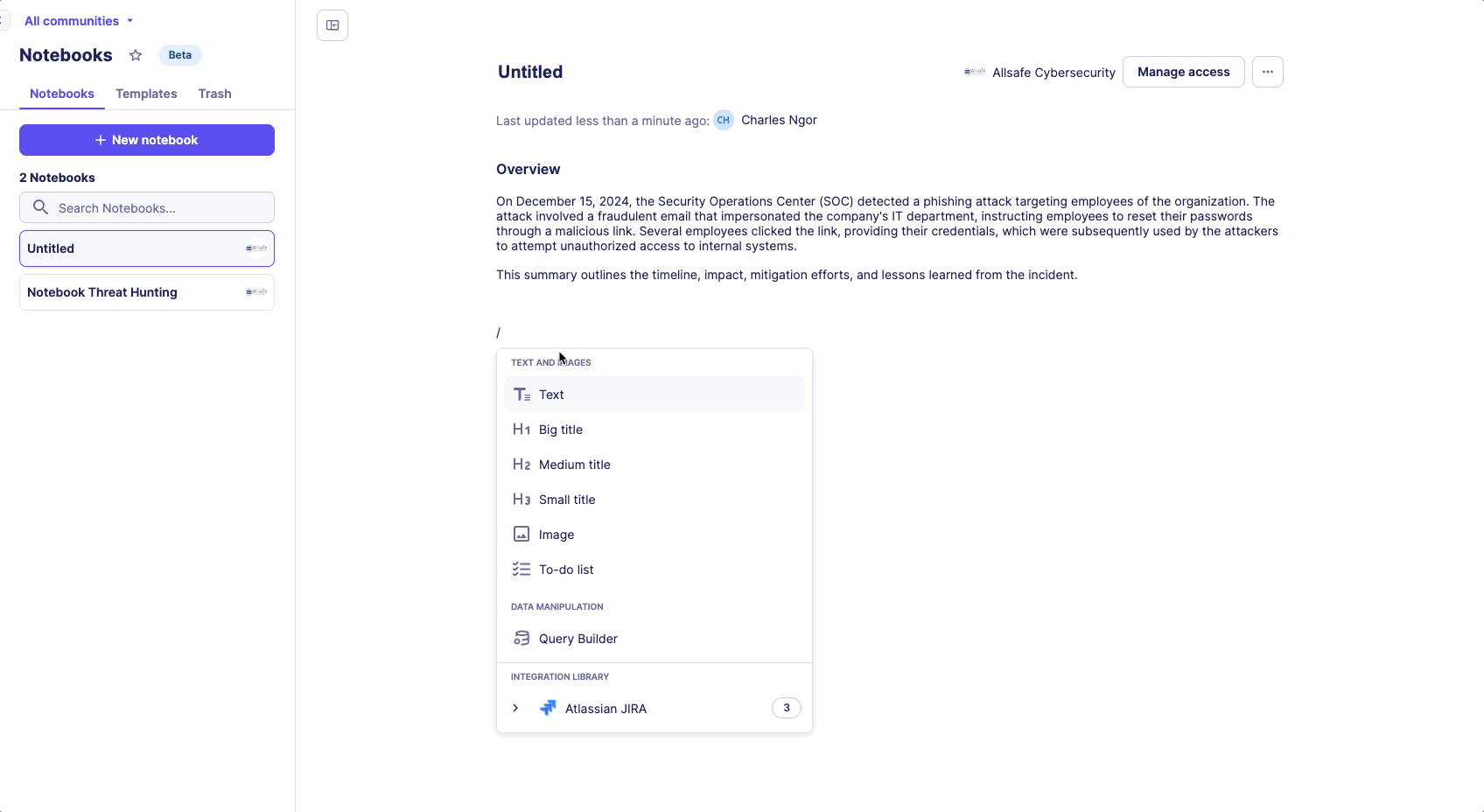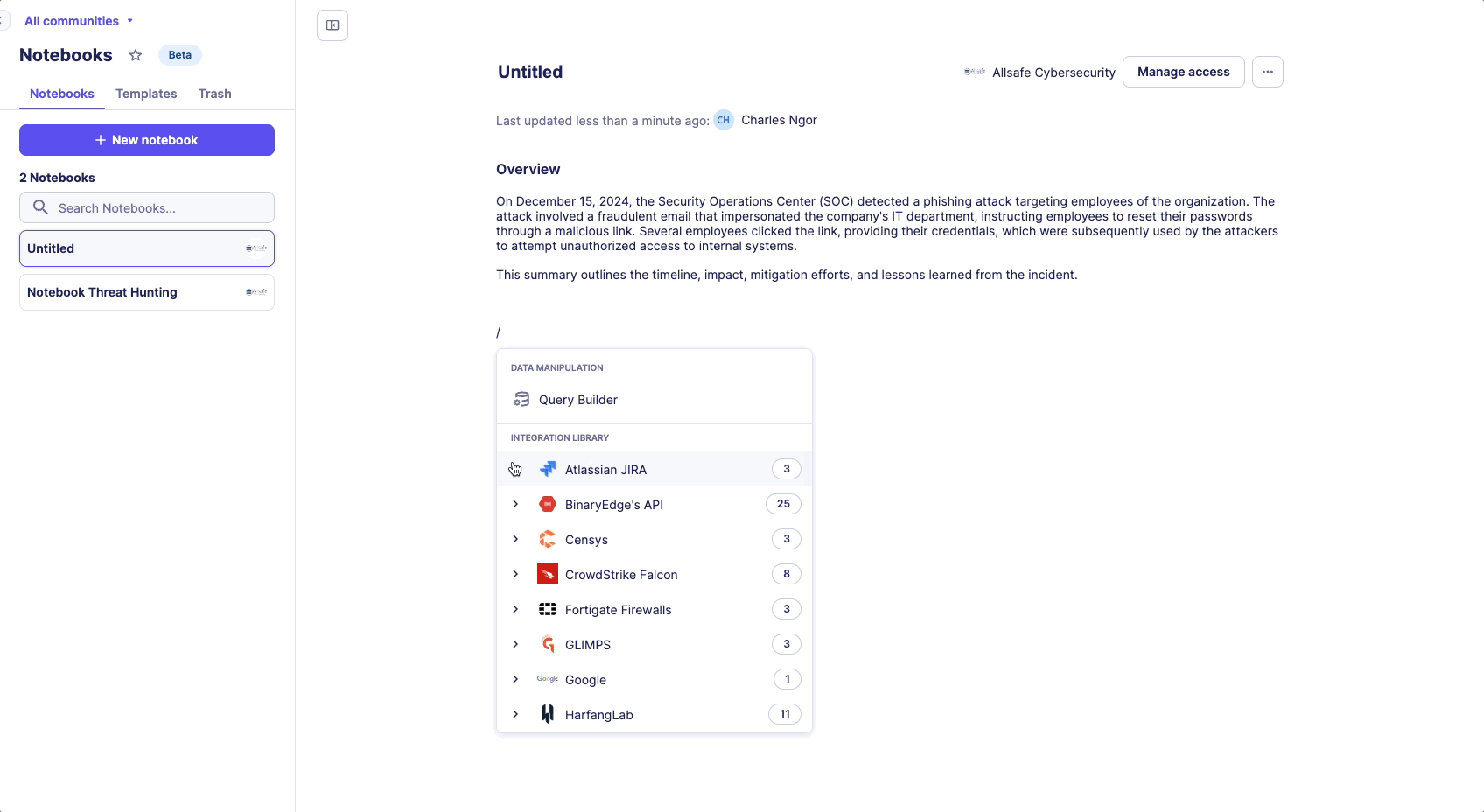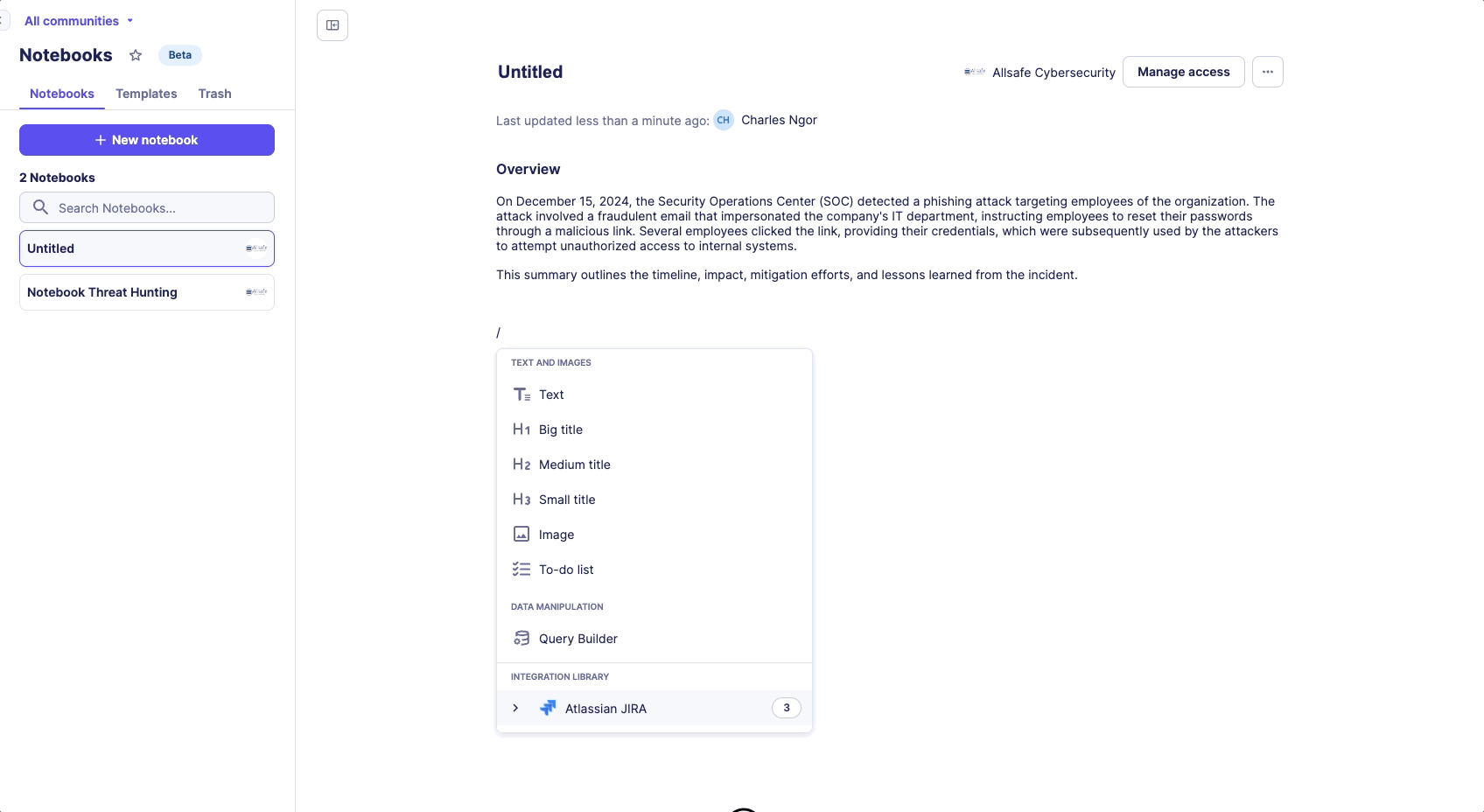
Accessing the Command Menu
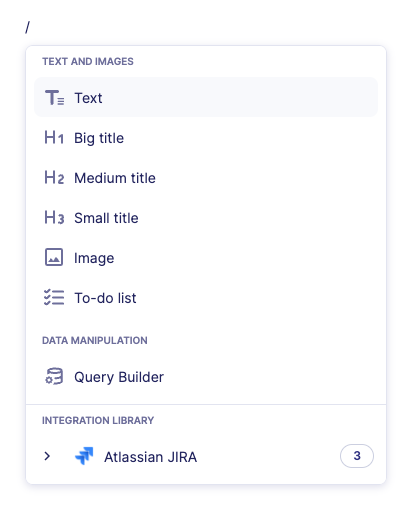
- Press the slash key (/) to open the Command menu
