Bitdefender GravityZone
Overview
Bitdefender GravityZone is an enterprise-level cybersecurity solution offering advanced threat prevention, detection, and response for endpoints, networks, and cloud environments. It features centralized management for streamlined security oversight.
- Vendor: Bitdefender
- Supported environment: Cloud
- Version compatibility: 6.55, 6.56 (Latest version as of now)
- Detection based on: Telemetry / Alert
- Supported application or feature:
- Antiphishing
- Application Control
- Application Inventory
- Antimalware
- Advanced Threat Control
- Data Protection
- Exchange Malware Detected
- Invalid Exchange user credentials
- Firewall
- Hyper Detect
- Sandbox Analyzer Detection
- Antiexploit
- Network Attack Defense
- User Control/Content Control
- Storage Antimalware Event
- Login from new device
- Authentication audit
- SMTP Connection
- Internet Connection
- Malware Outbreak
Configure
This setup guide will show you how to forward your Bitdefender GravityZone events to Sekoia.io.
Steps to follow
Create a BitDefender GravityZone API key
- Log in the BitDefender GravityZone console
- On the top-right bar, open your personal panel and click
My Account
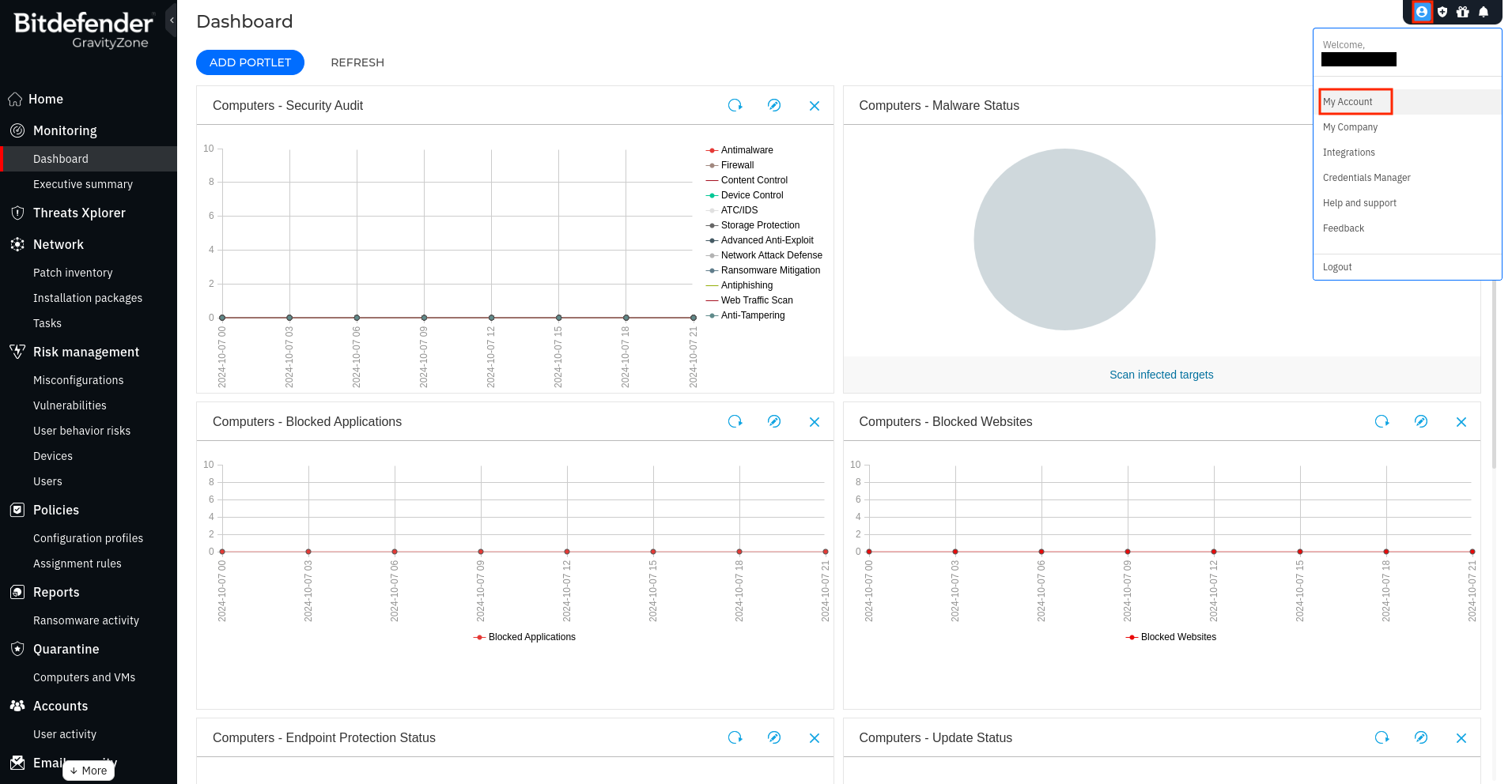
- Scroll down to the
API keyssection and click+ Add
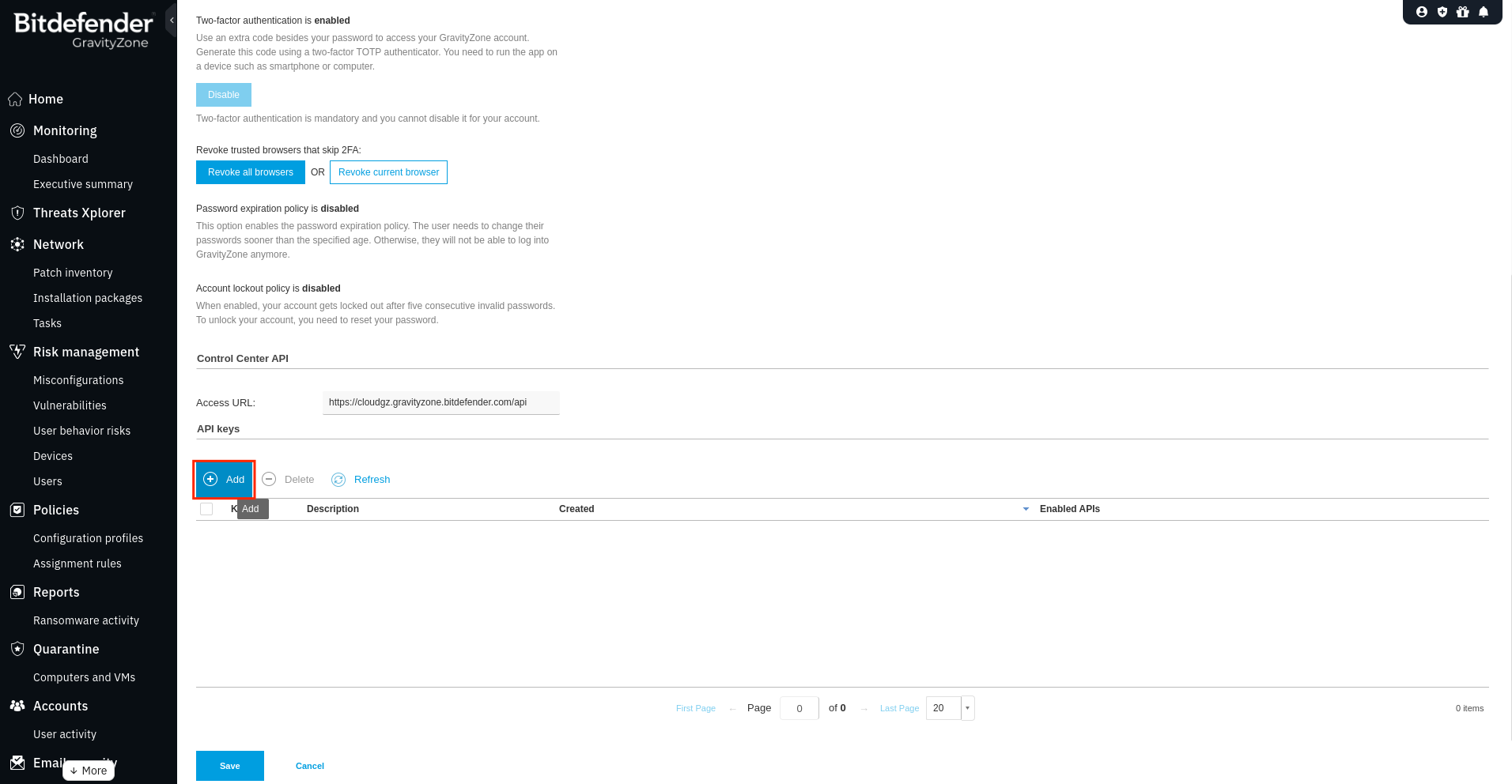
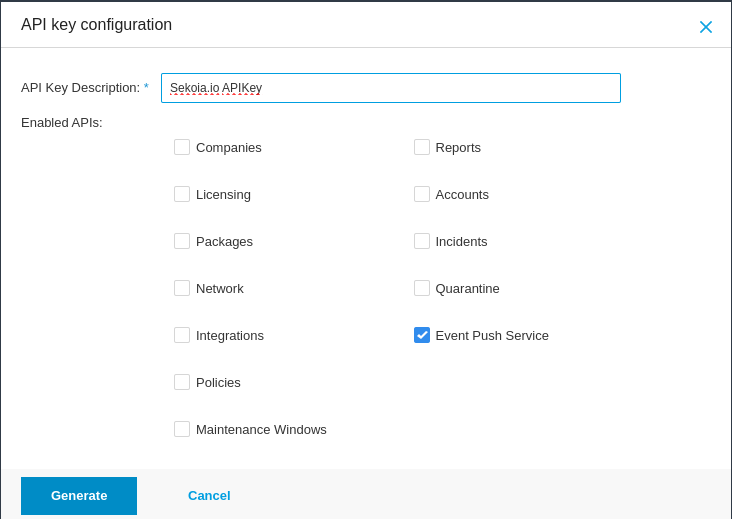
- Type a name for the API Key, select the
Event Push Servicecheckbox and clickGenerate
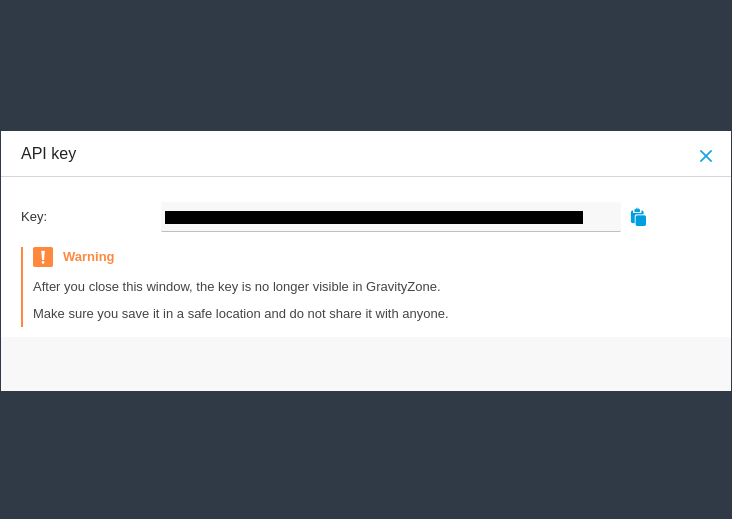
- Save the API Key
Create an intake
Go to the intake page and create a new intake from the format Bitdefender GravityZone. Copy the intake key.
Set the push events settings
Bitdefender GravityZone have an ability to setup push events settings using http request.
Two ways are suggested in order to set up the forwarding of your events to Sekoia.io.
If you are not a shell expert, we recommend to use the "python script" way as it is easier to set up.
So you can setup it in two ways:
- Open terminal
- Create virtual env and install requests library:
$ python3 -m venv /tmp/venv $ /tmp/venv/bin/pip install requests - Export your API Key and Intake key to environment variables:
$ export BITDEFENDER_APIKEY="your_api_key" $ export SEKOIAIO_INTAKE_KEY="your_intake_key" - Create python script with the following content:
from posixpath import join as urljoin import base64 import sys import argparse import requests BITDEFENDER_PUSH_URL = "https://cloudgz.gravityzone.bitdefender.com/api/v1.0/jsonrpc/push" def activate_forwarding(apikey: str, intake_key: str, base_url: str): # Convert the API key to base64 for the Basic Authorization header key = base64.b64encode(b':'+intake_key.encode('utf-8')).decode('utf-8') # compute the endpoint URL endpoint_url = urljoin(base_url.rstrip("/"), "jsons?path=%24.events&status_code=200") # Prepare the payload payload = { "id": "be630db8-24c2-481c-b150-a79807dd6f7d", "jsonrpc": "2.0", "method": "setPushEventSettings", "params": { "status": 1, "serviceType": "cef", "serviceSettings": { "url": endpoint_url, "requireValidSslCertificate": True, "authorization": f"Basic {key}" }, "subscribeToEventTypes": { "adcloud": True, "antiexploit": True, "aph": True, "av": True, "avc": True, "dp": True, "endpoint-moved-in": True, "endpoint-moved-out": True, "exchange-malware": True, "exchange-user-credentials": True, "fw": True, "hd": True, "hwid-change": True, "install": False, "modules": False, "network-monitor": True, "network-sandboxing": True, "new-incident": True, "ransomware-mitigation": True, "registration": True, "security-container-update-available": False, "supa-update-status": False, "sva": False, "sva-load": False, "task-status": False, "troubleshooting-activity": True, "uc": True, "uninstall": False } } } # Create the push setting against the Bitdefender API response = requests.post( url=BITDEFENDER_PUSH_URL, auth=requests.auth.HTTPBasicAuth(apikey,""), json=payload, ) # Check the result of the creation if response.status_code == 200 and response.json().get("result") == True: setting_id = response.json().get("id") print(f"The push setting was successfully created. ID: {setting_id}") else: print(f"The creation of the forwarding failed. Reason: {response.content}") if __name__ == '__main__': parser = argparse.ArgumentParser(prog=sys.argv[0], description='activate the forwarding of events to Sekoia.io') parser.add_argument('apikey') parser.add_argument('intake_key') parser.add_argument('--base-url', default='https://intake.sekoia.io', help='The base URL to the Sekoia.io region (see https://docs.sekoia.io/getting_started/regions/ for more information; default to FRA1)') args = parser.parse_args() activate_forwarding(args.apikey, args.intake_key, args.base_url) - Run the script with the following command:
