FortiMail
Overview
Fortinet cybersecurity solutions sell physical products such as firewalls, plus software and services such as anti-virus protection, intrusion prevention systems, and endpoint security components.
- Vendor: Fortinet
- Supported environment: On Premise
- Detection based on: Telemetry
- Supported application or feature: Email Security
High-Level Architecture Diagram
- Type of integration: Outbound (PUSH to Sekoia.io)
- Schema
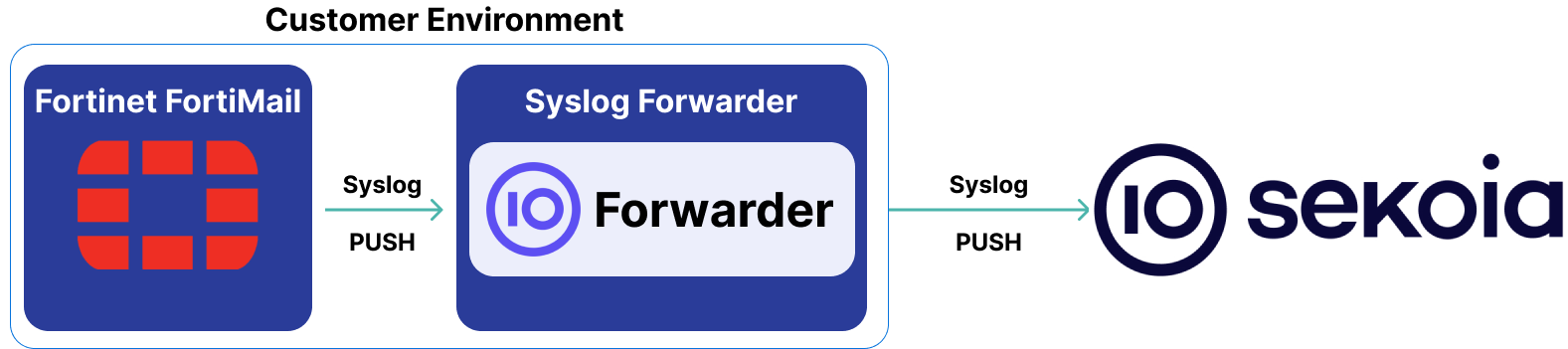
Specification
Prerequisites
- Resource:
- Self-managed syslog forwarder
- Network:
- Outbound traffic allowed
- Permissions:
- Administrator privileges on the FortiMail appliance
- Root access to the Linux server with the syslog forwarder
Transport Protocol/Method
- Indirect Syslog
Logs details
- Supported functionalities: See section Overview
- Supported type(s) of structure: Key-Value
- Supported verbosity level: Informational
Note
Log levels are based on the taxonomy of RFC5424. Adapt according to the terminology used by the editor.
Step-by-Step Configuration Procedure
Instructions on the 3rd Party Solution
This setup guide will show you how to forward your FortiMail logs to Sekoia.io by means of a syslog transport channel.
FortiMail Logs
- On FortiMail appliances, most of the important hardware and software activities that are relevant for security detection and analysis are logged into six files:
- History (statistics): Records all email traffic going through the FortiMail unit.
- System Event (kevent): Records system management activities, including changes to the system configuration as well as administrator and user log-ins and log-outs.
- Mail Event (event): Records mail activities.
- Antispam (spam): Records spam detection events.
- Antivirus (virus): Records virus intrusion events.
- Encryption (encrypt): Records detection of IBE-related events.
Transport to the Collector
-
Prerequisites:
- Administrator privileges on the FortiMail appliance
- Traffic towards the syslog must be open on
UDP 514
-
Configure Logging to a Syslog Server:
- Go to
Log and Report > Log Settings > Remote. - Click
Newto create a new entry OR double-click an existing entry to modify it. - Select
Enableto allow logging to a remote host. - In
Profile name, enter a profile name. - In
IP, enter the IP address of theSyslog serverwhere the FortiMail unit will store the logs. - In
Port, enter the UDP port number on which the Syslog server listens for connections (by default,UDP 514). - From
Level, select the severity level that a log message must equal or exceed in order to be recorded to this storage location. -
From
Facility, select the facility identifier that the FortiMail unit will use to identify itself when sending log messages.To easily identify log messages from the FortiMail unit when they are stored on a remote logging server, enter a unique facility identifier, and verify that no other network devices use the same facility identifier.
-
From
Log protocol, selectSyslog. - In
Logging Policy Configuration, enable the types of logs you want to record to this storage location. - Click
Create.
- Go to
Instruction on Sekoia
Configure Your Intake
This section will guide you through creating the intake object in Sekoia, which provides a unique identifier called the "Intake key." The Intake key is essential for later configuration, as it references the Community, Entity, and Parser (Intake Format) used when receiving raw events on Sekoia.
- Go to the Sekoia Intake page.
- Click on the
+ New Intakebutton at the top right of the page. - Search for your Intake by the product name in the search bar.
- Give it a Name and associate it with an Entity (and a Community if using multi-tenant mode).
- Click on
Create.
Note
For more details on how to use the Intake page and to find the Intake key you just created, refer to this documentation.
Configure a forwarder
To forward events using syslog to Sekoia.io, you need to update the syslog header with the intake key you previously created. Here is an example of your message before the forwarder
<%pri%>1 %timestamp:::date-rfc3339% %hostname% %app-name% %procid% LOG RAW_MESSAGE
<%pri%>1 %timestamp:::date-rfc3339% %hostname% %app-name% %procid% LOG [SEKOIA@53288 intake_key=\"YOUR_INTAKE_KEY\"] RAW_MESSAGE
To achieve this you can:
- Use the Sekoia.io forwarder which is the official supported way to collect data using the syslog protocol in Sekoia.io. In charge of centralizing data coming from many equipments/sources and forwarding them to Sekoia.io with the apporpriated format, it is a prepackaged option. You only have to provide your intake key as parameter.
- Use your own Syslog service instance. Maybe you already have an intance of one of these components on your side and want to reuse it in order to centralize data before forwarding them to Sekoia.io. When using this mode, you have to configure and maintain your component in order to respect the expected Sekoia.io format.
Warning
Only the Sekoia.io forwarder is officially supported. Other options are documented for reference purposes but do not have official support.
Raw Events Samples
In this section, you will find examples of raw logs as generated natively by the source. These examples are provided to help integrators understand the data format before ingestion into Sekoia.io. It is crucial for setting up the correct parsing stages and ensuring that all relevant information is captured.
