Tenable.io
Overview
Tenable.io is a cloud-based exposure and vulnerability management platform that provides continuous visibility across on‑prem, cloud, container, and web application assets, combining automated discovery and scans with risk-based prioritization to help teams find, prioritize, and remediate issues faster—backed by granular admin controls, compliance reporting, and APIs/integrations that fit seamlessly into existing IT and SecOps workflows.
- Vendor: Tenable
- Product: Tenable Vulnerability Management
- Supported environment: SaaS
Configure
How to create an API token
To connect Tenable.io to Sekoia.io, you need to create an API key pair (Access Key and Secret Key) in your Tenable.io account. Follow these steps:
-
Access the My Account page.
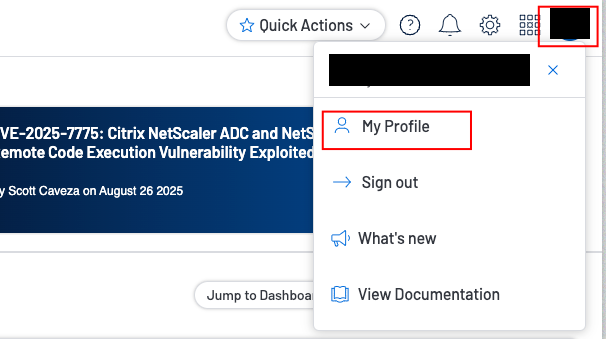
-
Click the API Keys tab.

-
Click Generate to generate credentials.
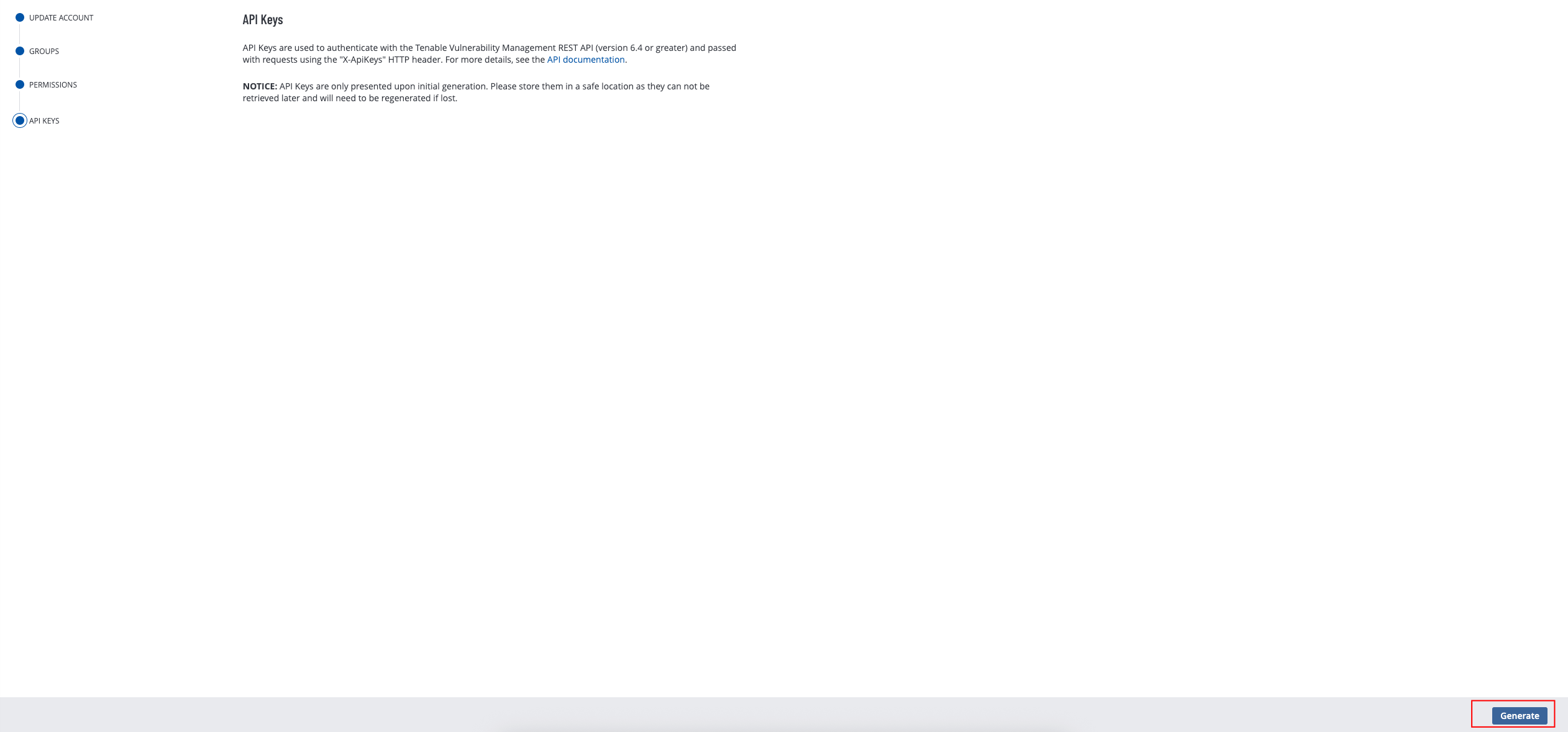
-
Copy the new access and secret keys to a safe location and start using them in Sekoia.io.
Warning
- Any existing API keys are replaced when you click the Generate button. You must update the applications where the previous API keys were used.
- The secret key is only shown when you create it. If you lose it, you must generate a new key pair.
Create your asset
To start getting your Tenable.io assets into Sekoia.io, you need to create an asset connector on the Assets page. To do so, follow these steps:
-
Click the Asset connectors button to create a new connector.
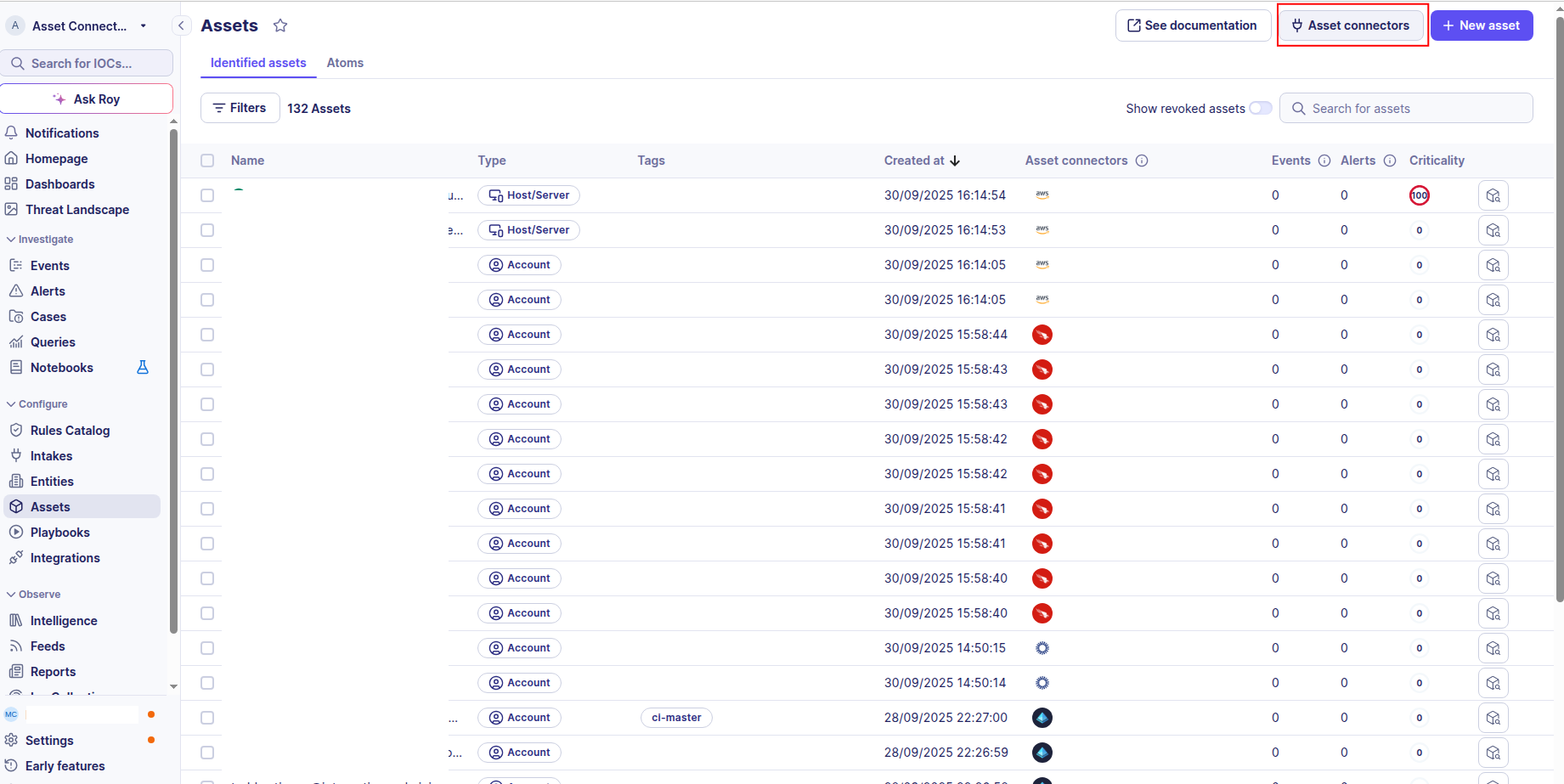
-
Click the + New connector button.
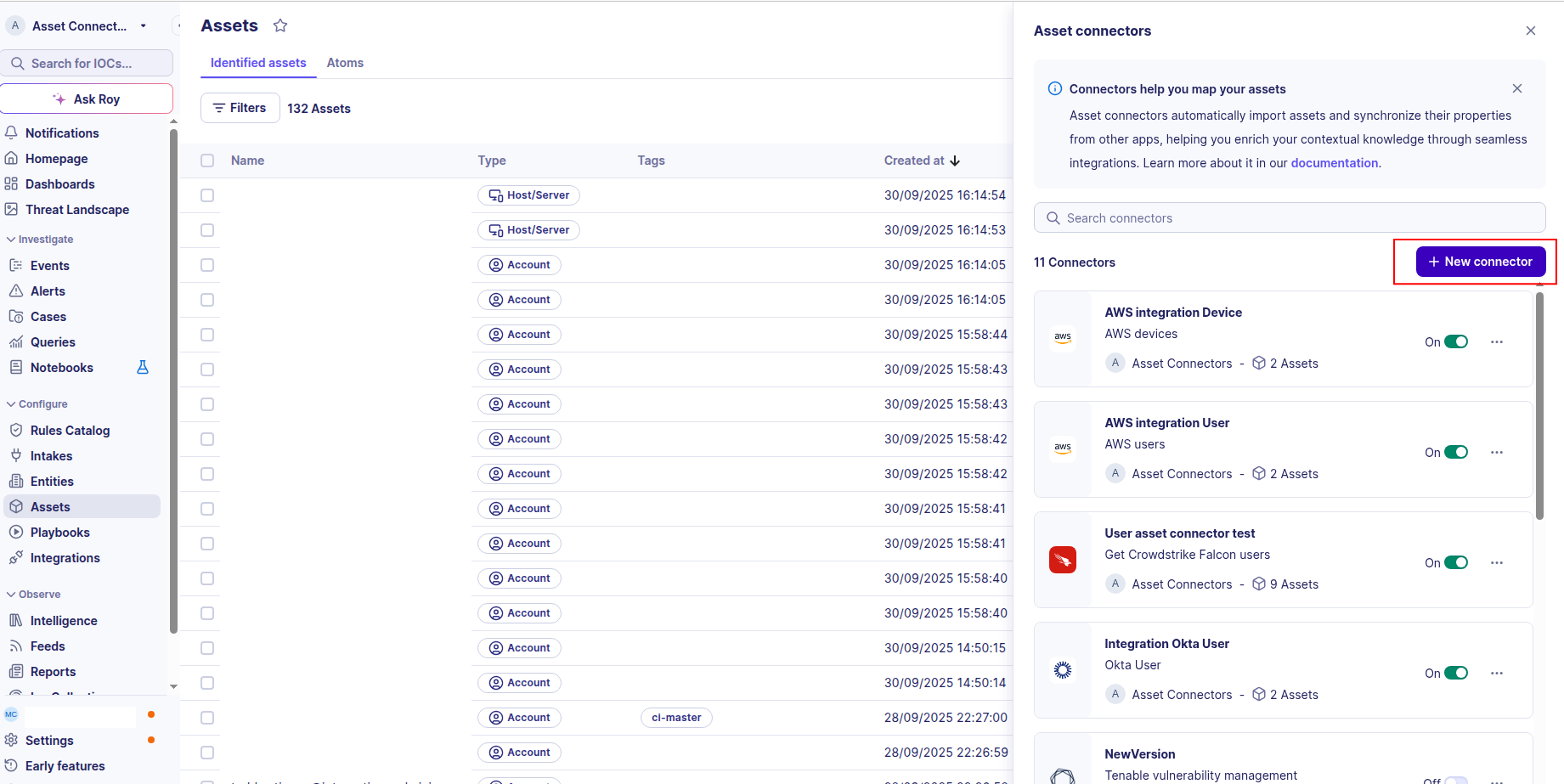
-
Choose Tenable Vulnerability Management, give it a name, and fill the required fields:
-
Test the connection by clicking the Test connector button.