$ /tmp/venv/bin/python3 bitdefender_activate_forwarding.py "${BITDEFENDER_APIKEY}" "${SEKOIAIO_INTAKE_KEY}"
Note
For other regions, you have to specify the --base-url parameter when running the script. For example, for the US region, you can run:
$ /tmp/venv/bin/python3 bitdefender_activate_forwarding.py "${BITDEFENDER_APIKEY}" "${SEKOIAIO_INTAKE_KEY}" --base-url "https://app.usa1.sekoia.io/api/v1/intake-http"
- Open your terminal
- Export your API Key and Intake key to environment variables:
$ export BITDEFENDER_APIKEY="your_api_key" $ export SEKOIAIO_INTAKE_KEY="your_intake_key" $ export SEKOIA_BASE_URL="https://intake.sekoia.io" # adapt according to your region, see https://docs.sekoia.io/getting_started/regions/ - Convert the Bitdefender APIKey into base64:
$ echo -n '${BITDEFENDER_APIKEY}:' | base64 - Convert the Intake Key into base64:
$ echo -n ':${SEKOIA_INTAKE_KEY}' | base64 - Create
payload.jsonwith following content ( replacebase64_intake_keywith the value from the previous steps):{ "id": "be630db8-24c2-481c-b150-a79807dd6f7d", "jsonrpc": "2.0", "method": "setPushEventSettings", "params": { "status": 1, "serviceType": "cef", "serviceSettings": { "url": "${SEKOIA_BASE_URL}/jsons?path=%24.events&status_code=200", "authorization": "Basic <base64_intake_key>", "requireValidSslCertificate": false }, "subscribeToEventTypes": { "adcloud": false, "antiexploit": true, "aph": true, "av": true, "avc": true, "dp": true, "endpoint-moved-in": true, "endpoint-moved-out": true, "exchange-malware": true, "exchange-user-credentials": true, "fw": true, "hd": true, "hwid-change": true, "install": false, "modules": false, "network-monitor": true, "network-sandboxing": true, "new-incident": true, "ransomware-mitigation": true, "registration": true, "security-container-update-available": false, "supa-update-status": false, "sva": false, "sva-load": false, "task-status": false, "troubleshooting-activity": true, "uc": true, "uninstall": false } } } - Send the payload to the Bitdefender API (replace
base64_api_keywith the value from the previous steps):$ curl -k -X POST \ https://cloudgz.gravityzone.bitdefender.com/api/v1.0/jsonrpc/push \ -H "Authorization: Basic <base64_api_key>" \ -H 'cache-control: no-cache' \ -H 'content-type: application/json' \ -d @payload.json
Warning
The setPushEventSettings can take up to 2 hours to be effective, or may require to repeat the operation twice
Enjoy your events on the Events page
Raw Events Samples
In this section, you will find examples of raw logs as generated natively by the source. These examples are provided to help integrators understand the data format before ingestion into Sekoia.io. It is crucial for setting up the correct parsing stages and ensuring that all relevant information is captured.
CEF:0|Bitdefender|GravityZone|6.50.0-27|10|AntiMalware|9|BitdefenderGZModule=av BitdefenderGZCompanyId=8646b1be9aae4aefb3b23147 dvchost=Desktop-JDO BitdefenderGZComputerFQDN=desktop-jdo.example.org dvc=10.0.0.4 deviceExternalId=devId123 BitdefenderGZMalwareType=file BitdefenderGZMalwareName=EICAR-Test-File (not a virus) act=blocked filePath=C:\\\\Users\\\\jdoe\\\\Downloads\\\\b93ef2d1-160c-4bd9-9cbb-cb59ca59939e.tmp BitdefenderGZDetectionTime=2024-05-15T09:06:52.000Z BitdefenderGZSignaturesNumber=7.96749 BitdefenderGZScanEngineType=2 BitdefenderGZCleanedMalwareCnt=0 BitdefenderGZBlockedMalwareCnt=1 BitdefenderGZDeletedMalwareCnt=0 BitdefenderGZQuarantinedMalwareCnt=0 BitdefenderGZIgnoredMalwareCnt=0 BitdefenderGZPresentMalwareCnt=0 suser=jdoe suid=S-1-5-21-1111111111-222222222-3333333333-500