time=10:45:27 device_id=123 log_id=000000 type=encrypt pri=information session_id="ziuhiohzf" msg="User user1@1.ca read secure message, id:'ziuhiohzf', sent from: 'user2@2.ca', subject: 'ppt file'"
to=<jdoe@example.com> delay=00:00:06 xdelay=00:00:06 mailer=esmtp pri=165917 relay= [3.4.5.6] dsn=2.0.0 stat=Sent (Ok: queued as 4T9pxY2qZtz2XPBPX)
time=17:07:46.124 device_id=FEVM020000087260 log_id=00000 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id="1Z11R1T1" msg="from=person.fr, size=26135, class=0, nrcpts=1, msgid=something.com, proto=ESMTP, daemon=SMTP_MTA, relay=notifications [1.1.1.1]"
time=05:25:47.932 device_id=TestDeviceId log_id=0003014907 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id="testsessionid" msg="from=<info@testtest-error.art>, size=0, class=0, nrcpts=0, proto=SMTP, daemon=SMTP_MTA, relay=[1.2.3.4]"
time=18:33:35.615 device_id=xcvfg log_id=0003007072 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id="13KGXMHI007058-13KGXMHK007058" msg="to=<contact@example.com>, delay=00:00:06, xdelay=00:00:06, mailer=esmtp, pri=165917, relay= [188.165.36.237], dsn=2.0.0, stat=Sent (Ok: queued as 4T9pxY2qZtz2XPBPX)"
time=18:33:35.615 device_id=xcvfg log_id=0003007072 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id="13KGXMHI007058-13KGXMHK007058" msg="to=<contact@example.com>, delay=00:00:06, xdelay=00:00:06, mailer=esmtp, pri=165917, relay=smtp.example.org [188.165.36.237], dsn=2.0.0, stat=Sent (Ok: queued as 4T9pxY2qZtz2XPBPX)"
time=18:33:36.601 device_id=123456 log_id=0003007110 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id="12345" msg="STARTTLS=server, relay=something.com [1.1.1.1], version=TLSv1.2, verify=NO, cipher=ECDHE-RSA-something, bits=256/256"
time=18:33:35.615 device_id=xcvfg log_id=0003007072 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id="13KGXMHI007058-13KGXMHK007058" msg="to=<mh.fr>, delay=00:00:13, xdelay=00:00:12, mailer=esmtp, pri=50733, relay=email.fr. [1.1.1.1], dsn=2.0.0, stat=Sent (Ok: queued as C41457FCE6)"
time=15:12:29.013 device_id=FEVM020000087260 log_id=0003014581 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id="13RDCREi014579-13RDCREj014579" msg="to=<sjira.eu>, delay=00:00:02, xdelay=00:00:01, mailer=esmtp, pri=40733, relay=mail.eu. [1.1.1.1], dsn=2.0.0, stat=Sent (<email.fr> [InternalId=96830037688413, Hostname=sphinx] 12426 bytes in 0.118, 102,604 KB/sec Queued mail for delivery)"
time=17:34:06.188 device_id=0000 log_id=123 type=kevent subtype=dns pri=information msg="UDP DNS response is truncated, try DNS query in TCP (happened 385350 time(s)), DNS question section:{name=something.com, qtype=16, class=1}"
time=11:19:15.002 device_id=123 log_id=0701031743 type=kevent subtype=admin pri=information scope=o365 user=j.doe ui=GUI(1.2.3.4) action=login status=success reason=none msg="User j.doe login successfully from GUI(1.2.3.4)"
time=15:03:24.344 device_id=FFFF log_id=YY type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id="AAA-BBB" msg="to=<johndoe>, delay=00:00:01, xdelay=00:00:01, mailer=esmtp, pri=2290731, relay= [1.2.3.4], dsn=2.0.0, stat=Sent (ok: Message 88943067 accepted)"
time=14:35:47.153 device_id=123 log_id=0000 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id="14SCZkrD013672-14SCZkrF013672" msg="STARTTLS=client, cert-subject=/CN=EX-01, cert-issuer=/CN=EX-01, verifymsg=unable to get local issuer certificate"
time=16:10:33.138 device_id=123 log_id=123 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id="000" msg="STARTTLS=server, cert-subject=/C=US/ST=California/L=Mountain View/O=Google LLC/CN=something.com, cert-issuer=issuer, verifymsg=unable to get local issuer certificate"
time=14:25:48.564 device_id=123 log_id=0000 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id="0000" msg="STARTTLS=server, cert-subject=/something.fr, cert-issuer=issuer name, verifymsg=self signed certificate in certificate chain"
time=10:50:36.931 device_id=FEVM020000087260 log_id=0003008733 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id="1548fVq5008733-1548fVq5008733" msg="to=postmaster, delay=00:00:50, mailer=local, pri=58900, dsn=5.1.1, stat=User unknown(Reason from remote:550 5.1.1 User unknown)"
time=16:01:46.183 device_id=123 log_id=123 type=spam subtype=default pri=information session_id="00000" client_name="mail.outlook.com" client_ip="2.2.2.2" dst_ip="1.1.1.1" from="" to="mail.fr" subject="Détail de votre quarantaine: [ 1 message(s) en quarantaine entre le jeu. 15 avr. 2021 14 h 00 +0200 et le jeu. 15 avr. 2021 16 h 00 +0200 ]" msg="File name: icon_deleteall.png, scanned by Antivirus Scanner(clean)"
time=15:08:03.466 device_id=device log_id=121416 type=spam subtype=default pri=information session_id="123456" client_name="client" client_ip="2.2.2.2" dst_ip="1.1.1.1" from="whatever.com" to="something.com" subject="définitivement aimé cette idée et a pris la décision de vous la montrer" msg="FortiGuard-AntiSpam identified spam URL: http://something.something.photos/apmix"
time=10:00:08.543 device_id=abc log_id=0300025551 type=spam subtype=default pri=information session_id="123456" client_name="something.live" client_ip="2.2.2.2" dst_ip="1.1.1.1" from="nereply.live" to="info@pms-becus.com" subject="new order to UK" msg="File name: file.ppt(checksum:122452), scanned by Antivirus Scanner(detected)"
time=09:59:32.943 device_id=FEVM020000087260 log_id=0300025171 type=spam subtype=default pri=information session_id="15N7xWCW025167-15N7xWCX025167" client_name="mail@sth.com" client_ip="2.2.2.2" dst_ip="1.1.1.1" from="target.fr" to="source.com" subject="Vos impressions de documents au meilleur prix !" msg="FortiGuard-WebFilter identified URL: url.fr, category: Spam URLs, id: 86."
time=14:16:45.427 device_id=123 log_id=0300017253 type=spam subtype=default pri=information session_id="15N7xWCW025167-15N7xWCX025167" client_name="mail.example.org" client_ip="1.2.3.4" dst_ip="5.6.7.8" from="johndoe@example.org" to="jane.doe@example.org" subject="Ring phone promotion" msg="FortiGuard-WebFilter identified URL(category: Phishing, id: 61): https://www.example.org/emailing/promotion.html"
time=11:37:27.544 device_id=ABC log_id=0200017947 type=statistics pri=information session_id="123" client_name="Address.com" client_ip="2.2.2.2" client_cc="FR" dst_ip="1.1.1.1" from="something.fr" hfrom="something.fr" to="something.fr" polid="0:1:1" domain="host.com" mailer="mta" resolved="OK" src_type="int" direction="in" virus="" disposition="Accept" classifier="Domain Safe" message_length="112389" subject=confidential subject
time=16:17:10.683 device_id=ABC log_id=1234271 type=virus subtype=fortisandbox pri=information from="" to="" client_name="" client_ip="" session_id="123456789" msg="File file.pdf (checksum: 1234271) has been scanned by FortiSandbox. Scan result: rating=CLEAN"
time=14:18:20.030 device_id=123 log_id=0103021373 type=virus subtype=fortisandbox pri=information scope=o365 from="" to="" client_name="" client_ip="" session_id="15N7xWCW025167-15N7xWCX025167" msg="URL https://example.org/path/image.jpg has been scanned by FortiSandbox. Scan result: rating=CLEAN"
time=14:18:14.805 device_id=123 log_id=0103001910 type=virus subtype=fortisandbox pri=information from="" to="" client_name="" client_ip="" session_id="15N7xWCW025167-15N7xWCX025167" msg="URL https://example.org/path/image.jpg has been scanned by FortiSandbox. Scan result: rating=CLEAN"
Detection section
The following section provides information for those who wish to learn more about the detection capabilities enabled by collecting this intake. It includes details about the built-in rule catalog, event categories, and ECS fields extracted from raw events. This is essential for users aiming to create custom detection rules, perform hunting activities, or pivot in the events page.
Related Built-in Rules
The following Sekoia.io built-in rules match the intake Fortinet FortiMail. This documentation is updated automatically and is based solely on the fields used by the intake which are checked against our rules. This means that some rules will be listed but might not be relevant with the intake.
SEKOIA.IO x Fortinet FortiMail on ATT&CK Navigator
Advanced IP Scanner
Detects the use of Advanced IP Scanner. Seems to be a popular tool for ransomware groups.
- Effort: master
Burp Suite Tool Detected
Burp Suite is a cybersecurity tool. When used as a proxy service, its purpose is to intercept packets and modify them to send them to the server. Burp Collaborator is a network service that Burp Suite uses to help discover many kinds of vulnerabilities (vulnerabilities scanner).