- Access notebook capabilities
Tip
When the command menu is open, quickly search for an integration by typing its name.
Available Commands
- Text formatting options
- Query builder insertion
- Automation insertion
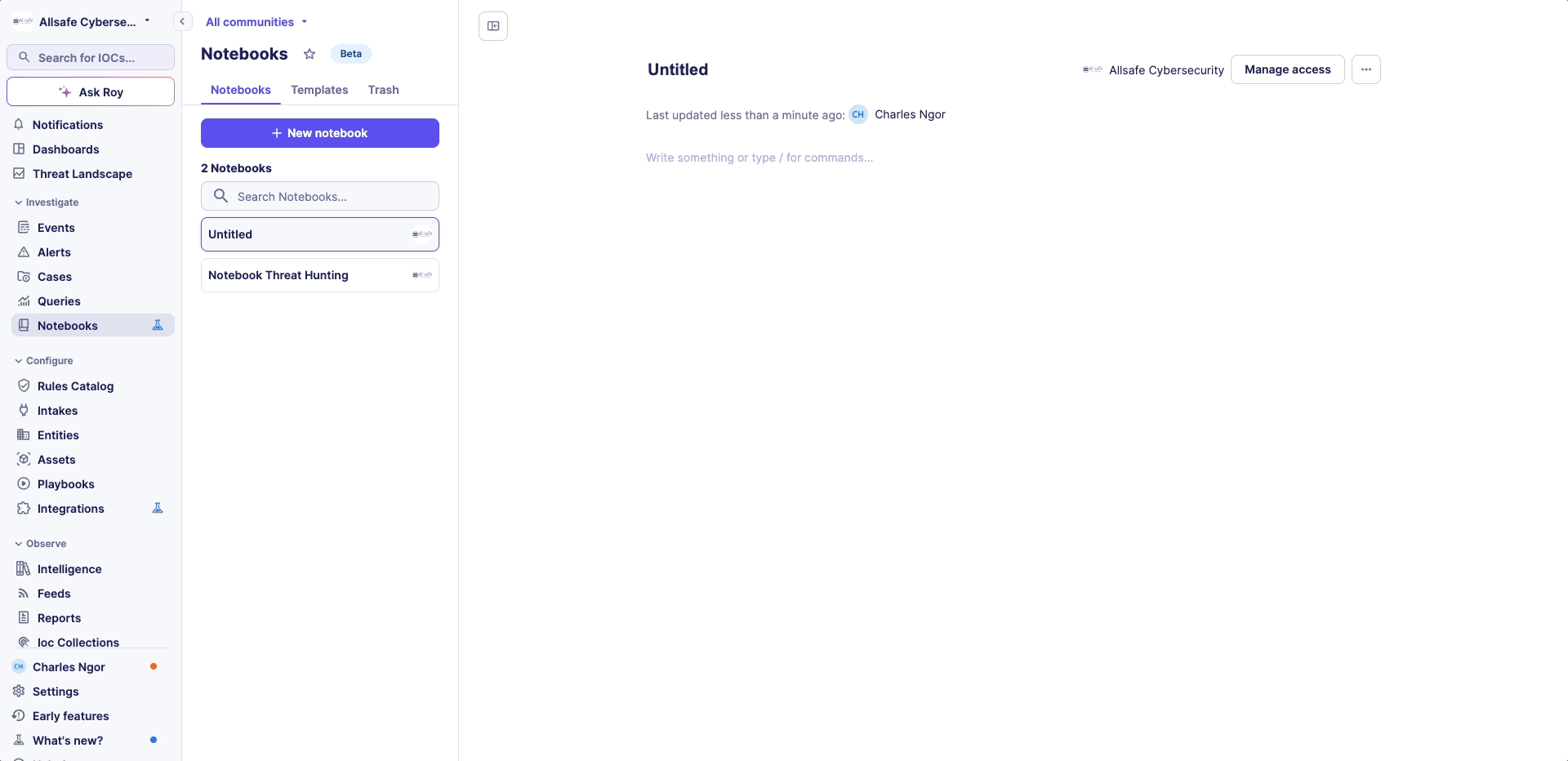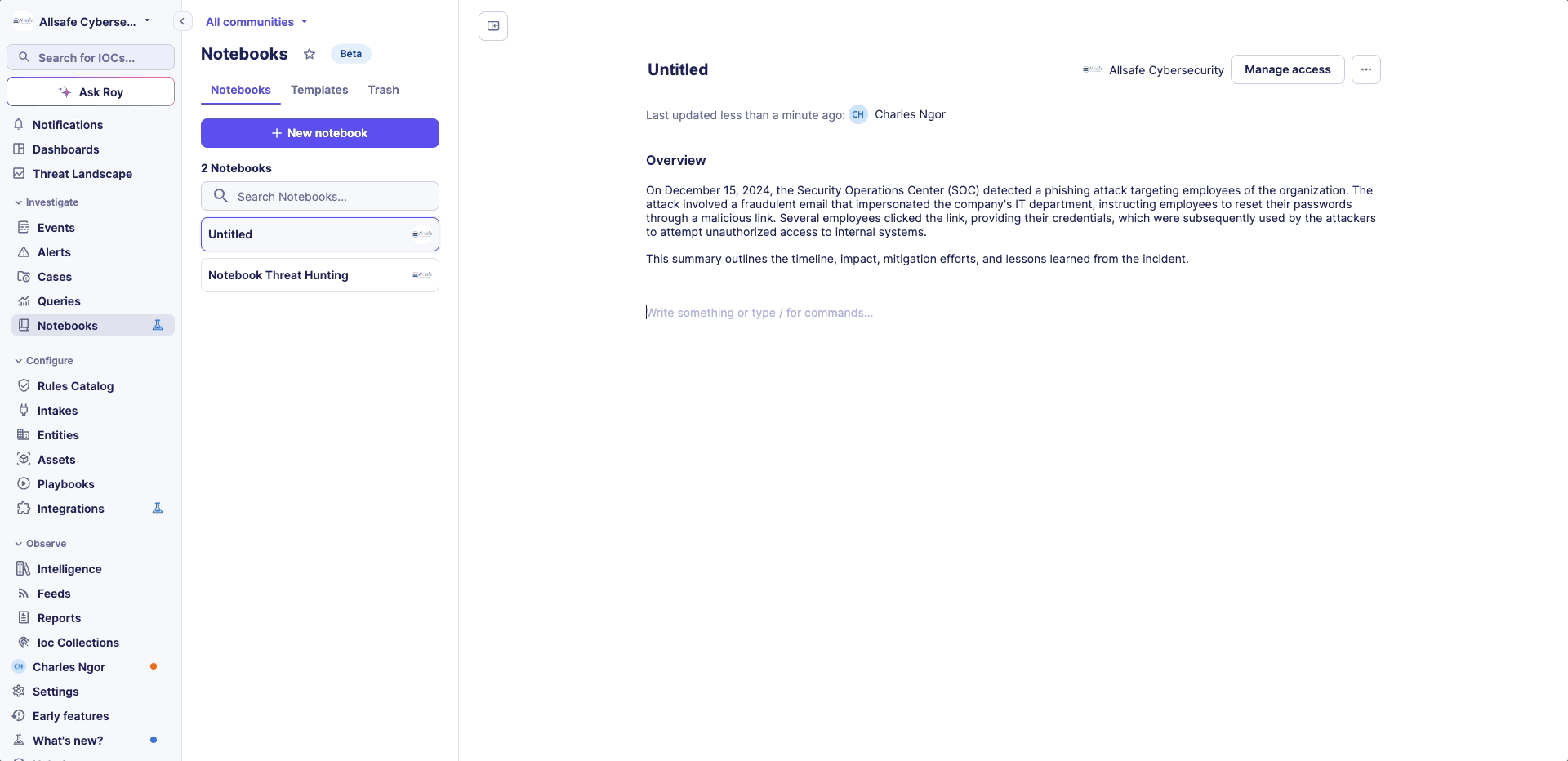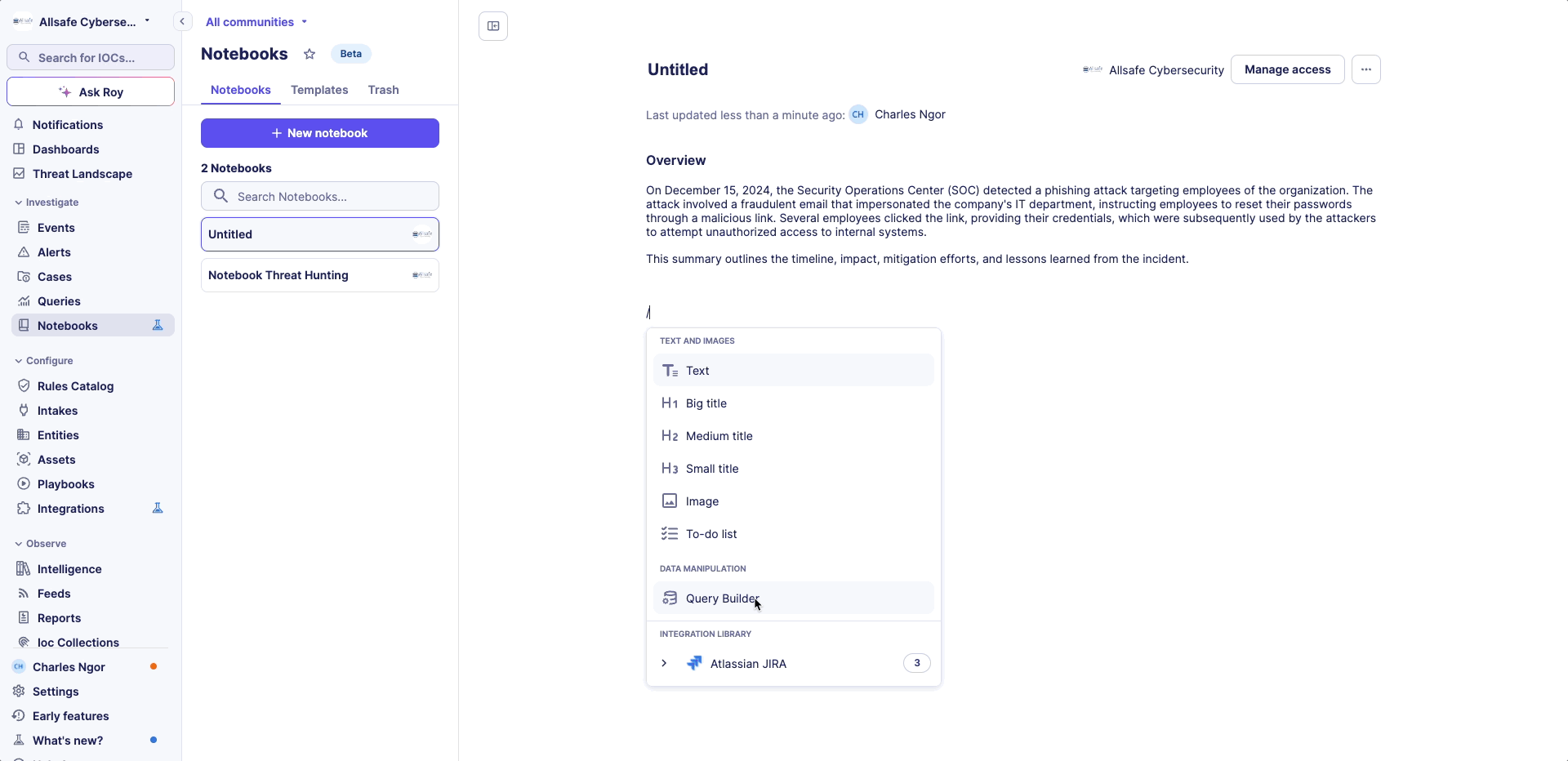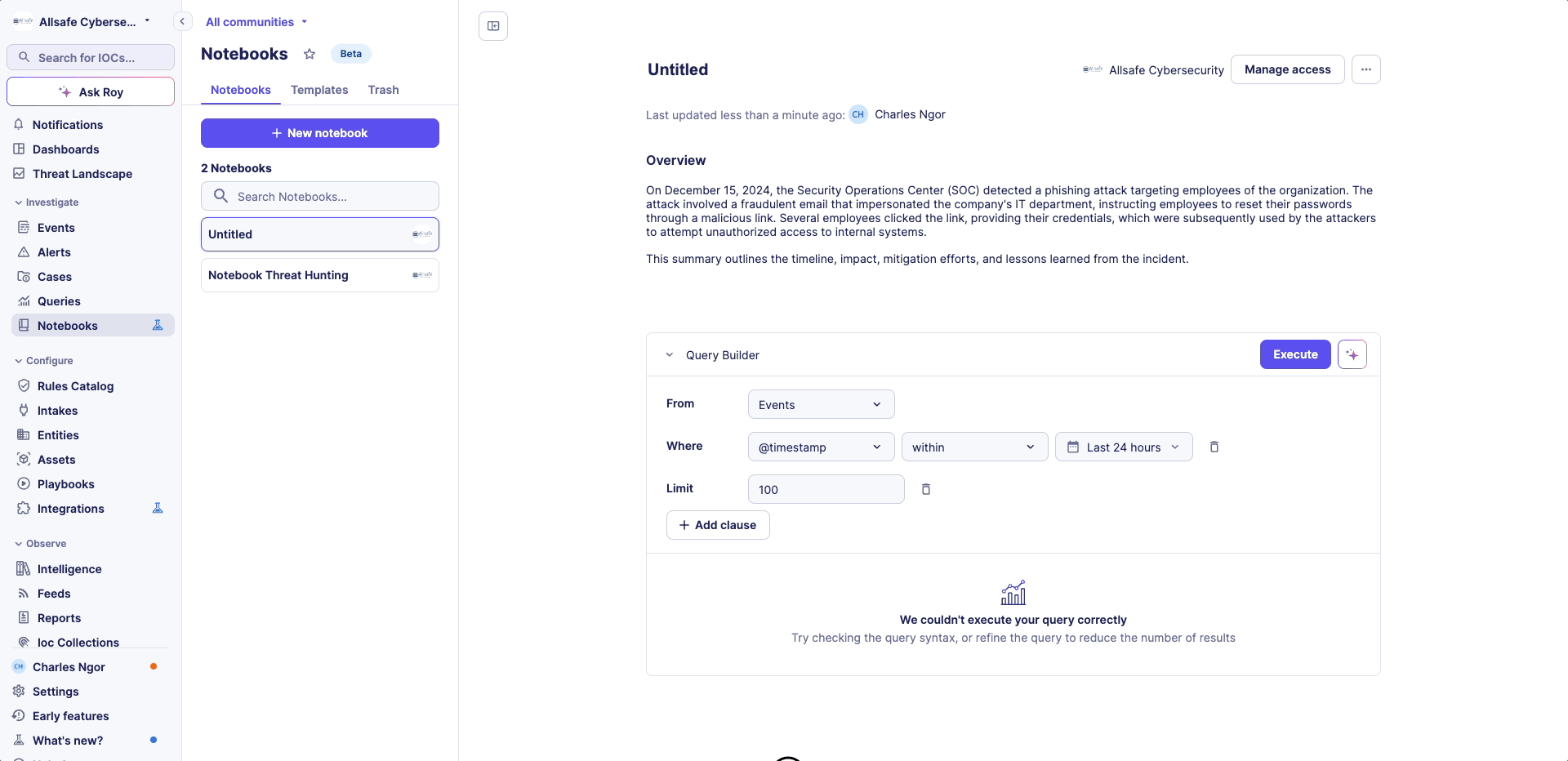
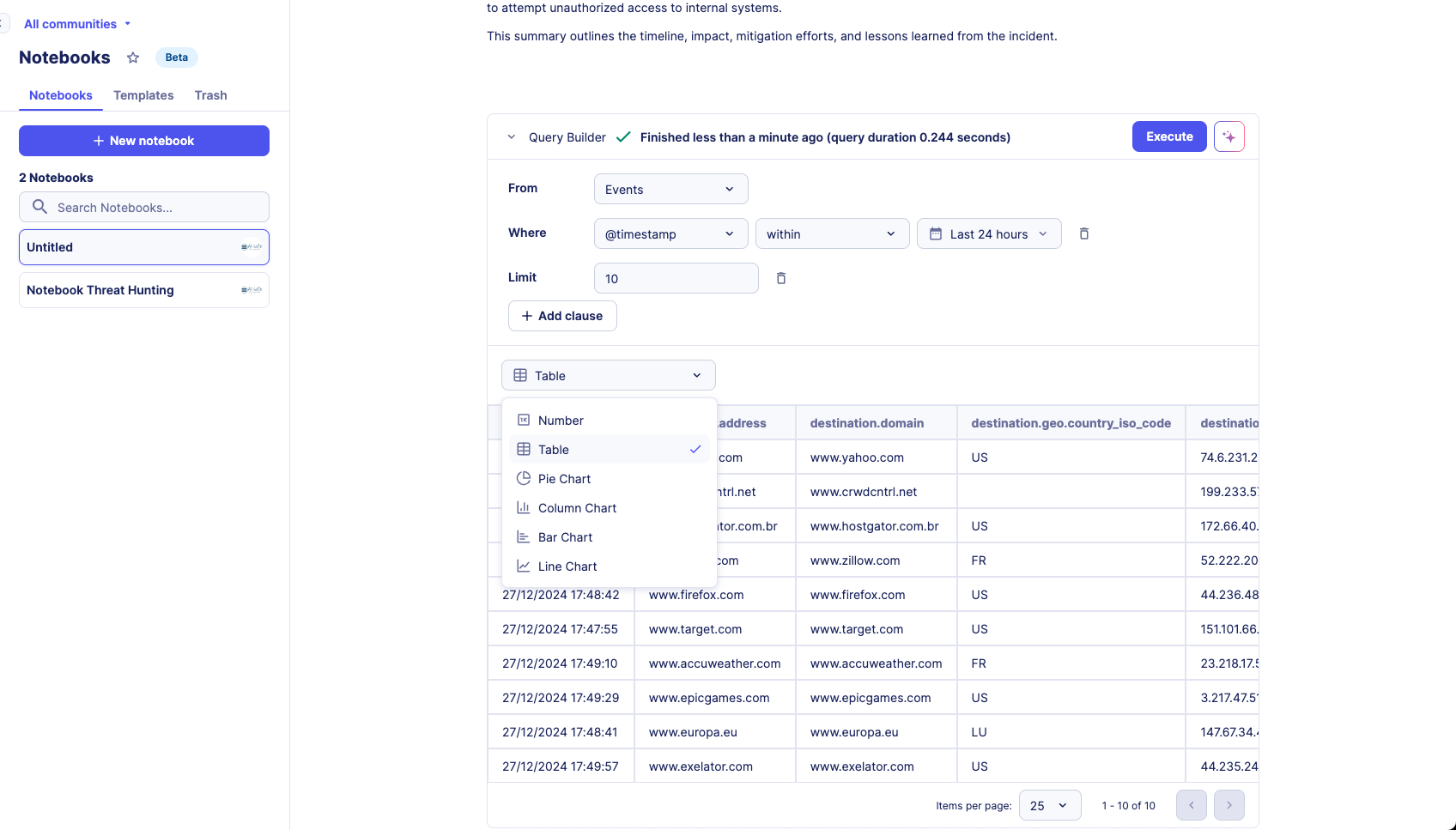
Query Builder Editor
