Microsoft Sentinel
Overview
- Vendor: Microsoft
- Supported environment: SaaS
- Detection based on: Alerts
- Supported application or feature:
- Incidents
Microsoft Sentinel is a cloud-native security information and event management (SIEM) service that provides intelligent security analytics for your entire enterprise at cloud scale. Get immediate visibility into your cloud, on-premises, and hybrid environments. Detect and respond to threats with built-in machine learning and artificial intelligence.
Specification
Prerequisites
-
Resource:
- Azure cloud tenant
- Microsoft Sentinel instance
-
Permissions:
- Administrator permissions to the Azure instance
Transport Protocol/Method
- HTTP/HTTPS for SaaS
Logs details
- Supported functionalities: See section Overview
- Supported type(s) of structure: JSON
- Supported verbosity level: Alert
Step-by-Step Configuration Procedure
Create an api key
Create an Azure application
- On the Azure Portal, in the search bar, go to
App registrations
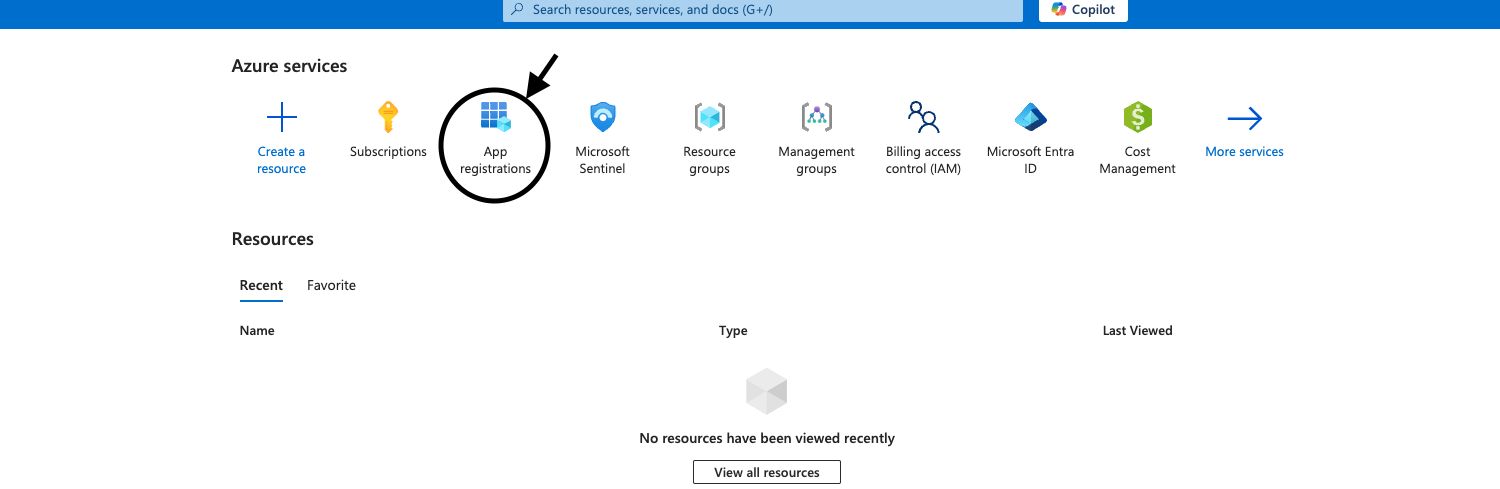
- Click
+ New registration - Type a name
- Select
Accounts in this organizational directory onlyoption as account type - Click
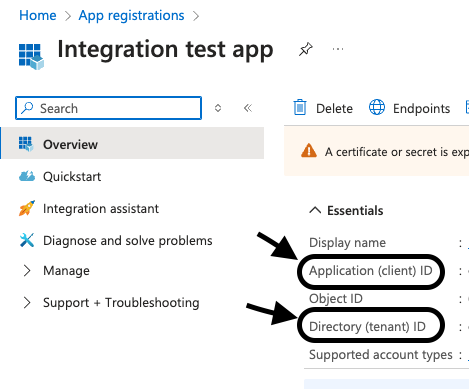
Register - From the
Overviewpage, copyApplication (client) IDandDirectory (tenant) ID
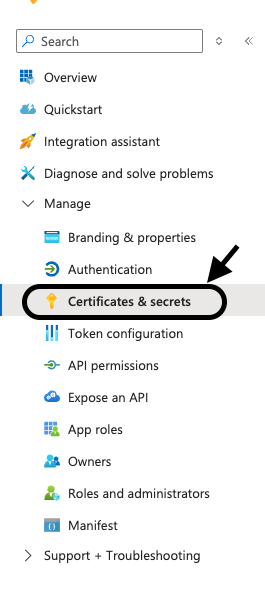
Create a client secret
- Go to
Manage>Certificates & secrets
- Click
+ New client secret
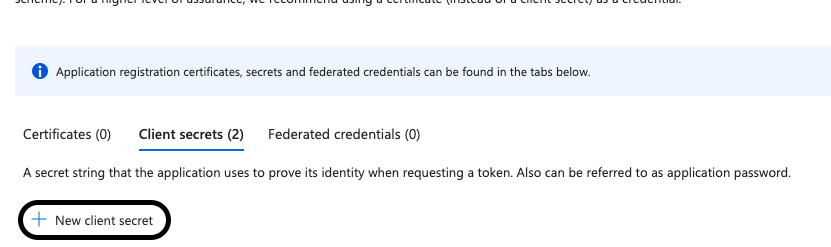
- Type a description and select the desirated expiration period
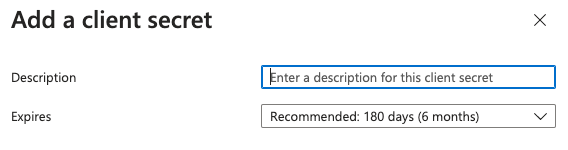
- Click
Add - Copy the
Valueof the client secret
Add role to the app
- In the search bar, go to
Subscriptions - Click on one of your subscriptions
- On the right panel, Click
Access control (IAM) - Click
+ Add>Add role assignment - In the
job function rolessub-tab, search forMicrosoft Sentinel Contributorand select it - Click
Next - Select
User, group or service principalas access - Click
+ Select members - Type the name of the Azure application created previously, select it and click
Select - Click
Review + assign - In the
Overviewpart, you can find theSubscription ID
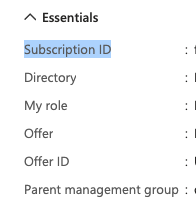
Note
- You can find the
workspacenameon theOverviewpage under name when you create yourMicrosoft Sentinelinstance. - The
resourcegroupdepends on the resource group in which you placed your instance. You can also find this on theOverview pageunderResource Group.
Create the intake
Go to the intake page and create a new intake from the format Microsoft Sentinel.
Raw Events Samples
In this section, you will find examples of raw logs as generated natively by the source. These examples are provided to help integrators understand the data format before ingestion into Sekoia.io. It is crucial for setting up the correct parsing stages and ensuring that all relevant information is captured.