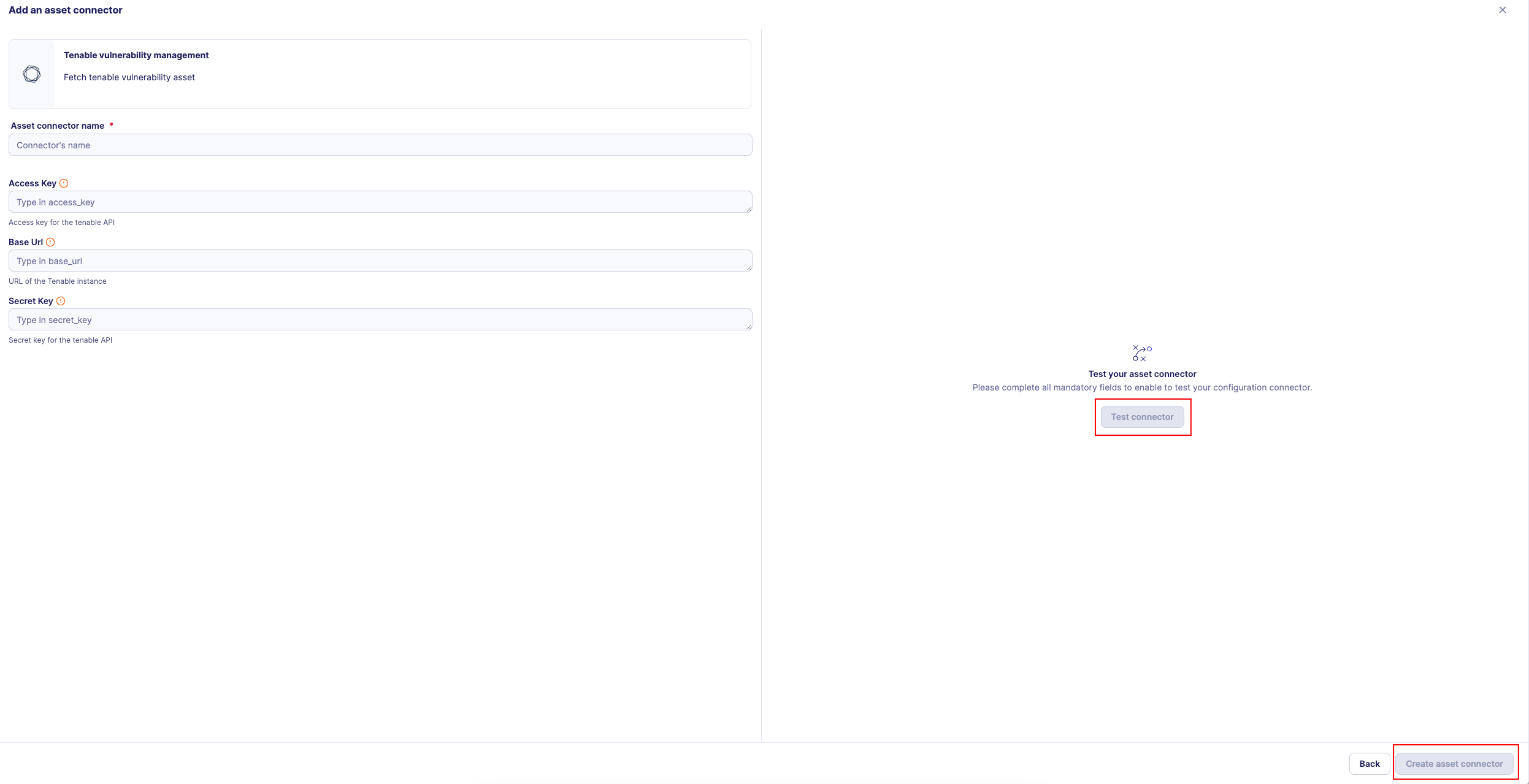
-
Click the Create asset connector button.
OCSF Mapping for Tenable Vulnerabilities
OCSF Class: vulnerability_finding
Class UID: 2002
Information Collected
The Tenable Vulnerabilities fetches comprehensive information and transforms it into the OCSF (Open Cybersecurity Schema Framework) format for standardized security monitoring and asset management.
API Response Examples
Tenable Critical Vulnerability
Critical vulnerability finding with CVE information
{
"vuln": {
"finding_id": "finding_12345",
"state": "OPEN",
"first_found": "2024-01-15T10:30:00.000Z",
"last_found": "2025-08-26T09:30:00.000Z",
"severity": "critical",
"plugin": {
"id": 11219,
"name": "Microsoft Windows SMB Shares Enumeration",
"type": "remote",
"synopsis": "The remote host is running an operating system that supports SMB.",
"description": "The remote host is running an operating system that supports SMB. It is possible to enumerate shares on the remote host.",
"see_also": [
"https://tools.ietf.org/html/rfc1001",
"https://tools.ietf.org/html/rfc1002"
],
"cve": [
"CVE-2020-1234",
"CVE-2020-5678"
],
"cvss_base_score": 9.8,
"cvss3_base_score": 9.8,
"publication_date": "2020-06-15T00:00:00.000Z",
"version": "1.42",
"vpr_v2": {
"score": 8.5
}
},
"source": "tenable_io"
},
"asset_info": {
"id": "a1b2c3d4e5f6g7h8",
"name": "PROD-SERVER-001",
"fqdn": [
"prod-server-001.example.com"
],
"hostname": [
"PROD-SERVER-001"
],
"ipv4": [
"192.168.1.50",
"10.0.0.25"
],
"system_type": [
"General Purpose"
],
"operating_system": [
"Windows Server 2019"
],
"aws_region": [
"us-east-1"
],
"first_seen": "2023-06-04T10:00:00.000Z",
"last_seen": "2025-08-26T09:30:00.000Z",
"created_at": "2023-06-04T10:00:00.000Z",
"has_agent": true,
"interfaces": [