- Display data in tables
- Create various data visualizations, including pie charts, line charts, bar charts, column charts, and numeric displays
Sharing Notebooks
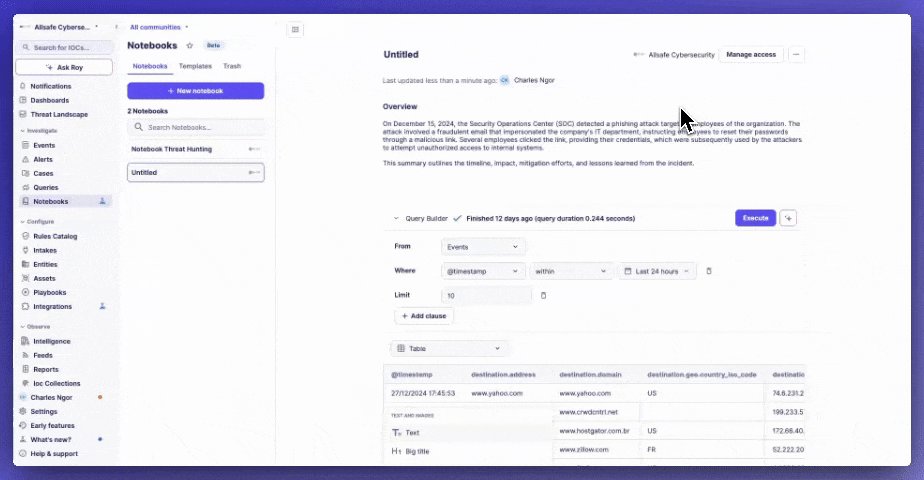