{
"additional_properties": {},
"id": "/subscriptions/f1fa95bf-0000-0000-0000-910a79dc1f7b/resourceGroups/test/providers/Microsoft.OperationalInsights/workspaces/Test/providers/Microsoft.SecurityInsights/Incidents/13000000-0000-0000-0000-9b8460000000",
"name": "13000000-0000-0000-0000-9b8460000000",
"type": "Microsoft.SecurityInsights/Incidents",
"system_data": null,
"etag": "2e002c01-0000-0d00-0000-67a000000000",
"additional_data": {
"additional_properties": {},
"alerts_count": 0,
"bookmarks_count": 0,
"comments_count": 0,
"alert_product_names": [],
"tactics": []
},
"classification": "FalsePositive",
"classification_comment": "Not a malicious activity",
"classification_reason": "IncorrectAlertLogic",
"created_time_utc": "2025-02-03T13:32:12.236416+00:00",
"description": "connector test",
"incident_url": "https://portal.azure.com/#asset/Microsoft_Azure_Security_Insights/Incident/subscriptions/f1fa95bf-0000-0000-0000-910a79dc1f7b/resourceGroups/test/providers/Microsoft.OperationalInsights/workspaces/Test/providers/Microsoft.SecurityInsights/Incidents/13000000-0000-0000-0000-9b8460000000",
"incident_number": 11,
"labels": [
{
"additional_properties": {},
"label_name": "test",
"label_type": "User"
}
],
"last_activity_time_utc": "2025-02-03T13:32:11.509000+00:00",
"last_modified_time_utc": "2025-02-03T13:32:12.236416+00:00",
"owner": {
"additional_properties": {},
"assigned_to": "joe doe",
"email": "joe.doe@test.com",
"user_principal_name": "joe.doe@test.com",
"object_id": "40f54000-0000-0000-0000-4c990e00000000"
},
"related_analytic_rule_ids": [],
"severity": "Medium",
"status": "New",
"title": "test 11"
}
{
"additional_properties": {},
"id": "/subscriptions/f1fa95bf-631e-48e9-bbc7-910a79dc1f7b/resourceGroups/test/providers/Microsoft.OperationalInsights/workspaces/Test/providers/Microsoft.SecurityInsights/Incidents/2f880001-0000-0000-0000-30000d1a3000",
"name": "2f880001-0000-0000-0000-30000d1a3000",
"type": "Microsoft.SecurityInsights/Incidents",
"system_data": null,
"etag": "2d001bf8-0000-0d00-0000-67a000000000",
"additional_data": {
"additional_properties": {},
"alerts_count": 0,
"bookmarks_count": 0,
"comments_count": 0,
"alert_product_names": [],
"tactics": []
},
"classification": null,
"classification_comment": null,
"classification_reason": null,
"created_time_utc": "2025-02-03T13:29:41.551768+00:00",
"description": "connector test",
"incident_url": "https://portal.azure.com/#asset/Microsoft_Azure_Security_Insights/Incident/subscriptions/f1fa95bf-631e-48e9-bbc7-910a79dc1f7b/resourceGroups/test/providers/Microsoft.OperationalInsights/workspaces/Test/providers/Microsoft.SecurityInsights/Incidents/2f884fd1-aa45-4d80-8118-30accd1a389b",