{
"name": "eth0",
"ipv4": "192.168.1.50",
"mac": "00:1A:2B:3C:4D:5E"
}
]
}
}
Tenable Medium Vulnerability
Medium severity vulnerability finding
{
"vuln": {
"finding_id": "finding_67890",
"state": "REOPENED",
"first_found": "2024-03-20T14:15:00.000Z",
"last_found": "2025-08-20T08:45:00.000Z",
"severity": "medium",
"plugin": {
"id": 10662,
"name": "Apache Web Server Multiple Vulnerabilities",
"type": "remote",
"synopsis": "The remote host is running Apache Web Server.",
"description": "The remote host is running a version of Apache Web Server that is affected by multiple vulnerabilities.",
"see_also": [
"https://httpd.apache.org/security/vulnerabilities_24.html"
],
"cve": [
"CVE-2021-41773"
],
"cvss_base_score": 7.5,
"cvss3_base_score": 7.5,
"publication_date": "2021-10-05T00:00:00.000Z",
"version": "2.15",
"vpr_v2": {
"score": 5.2
}
},
"source": "tenable_io"
},
"asset_info": {
"id": "b2c3d4e5f6g7h8i9",
"name": "WEB-SERVER-002",
"fqdn": [
"web-server-002.example.com"
],
"hostname": [
"WEB-SERVER-002"
],
"ipv4": [
"192.168.1.60"
],
"system_type": [
"Web Server"
],
"operating_system": [
"Ubuntu 20.04 LTS"
],
"gcp_zone": [
"us-central1-a"
],
"first_seen": "2023-06-04T10:00:00.000Z",
"last_seen": "2025-08-26T09:30:00.000Z",
"created_at": "2023-06-04T10:00:00.000Z",
"has_agent": false,
"interfaces": [
{
"name": "eth0",
"ipv4": "192.168.1.60",
"mac": "00:2C:3D:4E:5F:60"
}
]
}
}
Data Mapping Table
The following table shows how source data is mapped to OCSF model fields:
| Source Field | OCSF Field Path | Description | Data Type | Logic |
|---|---|---|---|---|
vuln.state |
activity_id |
OCSF activity ID based on vulnerability state | integer |
Map OPEN=1 (Create), REOPENED=2 (Updated), FIXED=3 (Close) |
vuln.state |
activity_name |