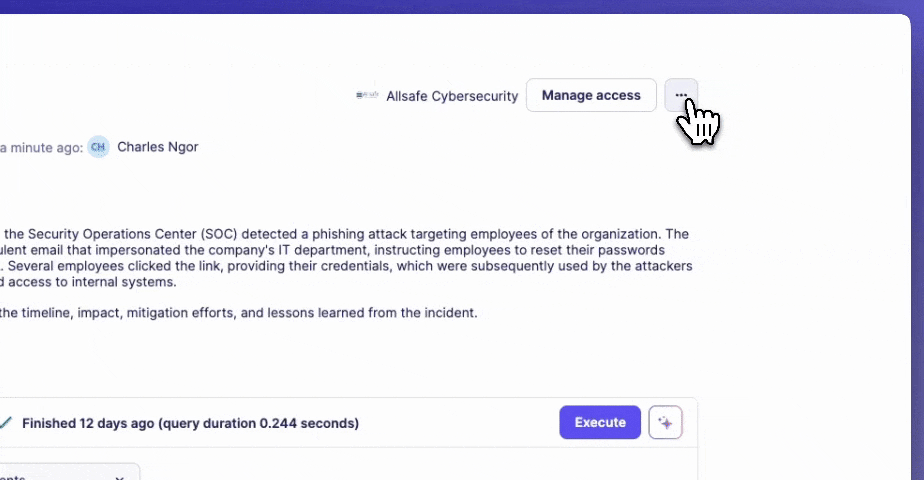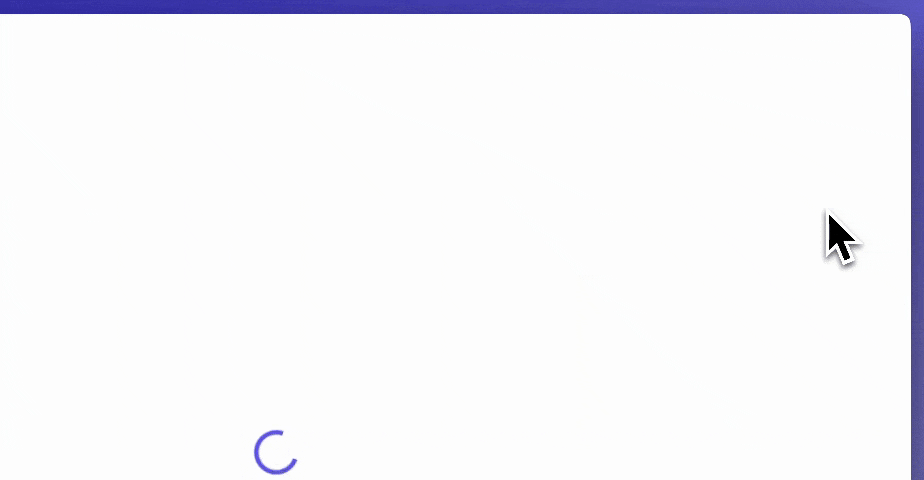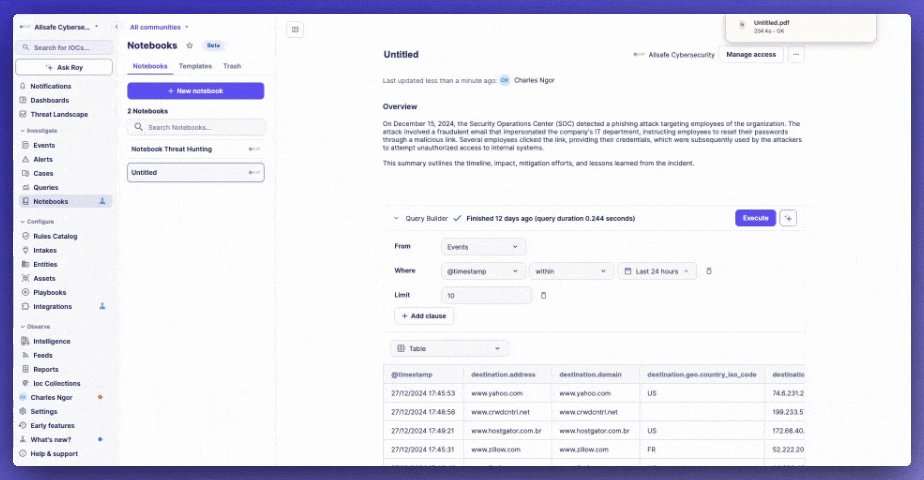
Export notebook as PDF
Convert notebooks into PDF files to efficiently share incident, threat hunting, and KPI reports.