CEF:0|Bitdefender|GravityZone|6.50.0-27|10|AntiMalware|9|BitdefenderGZModule=av BitdefenderGZCompanyId=8646b1be9aae4aefb3b23147 dvchost=Desktop-JDO BitdefenderGZComputerFQDN=desktop-jdo.example.org dvc=10.0.0.4 deviceExternalId=devId321 BitdefenderGZMalwareType=file BitdefenderGZMalwareName=EICAR-Test-File (not a virus) BitdefenderGZMalwareHash=275a021bbfb6489e54d471899f7db9d1663fc695ec2fe2a2c4538aabf651fd0f act=blocked filePath=C:\\\\Users\\\\jdoe\\\\Downloads\\\\b93ef2d1-160c-4bd9-9cbb-cb59ca59939e.tmp BitdefenderGZDetectionTime=2024-05-15T09:06:53.000Z BitdefenderGZSignaturesNumber=7.96749 BitdefenderGZScanEngineType=2 BitdefenderGZCleanedMalwareCnt=0 BitdefenderGZBlockedMalwareCnt=1 BitdefenderGZDeletedMalwareCnt=0 BitdefenderGZQuarantinedMalwareCnt=0 BitdefenderGZIgnoredMalwareCnt=0 BitdefenderGZPresentMalwareCnt=0 suser=jdoe suid=S-1-5-21-1111111111-222222222-3333333333-500
CEF:0|Bitdefender|GZ|6.50.0-27|6|Login from new device|3|start=Jun 11 2024 12:34:56+01:00 BitdefenderGZCompanyName=example suser=jdoe BitdefenderGZLoginOS=Win11 BitdefenderGZAuthenticationBrowserName=Chrome BitdefenderGZAuthenticationBrowserVersion=129.0.6668.70 dvchost=1.2.3.4
CEF:0|Bitdefender|GravityZone|6.65.0-1|170000|New Incident|3|BitdefenderGZModule=new-incident dvchost=EXAMPLE BitdefenderGZComputerFQDN=example.com dvc=5.6.7.8, 1.2.3.4 deviceExternalId=DEVICE BitdefenderGZIncidentId=INCIDENT BitdefenderGZSeverityScore=43 BitdefenderGZAttackEntry=1234567890 BitdefenderGZMainAction=blocked BitdefenderGZDetectionName=Cloud Virus request=https://example.com/ spt=443 src=192.168.108.208 sproc=c:\\program files (x86)\\example\\app.exe BitdefenderGZAttackTypes=["Other"] BitdefenderGZAttCkId=["T1047","T1082","T1055","T1518","T1036","T1059","T1140","T1203","T1218","T1548","T1560","T1569","T1134","T1071","T1573","T1095","T1571","T1030","T1053","T1543","T1559"] start=2025-09-02T04:36:34.013Z BitdefenderGZCompanyId=COMPANY BitdefenderGZEndpointId=ENDPOINT
"CEF:0|Bitdefender|GravityZone|6.61.0-1|10|AntiMalware|9|BitdefenderGZModule=av BitdefenderGZCompanyId=00000000000000000000orgId dvchost=test-host-name BitdefenderGZComputerFQDN=test-host-name dvc=1.2.3.4 deviceExternalId=devId123 BitdefenderGZMalwareType=file BitdefenderGZMalwareName=Test BitdefenderGZMalwareHash=8b3f191819931d1f2cef7289239b5f77c00b079847b9c2636e56854d1e5eff71 act=deleted filePath=C:\\\\eicar0000001.txt BitdefenderGZDetectionTime=2017-09-08T12:01:36.000Z"
CEF:0|Bitdefender|GravityZone|6.67.0-1|170000|New Incident|3|BitdefenderGZModule=new-incident dvchost=HOST-01 BitdefenderGZComputerFQDN=host01.example.local dvc=1.2.3.4, 1.2.3.4 deviceExternalId=devId-000000000000000000000000 BitdefenderGZIncidentId=000000000000000000000000 BitdefenderGZSeverityScore=39 BitdefenderGZAttackEntry=000000000 BitdefenderGZMainAction=no action BitdefenderGZDetectionName=SuspiciousPcaluaSpawned fileHash=00000000000000000000000000000000 BitdefenderGZFileHashSha256=0000000000000000000000000000000000000000000000000000000000000000 spid=1111 sproc=c:\\windows\\system32\\system.exe BitdefenderGZParentPid=2222 BitdefenderGZParentPath=c:\\windows\\system32\\system.exe BitdefenderGZAttackTypes=["Malware"] BitdefenderGZAttCkId=["T1053","T1059","T1202","T1218","T1548","T1569","T1083","T1106","T1497","T1112","T1491","T1027","T1203","T1070","T1565","T1080","T1547","T1113","T1134","T1543","T1574","T1197","T1055"] BitdefenderGZProcessCommandLine="C:\\Windows\\System32\\system.exe" -a "C:\\Program Files\\Example\\App\\App.exe" -d "C:\\Program Files\\Example\\App" start=2025-10-15T05:48:34.731Z suser=john.doe@test BitdefenderGZCompanyId=000000000000000000000000 BitdefenderGZEndpointId=000000000000000000000000 suid=S-1-5-21-0000000000-0000000000-0000000000-00000
CEF:0|Bitdefender|GravityZone|6.40.1-1|1000|Web Control|9|BitdefenderGZModule=uc dvchost=example BitdefenderGZComputerFQDN=example.test.local dvc=1.2.3.4 deviceExternalId=1234567890abcdef12345678 BitdefenderGZApplicationControlType=http request=external-content.domain.com/ip3/www.test_request.com BitdefenderGZApplicationControlBlockType=http_categories BitdefenderGZDataCategories=Ads act=uc_site_blocked end=Dec 16 2024 12:34:33 Z cnt=1 suser=john.doe@test.local suid=S-1-5-21-1111111111-222222222-3333333333-500
CEF:0|Bitdefender|GravityZone|6.62.0-2|1000|Web Control|9|BitdefenderGZModule=uc BitdefenderGZCompanyId=123123123123123 dvchost=test BitdefenderGZComputerFQDN=test.test.local dvc=1.2.3.4 deviceExternalId=123123123123123213 BitdefenderGZApplicationControlType=http request=https://test.com BitdefenderGZApplicationControlBlockType=http_antimalware act=uc_site_blocked end=2025-06-02T20:43:28.000Z cnt=1 suser=test.user@test suid=S-1-5-21-1111111111-222222222-3333333333-500