OCSF activity name derived from vulnerability state | string |
Map state to activity (OPEN->Create, REOPENED->Updated, FIXED->Close) |
static: Findings |
category_name |
OCSF category name for security findings | string |
Always 'Findings' for vulnerability findings |
static: 2 |
category_uid |
OCSF category UID | integer |
Always 2 for Findings category |
static: Vulnerability Finding |
class_name |
OCSF class name | string |
Always 'Vulnerability Finding' |
static: 2002 |
class_uid |
OCSF class UID | integer |
Always 2002 for Vulnerability Finding |
computed: 200200 + activity_id |
type_uid |
OCSF type UID | integer |
Base 200200 + activity_id (1=200201, 2=200202, 3=200203) |
computed: 'Vulnerability Finding: ' + activity_name |
type_name |
OCSF type name | string |
Concatenate 'Vulnerability Finding: ' with activity name |
vuln.first_found |
time |
OCSF event timestamp (vulnerability first found time) | integer |
Convert ISO 8601 to Unix epoch for OCSF event timestamp |
static: Tenable |
metadata.product.name |
Source product name | string |
Always 'Tenable' |
vuln.plugin.version |
metadata.version |
Plugin/mapping version | string |
Direct mapping of plugin version |
static: 1.6.0 |
metadata.ocsf_version |
OCSF schema version | string |
Fixed OCSF schema version |
vuln.finding_id |
finding.uid |
Unique finding identifier | string |
Direct mapping of finding identifier |
vuln.plugin.type |
finding.type |
Finding type | string |
Direct mapping of plugin type (remote, local, etc.) |
vuln.source |
finding.source |
Source system of the finding | string |
Direct mapping of vulnerability source |
vuln.plugin.name |
finding.title |
Finding title | string |
Direct mapping of plugin name as finding title |
vuln.plugin.synopsis || vuln.plugin.description |