- Effort: intermediate
CVE-2020-0688 Microsoft Exchange Server Exploit
Detects the exploitation of CVE-2020-0688. The POC exploit a .NET serialization vulnerability in the Exchange Control Panel (ECP) web page. The vulnerability is due to Microsoft Exchange Server not randomizing the keys on a per-installation basis resulting in them using the same validationKey and decryptionKey values. With knowledge of these, values an attacker can craft a special viewstate to use an OS command to be executed by NT_AUTHORITY\SYSTEM using .NET deserialization. To exploit this vulnerability, an attacker needs to leverage the credentials of an account it had already compromised to authenticate to OWA.
- Effort: elementary
CVE-2020-17530 Apache Struts RCE
Detects the exploitation of the Apache Struts RCE vulnerability (CVE-2020-17530).
- Effort: intermediate
CVE-2021-20021 SonicWall Unauthenticated Administrator Access
Detects the exploitation of SonicWall Unauthenticated Admin Access.
- Effort: advanced
CVE-2021-20023 SonicWall Arbitrary File Read
Detects Arbitrary File Read, which can be used with other vulnerabilities as a mean to obtain outputs generated by attackers, or sensitive data.
- Effort: advanced
CVE-2021-22893 Pulse Connect Secure RCE Vulnerability
Detects potential exploitation of the authentication by-pass vulnerability that can allow an unauthenticated user to perform remote arbitrary file execution on the Pulse Connect Secure gateway. It is highly recommended to apply the Pulse Secure mitigations and seach for indicators of compromise on affected servers if you are in doubt over the integrity of your Pulse Connect Secure product.
- Effort: intermediate
Certify Or Certipy
Detects the use of certify and certipy which are two different tools used to enumerate and abuse Active Directory Certificate Services.
- Effort: advanced
Cobalt Strike Default Beacons Names
Detects the default names of Cobalt Strike beacons / payloads.
- Effort: intermediate
Correlation Potential DNS Tunnel
Detects domain name which is longer than 62 characters and requested at least 50 times in a 10 minutes range time. Long domain names are distinctive of DNS tunnels.
- Effort: advanced
Credential Dump Tools Related Files
Detects processes or file names related to credential dumping tools and the dropped files they generate by default.
- Effort: advanced
Cryptomining
Detection of domain names potentially related to cryptomining activities.
- Effort: master
Detect requests to Konni C2 servers
This rule detects requests to Konni C2 servers. These patterns come from an analysis done in 2022, September.
- Effort: elementary
Discord Suspicious Download
Discord is a messaging application. It allows users to create their own communities to share messages and attachments. Those attachments have little to no overview and can be downloaded by almost anyone, which has been abused by attackers to host malicious payloads.
- Effort: advanced
Dynamic DNS Contacted
Detect communication with dynamic dns domain. This kind of domain is often used by attackers. This rule can trigger false positive in non-controlled environment because dynamic dns is not always malicious.
- Effort: master
EvilProxy Phishing Domain
Detects subdomains potentially generated by the EvilProxy adversary-in-the-middle phishing platform. Inspect the other subdomains of the domain to identify the landing page, and determine if the user submitted credentials. This rule has a small percentage of false positives on legitimate domains.
- Effort: intermediate
Exfiltration Domain
Detects traffic toward a domain flagged as a possible exfiltration vector.
- Effort: master
HackTools Suspicious Names
Quick-win rule to detect the default process names or file names of several HackTools.
- Effort: advanced
Koadic MSHTML Command
Detects Koadic payload using MSHTML module
- Effort: intermediate
PasswordDump SecurityXploded Tool
Detects the execution of the PasswordDump SecurityXploded Tool
- Effort: elementary
Possible Malicious File Double Extension
Detects request to potential malicious file with double extension
- Effort: elementary
Potential DNS Tunnel
Detects domain name which is longer than 62 characters. Long domain names are distinctive of DNS tunnels.
- Effort: advanced
ProxyShell Microsoft Exchange Suspicious Paths
Detects suspicious calls to Microsoft Exchange resources, in locations related to webshells observed in campaigns using this vulnerability.
- Effort: elementary
RTLO Character
Detects RTLO (Right-To-Left character) in file and process names.
- Effort: elementary
Raccoon Stealer 2.0 Legitimate Third-Party DLL Download URL
Detects Raccoon Stealer 2.0 malware downloading legitimate third-party DLLs from its C2 server. These legitimate DLLs are used by the information stealer to collect data on the compromised hosts.
- Effort: elementary
Remote Access Tool Domain
Detects traffic toward a domain flagged as a Remote Administration Tool (RAT).
- Effort: master
Remote Monitoring and Management Software - AnyDesk
Detect artifacts related to the installation or execution of the Remote Monitoring and Management tool AnyDesk.
- Effort: master
Remote Monitoring and Management Software - Atera
Detect artifacts related to the installation or execution of the Remote Monitoring and Management tool Atera.
- Effort: master
SEKOIA.IO Intelligence Feed
Detect threats based on indicators of compromise (IOCs) collected by SEKOIA's Threat and Detection Research team.
- Effort: elementary
Sekoia.io EICAR Detection
Detects observables in Sekoia.io CTI tagged as EICAR, which are fake samples meant to test detection.
- Effort: master
Sign-In Via Known AiTM Phishing Kit
Detects a sign-in attempt from an IP address belonging to a known adversary-in-the-middle phishing kit.
- Effort: elementary
Suspicious Download Links From Legitimate Services
Detects users clicking on Google docs links to download suspicious files. This technique was used a lot by Bazar Loader in the past.
- Effort: intermediate
Suspicious Email Attachment Received
Detects email containing a suspicious file as an attachment, based on its extension.
- Effort: advanced
Suspicious File Name
Detects suspicious file name possibly linked to malicious tool.
- Effort: advanced
Suspicious PROCEXP152.sys File Created In Tmp
Detects the creation of the PROCEXP152.sys file in the application-data local temporary folder. This driver is used by Sysinternals Process Explorer but also by KDU (https://github.com/hfiref0x/KDU) or Ghost-In-The-Logs (https://github.com/bats3c/Ghost-In-The-Logs), which uses KDU. Note - Clever attackers may easily bypass this detection by just renaming the driver filename. Therefore just Medium-level and don't rely on it.
- Effort: advanced
Suspicious TOR Gateway
Detects suspicious TOR gateways. Gateways are often used by the victim to pay and decrypt the encrypted files without installing TOR. Tor intercepts the network traffic from one or more apps on user’s computer, usually the user web browser, and shuffles it through a number of randomly-chosen computers before passing it on to its destination. This disguises user location, and makes it harder for servers to pick him/her out on repeat visits, or to tie together separate visits to different sites, this making tracking and surveillance more difficult. Before a network packet starts its journey, user’s computer chooses a random list of relays and repeatedly encrypts the data in multiple layers, like an onion. Each relay knows only enough to strip off the outermost layer of encryption, before passing what’s left on to the next relay in the list.
- Effort: advanced
Suspicious URI Used In A Lazarus Campaign
Detects suspicious requests to a specific URI, usually on an .asp page. The website is often compromised.
- Effort: intermediate
TOR Usage Generic Rule
Detects TOR usage globally, whether the IP is a destination or source. TOR is short for The Onion Router, and it gets its name from how it works. TOR intercepts the network traffic from one or more apps on user’s computer, usually the user web browser, and shuffles it through a number of randomly-chosen computers before passing it on to its destination. This disguises user location, and makes it harder for servers to pick him/her out on repeat visits, or to tie together separate visits to different sites, this making tracking and surveillance more difficult. Before a network packet starts its journey, user’s computer chooses a random list of relays and repeatedly encrypts the data in multiple layers, like an onion. Each relay knows only enough to strip off the outermost layer of encryption, before passing what’s left on to the next relay in the list.