"incident_number": 10,
"labels": [
{
"additional_properties": {},
"label_name": "test",
"label_type": "User"
}
],
"last_activity_time_utc": "2025-02-03T13:29:40.831000+00:00",
"last_modified_time_utc": "2025-02-03T13:29:41.551768+00:00",
"owner": {
"additional_properties": {},
"assigned_to": "joe doe",
"email": "joe.doe@test.com",
"user_principal_name": "joe.doe@test.com",
"object_id": "40f54fde-0000-0000-0000-4c990e00000000"
},
"related_analytic_rule_ids": [],
"severity": "Medium",
"status": "New",
"title": "test 10"
}
{
"additional_properties": {},
"id": "/subscriptions/f1fa95bf-631e-48e9-bbc7-910a79dc1f7b/resourceGroups/test/providers/Microsoft.OperationalInsights/workspaces/Test/providers/Microsoft.SecurityInsights/Incidents/368693b4-8d49-4bd7-ac9c-a6f1f2232a9a",
"name": "368693b4-8888-4444-cccc-aafff2232292",
"type": "Microsoft.SecurityInsights/Incidents",
"system_data": null,
"etag": "\"5b022666-0000-0d00-0000-ccb5cccc0000\"",
"additional_data": {
"additional_properties": {},
"alerts_count": 0,
"bookmarks_count": 0,
"comments_count": 0,
"alert_product_names": [],
"tactics": []
},
"classification": null,
"classification_comment": null,
"classification_reason": null,
"created_time_utc": "2025-02-19T11:36:38.757960+00:00",
"description": ":D",
"incident_url": "https://portal.azure.com/#asset/Microsoft_Azure_Security_Insights/Incident/subscriptions/f1fa95bf-631e-48e9-bbc7-910a79dc1f7b/resourceGroups/test/providers/Microsoft.OperationalInsights/workspaces/Test/providers/Microsoft.SecurityInsights/Incidents/36666344-8888-bbbb-cccc-a111fff3339a",
"incident_number": 14,
"labels": [
{
"additional_properties": {},
"label_name": "test_label",
"label_type": "User"
}
],
"last_activity_time_utc": "2025-02-19T11:36:38.207000+00:00",
"last_modified_time_utc": "2025-02-19T11:36:38.757960+00:00",
"owner": {
"additional_properties": {},
"assigned_to": null,
"email": null,
"user_principal_name": null,
"object_id": null
},
"related_analytic_rule_ids": [],
"severity": "Low",
"status": "Active",
"title": "Test 22"
}
{
"additional_properties": {},
"id": "/subscriptions/f1fa95bf-631e-48e9-bbc7-910a79dc1f7b/resourceGroups/integration/providers/Microsoft.OperationalInsights/workspaces/Integration/providers/Microsoft.SecurityInsights/Incidents/368693b4-8d49-4bd7-ac9c-a6f1f2232a9a",
"name": "368693b4-8d49-4bd7-ac9c-a6f1f2232a9a",
"type": "Microsoft.SecurityInsights/Incidents",
"system_data": null,
"etag": "\"5b02465b-0000-0d00-0000-67b5c2460000\"",
"additional_data": {
"additional_properties": {},
"alerts_count": 0,
"bookmarks_count": 0,
"comments_count": 0,
"alert_product_names": [],
"tactics": []
},
"classification": null,
"classification_comment": null,
"classification_reason": null,
"created_time_utc": "2025-02-19T11:36:38.757960+00:00",