CEF:0|Bitdefender|GravityZone|6.62.0-2|1000|Web Control|9|BitdefenderGZModule=uc BitdefenderGZCompanyId=12312312313123123 dvchost=TEST-TEST BitdefenderGZComputerFQDN=test.test.local dvc=1.2.3.4 deviceExternalId=123123123213 BitdefenderGZApplicationControlType=http request=https://test.org BitdefenderGZApplicationControlBlockType=http_antimalware act=uc_site_blocked end=2025-06-01T09:06:08.000Z cnt=2 suser=test.user@test suid=S-1-5-21-1111111111-222222222-3333333333-500
CEF:0|Bitdefender|GravityZone|6.63.0-1|1000|Web Control|9|BitdefenderGZModule=uc BitdefenderGZCompanyId=1234567890abcdef12345678 dvchost=example BitdefenderGZComputerFQDN=example.test.local dvc=1.2.3.4 deviceExternalId=1234567890abcdef12345678 BitdefenderGZApplicationControlType=http request=https://external-content.domain.com BitdefenderGZApplicationControlBlockType=http_antimalware act=uc_site_blocked end=2025-06-20T12:34:56.000Z cnt=1 suser=john.doe@test.local suid=S-1-5-21-1111111111-2222222222-3333333333-4444
Detection section
The following section provides information for those who wish to learn more about the detection capabilities enabled by collecting this intake. It includes details about the built-in rule catalog, event categories, and ECS fields extracted from raw events. This is essential for users aiming to create custom detection rules, perform hunting activities, or pivot in the events page.
Related Built-in Rules
The following Sekoia.io built-in rules match the intake Bitdefender GravityZone. This documentation is updated automatically and is based solely on the fields used by the intake which are checked against our rules. This means that some rules will be listed but might not be relevant with the intake.
SEKOIA.IO x Bitdefender GravityZone on ATT&CK Navigator
Bazar Loader DGA (Domain Generation Algorithm)
Detects Bazar Loader domains based on the Bazar Loader DGA
- Effort: elementary
Bitdefender GravityZone Endpoint Detection
Bitdefender GravityZone detected a malicious activity on an endpoint
- Effort: master
Burp Suite Tool Detected
Burp Suite is a cybersecurity tool. When used as a proxy service, its purpose is to intercept packets and modify them to send them to the server. Burp Collaborator is a network service that Burp Suite uses to help discover many kinds of vulnerabilities (vulnerabilities scanner).
- Effort: intermediate
CVE-2020-0688 Microsoft Exchange Server Exploit
Detects the exploitation of CVE-2020-0688. The POC exploit a .NET serialization vulnerability in the Exchange Control Panel (ECP) web page. The vulnerability is due to Microsoft Exchange Server not randomizing the keys on a per-installation basis resulting in them using the same validationKey and decryptionKey values. With knowledge of these, values an attacker can craft a special viewstate to use an OS command to be executed by NT_AUTHORITY\SYSTEM using .NET deserialization. To exploit this vulnerability, an attacker needs to leverage the credentials of an account it had already compromised to authenticate to OWA.
- Effort: elementary
CVE-2020-17530 Apache Struts RCE
Detects the exploitation of the Apache Struts RCE vulnerability (CVE-2020-17530).
- Effort: intermediate
CVE-2021-20021 SonicWall Unauthenticated Administrator Access
Detects the exploitation of SonicWall Unauthenticated Admin Access.
- Effort: advanced
CVE-2021-20023 SonicWall Arbitrary File Read
Detects Arbitrary File Read, which can be used with other vulnerabilities as a mean to obtain outputs generated by attackers, or sensitive data.
- Effort: advanced
CVE-2021-22893 Pulse Connect Secure RCE Vulnerability
Detects potential exploitation of the authentication by-pass vulnerability that can allow an unauthenticated user to perform remote arbitrary file execution on the Pulse Connect Secure gateway. It is highly recommended to apply the Pulse Secure mitigations and seach for indicators of compromise on affected servers if you are in doubt over the integrity of your Pulse Connect Secure product.
- Effort: intermediate
Cryptomining
Detection of domain names potentially related to cryptomining activities.