- Effort: master
Telegram Bot API Request
Detects suspicious DNS queries to api.telegram.org used by Telegram Bots of any kind
- Effort: advanced
WCE wceaux.dll Creation
Detects wceaux.dll creation while Windows Credentials Editor (WCE) is executed.
- Effort: intermediate
Event Categories
The following table lists the data source offered by this integration.
| Data Source | Description |
|---|---|
Email gateway |
date_source: "Fortinet email security solution" |
Transformed Events Samples after Ingestion
This section demonstrates how the raw logs will be transformed by our parsers. It shows the extracted fields that will be available for use in the built-in detection rules and hunting activities in the events page. Understanding these transformations is essential for analysts to create effective detection mechanisms with custom detection rules and to leverage the full potential of the collected data.
{
"message": "time=10:45:27 device_id=123 log_id=000000 type=encrypt pri=information session_id=\"ziuhiohzf\" msg=\"User user1@1.ca read secure message, id:'ziuhiohzf', sent from: 'user2@2.ca', subject: 'ppt file'\"",
"event": {
"kind": "encrypt",
"message": "User user1@1.ca read secure message, id:'ziuhiohzf', sent from: 'user2@2.ca', subject: 'ppt file'"
},
"action": {
"outcome_reason": "User user1@1.ca read secure message, id:'ziuhiohzf', sent from: 'user2@2.ca', subject: 'ppt file'",
"properties": {
"device_id": "123",
"log_id": "000000",
"session_id": "ziuhiohzf"
}
},
"log": {
"hostname": "abc",
"level": "information"
}
}
{
"message": "to=<jdoe@example.com> delay=00:00:06 xdelay=00:00:06 mailer=esmtp pri=165917 relay= [3.4.5.6] dsn=2.0.0 stat=Sent (Ok: queued as 4T9pxY2qZtz2XPBPX)",
"action": {
"properties": {
"mailer": "esmtp"
}
},
"email": {
"to": {
"address": [
"jdoe@example.com"
]
}
},
"log": {
"level": "165917"
}
}
{
"message": "time=17:07:46.124 device_id=FEVM020000087260 log_id=00000 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id=\"1Z11R1T1\" msg=\"from=person.fr, size=26135, class=0, nrcpts=1, msgid=something.com, proto=ESMTP, daemon=SMTP_MTA, relay=notifications [1.1.1.1]\"",
"event": {
"action": "NONE",
"category": "smtp",
"kind": "event",
"message": "from=person.fr, size=26135, class=0, nrcpts=1, msgid=something.com, proto=ESMTP, daemon=SMTP_MTA, relay=notifications [1.1.1.1]"
},
"action": {
"outcome_reason": "from=person.fr, size=26135, class=0, nrcpts=1, msgid=something.com, proto=ESMTP, daemon=SMTP_MTA, relay=notifications [1.1.1.1]",
"properties": {
"class": "0",
"daemon": "SMTP_MTA",
"device_id": "FEVM020000087260",
"log_id": "00000",
"message_id": "something.com",
"nrcpts": "1",
"relay": "notifications",
"session_id": "1Z11R1T1",
"user_identifier": "mail"
}
},
"destination": {
"address": "notifications",
"domain": "notifications",
"ip": "1.1.1.1"
},
"email": {
"from": {
"address": [
"person.fr"
]
}
},
"file": {
"size": 26135
},
"log": {
"hostname": "hostname",
"level": "information"
},
"network": {
"protocol": "ESMTP"
},
"related": {
"hosts": [
"notifications"
],
"ip": [
"1.1.1.1"
]
}
}
{
"message": "time=05:25:47.932 device_id=TestDeviceId log_id=0003014907 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id=\"testsessionid\" msg=\"from=<info@testtest-error.art>, size=0, class=0, nrcpts=0, proto=SMTP, daemon=SMTP_MTA, relay=[1.2.3.4]\"",
"event": {
"action": "NONE",
"category": "smtp",
"kind": "event",
"message": "from=<info@testtest-error.art>, size=0, class=0, nrcpts=0, proto=SMTP, daemon=SMTP_MTA, relay=[1.2.3.4]"
},
"action": {
"outcome_reason": "from=<info@testtest-error.art>, size=0, class=0, nrcpts=0, proto=SMTP, daemon=SMTP_MTA, relay=[1.2.3.4]",
"properties": {
"class": "0",
"daemon": "SMTP_MTA",
"device_id": "TestDeviceId",
"log_id": "0003014907",
"nrcpts": "0",
"relay": "1.2.3.4",
"session_id": "testsessionid",
"user_identifier": "mail"
}
},
"destination": {
"address": "1.2.3.4",
"ip": "1.2.3.4"
},
"email": {
"from": {
"address": [
"info@testtest-error.art"
]
}
},
"file": {
"size": 0
},
"log": {
"level": "information"
},
"network": {
"protocol": "SMTP"
},
"related": {
"ip": [
"1.2.3.4"
]
}
}
{
"message": "time=18:33:35.615 device_id=xcvfg log_id=0003007072 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id=\"13KGXMHI007058-13KGXMHK007058\" msg=\"to=<contact@example.com>, delay=00:00:06, xdelay=00:00:06, mailer=esmtp, pri=165917, relay= [188.165.36.237], dsn=2.0.0, stat=Sent (Ok: queued as 4T9pxY2qZtz2XPBPX)\"",
"event": {
"action": "NONE",
"category": "smtp",
"kind": "event",
"message": "to=<contact@example.com>, delay=00:00:06, xdelay=00:00:06, mailer=esmtp, pri=165917, relay= [188.165.36.237], dsn=2.0.0, stat=Sent (Ok: queued as 4T9pxY2qZtz2XPBPX)",
"reason": "Sent (Ok: queued as 4T9pxY2qZtz2XPBPX)"
},
"action": {
"outcome_reason": "to=<contact@example.com>, delay=00:00:06, xdelay=00:00:06, mailer=esmtp, pri=165917, relay= [188.165.36.237], dsn=2.0.0, stat=Sent (Ok: queued as 4T9pxY2qZtz2XPBPX)",
"properties": {
"delay": "00:00:06",
"device_id": "xcvfg",
"dsn_version": "2.0.0",
"log_id": "0003007072",
"mailer": "esmtp",
"priority_level_msg": "165917",
"relay": "188.165.36.237",
"session_id": "13KGXMHI007058-13KGXMHK007058",
"user_identifier": "mail",
"xdelay": "00:00:06"
}
},
"destination": {
"address": "188.165.36.237",
"ip": "188.165.36.237"
},
"email": {
"to": {
"address": [
"contact@example.com"
]
}
},
"log": {
"level": "information"
},
"related": {
"ip": [
"188.165.36.237"
]
},
"user": {
"email": "contact@example.com"
}
}
{