"description": ":D",
"incident_url": "https://portal.azure.com/#asset/Microsoft_Azure_Security_Insights/Incident/subscriptions/f1fa95bf-631e-48e9-bbc7-910a79dc1f7b/resourceGroups/integration/providers/Microsoft.OperationalInsights/workspaces/Integration/providers/Microsoft.SecurityInsights/Incidents/368693b4-8d49-4bd7-ac9c-a6f1f2232a9a",
"incident_number": 14,
"labels": [
{
"additional_properties": {},
"label_name": "tagada",
"label_type": "User"
}
],
"last_activity_time_utc": "2025-02-19T11:36:38.207000+00:00",
"last_modified_time_utc": "2025-02-19T11:36:38.757960+00:00",
"owner": {
"additional_properties": {},
"assigned_to": null,
"email": null,
"user_principal_name": null,
"object_id": null
},
"related_analytic_rule_ids": [],
"severity": "Low",
"status": "Active",
"title": "Test 22"
}
Detection section
The following section provides information for those who wish to learn more about the detection capabilities enabled by collecting this intake. It includes details about the built-in rule catalog, event categories, and ECS fields extracted from raw events. This is essential for users aiming to create custom detection rules, perform hunting activities, or pivot in the events page.
No related built-in rules was found. This message is automatically generated.
Event Categories
The following table lists the data source offered by this integration.
| Data Source | Description |
|---|---|
Office 365 account logs |
Activity logs that provide data related to user accounts in Office 365. |
Office 365 audit logs |
Logs that detail actions taken by users and admins within Office 365 applications. |
Office 365 trace logs |
Logs that help in troubleshooting and monitoring the performance of Office 365 services. |
Third-party application logs |
Logs from applications not developed by Microsoft that can report security-relevant events. |
Windows event logs |
Logs generated by Windows systems that provide crucial information about system events, errors, and security. |
Web application firewall logs |
Security logs related to the actions of a web application firewall protecting a web applications. |
In details, the following table denotes the type of events produced by this integration.
| Name | Values |
|---|---|
| Kind | alert |
| Category | intrusion_detection |
| Type | info |
Transformed Events Samples after Ingestion
This section demonstrates how the raw logs will be transformed by our parsers. It shows the extracted fields that will be available for use in the built-in detection rules and hunting activities in the events page. Understanding these transformations is essential for analysts to create effective detection mechanisms with custom detection rules and to leverage the full potential of the collected data.