finding.description |
Finding description | string |
Use synopsis if available, otherwise use description |
vuln.plugin.see_also[0] |
finding.reference_url |
Primary reference URL | string |
Extract first reference URL from see_also array |
vuln.first_found |
finding.first_seen_time |
Finding first seen timestamp (Unix epoch) | integer |
Convert ISO 8601 to Unix epoch |
vuln.last_found |
finding.last_seen_time |
Finding last seen timestamp (Unix epoch) | integer |
Convert ISO 8601 to Unix epoch |
vuln.plugin.publication_date |
finding.created_time |
Finding/vulnerability creation timestamp (Unix epoch) | integer |
Convert ISO 8601 to Unix epoch |
static: Tenable Vulnerability Management |
finding.product.name |
Product providing the finding | string |
Always 'Tenable Vulnerability Management' |
static: N/A |
finding.fingerprints |
Finding fingerprints | string |
Placeholder for fingerprint data |
static: [{phase: Other, phase_id: 99}] |
finding.kill_chain |
Kill chain phases | array[object] |
Default kill chain phase |
vuln.plugin.cve |
vulnerabilities |
Associated vulnerabilities/CVEs | array[object] |
Create vulnerability objects with CVE IDs |
static: CVE |
vulnerabilities[0].type |
Vulnerability type identifier | string |
Always 'CVE' for vulnerability type |
vuln.plugin.cvss_base_score |
vulnerabilities[0].cvss.score |
CVSS base score | double |
Direct mapping of CVSS base score |
vuln.plugin.cvss3_base_score |
vulnerabilities[0].cvss3.score |
CVSS v3 base score | double |
Direct mapping of CVSS v3 base score |
vuln.plugin.description |
vulnerabilities[0].description |
Vulnerability description | string |
Direct mapping of plugin description |
vuln.plugin.name |
vulnerabilities[0].name |
Vulnerability name | string |