"message": "time=18:33:35.615 device_id=xcvfg log_id=0003007072 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id=\"13KGXMHI007058-13KGXMHK007058\" msg=\"to=<contact@example.com>, delay=00:00:06, xdelay=00:00:06, mailer=esmtp, pri=165917, relay=smtp.example.org [188.165.36.237], dsn=2.0.0, stat=Sent (Ok: queued as 4T9pxY2qZtz2XPBPX)\"",
"event": {
"action": "NONE",
"category": "smtp",
"kind": "event",
"message": "to=<contact@example.com>, delay=00:00:06, xdelay=00:00:06, mailer=esmtp, pri=165917, relay=smtp.example.org [188.165.36.237], dsn=2.0.0, stat=Sent (Ok: queued as 4T9pxY2qZtz2XPBPX)",
"reason": "Sent (Ok: queued as 4T9pxY2qZtz2XPBPX)"
},
"action": {
"outcome_reason": "to=<contact@example.com>, delay=00:00:06, xdelay=00:00:06, mailer=esmtp, pri=165917, relay=smtp.example.org [188.165.36.237], dsn=2.0.0, stat=Sent (Ok: queued as 4T9pxY2qZtz2XPBPX)",
"properties": {
"delay": "00:00:06",
"device_id": "xcvfg",
"dsn_version": "2.0.0",
"log_id": "0003007072",
"mailer": "esmtp",
"priority_level_msg": "165917",
"relay": "smtp.example.org",
"session_id": "13KGXMHI007058-13KGXMHK007058",
"user_identifier": "mail",
"xdelay": "00:00:06"
}
},
"destination": {
"address": "smtp.example.org",
"domain": "smtp.example.org",
"ip": "188.165.36.237",
"size_in_char": 16
},
"email": {
"to": {
"address": [
"contact@example.com"
]
}
},
"log": {
"level": "information"
},
"related": {
"hosts": [
"smtp.example.org"
],
"ip": [
"188.165.36.237"
]
},
"user": {
"email": "contact@example.com"
}
}
{
"message": "time=18:33:36.601 device_id=123456 log_id=0003007110 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id=\"12345\" msg=\"STARTTLS=server, relay=something.com [1.1.1.1], version=TLSv1.2, verify=NO, cipher=ECDHE-RSA-something, bits=256/256\"",
"event": {
"action": "NONE",
"category": "smtp",
"kind": "event",
"message": "STARTTLS=server, relay=something.com [1.1.1.1], version=TLSv1.2, verify=NO, cipher=ECDHE-RSA-something, bits=256/256"
},
"action": {
"outcome_reason": "STARTTLS=server, relay=something.com [1.1.1.1], version=TLSv1.2, verify=NO, cipher=ECDHE-RSA-something, bits=256/256",
"properties": {
"bits_sent_ratio": "256/256",
"device_id": "123456",
"log_id": "0003007110",
"relay": "something.com",
"session_id": "12345",
"start_tls": "server",
"user_identifier": "mail",
"verify": "NO"
}
},
"destination": {
"address": "something.com",
"domain": "something.com",
"ip": "1.1.1.1"
},
"log": {
"hostname": "123",
"level": "information"
},
"related": {
"hosts": [
"something.com"
],
"ip": [
"1.1.1.1"
]
},
"tls": {
"cipher": "ECDHE-RSA-something"
}
}
{
"message": "time=18:33:35.615 device_id=xcvfg log_id=0003007072 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id=\"13KGXMHI007058-13KGXMHK007058\" msg=\"to=<mh.fr>, delay=00:00:13, xdelay=00:00:12, mailer=esmtp, pri=50733, relay=email.fr. [1.1.1.1], dsn=2.0.0, stat=Sent (Ok: queued as C41457FCE6)\"",
"event": {
"action": "NONE",
"category": "smtp",
"kind": "event",
"message": "to=<mh.fr>, delay=00:00:13, xdelay=00:00:12, mailer=esmtp, pri=50733, relay=email.fr. [1.1.1.1], dsn=2.0.0, stat=Sent (Ok: queued as C41457FCE6)",
"reason": "Sent (Ok: queued as C41457FCE6)"
},
"action": {
"outcome_reason": "to=<mh.fr>, delay=00:00:13, xdelay=00:00:12, mailer=esmtp, pri=50733, relay=email.fr. [1.1.1.1], dsn=2.0.0, stat=Sent (Ok: queued as C41457FCE6)",
"properties": {
"delay": "00:00:13",
"device_id": "xcvfg",
"dsn_version": "2.0.0",
"log_id": "0003007072",
"mailer": "esmtp",
"priority_level_msg": "50733",
"relay": "email.fr.",
"session_id": "13KGXMHI007058-13KGXMHK007058",
"user_identifier": "mail",
"xdelay": "00:00:12"
}
},
"destination": {
"address": "email.fr.",
"domain": "email.fr.",
"ip": "1.1.1.1",
"size_in_char": 9
},
"email": {
"to": {
"address": [
"mh.fr"
]
}
},
"log": {
"hostname": "1234",
"level": "information"
},
"related": {
"hosts": [
"email.fr."
],
"ip": [
"1.1.1.1"
]
},
"user": {
"email": "mh.fr"
}
}
{
"message": "time=15:12:29.013 device_id=FEVM020000087260 log_id=0003014581 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id=\"13RDCREi014579-13RDCREj014579\" msg=\"to=<sjira.eu>, delay=00:00:02, xdelay=00:00:01, mailer=esmtp, pri=40733, relay=mail.eu. [1.1.1.1], dsn=2.0.0, stat=Sent (<email.fr> [InternalId=96830037688413, Hostname=sphinx] 12426 bytes in 0.118, 102,604 KB/sec Queued mail for delivery)\"",
"event": {
"action": "NONE",
"category": "smtp",
"kind": "event",
"message": "to=<sjira.eu>, delay=00:00:02, xdelay=00:00:01, mailer=esmtp, pri=40733, relay=mail.eu. [1.1.1.1], dsn=2.0.0, stat=Sent (<email.fr> [InternalId=96830037688413, Hostname=sphinx] 12426 bytes in 0.118, 102,604 KB/sec Queued mail for delivery)",
"reason": "Sent (<email.fr> [InternalId=96830037688413, Hostname=sphinx] 12426 bytes in 0.118, 102,604 KB/sec Queued mail for delivery)"
},
"action": {
"outcome_reason": "to=<sjira.eu>, delay=00:00:02, xdelay=00:00:01, mailer=esmtp, pri=40733, relay=mail.eu. [1.1.1.1], dsn=2.0.0, stat=Sent (<email.fr> [InternalId=96830037688413, Hostname=sphinx] 12426 bytes in 0.118, 102,604 KB/sec Queued mail for delivery)",
"properties": {
"delay": "00:00:02",
"device_id": "FEVM020000087260",
"dsn_version": "2.0.0",
"log_id": "0003014581",
"mailer": "esmtp",
"priority_level_msg": "40733",
"relay": "mail.eu.",
"session_id": "13RDCREi014579-13RDCREj014579",
"user_identifier": "mail",
"xdelay": "00:00:01"
}
},
"destination": {
"address": "mail.eu.",
"domain": "mail.eu.",
"ip": "1.1.1.1",
"size_in_char": 8
},
"email": {
"to": {
"address": [
"sjira.eu"
]
}
},
"log": {
"hostname": "1234",
"level": "information"
},
"related": {
"hosts": [
"mail.eu."