{
"message": "{\"additional_properties\":{},\"id\":\"/subscriptions/f1fa95bf-0000-0000-0000-910a79dc1f7b/resourceGroups/test/providers/Microsoft.OperationalInsights/workspaces/Test/providers/Microsoft.SecurityInsights/Incidents/13000000-0000-0000-0000-9b8460000000\",\"name\":\"13000000-0000-0000-0000-9b8460000000\",\"type\":\"Microsoft.SecurityInsights/Incidents\",\"system_data\":null,\"etag\":\"2e002c01-0000-0d00-0000-67a000000000\",\"additional_data\":{\"additional_properties\":{},\"alerts_count\":0,\"bookmarks_count\":0,\"comments_count\":0,\"alert_product_names\":[],\"tactics\":[]},\"classification\":\"FalsePositive\",\"classification_comment\":\"Not a malicious activity\",\"classification_reason\":\"IncorrectAlertLogic\",\"created_time_utc\":\"2025-02-03T13:32:12.236416+00:00\",\"description\":\"connector test\",\"incident_url\":\"https://portal.azure.com/#asset/Microsoft_Azure_Security_Insights/Incident/subscriptions/f1fa95bf-0000-0000-0000-910a79dc1f7b/resourceGroups/test/providers/Microsoft.OperationalInsights/workspaces/Test/providers/Microsoft.SecurityInsights/Incidents/13000000-0000-0000-0000-9b8460000000\",\"incident_number\":11,\"labels\":[{\"additional_properties\":{},\"label_name\":\"test\",\"label_type\":\"User\"}],\"last_activity_time_utc\":\"2025-02-03T13:32:11.509000+00:00\",\"last_modified_time_utc\":\"2025-02-03T13:32:12.236416+00:00\",\"owner\":{\"additional_properties\":{},\"assigned_to\":\"joe doe\",\"email\":\"joe.doe@test.com\",\"user_principal_name\":\"joe.doe@test.com\",\"object_id\":\"40f54000-0000-0000-0000-4c990e00000000\"},\"related_analytic_rule_ids\":[],\"severity\":\"Medium\",\"status\":\"New\",\"title\":\"test 11\"}",
"event": {
"category": [
"intrusion_detection"
],
"end": "2025-02-03T13:32:12.236416Z",
"kind": "alert",
"reason": "connector test",
"type": [
"info"
],
"url": "https://portal.azure.com/#asset/Microsoft_Azure_Security_Insights/Incident/subscriptions/f1fa95bf-0000-0000-0000-910a79dc1f7b/resourceGroups/test/providers/Microsoft.OperationalInsights/workspaces/Test/providers/Microsoft.SecurityInsights/Incidents/13000000-0000-0000-0000-9b8460000000"
},
"@timestamp": "2025-02-03T13:32:12.236416Z",
"log": {
"level": "Medium"
},
"microsoft": {
"sentinel": {
"classification": {
"comment": "Not a malicious activity",
"reason": "IncorrectAlertLogic",
"type": "FalsePositive"
},
"incident": {
"number": "11"
},
"status": "New",
"title": "test 11"
}
},
"observer": {
"product": "Sentinel",
"vendor": "Microsoft"
},
"user": {
"email": "joe.doe@test.com"
}
}
{
"message": "{\"additional_properties\":{},\"id\":\"/subscriptions/f1fa95bf-631e-48e9-bbc7-910a79dc1f7b/resourceGroups/test/providers/Microsoft.OperationalInsights/workspaces/Test/providers/Microsoft.SecurityInsights/Incidents/2f880001-0000-0000-0000-30000d1a3000\",\"name\":\"2f880001-0000-0000-0000-30000d1a3000\",\"type\":\"Microsoft.SecurityInsights/Incidents\",\"system_data\":null,\"etag\":\"2d001bf8-0000-0d00-0000-67a000000000\",\"additional_data\":{\"additional_properties\":{},\"alerts_count\":0,\"bookmarks_count\":0,\"comments_count\":0,\"alert_product_names\":[],\"tactics\":[]},\"classification\":null,\"classification_comment\":null,\"classification_reason\":null,\"created_time_utc\":\"2025-02-03T13:29:41.551768+00:00\",\"description\":\"connector test\",\"incident_url\":\"https://portal.azure.com/#asset/Microsoft_Azure_Security_Insights/Incident/subscriptions/f1fa95bf-631e-48e9-bbc7-910a79dc1f7b/resourceGroups/test/providers/Microsoft.OperationalInsights/workspaces/Test/providers/Microsoft.SecurityInsights/Incidents/2f884fd1-aa45-4d80-8118-30accd1a389b\",\"incident_number\":10,\"labels\":[{\"additional_properties\":{},\"label_name\":\"test\",\"label_type\":\"User\"}],\"last_activity_time_utc\":\"2025-02-03T13:29:40.831000+00:00\",\"last_modified_time_utc\":\"2025-02-03T13:29:41.551768+00:00\",\"owner\":{\"additional_properties\":{},\"assigned_to\":\"joe doe\",\"email\":\"joe.doe@test.com\",\"user_principal_name\":\"joe.doe@test.com\",\"object_id\":\"40f54fde-0000-0000-0000-4c990e00000000\"},\"related_analytic_rule_ids\":[],\"severity\":\"Medium\",\"status\":\"New\",\"title\":\"test 10\"}",