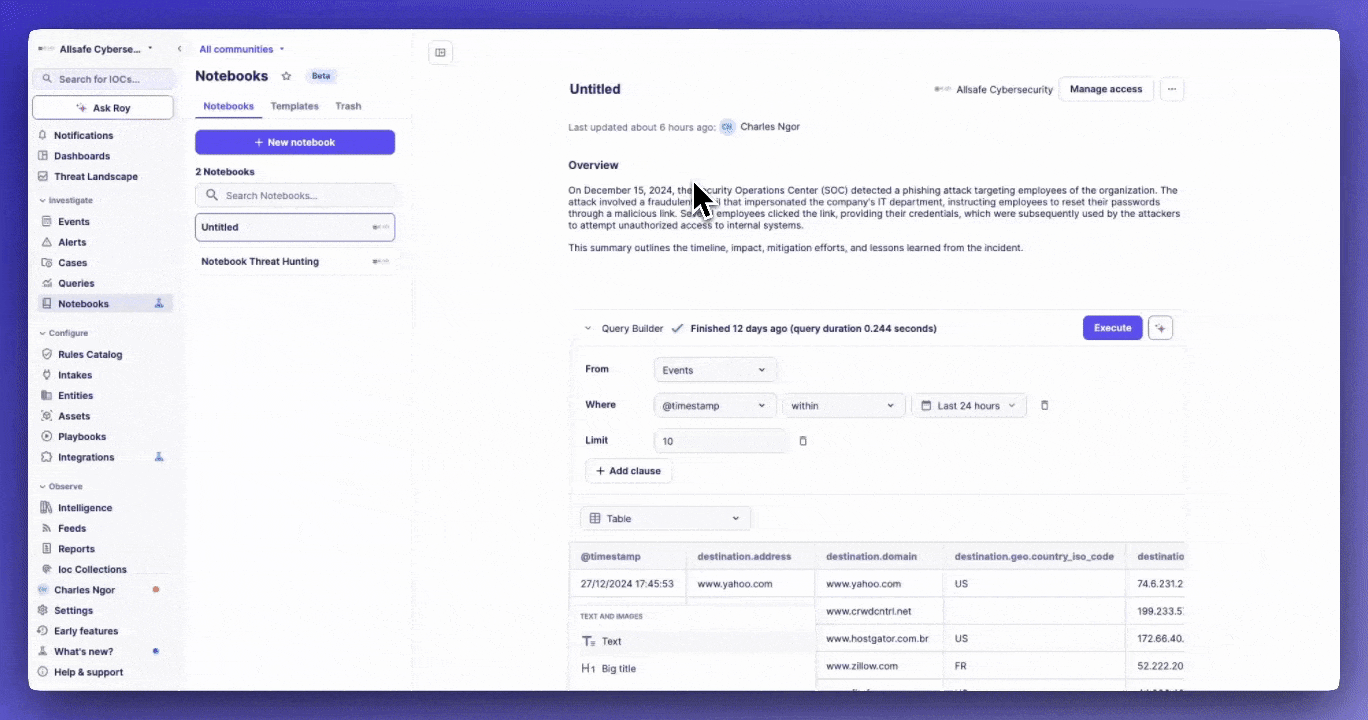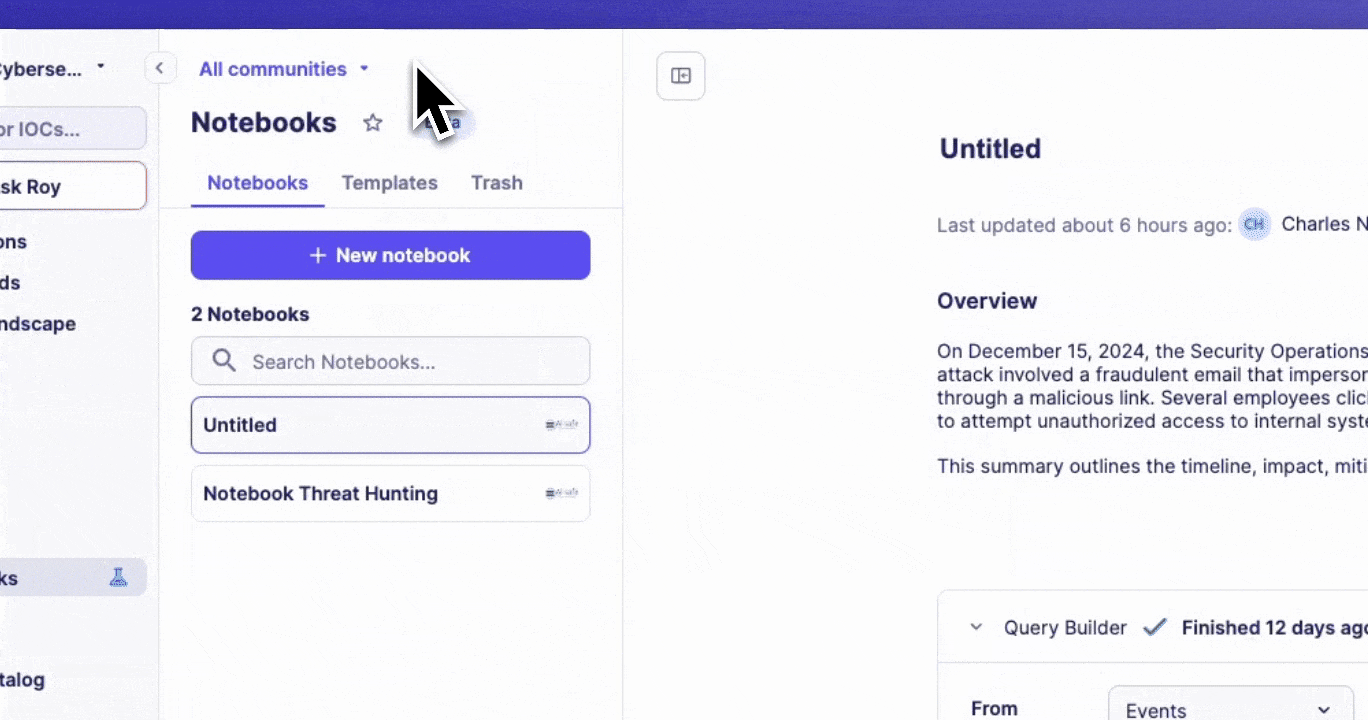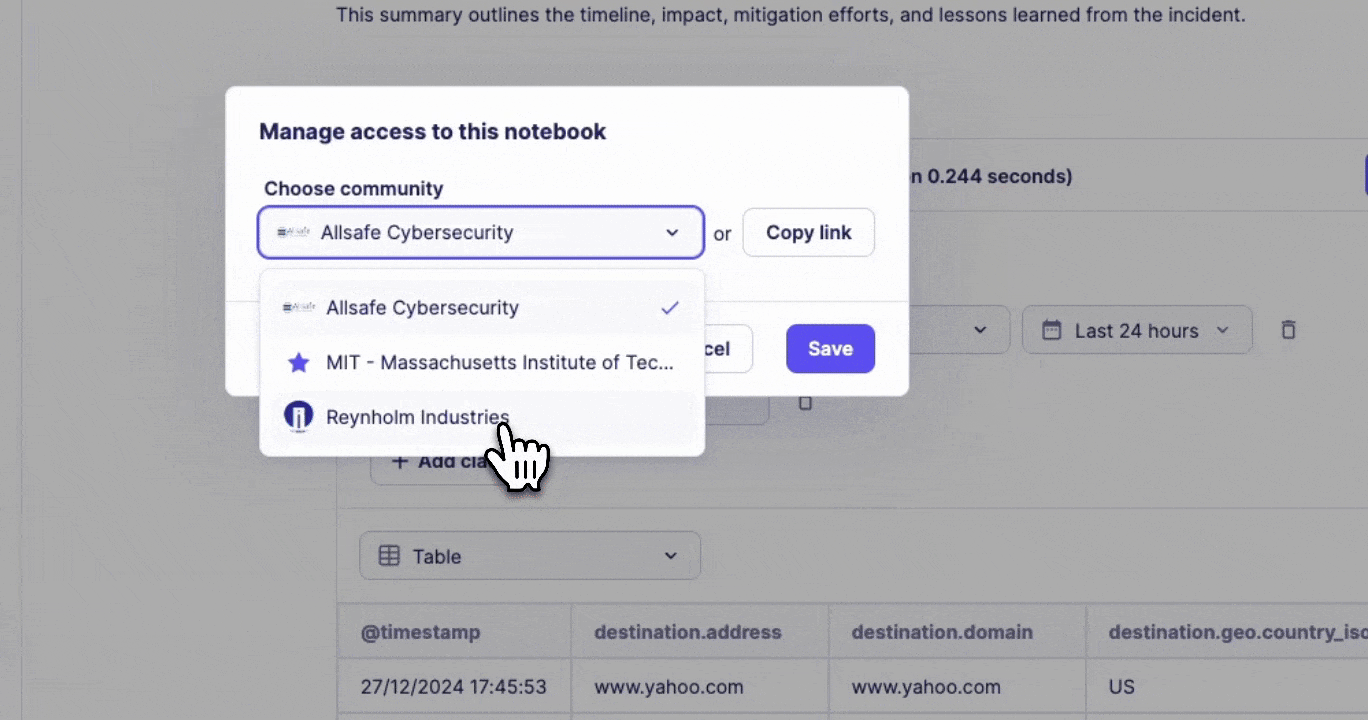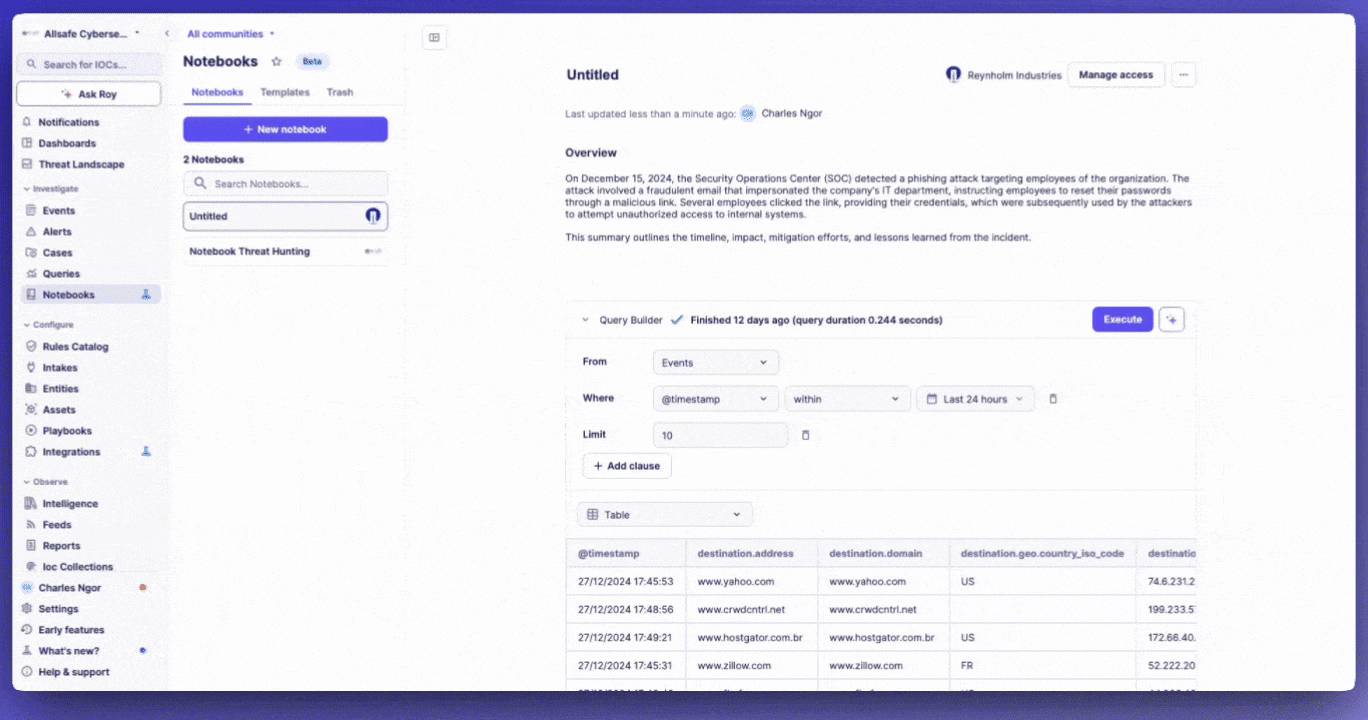
Multi-tenant support
- Individual notebook sharing
- Customer-specific reporting
- Secure information distribution
Share notebooks and templates directly with child tenants to ensure secure information