],
"ip": [
"1.1.1.1"
]
},
"user": {
"email": "sjira.eu"
}
}
{
"message": "time=17:34:06.188 device_id=0000 log_id=123 type=kevent subtype=dns pri=information msg=\"UDP DNS response is truncated, try DNS query in TCP (happened 385350 time(s)), DNS question section:{name=something.com, qtype=16, class=1}\"",
"event": {
"category": "dns",
"kind": "kevent",
"message": "UDP DNS response is truncated, try DNS query in TCP (happened 385350 time(s)), DNS question section:{name=something.com, qtype=16, class=1}"
},
"action": {
"outcome_reason": "UDP DNS response is truncated, try DNS query in TCP (happened 385350 time(s)), DNS question section:{name=something.com, qtype=16, class=1}",
"properties": {
"device_id": "0000",
"log_id": "123"
}
},
"log": {
"hostname": "hostname",
"level": "information"
}
}
{
"message": "time=11:19:15.002 device_id=123 log_id=0701031743 type=kevent subtype=admin pri=information scope=o365 user=j.doe ui=GUI(1.2.3.4) action=login status=success reason=none msg=\"User j.doe login successfully from GUI(1.2.3.4)\"",
"event": {
"action": "login",
"category": "admin",
"kind": "kevent",
"message": "User j.doe login successfully from GUI(1.2.3.4)"
},
"action": {
"outcome_reason": "User j.doe login successfully from GUI(1.2.3.4)",
"properties": {
"device_id": "123",
"event_status": "success",
"log_id": "0701031743",
"user_identifier": "GUI(1.2.3.4)"
}
},
"log": {
"level": "information"
},
"related": {
"ip": [
"1.2.3.4"
]
},
"source": {
"address": "1.2.3.4",
"ip": "1.2.3.4"
}
}
{
"message": "time=15:03:24.344 device_id=FFFF log_id=YY type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id=\"AAA-BBB\" msg=\"to=<johndoe>, delay=00:00:01, xdelay=00:00:01, mailer=esmtp, pri=2290731, relay= [1.2.3.4], dsn=2.0.0, stat=Sent (ok: Message 88943067 accepted)\"",
"event": {
"action": "NONE",
"category": "smtp",
"kind": "event",
"message": "to=<johndoe>, delay=00:00:01, xdelay=00:00:01, mailer=esmtp, pri=2290731, relay= [1.2.3.4], dsn=2.0.0, stat=Sent (ok: Message 88943067 accepted)",
"reason": "Sent (ok: Message 88943067 accepted)"
},
"action": {
"outcome_reason": "to=<johndoe>, delay=00:00:01, xdelay=00:00:01, mailer=esmtp, pri=2290731, relay= [1.2.3.4], dsn=2.0.0, stat=Sent (ok: Message 88943067 accepted)",
"properties": {
"delay": "00:00:01",
"device_id": "FFFF",
"dsn_version": "2.0.0",
"log_id": "YY",
"mailer": "esmtp",
"priority_level_msg": "2290731",
"relay": "1.2.3.4",
"session_id": "AAA-BBB",
"user_identifier": "mail",
"xdelay": "00:00:01"
}
},
"destination": {
"address": "1.2.3.4",
"ip": "1.2.3.4"
},
"email": {
"to": {
"address": [
"johndoe"
]
}
},
"log": {
"hostname": "abc",
"level": "information"
},
"related": {
"ip": [
"1.2.3.4"
]
},
"user": {
"email": "johndoe"
}
}
{
"message": "time=14:35:47.153 device_id=123 log_id=0000 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id=\"14SCZkrD013672-14SCZkrF013672\" msg=\"STARTTLS=client, cert-subject=/CN=EX-01, cert-issuer=/CN=EX-01, verifymsg=unable to get local issuer certificate\"",
"event": {
"action": "NONE",
"category": "smtp",
"kind": "event",
"message": "STARTTLS=client, cert-subject=/CN=EX-01, cert-issuer=/CN=EX-01, verifymsg=unable to get local issuer certificate",
"reason": "unable to get local issuer certificate"
},
"action": {
"outcome_reason": "STARTTLS=client, cert-subject=/CN=EX-01, cert-issuer=/CN=EX-01, verifymsg=unable to get local issuer certificate",
"properties": {
"device_id": "123",
"log_id": "0000",
"session_id": "14SCZkrD013672-14SCZkrF013672",
"start_tls": "client",
"user_identifier": "mail"
}
},
"log": {
"hostname": "hostname",
"level": "information"
},
"tls": {
"client": {
"issuer": "/CN=EX-01",
"subject": "/CN=EX-01"
}
}
}
{
"message": "time=16:10:33.138 device_id=123 log_id=123 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id=\"000\" msg=\"STARTTLS=server, cert-subject=/C=US/ST=California/L=Mountain View/O=Google LLC/CN=something.com, cert-issuer=issuer, verifymsg=unable to get local issuer certificate\"",
"event": {
"action": "NONE",
"category": "smtp",
"kind": "event",
"message": "STARTTLS=server, cert-subject=/C=US/ST=California/L=Mountain View/O=Google LLC/CN=something.com, cert-issuer=issuer, verifymsg=unable to get local issuer certificate",
"reason": "unable to get local issuer certificate"
},
"action": {
"outcome_reason": "STARTTLS=server, cert-subject=/C=US/ST=California/L=Mountain View/O=Google LLC/CN=something.com, cert-issuer=issuer, verifymsg=unable to get local issuer certificate",
"properties": {
"device_id": "123",
"log_id": "123",
"session_id": "000",
"start_tls": "server",
"user_identifier": "mail"
}
},
"log": {
"hostname": "ABC",
"level": "information"
},
"tls": {
"server": {
"issuer": "issuer",
"subject": "/C=US/ST=California/L=Mountain View/O=Google LLC/CN=something.com"
}
}
}
{
"message": "time=14:25:48.564 device_id=123 log_id=0000 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id=\"0000\" msg=\"STARTTLS=server, cert-subject=/something.fr, cert-issuer=issuer name, verifymsg=self signed certificate in certificate chain\"",
"event": {
"action": "NONE",
"category": "smtp",
"kind": "event",
"message": "STARTTLS=server, cert-subject=/something.fr, cert-issuer=issuer name, verifymsg=self signed certificate in certificate chain",
"reason": "self signed certificate in certificate chain"
},
"action": {
"outcome_reason": "STARTTLS=server, cert-subject=/something.fr, cert-issuer=issuer name, verifymsg=self signed certificate in certificate chain",
"properties": {
"device_id": "123",
"log_id": "0000",
"session_id": "0000",
"start_tls": "server",
"user_identifier": "mail"
}
},
"log": {
"hostname": "hostname",
"level": "information"
},
"tls": {
"server": {
"issuer": "issuer name",
"subject": "/something.fr"
}
}
}
{
"message": "time=10:50:36.931 device_id=FEVM020000087260 log_id=0003008733 type=event subtype=smtp pri=information user=mail ui=mail action=NONE status=N/A session_id=\"1548fVq5008733-1548fVq5008733\" msg=\"to=postmaster, delay=00:00:50, mailer=local, pri=58900, dsn=5.1.1, stat=User unknown(Reason from remote:550 5.1.1 User unknown)\"",
"event": {
"action": "NONE",
"category": "smtp",
"kind": "event",
"message": "to=postmaster, delay=00:00:50, mailer=local, pri=58900, dsn=5.1.1, stat=User unknown(Reason from remote:550 5.1.1 User unknown)",
"reason": "User unknown(Reason from remote:550 5.1.1 User unknown)"
},
"action": {
"outcome_reason": "to=postmaster, delay=00:00:50, mailer=local, pri=58900, dsn=5.1.1, stat=User unknown(Reason from remote:550 5.1.1 User unknown)",
"properties": {
"delay": "00:00:50",
"device_id": "FEVM020000087260",
"dsn_version": "5.1.1",
"log_id": "0003008733",
"mailer": "local",
"priority_level_msg": "58900",
"session_id": "1548fVq5008733-1548fVq5008733",
"user_identifier": "mail"
}
},
"email": {
"to": {
"address": [
"postmaster"
]
}
},
"log": {
"hostname": "00000",
"level": "information"
},
"user": {
"email": "postmaster"
}
}
{
"message": "time=16:01:46.183 device_id=123 log_id=123 type=spam subtype=default pri=information session_id=\"00000\" client_name=\"mail.outlook.com\" client_ip=\"2.2.2.2\" dst_ip=\"1.1.1.1\" from=\"\" to=\"mail.fr\" subject=\"D\u00e9tail de votre quarantaine: [ 1 message(s) en quarantaine entre le jeu. 15 avr. 2021 14 h 00 +0200 et le jeu. 15 avr. 2021 16 h 00 +0200 ]\" msg=\"File name: icon_deleteall.png, scanned by Antivirus Scanner(clean)\"",