"event": {
"category": [
"intrusion_detection"
],
"end": "2025-02-03T13:29:41.551768Z",
"kind": "alert",
"reason": "connector test",
"type": [
"info"
],
"url": "https://portal.azure.com/#asset/Microsoft_Azure_Security_Insights/Incident/subscriptions/f1fa95bf-631e-48e9-bbc7-910a79dc1f7b/resourceGroups/test/providers/Microsoft.OperationalInsights/workspaces/Test/providers/Microsoft.SecurityInsights/Incidents/2f884fd1-aa45-4d80-8118-30accd1a389b"
},
"@timestamp": "2025-02-03T13:29:41.551768Z",
"log": {
"level": "Medium"
},
"microsoft": {
"sentinel": {
"incident": {
"number": "10"
},
"status": "New",
"title": "test 10"
}
},
"observer": {
"product": "Sentinel",
"vendor": "Microsoft"
},
"user": {
"email": "joe.doe@test.com"
}
}
{
"message": "{\"additional_properties\":{},\"id\":\"/subscriptions/f1fa95bf-631e-48e9-bbc7-910a79dc1f7b/resourceGroups/test/providers/Microsoft.OperationalInsights/workspaces/Test/providers/Microsoft.SecurityInsights/Incidents/368693b4-8d49-4bd7-ac9c-a6f1f2232a9a\",\"name\":\"368693b4-8888-4444-cccc-aafff2232292\",\"type\":\"Microsoft.SecurityInsights/Incidents\",\"system_data\":null,\"etag\":\"\\\"5b022666-0000-0d00-0000-ccb5cccc0000\\\"\",\"additional_data\":{\"additional_properties\":{},\"alerts_count\":0,\"bookmarks_count\":0,\"comments_count\":0,\"alert_product_names\":[],\"tactics\":[]},\"classification\":null,\"classification_comment\":null,\"classification_reason\":null,\"created_time_utc\":\"2025-02-19T11:36:38.757960+00:00\",\"description\":\":D\",\"incident_url\":\"https://portal.azure.com/#asset/Microsoft_Azure_Security_Insights/Incident/subscriptions/f1fa95bf-631e-48e9-bbc7-910a79dc1f7b/resourceGroups/test/providers/Microsoft.OperationalInsights/workspaces/Test/providers/Microsoft.SecurityInsights/Incidents/36666344-8888-bbbb-cccc-a111fff3339a\",\"incident_number\":14,\"labels\":[{\"additional_properties\":{},\"label_name\":\"test_label\",\"label_type\":\"User\"}],\"last_activity_time_utc\":\"2025-02-19T11:36:38.207000+00:00\",\"last_modified_time_utc\":\"2025-02-19T11:36:38.757960+00:00\",\"owner\":{\"additional_properties\":{},\"assigned_to\":null,\"email\":null,\"user_principal_name\":null,\"object_id\":null},\"related_analytic_rule_ids\":[],\"severity\":\"Low\",\"status\":\"Active\",\"title\":\"Test 22\"}",
"event": {
"category": [
"intrusion_detection"
],
"end": "2025-02-19T11:36:38.757960Z",
"kind": "alert",
"reason": ":D",
"type": [
"info"
],
"url": "https://portal.azure.com/#asset/Microsoft_Azure_Security_Insights/Incident/subscriptions/f1fa95bf-631e-48e9-bbc7-910a79dc1f7b/resourceGroups/test/providers/Microsoft.OperationalInsights/workspaces/Test/providers/Microsoft.SecurityInsights/Incidents/36666344-8888-bbbb-cccc-a111fff3339a"
},
"@timestamp": "2025-02-19T11:36:38.757960Z",
"log": {
"level": "Low"
},
"microsoft": {
"sentinel": {
"incident": {
"number": "14"
},
"status": "Active",
"title": "Test 22"
}
},
"observer": {
"product": "Sentinel",
"vendor": "Microsoft"
}
}
{