distribution, provide incident reports, and share best practices with customers.
Notebook Management
Organization
- Use the search bar to find notebooks by their titles
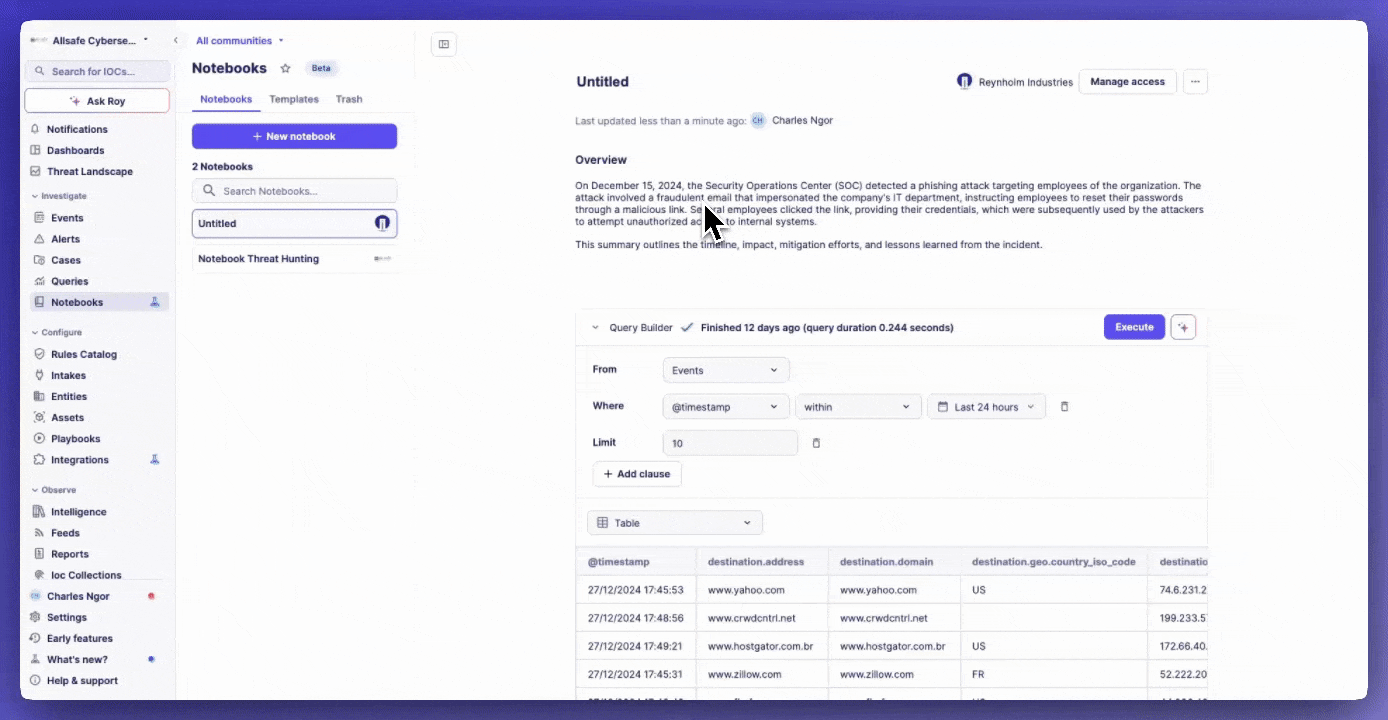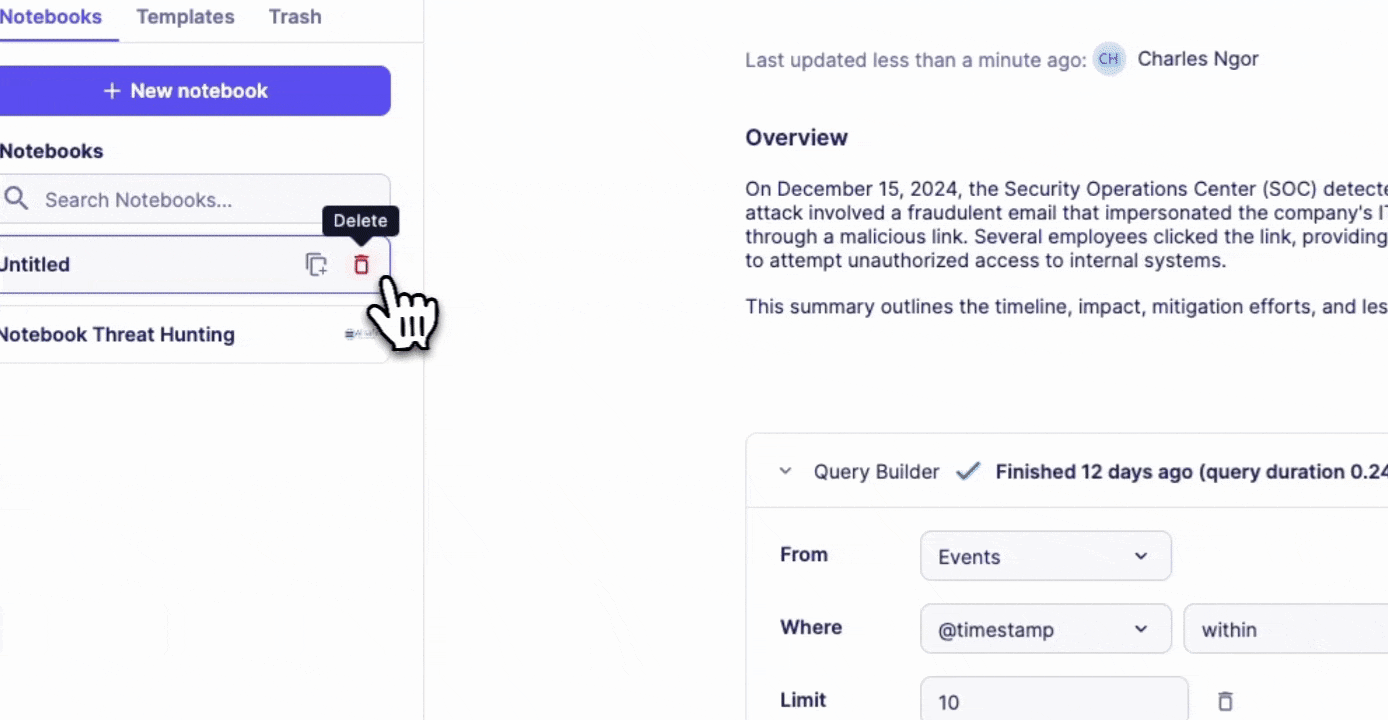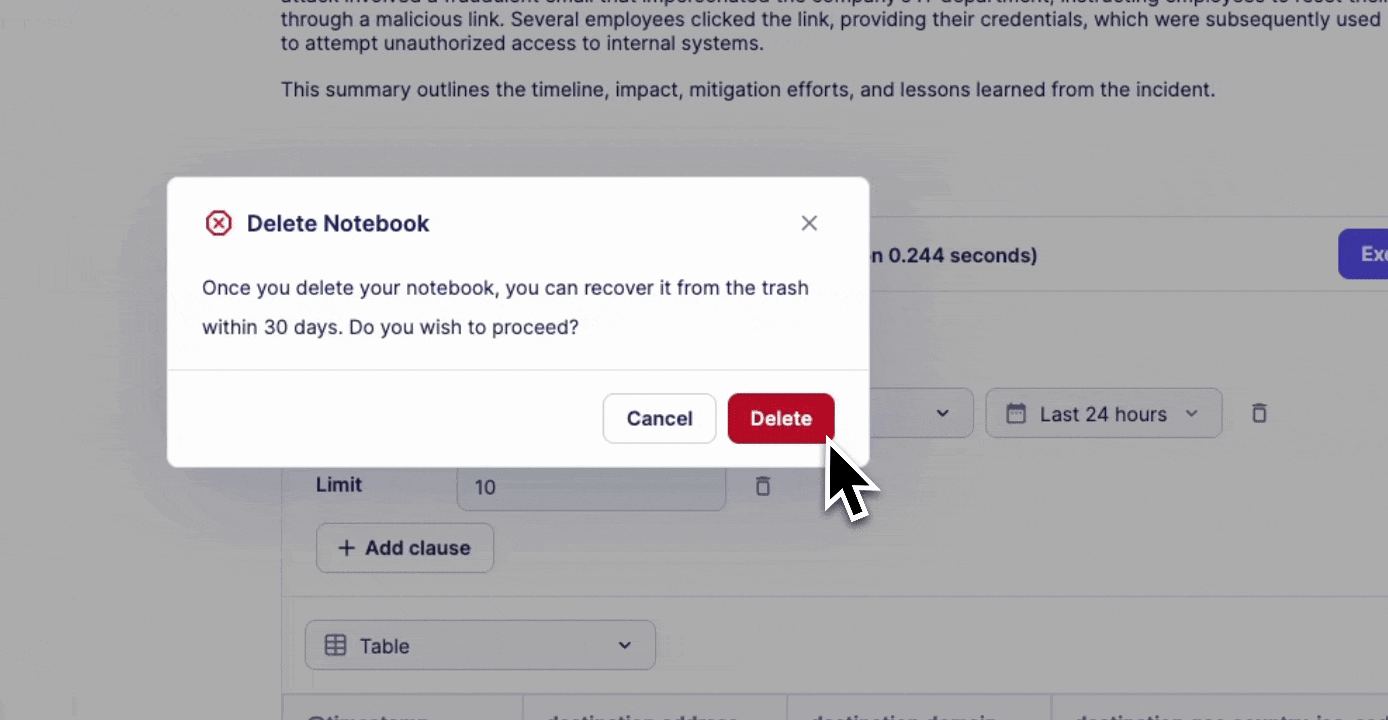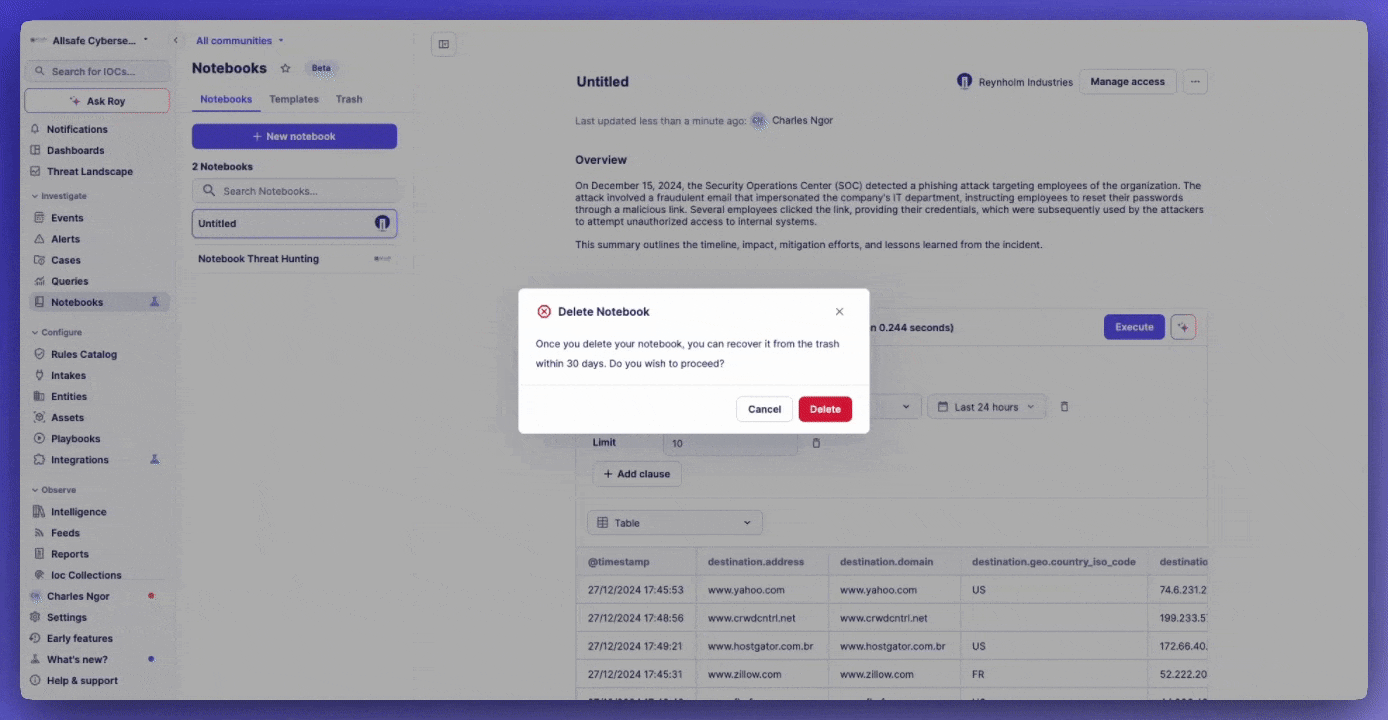
Deletion and Recovery
- Soft delete notebooks to trash
- 30-day recovery period
- Permanent deletion after 30 days
- Restore option available
Best Practices
- Use templates for standardized investigations
- Document all investigation steps
- Include relevant screenshots and evidence
- Utilize data visualization for complex data
- Maintain consistent formatting
- Regular template updates
- Proper sharing permissions management