Direct mapping of plugin name as vulnerability name |
vuln.plugin.name |
vulnerabilities[0].title |
Vulnerability title | string |
Direct mapping of plugin name as vulnerability title |
vuln.plugin.description |
vulnerabilities[0].details |
Vulnerability details | string |
Direct mapping of plugin description for details |
vuln.plugin.see_also |
vulnerabilities[0].references |
Vulnerability reference links | array[string] |
Direct mapping of see_also links as references |
vuln.severity |
vulnerabilities[0].severity |
Vulnerability severity level | string |
Direct mapping of severity (critical, high, medium, low, info) |
static: Tenable |
vulnerabilities[0].source |
Vulnerability source | string |
Always 'Tenable' |
asset_info.id |
device.uid |
Device unique identifier | string |
Direct mapping of asset ID |
asset_info.system_type[0] |
device.type |
Device type | string |
Direct mapping of system type |
asset_info.system_type[0] |
device.type_id |
OCSF device type ID | integer |
Map system type to OCSF device type ID |
asset_info.hostname[0] || asset_info.name || asset_info.fqdn[0] |
device.hostname |
Device hostname | string |
Use hostname if available, otherwise name, otherwise FQDN |
asset_info.name |
device.name |
Device name | string |
Direct mapping of asset name |
asset_info.ipv4[0] |
device.ip |
Primary IPv4 address | string |
Extract first IPv4 address |
asset_info.operating_system[0] |
device.os.name |
Operating system name | string |
Direct mapping of operating system |
asset_info.operating_system[0] |
device.os.type |
Operating system type | string |
Map OS to OCSF OS type enum |
asset_info.operating_system[0] |
device.os.version |
Operating system version | string |
Extract version from OS string if available |