- Effort: master
Detect requests to Konni C2 servers
This rule detects requests to Konni C2 servers. These patterns come from an analysis done in 2022, September.
- Effort: elementary
Discord Suspicious Download
Discord is a messaging application. It allows users to create their own communities to share messages and attachments. Those attachments have little to no overview and can be downloaded by almost anyone, which has been abused by attackers to host malicious payloads.
- Effort: advanced
Download Files From Suspicious TLDs
Detects download of certain file types from hosts in suspicious TLDs
- Effort: master
Dynamic DNS Contacted
Detect communication with dynamic dns domain. This kind of domain is often used by attackers. This rule can trigger false positive in non-controlled environment because dynamic dns is not always malicious.
- Effort: master
EvilProxy Phishing Domain
Detects subdomains potentially generated by the EvilProxy adversary-in-the-middle phishing platform. Inspect the other subdomains of the domain to identify the landing page, and determine if the user submitted credentials. This rule has a small percentage of false positives on legitimate domains.
- Effort: intermediate
Exfiltration Domain
Detects traffic toward a domain flagged as a possible exfiltration vector.
- Effort: master
Koadic MSHTML Command
Detects Koadic payload using MSHTML module
- Effort: intermediate
Possible Malicious File Double Extension
Detects request to potential malicious file with double extension
- Effort: elementary
Potential Azure AD Phishing Page (Adversary-in-the-Middle)
Detects an HTTP request to an URL typical of the Azure AD authentication flow, but towards a domain that is not one the legitimate Microsoft domains used for Azure AD authentication.
- Effort: intermediate
Process Trace Alteration
PTrace syscall provides a means by which one process ("tracer") may observe and control the execution of another process ("tracee") and examine and change the tracee's memory and registers. Attacker might want to abuse ptrace functionnality to analyse memory process. It requires to be admin or set ptrace_scope to 0 to allow all user to trace any process.
- Effort: advanced
ProxyShell Microsoft Exchange Suspicious Paths
Detects suspicious calls to Microsoft Exchange resources, in locations related to webshells observed in campaigns using this vulnerability.
- Effort: elementary
Raccoon Stealer 2.0 Legitimate Third-Party DLL Download URL
Detects Raccoon Stealer 2.0 malware downloading legitimate third-party DLLs from its C2 server. These legitimate DLLs are used by the information stealer to collect data on the compromised hosts.
- Effort: elementary
Remote Access Tool Domain
Detects traffic toward a domain flagged as a Remote Administration Tool (RAT).
- Effort: master
Remote Monitoring and Management Software - AnyDesk
Detect artifacts related to the installation or execution of the Remote Monitoring and Management tool AnyDesk.
- Effort: master
Remote Monitoring and Management Software - Atera
Detect artifacts related to the installation or execution of the Remote Monitoring and Management tool Atera.
- Effort: master
SEKOIA.IO Intelligence Feed
Detect threats based on indicators of compromise (IOCs) collected by SEKOIA's Threat and Detection Research team.
- Effort: elementary
Sekoia.io EICAR Detection
Detects observables in Sekoia.io CTI tagged as EICAR, which are fake samples meant to test detection.
- Effort: master
SolarWinds Wrong Child Process
Detects SolarWinds process starting an unusual child process. Process solarwinds.businesslayerhost.exe and solarwinds.businesslayerhostx64.exe created an unexepected child process which doesn't correspond to the legitimate ones.
- Effort: intermediate
Suspicious Download Links From Legitimate Services
Detects users clicking on Google docs links to download suspicious files. This technique was used a lot by Bazar Loader in the past.
- Effort: intermediate
Suspicious PROCEXP152.sys File Created In Tmp
Detects the creation of the PROCEXP152.sys file in the application-data local temporary folder. This driver is used by Sysinternals Process Explorer but also by KDU (https://github.com/hfiref0x/KDU) or Ghost-In-The-Logs (https://github.com/bats3c/Ghost-In-The-Logs), which uses KDU. Note - Clever attackers may easily bypass this detection by just renaming the driver filename. Therefore just Medium-level and don't rely on it.
- Effort: advanced
Suspicious TOR Gateway
Detects suspicious TOR gateways. Gateways are often used by the victim to pay and decrypt the encrypted files without installing TOR. Tor intercepts the network traffic from one or more apps on user’s computer, usually the user web browser, and shuffles it through a number of randomly-chosen computers before passing it on to its destination. This disguises user location, and makes it harder for servers to pick him/her out on repeat visits, or to tie together separate visits to different sites, this making tracking and surveillance more difficult. Before a network packet starts its journey, user’s computer chooses a random list of relays and repeatedly encrypts the data in multiple layers, like an onion. Each relay knows only enough to strip off the outermost layer of encryption, before passing what’s left on to the next relay in the list.
- Effort: advanced
Suspicious URI Used In A Lazarus Campaign
Detects suspicious requests to a specific URI, usually on an .asp page. The website is often compromised.
- Effort: intermediate
TOR Usage Generic Rule
Detects TOR usage globally, whether the IP is a destination or source. TOR is short for The Onion Router, and it gets its name from how it works. TOR intercepts the network traffic from one or more apps on user’s computer, usually the user web browser, and shuffles it through a number of randomly-chosen computers before passing it on to its destination. This disguises user location, and makes it harder for servers to pick him/her out on repeat visits, or to tie together separate visits to different sites, this making tracking and surveillance more difficult. Before a network packet starts its journey, user’s computer chooses a random list of relays and repeatedly encrypts the data in multiple layers, like an onion. Each relay knows only enough to strip off the outermost layer of encryption, before passing what’s left on to the next relay in the list.
- Effort: master
WAF Block Rule
Detects when one of WAF rule blocked an HTTP request. This rule often needs fine tuning according to the environment.
- Effort: master
WAF Correlation Block actions
Detection of multiple block actions (more than 30) triggered by the same source by WAF detection rules
- Effort: master
Event Categories
The following table lists the data source offered by this integration.
| Data Source | Description |
|---|---|
Authentication logs |
None |
Network device logs |
None |
File monitoring |
None |
In details, the following table denotes the type of events produced by this integration.
| Name | Values |
|---|---|
| Kind | alert |
| Category | `` |
| Type | denied, info, start |
Transformed Events Samples after Ingestion
This section demonstrates how the raw logs will be transformed by our parsers. It shows the extracted fields that will be available for use in the built-in detection rules and hunting activities in the events page. Understanding these transformations is essential for analysts to create effective detection mechanisms with custom detection rules and to leverage the full potential of the collected data.