"message": "{\"additional_properties\":{},\"id\":\"/subscriptions/f1fa95bf-631e-48e9-bbc7-910a79dc1f7b/resourceGroups/integration/providers/Microsoft.OperationalInsights/workspaces/Integration/providers/Microsoft.SecurityInsights/Incidents/368693b4-8d49-4bd7-ac9c-a6f1f2232a9a\",\"name\":\"368693b4-8d49-4bd7-ac9c-a6f1f2232a9a\",\"type\":\"Microsoft.SecurityInsights/Incidents\",\"system_data\":null,\"etag\":\"\\\"5b02465b-0000-0d00-0000-67b5c2460000\\\"\",\"additional_data\":{\"additional_properties\":{},\"alerts_count\":0,\"bookmarks_count\":0,\"comments_count\":0,\"alert_product_names\":[],\"tactics\":[]},\"classification\":null,\"classification_comment\":null,\"classification_reason\":null,\"created_time_utc\":\"2025-02-19T11:36:38.757960+00:00\",\"description\":\":D\",\"incident_url\":\"https://portal.azure.com/#asset/Microsoft_Azure_Security_Insights/Incident/subscriptions/f1fa95bf-631e-48e9-bbc7-910a79dc1f7b/resourceGroups/integration/providers/Microsoft.OperationalInsights/workspaces/Integration/providers/Microsoft.SecurityInsights/Incidents/368693b4-8d49-4bd7-ac9c-a6f1f2232a9a\",\"incident_number\":14,\"labels\":[{\"additional_properties\":{},\"label_name\":\"tagada\",\"label_type\":\"User\"}],\"last_activity_time_utc\":\"2025-02-19T11:36:38.207000+00:00\",\"last_modified_time_utc\":\"2025-02-19T11:36:38.757960+00:00\",\"owner\":{\"additional_properties\":{},\"assigned_to\":null,\"email\":null,\"user_principal_name\":null,\"object_id\":null},\"related_analytic_rule_ids\":[],\"severity\":\"Low\",\"status\":\"Active\",\"title\":\"Test 22\"}",
"event": {
"category": [
"intrusion_detection"
],
"end": "2025-02-19T11:36:38.757960Z",
"kind": "alert",
"reason": ":D",
"type": [
"info"
],
"url": "https://portal.azure.com/#asset/Microsoft_Azure_Security_Insights/Incident/subscriptions/f1fa95bf-631e-48e9-bbc7-910a79dc1f7b/resourceGroups/integration/providers/Microsoft.OperationalInsights/workspaces/Integration/providers/Microsoft.SecurityInsights/Incidents/368693b4-8d49-4bd7-ac9c-a6f1f2232a9a"
},
"@timestamp": "2025-02-19T11:36:38.757960Z",
"log": {
"level": "Low"
},
"microsoft": {
"sentinel": {
"incident": {
"number": "14"
},
"status": "Active",
"title": "Test 22"
}
},
"observer": {
"product": "Sentinel",
"vendor": "Microsoft"
}
}
Extracted Fields
The following table lists the fields that are extracted, normalized under the ECS format, analyzed and indexed by the parser. It should be noted that infered fields are not listed.
| Name | Type | Description |
|---|---|---|
@timestamp |
date |
Date/time when the event originated. |
event.category |
keyword |
Event category. The second categorization field in the hierarchy. |
event.end |
date |
event.end contains the date when the event ended or when the activity was last observed. |
event.kind |
keyword |
The kind of the event. The highest categorization field in the hierarchy. |
event.reason |
keyword |
Reason why this event happened, according to the source |
event.type |
keyword |
Event type. The third categorization field in the hierarchy. |
event.url |
keyword |
Event investigation URL |
log.level |
keyword |
Log level of the log event. |
microsoft.sentinel.classification.comment |
keyword |
Comment on the classification of the alert |
microsoft.sentinel.classification.reason |
keyword |
Reason for the classification of the alert |
microsoft.sentinel.classification.type |
keyword |
Type of the classification |
microsoft.sentinel.incident.number |
keyword |
Incident number of the alert |
microsoft.sentinel.status |
keyword |
Status of the alert |
microsoft.sentinel.title |
keyword |
Title of the alert |
observer.product |
keyword |
The product name of the observer. |
observer.vendor |
keyword |
Vendor name of the observer. |
user.email |
keyword |
User email address. |
For more information on the Intake Format, please find the code of the Parser, Smart Descriptions, and Supported Events here.