asset_info.interfaces |
device.network_interfaces |
Network interfaces | array[object] |
Direct mapping of network interfaces |
asset_info.aws_region[0] || asset_info.azure_location[0] || asset_info.gcp_zone[0] |
device.region |
Cloud region/location | string |
Use AWS region if available, otherwise Azure location, otherwise GCP zone |
asset_info.first_seen |
device.created_time |
Device creation/first seen timestamp (Unix epoch) | integer |
Convert ISO 8601 to Unix epoch |
asset_info.last_seen |
device.last_seen_time |
Device last seen timestamp (Unix epoch) | integer |
Convert ISO 8601 to Unix epoch |
asset_info.created_at |
device.updated_time |
Device updated timestamp (Unix epoch) | integer |
Convert ISO 8601 to Unix epoch |
asset_info.has_agent |
device.has_agent |
Whether device has Tenable agent | boolean |
Direct mapping of agent presence |
static: Tenable |
device.source |
Device information source | string |
Always 'Tenable' |
vuln.plugin.vpr_v2.score |
severity |
Overall event severity | string |
Map VPR score to severity level (8.5+=Critical, 6.5+=High, 4.5+=Medium, 2.5+=Low, <2.5=Informational) |
vuln.plugin.vpr_v2.score |
severity_id |
OCSF severity ID | integer |
Map VPR score to OCSF severity ID (5=Critical, 4=High, 3=Medium, 2=Low, 1=Informational) |
vuln.plugin.vpr_v2.score |
confidence_id |
OCSF confidence ID based on VPR score | integer |
Map VPR score to confidence (3=High [7+], 2=Medium [4-7), 1=Low [<4]) |
OCSF Model Structure
Vulnerability Finding: Create
Transformed Tenable vulnerability finding to OCSF Vulnerability Finding event
{
"activity_id": 1,
"activity_name": "Create",
"category_name": "Findings",
"category_uid": 2,
"class_name": "Vulnerability Finding",
"class_uid": 2002,