{
"message": "CEF:0|Bitdefender|GravityZone|6.50.0-27|10|AntiMalware|9|BitdefenderGZModule=av BitdefenderGZCompanyId=8646b1be9aae4aefb3b23147 dvchost=Desktop-JDO BitdefenderGZComputerFQDN=desktop-jdo.example.org dvc=10.0.0.4 deviceExternalId=devId123 BitdefenderGZMalwareType=file BitdefenderGZMalwareName=EICAR-Test-File (not a virus) act=blocked filePath=C:\\\\\\\\Users\\\\\\\\jdoe\\\\\\\\Downloads\\\\\\\\b93ef2d1-160c-4bd9-9cbb-cb59ca59939e.tmp BitdefenderGZDetectionTime=2024-05-15T09:06:52.000Z BitdefenderGZSignaturesNumber=7.96749 BitdefenderGZScanEngineType=2 BitdefenderGZCleanedMalwareCnt=0 BitdefenderGZBlockedMalwareCnt=1 BitdefenderGZDeletedMalwareCnt=0 BitdefenderGZQuarantinedMalwareCnt=0 BitdefenderGZIgnoredMalwareCnt=0 BitdefenderGZPresentMalwareCnt=0 suser=jdoe suid=S-1-5-21-1111111111-222222222-3333333333-500",
"event": {
"action": "blocked",
"category": [
"malware"
],
"module": "av",
"severity": 9,
"type": [
"info"
]
},
"@timestamp": "2024-05-15T09:06:52Z",
"device": {
"id": "devId123"
},
"host": {
"ip": [
"10.0.0.4"
],
"name": "desktop-jdo.example.org"
},
"observer": {
"product": "GravityZone",
"vendor": "Bitdefender",
"version": "6.50.0-27"
},
"organization": {
"id": "8646b1be9aae4aefb3b23147"
},
"related": {
"ip": [
"10.0.0.4"
],
"user": [
"jdoe"
]
},
"source": {
"user": {
"id": "S-1-5-21-1111111111-222222222-3333333333-500",
"name": "jdoe"
}
},
"threat": {
"indicator": {
"file": {
"name": "b93ef2d1-160c-4bd9-9cbb-cb59ca59939e.tmp",
"path": "C:\\\\\\\\Users\\\\\\\\jdoe\\\\\\\\Downloads\\\\\\\\b93ef2d1-160c-4bd9-9cbb-cb59ca59939e.tmp"
},
"name": "EICAR-Test-File (not a virus)",
"type": "file"
}
}
}
{
"message": "CEF:0|Bitdefender|GravityZone|6.50.0-27|10|AntiMalware|9|BitdefenderGZModule=av BitdefenderGZCompanyId=8646b1be9aae4aefb3b23147 dvchost=Desktop-JDO BitdefenderGZComputerFQDN=desktop-jdo.example.org dvc=10.0.0.4 deviceExternalId=devId321 BitdefenderGZMalwareType=file BitdefenderGZMalwareName=EICAR-Test-File (not a virus) BitdefenderGZMalwareHash=275a021bbfb6489e54d471899f7db9d1663fc695ec2fe2a2c4538aabf651fd0f act=blocked filePath=C:\\\\\\\\Users\\\\\\\\jdoe\\\\\\\\Downloads\\\\\\\\b93ef2d1-160c-4bd9-9cbb-cb59ca59939e.tmp BitdefenderGZDetectionTime=2024-05-15T09:06:53.000Z BitdefenderGZSignaturesNumber=7.96749 BitdefenderGZScanEngineType=2 BitdefenderGZCleanedMalwareCnt=0 BitdefenderGZBlockedMalwareCnt=1 BitdefenderGZDeletedMalwareCnt=0 BitdefenderGZQuarantinedMalwareCnt=0 BitdefenderGZIgnoredMalwareCnt=0 BitdefenderGZPresentMalwareCnt=0 suser=jdoe suid=S-1-5-21-1111111111-222222222-3333333333-500",
"event": {
"action": "blocked",
"category": [
"malware"
],
"module": "av",
"severity": 9,
"type": [
"info"
]
},
"@timestamp": "2024-05-15T09:06:53Z",
"device": {
"id": "devId321"
},
"host": {
"ip": [
"10.0.0.4"
],
"name": "desktop-jdo.example.org"
},
"observer": {
"product": "GravityZone",
"vendor": "Bitdefender",
"version": "6.50.0-27"
},
"organization": {
"id": "8646b1be9aae4aefb3b23147"
},
"related": {
"ip": [
"10.0.0.4"
],
"user": [
"jdoe"
]
},
"source": {
"user": {
"id": "S-1-5-21-1111111111-222222222-3333333333-500",
"name": "jdoe"
}
},
"threat": {
"indicator": {
"file": {
"hash": {
"sha256": "275a021bbfb6489e54d471899f7db9d1663fc695ec2fe2a2c4538aabf651fd0f"
},
"name": "b93ef2d1-160c-4bd9-9cbb-cb59ca59939e.tmp",
"path": "C:\\\\\\\\Users\\\\\\\\jdoe\\\\\\\\Downloads\\\\\\\\b93ef2d1-160c-4bd9-9cbb-cb59ca59939e.tmp"
},
"name": "EICAR-Test-File (not a virus)",
"type": "file"
}
}
}
{
"message": "CEF:0|Bitdefender|GZ|6.50.0-27|6|Login from new device|3|start=Jun 11 2024 12:34:56+01:00 BitdefenderGZCompanyName=example suser=jdoe BitdefenderGZLoginOS=Win11 BitdefenderGZAuthenticationBrowserName=Chrome BitdefenderGZAuthenticationBrowserVersion=129.0.6668.70 dvchost=1.2.3.4",
"event": {
"category": [
"authentication"
],
"outcome": "success",
"severity": 3,
"start": "2024-06-11T11:34:56Z",
"type": [
"start"
]
},
"host": {
"name": "1.2.3.4"
},
"observer": {
"product": "GZ",
"vendor": "Bitdefender",
"version": "6.50.0-27"
},
"related": {
"user": [
"jdoe"
]
},
"source": {
"user": {
"name": "jdoe"
}
}
}
{
"message": "CEF:0|Bitdefender|GravityZone|6.65.0-1|170000|New Incident|3|BitdefenderGZModule=new-incident dvchost=EXAMPLE BitdefenderGZComputerFQDN=example.com dvc=5.6.7.8, 1.2.3.4 deviceExternalId=DEVICE BitdefenderGZIncidentId=INCIDENT BitdefenderGZSeverityScore=43 BitdefenderGZAttackEntry=1234567890 BitdefenderGZMainAction=blocked BitdefenderGZDetectionName=Cloud Virus request=https://example.com/ spt=443 src=192.168.108.208 sproc=c:\\\\program files (x86)\\\\example\\\\app.exe BitdefenderGZAttackTypes=[\"Other\"] BitdefenderGZAttCkId=[\"T1047\",\"T1082\",\"T1055\",\"T1518\",\"T1036\",\"T1059\",\"T1140\",\"T1203\",\"T1218\",\"T1548\",\"T1560\",\"T1569\",\"T1134\",\"T1071\",\"T1573\",\"T1095\",\"T1571\",\"T1030\",\"T1053\",\"T1543\",\"T1559\"] start=2025-09-02T04:36:34.013Z BitdefenderGZCompanyId=COMPANY BitdefenderGZEndpointId=ENDPOINT",
"event": {
"category": [
"process"
],
"kind": "alert",
"module": "new-incident",
"severity": 3,
"start": "2025-09-02T04:36:34.013000Z",
"type": [
"info"
]
},
"device": {
"id": "DEVICE"
},
"host": {
"id": "ENDPOINT",
"ip": [
"1.2.3.4",
"5.6.7.8"
],
"name": "example.com"
},
"observer": {
"product": "GravityZone",
"vendor": "Bitdefender",
"version": "6.65.0-1"
},
"organization": {
"id": "COMPANY"
},
"related": {
"ip": [
"1.2.3.4",
"5.6.7.8"
]
},
"url": {
"domain": "example.com",
"full": "https://example.com/",
"original": "https://example.com/",
"path": "/",
"port": 443,
"registered_domain": "example.com",
"scheme": "https",
"top_level_domain": "com"
}
}
{
"message": "\"CEF:0|Bitdefender|GravityZone|6.61.0-1|10|AntiMalware|9|BitdefenderGZModule=av BitdefenderGZCompanyId=00000000000000000000orgId dvchost=test-host-name BitdefenderGZComputerFQDN=test-host-name dvc=1.2.3.4 deviceExternalId=devId123 BitdefenderGZMalwareType=file BitdefenderGZMalwareName=Test BitdefenderGZMalwareHash=8b3f191819931d1f2cef7289239b5f77c00b079847b9c2636e56854d1e5eff71 act=deleted filePath=C:\\\\\\\\eicar0000001.txt BitdefenderGZDetectionTime=2017-09-08T12:01:36.000Z\"",