"event": {
"category": "default",
"kind": "spam",
"message": "File name: icon_deleteall.png, scanned by Antivirus Scanner(clean)"
},
"action": {
"outcome_reason": "File name: icon_deleteall.png, scanned by Antivirus Scanner(clean)",
"properties": {
"device_id": "123",
"event_status": "clean",
"log_id": "123",
"session_id": "00000"
}
},
"destination": {
"address": "1.1.1.1",
"ip": "1.1.1.1"
},
"email": {
"subject": "D\u00e9tail de votre quarantaine: [ 1 message(s) en quarantaine entre le jeu. 15 avr. 2021 14 h 00 +0200 et le jeu. 15 avr. 2021 16 h 00 +0200 ]",
"to": {
"address": [
"mail.fr"
]
}
},
"file": {
"name": "icon_deleteall.png",
"type": "file"
},
"log": {
"hostname": "hostname",
"level": "information"
},
"related": {
"ip": [
"1.1.1.1",
"2.2.2.2"
]
},
"source": {
"address": "mail.outlook.com",
"ip": "2.2.2.2"
}
}
{
"message": "time=15:08:03.466 device_id=device log_id=121416 type=spam subtype=default pri=information session_id=\"123456\" client_name=\"client\" client_ip=\"2.2.2.2\" dst_ip=\"1.1.1.1\" from=\"whatever.com\" to=\"something.com\" subject=\"d\u00e9finitivement aim\u00e9 cette id\u00e9e et a pris la d\u00e9cision de vous la montrer\" msg=\"FortiGuard-AntiSpam identified spam URL: http://something.something.photos/apmix\"",
"event": {
"category": "default",
"kind": "spam",
"message": "FortiGuard-AntiSpam identified spam URL: http://something.something.photos/apmix"
},
"action": {
"outcome_reason": "FortiGuard-AntiSpam identified spam URL: http://something.something.photos/apmix",
"properties": {
"device_id": "device",
"log_id": "121416",
"session_id": "123456"
}
},
"destination": {
"address": "1.1.1.1",
"ip": "1.1.1.1"
},
"email": {
"from": {
"address": [
"whatever.com"
]
},
"subject": "d\u00e9finitivement aim\u00e9 cette id\u00e9e et a pris la d\u00e9cision de vous la montrer",
"to": {
"address": [
"something.com"
]
}
},
"log": {
"hostname": "abc",
"level": "information"
},
"related": {
"ip": [
"1.1.1.1",
"2.2.2.2"
]
},
"source": {
"address": "client",
"ip": "2.2.2.2"
},
"url": {
"domain": "something.something.photos",
"full": "http://something.something.photos/apmix",
"path": "/apmix",
"port": 80,
"registered_domain": "something.photos",
"scheme": "http",
"subdomain": "something",
"top_level_domain": "photos"
}
}
{
"message": "time=10:00:08.543 device_id=abc log_id=0300025551 type=spam subtype=default pri=information session_id=\"123456\" client_name=\"something.live\" client_ip=\"2.2.2.2\" dst_ip=\"1.1.1.1\" from=\"nereply.live\" to=\"info@pms-becus.com\" subject=\"new order to UK\" msg=\"File name: file.ppt(checksum:122452), scanned by Antivirus Scanner(detected)\"",
"event": {
"category": "default",
"kind": "spam",
"message": "File name: file.ppt(checksum:122452), scanned by Antivirus Scanner(detected)"
},
"action": {
"outcome_reason": "File name: file.ppt(checksum:122452), scanned by Antivirus Scanner(detected)",
"properties": {
"device_id": "abc",
"event_status": "detected",
"log_id": "0300025551",
"session_id": "123456"
}
},
"destination": {
"address": "1.1.1.1",
"ip": "1.1.1.1"
},
"email": {
"from": {
"address": [
"nereply.live"
]
},
"subject": "new order to UK",
"to": {
"address": [
"info@pms-becus.com"
]
}
},
"file": {
"hash": {
"sha256": "122452"
},
"name": "file.ppt",
"type": "file"
},
"log": {
"hostname": "abc",
"level": "information"
},
"related": {
"hash": [
"122452"
],
"ip": [
"1.1.1.1",
"2.2.2.2"
]
},
"source": {
"address": "something.live",
"ip": "2.2.2.2"
}
}
{
"message": "time=09:59:32.943 device_id=FEVM020000087260 log_id=0300025171 type=spam subtype=default pri=information session_id=\"15N7xWCW025167-15N7xWCX025167\" client_name=\"mail@sth.com\" client_ip=\"2.2.2.2\" dst_ip=\"1.1.1.1\" from=\"target.fr\" to=\"source.com\" subject=\"Vos impressions de documents au meilleur prix !\" msg=\"FortiGuard-WebFilter identified URL: url.fr, category: Spam URLs, id: 86.\"",
"event": {
"category": "default",
"kind": "spam",
"message": "FortiGuard-WebFilter identified URL: url.fr, category: Spam URLs, id: 86."
},
"action": {
"outcome_reason": "FortiGuard-WebFilter identified URL: url.fr, category: Spam URLs, id: 86.",
"properties": {
"device_id": "FEVM020000087260",
"log_id": "0300025171",
"session_id": "15N7xWCW025167-15N7xWCX025167",
"spam_category": "Spam URLs",
"spam_id": 86
}
},
"destination": {
"address": "1.1.1.1",
"ip": "1.1.1.1"
},
"email": {
"from": {
"address": [
"target.fr"
]
},
"subject": "Vos impressions de documents au meilleur prix !",
"to": {
"address": [
"source.com"
]
}
},
"log": {
"hostname": "12345",
"level": "information"
},
"related": {
"ip": [
"1.1.1.1",
"2.2.2.2"
]
},
"source": {
"address": "mail@sth.com",
"ip": "2.2.2.2"
},
"url": {
"full": "url.fr",
"path": "url.fr"
}
}
{
"message": "time=14:16:45.427 device_id=123 log_id=0300017253 type=spam subtype=default pri=information session_id=\"15N7xWCW025167-15N7xWCX025167\" client_name=\"mail.example.org\" client_ip=\"1.2.3.4\" dst_ip=\"5.6.7.8\" from=\"johndoe@example.org\" to=\"jane.doe@example.org\" subject=\"Ring phone promotion\" msg=\"FortiGuard-WebFilter identified URL(category: Phishing, id: 61): https://www.example.org/emailing/promotion.html\"",
"event": {
"category": "default",
"kind": "spam",
"message": "FortiGuard-WebFilter identified URL(category: Phishing, id: 61): https://www.example.org/emailing/promotion.html"
},
"action": {
"outcome_reason": "FortiGuard-WebFilter identified URL(category: Phishing, id: 61): https://www.example.org/emailing/promotion.html",
"properties": {
"device_id": "123",
"log_id": "0300017253",
"session_id": "15N7xWCW025167-15N7xWCX025167"
}
},
"destination": {
"address": "5.6.7.8",
"ip": "5.6.7.8"
},
"email": {
"from": {
"address": [
"johndoe@example.org"
]
},
"subject": "Ring phone promotion",
"to": {
"address": [
"jane.doe@example.org"
]
}
},
"log": {
"hostname": "12345",
"level": "information"
},
"related": {
"ip": [
"1.2.3.4",
"5.6.7.8"
]
},
"source": {
"address": "mail.example.org",
"ip": "1.2.3.4"
},
"url": {
"domain": "www.example.org",
"full": "https://www.example.org/emailing/promotion.html",
"original": "https://www.example.org/emailing/promotion.html",
"path": "/emailing/promotion.html",
"port": 443,
"registered_domain": "example.org",
"scheme": "https",
"subdomain": "www",
"top_level_domain": "org"
}
}
{
"message": "time=11:37:27.544 device_id=ABC log_id=0200017947 type=statistics pri=information session_id=\"123\" client_name=\"Address.com\" client_ip=\"2.2.2.2\" client_cc=\"FR\" dst_ip=\"1.1.1.1\" from=\"something.fr\" hfrom=\"something.fr\" to=\"something.fr\" polid=\"0:1:1\" domain=\"host.com\" mailer=\"mta\" resolved=\"OK\" src_type=\"int\" direction=\"in\" virus=\"\" disposition=\"Accept\" classifier=\"Domain Safe\" message_length=\"112389\" subject=confidential subject",
"event": {
"kind": "statistics",
"outcome": "Accept"
},
"action": {
"outcome": "Accept",
"outcome_reason": "Domain Safe",
"properties": {
"device_id": "ABC",
"dns_resolution_attempt": "OK",
"host_sender": "something.fr",
"log_id": "0200017947",
"mailer": "mta",