"type_name": "Vulnerability Finding: Create",
"type_uid": 200201,
"severity": "Critical",
"severity_id": 5,
"confidence_id": 3,
"time": 1705314600,
"metadata": {
"product": {
"name": "Tenable"
},
"version": "1.42"
},
"finding": {
"uid": "finding_12345",
"type": "remote",
"source": "tenable_io",
"title": "Microsoft Windows SMB Shares Enumeration",
"description": "The remote host is running an operating system that supports SMB. It is possible to enumerate shares on the remote host.",
"reference_url": "https://tools.ietf.org/html/rfc1001",
"first_seen_time": 1705314600,
"last_seen_time": 1725184200,
"created_time": 1592179200,
"product": {
"name": "Tenable Vulnerability Management"
},
"fingerprints": "N/A",
"kill_chain": [
{
"phase": "Other",
"phase_id": 99
}
]
},
"vulnerabilities": [
{
"type": "CVE",
"name": "CVE-2020-1234",
"title": "Microsoft Windows SMB Shares Enumeration",
"description": "The remote host is running an operating system that supports SMB.",
"details": "The remote host is running an operating system that supports SMB. It is possible to enumerate shares on the remote host.",
"severity": "critical",
"source": "Tenable",
"references": [
"https://tools.ietf.org/html/rfc1001",
"https://tools.ietf.org/html/rfc1002"
],
"cvss": {
"score": 9.8
},
"cvss3": {
"score": 9.8
}
}
],
"device": {
"uid": "a1b2c3d4e5f6g7h8",
"name": "PROD-SERVER-001",
"hostname": "PROD-SERVER-001",
"type": "General Purpose",
"ip": "192.168.1.50",
"has_agent": true,
"region": "us-east-1",
"source": "Tenable",
"created_time": 1685854800,
"updated_time": 1685854800,
"last_seen_time": 1725184200,
"os": {
"name": "Windows Server 2019",
"type": "Windows",
"version": "2019"
},
"network_interfaces": [
{
"name": "eth0",
"ipv4": "192.168.1.50",
"mac": "00:1A:2B:3C:4D:5E"
}
]
}
}