"event": {
"action": "deleted",
"category": [
"malware"
],
"module": "av",
"severity": 9,
"type": [
"info"
]
},
"@timestamp": "2017-09-08T12:01:36Z",
"device": {
"id": "devId123"
},
"host": {
"ip": [
"1.2.3.4"
],
"name": "test-host-name"
},
"observer": {
"product": "GravityZone",
"vendor": "Bitdefender",
"version": "6.61.0-1"
},
"organization": {
"id": "00000000000000000000orgId"
},
"related": {
"ip": [
"1.2.3.4"
]
},
"threat": {
"indicator": {
"file": {
"hash": {
"sha256": "8b3f191819931d1f2cef7289239b5f77c00b079847b9c2636e56854d1e5eff71"
},
"name": "eicar0000001.txt",
"path": "C:\\\\\\\\eicar0000001.txt"
},
"name": "Test",
"type": "file"
}
}
}
{
"message": "CEF:0|Bitdefender|GravityZone|6.67.0-1|170000|New Incident|3|BitdefenderGZModule=new-incident dvchost=HOST-01 BitdefenderGZComputerFQDN=host01.example.local dvc=1.2.3.4, 1.2.3.4 deviceExternalId=devId-000000000000000000000000 BitdefenderGZIncidentId=000000000000000000000000 BitdefenderGZSeverityScore=39 BitdefenderGZAttackEntry=000000000 BitdefenderGZMainAction=no action BitdefenderGZDetectionName=SuspiciousPcaluaSpawned fileHash=00000000000000000000000000000000 BitdefenderGZFileHashSha256=0000000000000000000000000000000000000000000000000000000000000000 spid=1111 sproc=c:\\\\windows\\\\system32\\\\system.exe BitdefenderGZParentPid=2222 BitdefenderGZParentPath=c:\\\\windows\\\\system32\\\\system.exe BitdefenderGZAttackTypes=[\"Malware\"] BitdefenderGZAttCkId=[\"T1053\",\"T1059\",\"T1202\",\"T1218\",\"T1548\",\"T1569\",\"T1083\",\"T1106\",\"T1497\",\"T1112\",\"T1491\",\"T1027\",\"T1203\",\"T1070\",\"T1565\",\"T1080\",\"T1547\",\"T1113\",\"T1134\",\"T1543\",\"T1574\",\"T1197\",\"T1055\"] BitdefenderGZProcessCommandLine=\"C:\\\\Windows\\\\System32\\\\system.exe\" -a \"C:\\\\Program Files\\\\Example\\\\App\\\\App.exe\" -d \"C:\\\\Program Files\\\\Example\\\\App\" start=2025-10-15T05:48:34.731Z suser=john.doe@test BitdefenderGZCompanyId=000000000000000000000000 BitdefenderGZEndpointId=000000000000000000000000 suid=S-1-5-21-0000000000-0000000000-0000000000-00000",
"event": {
"category": [
"process"
],
"kind": "alert",
"module": "new-incident",
"severity": 3,
"start": "2025-10-15T05:48:34.731000Z",
"type": [
"info"
]
},
"device": {
"id": "devId-000000000000000000000000"
},
"host": {
"id": "000000000000000000000000",
"ip": [
"1.2.3.4",
"1.2.3.4"
],
"name": "host01.example.local"
},
"observer": {
"product": "GravityZone",
"vendor": "Bitdefender",
"version": "6.67.0-1"
},
"organization": {
"id": "000000000000000000000000"
},
"related": {
"ip": [
"1.2.3.4"
],
"user": [
"john.doe@test"
]
},
"source": {
"user": {
"id": "S-1-5-21-0000000000-0000000000-0000000000-00000",
"name": "john.doe@test"
}
}
}
{
"message": "CEF:0|Bitdefender|GravityZone|6.40.1-1|1000|Web Control|9|BitdefenderGZModule=uc dvchost=example BitdefenderGZComputerFQDN=example.test.local dvc=1.2.3.4 deviceExternalId=1234567890abcdef12345678 BitdefenderGZApplicationControlType=http request=external-content.domain.com/ip3/www.test_request.com BitdefenderGZApplicationControlBlockType=http_categories BitdefenderGZDataCategories=Ads act=uc_site_blocked end=Dec 16 2024 12:34:33 Z cnt=1 suser=john.doe@test.local suid=S-1-5-21-1111111111-222222222-3333333333-500",
"event": {
"action": "uc_site_blocked",
"category": [
"web"
],
"end": "2024-12-16T12:34:33Z",
"module": "uc",
"severity": 9,
"type": [
"info"
]
},
"bitdefender": {
"gravityzone": {
"application_control": {
"block_type": "http_categories",
"detection_count": 1,
"type": "http"
},
"data": {
"categories": "Ads"
}
}
},
"device": {
"id": "1234567890abcdef12345678"
},
"host": {
"ip": [
"1.2.3.4"
],
"name": "example.test.local"
},
"observer": {
"product": "GravityZone",
"vendor": "Bitdefender",
"version": "6.40.1-1"
},
"related": {
"hosts": [
"external-content.domain.com"
],
"ip": [
"1.2.3.4"
],
"user": [
"john.doe@test.local"
]
},
"source": {
"user": {
"id": "S-1-5-21-1111111111-222222222-3333333333-500",
"name": "john.doe@test.local"
}
},
"url": {
"domain": "external-content.domain.com",
"original": "external-content.domain.com/ip3/www.test_request.com",
"path": "/ip3/www.test_request.com",
"port": 80,
"scheme": "http"
}
}
{
"message": "CEF:0|Bitdefender|GravityZone|6.62.0-2|1000|Web Control|9|BitdefenderGZModule=uc BitdefenderGZCompanyId=123123123123123 dvchost=test BitdefenderGZComputerFQDN=test.test.local dvc=1.2.3.4 deviceExternalId=123123123123123213 BitdefenderGZApplicationControlType=http request=https://test.com BitdefenderGZApplicationControlBlockType=http_antimalware act=uc_site_blocked end=2025-06-02T20:43:28.000Z cnt=1 suser=test.user@test suid=S-1-5-21-1111111111-222222222-3333333333-500",
"event": {
"action": "uc_site_blocked",
"category": [
"web"
],
"end": "2025-06-02T20:43:28Z",
"module": "uc",
"severity": 9,
"type": [
"info"
]
},
"bitdefender": {
"gravityzone": {
"application_control": {
"block_type": "http_antimalware",
"detection_count": 1,
"type": "http"
}
}
},
"device": {
"id": "123123123123123213"
},
"host": {
"ip": [
"1.2.3.4"
],
"name": "test.test.local"
},
"observer": {
"product": "GravityZone",
"vendor": "Bitdefender",
"version": "6.62.0-2"
},
"organization": {
"id": "123123123123123"
},
"related": {
"ip": [
"1.2.3.4"
],
"user": [
"test.user@test"
]
},
"source": {
"user": {
"id": "S-1-5-21-1111111111-222222222-3333333333-500",
"name": "test.user@test"
}
},
"url": {
"domain": "test.com",
"full": "https://test.com",
"original": "https://test.com",
"port": 443,
"registered_domain": "test.com",
"scheme": "https",
"top_level_domain": "com"
}
}
{
"message": "CEF:0|Bitdefender|GravityZone|6.62.0-2|1000|Web Control|9|BitdefenderGZModule=uc BitdefenderGZCompanyId=12312312313123123 dvchost=TEST-TEST BitdefenderGZComputerFQDN=test.test.local dvc=1.2.3.4 deviceExternalId=123123123213 BitdefenderGZApplicationControlType=http request=https://test.org BitdefenderGZApplicationControlBlockType=http_antimalware act=uc_site_blocked end=2025-06-01T09:06:08.000Z cnt=2 suser=test.user@test suid=S-1-5-21-1111111111-222222222-3333333333-500",