"policy_id": "0:1:1",
"session_id": "123",
"source_country": "FR",
"src_type": "int"
}
},
"destination": {
"address": "1.1.1.1",
"ip": "1.1.1.1"
},
"email": {
"from": {
"address": [
"something.fr"
]
},
"to": {
"address": [
"something.fr"
]
}
},
"http": {
"request": {
"bytes": 112389
}
},
"log": {
"hostname": "B96f1GJTxDUKbh2l",
"level": "information"
},
"network": {
"direction": "in"
},
"related": {
"hosts": [
"host.com"
],
"ip": [
"1.1.1.1",
"2.2.2.2"
]
},
"source": {
"address": "Address.com",
"domain": "host.com",
"ip": "2.2.2.2",
"size_in_char": 8
}
}
{
"message": "time=16:17:10.683 device_id=ABC log_id=1234271 type=virus subtype=fortisandbox pri=information from=\"\" to=\"\" client_name=\"\" client_ip=\"\" session_id=\"123456789\" msg=\"File file.pdf (checksum: 1234271) has been scanned by FortiSandbox. Scan result: rating=CLEAN\"",
"event": {
"category": "fortisandbox",
"kind": "virus",
"message": "File file.pdf (checksum: 1234271) has been scanned by FortiSandbox. Scan result: rating=CLEAN"
},
"action": {
"outcome_reason": "File file.pdf (checksum: 1234271) has been scanned by FortiSandbox. Scan result: rating=CLEAN",
"properties": {
"device_id": "ABC",
"event_status": "CLEAN",
"log_id": "1234271",
"session_id": "123456789"
}
},
"file": {
"hash": {
"sha256": "1234271"
},
"name": "file.pdf",
"type": "file"
},
"log": {
"hostname": "hostname",
"level": "information"
},
"related": {
"hash": [
"1234271"
]
}
}
{
"message": "time=14:18:20.030 device_id=123 log_id=0103021373 type=virus subtype=fortisandbox pri=information scope=o365 from=\"\" to=\"\" client_name=\"\" client_ip=\"\" session_id=\"15N7xWCW025167-15N7xWCX025167\" msg=\"URL https://example.org/path/image.jpg has been scanned by FortiSandbox. Scan result: rating=CLEAN\"",
"event": {
"category": "fortisandbox",
"kind": "virus",
"message": "URL https://example.org/path/image.jpg has been scanned by FortiSandbox. Scan result: rating=CLEAN"
},
"action": {
"outcome_reason": "URL https://example.org/path/image.jpg has been scanned by FortiSandbox. Scan result: rating=CLEAN",
"properties": {
"device_id": "123",
"log_id": "0103021373",
"session_id": "15N7xWCW025167-15N7xWCX025167"
}
},
"log": {
"hostname": "hostname",
"level": "information"
},
"url": {
"domain": "example.org",
"full": "https://example.org/path/image.jpg",
"original": "https://example.org/path/image.jpg",
"path": "/path/image.jpg",
"port": 443,
"registered_domain": "example.org",
"scheme": "https",
"top_level_domain": "org"
}
}
{
"message": "time=14:18:14.805 device_id=123 log_id=0103001910 type=virus subtype=fortisandbox pri=information from=\"\" to=\"\" client_name=\"\" client_ip=\"\" session_id=\"15N7xWCW025167-15N7xWCX025167\" msg=\"URL https://example.org/path/image.jpg has been scanned by FortiSandbox. Scan result: rating=CLEAN\"",
"event": {
"category": "fortisandbox",
"kind": "virus",
"message": "URL https://example.org/path/image.jpg has been scanned by FortiSandbox. Scan result: rating=CLEAN"
},
"action": {
"outcome_reason": "URL https://example.org/path/image.jpg has been scanned by FortiSandbox. Scan result: rating=CLEAN",
"properties": {
"device_id": "123",
"log_id": "0103001910",
"session_id": "15N7xWCW025167-15N7xWCX025167"
}
},
"log": {
"level": "information"
},
"url": {
"domain": "example.org",
"full": "https://example.org/path/image.jpg",
"original": "https://example.org/path/image.jpg",
"path": "/path/image.jpg",
"port": 443,
"registered_domain": "example.org",
"scheme": "https",
"top_level_domain": "org"
}
}
Extracted Fields
The following table lists the fields that are extracted, normalized under the ECS format, analyzed and indexed by the parser. It should be noted that infered fields are not listed.
| Name | Type | Description |
|---|---|---|
action.properties.bits_sent_ratio |
keyword |
|
action.properties.class |
keyword |
|
action.properties.daemon |
keyword |
|
action.properties.delay |
keyword |
|
action.properties.device_id |
keyword |
|
action.properties.dns_resolution_attempt |
keyword |
|
action.properties.dsn_version |
keyword |
|
action.properties.event_status |
keyword |
|
action.properties.host_sender |
keyword |
|
action.properties.hostname_info |
keyword |
|
action.properties.log_id |
keyword |
|
action.properties.mailer |
keyword |
|
action.properties.message_id |
keyword |
|
action.properties.nrcpts |
keyword |
|
action.properties.policy_id |
keyword |
|
action.properties.priority_level_msg |
keyword |
|
action.properties.relay |
keyword |
|
action.properties.session_id |
keyword |
|
action.properties.source_country |
keyword |
|
action.properties.spam_category |
keyword |
|
action.properties.spam_id |
number |
|
action.properties.src_type |
keyword |
|
action.properties.start_tls |
keyword |
|
action.properties.stat |
keyword |
|
action.properties.user_identifier |
keyword |
|
action.properties.verify |
keyword |
|
action.properties.virus |
keyword |
|
action.properties.xdelay |
keyword |
|
destination.address |
keyword |
Destination network address. |
destination.domain |
keyword |
The domain name of the destination. |
destination.ip |
ip |
IP address of the destination. |
destination.size_in_char |
number |
|
email.from.address |
array |
|
email.subject |
keyword |
The subject of the email message. |
email.to.address |
array |
|
event.action |
keyword |
The action captured by the event. |
event.category |
keyword |
Event category. The second categorization field in the hierarchy. |
event.kind |
keyword |
The kind of the event. The highest categorization field in the hierarchy. |
event.reason |
keyword |
Reason why this event happened, according to the source |
file.hash.sha256 |
keyword |
SHA256 hash. |
file.name |
keyword |
Name of the file including the extension, without the directory. |
file.size |
long |
File size in bytes. |
file.type |
keyword |
File type (file, dir, or symlink). |
http.request.bytes |
long |
Total size in bytes of the request (body and headers). |
log.level |
keyword |
Log level of the log event. |
network.direction |
keyword |
Direction of the network traffic. |
network.protocol |
keyword |
Application protocol name. |
source.address |
keyword |
Source network address. |
source.domain |
keyword |
The domain name of the source. |
source.ip |
ip |
IP address of the source. |
source.size_in_char |
number |
|
tls.cipher |
keyword |
String indicating the cipher used during the current connection. |
tls.client.issuer |
keyword |
Distinguished name of subject of the issuer of the x.509 certificate presented by the client. |
tls.client.subject |
keyword |
Distinguished name of subject of the x.509 certificate presented by the client. |
tls.server.issuer |
keyword |
Subject of the issuer of the x.509 certificate presented by the server. |
tls.server.subject |
keyword |
Subject of the x.509 certificate presented by the server. |
url.full |
wildcard |
Full unparsed URL. |
url.original |
wildcard |
Unmodified original url as seen in the event source. |
user.email |
keyword |
User email address. |
user.name |
keyword |
Short name or login of the user. |
For more information on the Intake Format, please find the code of the Parser, Smart Descriptions, and Supported Events here.