"event": {
"action": "uc_site_blocked",
"category": [
"web"
],
"end": "2025-06-01T09:06:08Z",
"module": "uc",
"severity": 9,
"type": [
"info"
]
},
"bitdefender": {
"gravityzone": {
"application_control": {
"block_type": "http_antimalware",
"detection_count": 2,
"type": "http"
}
}
},
"device": {
"id": "123123123213"
},
"host": {
"ip": [
"1.2.3.4"
],
"name": "test.test.local"
},
"observer": {
"product": "GravityZone",
"vendor": "Bitdefender",
"version": "6.62.0-2"
},
"organization": {
"id": "12312312313123123"
},
"related": {
"ip": [
"1.2.3.4"
],
"user": [
"test.user@test"
]
},
"source": {
"user": {
"id": "S-1-5-21-1111111111-222222222-3333333333-500",
"name": "test.user@test"
}
},
"url": {
"domain": "test.org",
"full": "https://test.org",
"original": "https://test.org",
"port": 443,
"registered_domain": "test.org",
"scheme": "https",
"top_level_domain": "org"
}
}
{
"message": "CEF:0|Bitdefender|GravityZone|6.63.0-1|1000|Web Control|9|BitdefenderGZModule=uc BitdefenderGZCompanyId=1234567890abcdef12345678 dvchost=example BitdefenderGZComputerFQDN=example.test.local dvc=1.2.3.4 deviceExternalId=1234567890abcdef12345678 BitdefenderGZApplicationControlType=http request=https://external-content.domain.com BitdefenderGZApplicationControlBlockType=http_antimalware act=uc_site_blocked end=2025-06-20T12:34:56.000Z cnt=1 suser=john.doe@test.local suid=S-1-5-21-1111111111-2222222222-3333333333-4444",
"event": {
"action": "uc_site_blocked",
"category": [
"web"
],
"end": "2025-06-20T12:34:56Z",
"module": "uc",
"severity": 9,
"type": [
"info"
]
},
"bitdefender": {
"gravityzone": {
"application_control": {
"block_type": "http_antimalware",
"detection_count": 1,
"type": "http"
}
}
},
"device": {
"id": "1234567890abcdef12345678"
},
"host": {
"ip": [
"1.2.3.4"
],
"name": "example.test.local"
},
"observer": {
"product": "GravityZone",
"vendor": "Bitdefender",
"version": "6.63.0-1"
},
"organization": {
"id": "1234567890abcdef12345678"
},
"related": {
"ip": [
"1.2.3.4"
],
"user": [
"john.doe@test.local"
]
},
"source": {
"user": {
"id": "S-1-5-21-1111111111-2222222222-3333333333-4444",
"name": "john.doe@test.local"
}
},
"url": {
"domain": "external-content.domain.com",
"full": "https://external-content.domain.com",
"original": "https://external-content.domain.com",
"port": 443,
"registered_domain": "domain.com",
"scheme": "https",
"subdomain": "external-content",
"top_level_domain": "com"
}
}
Extracted Fields
The following table lists the fields that are extracted, normalized under the ECS format, analyzed and indexed by the parser. It should be noted that infered fields are not listed.
| Name | Type | Description |
|---|---|---|
@timestamp |
date |
Date/time when the event originated. |
bitdefender.gravityzone.application_control.block_type |
keyword |
Type of block detected by Bitdefender GravityZone Application Control. |
bitdefender.gravityzone.application_control.detection_count |
long |
Number of detections by Bitdefender GravityZone Application Control. |
bitdefender.gravityzone.application_control.type |
keyword |
Type of application control detected by Bitdefender GravityZone. |
bitdefender.gravityzone.data.categories |
keyword |
Data categories detected by Bitdefender GravityZone. |
bitdefender.gravityzone.exploit.type |
keyword |
Exploit type detected by Bitdefender GravityZone. |
destination.user.name |
keyword |
Short name or login of the user. |
email.sender.address |
keyword |
Address of the message sender. |
email.subject |
keyword |
The subject of the email message. |
event.action |
keyword |
The action captured by the event. |
event.end |
date |
event.end contains the date when the event ended or when the activity was last observed. |
event.kind |
keyword |
The kind of the event. The highest categorization field in the hierarchy. |
event.module |
keyword |
Name of the module this data is coming from. |
event.outcome |
keyword |
The outcome of the event. The lowest level categorization field in the hierarchy. |
event.severity |
long |
Numeric severity of the event. |
event.start |
date |
event.start contains the date when the event started or when the activity was first observed. |
event.type |
keyword |
Event type. The third categorization field in the hierarchy. |
file.path |
keyword |
Full path to the file, including the file name. |
host.id |
keyword |
Unique host id. |
host.ip |
ip |
Host ip addresses. |
host.name |
keyword |
Name of the host. |
observer.product |
keyword |
The product name of the observer. |
observer.vendor |
keyword |
Vendor name of the observer. |
observer.version |
keyword |
Observer version. |
organization.id |
keyword |
Unique identifier for the organization. |
process.parent.name |
keyword |
Process name. |
process.parent.path |
keyword |
Path of the parent process. |
rule.name |
keyword |
Rule name |
source.ip |
ip |
IP address of the source. |
source.user.id |
keyword |
Unique identifier of the user. |
source.user.name |
keyword |
Short name or login of the user. |
threat.indicator.file.hash.sha256 |
keyword |
SHA256 hash. |
threat.indicator.file.name |
keyword |
Name of the file including the extension, without the directory. |
threat.indicator.file.path |
keyword |
Full path to the file, including the file name. |
threat.indicator.type |
keyword |
Type of indicator |
url.domain |
keyword |
Domain of the url. |
url.original |
wildcard |
Unmodified original url as seen in the event source. |
url.path |
wildcard |
Path of the request, such as "/search". |
url.query |
keyword |
Query string of the request. |
url.scheme |
keyword |
Scheme of the url. |
For more information on the Intake Format, please find the code of the Parser, Smart Descriptions, and Supported Events here.