Microsoft Intune
Overview
- Vendor:
- Supported environment:
- Version compatibility:
- Detection based on: Telemetry
- Supported application or feature: AuditLogs, OperationalLogs, Devices, DeviceComplianceOrg
Microsoft Intune helps you protect your workforce's corporate data by managing devices and apps. Intune provides mobile device management (MDM) and mobile app management (MAM) from a secure cloud-based service that is administered using the Microsoft Endpoint Manager admin center. Using Intune, you ensure your workforce's corporate resources (data, devices, and apps) are correctly configured, accessed, and updated, meeting your company's compliance policies and requirements.
This setup guide describe how to forward events produced by Microsoft Intune to Sekoia.io.
Configure
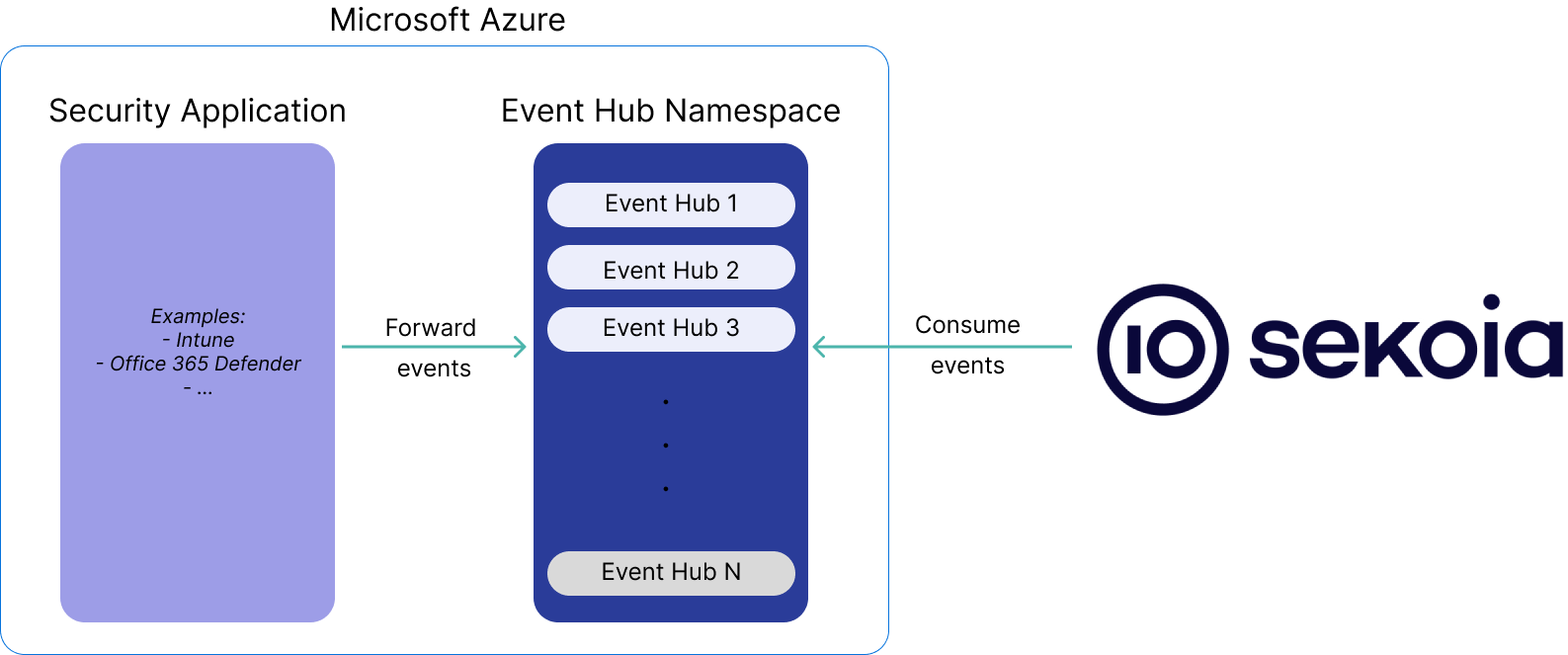
To forward Microsoft Intune events from Microsoft to Sekoia.io you need to send your event to an Azure Event Hub where Sekoia.io will collect the events.
Prerequisite
To send Microsoft Intune logs to Sekoia.io, there are some prerequisites:
- Have access to the Sekoia.io XDR Operations Center
- Be a Intune Service Administrator to perfom the interconnection with Azure Event Hub
- Be a Contributor on Azure to setup an Event Hub.
Azure Event Hubs is a cloud-based event streaming platform and event ingestion service provided by Microsoft Azure. It is designed to handle large amounts of event data generated by various applications, devices, and services in real-time. Event Hubs enables you to ingest, process, and store events, logs, telemetry data, and other streaming data for further analysis, monitoring, and processing. Two ways are suggested in order to set up everything you need to forward your events on Sekoia.io.
If you are not an expert and want an easy way to configure the ressources on Azure, we recommend to use to Automatic way as it is easier to set up.
These two ways will create an Azure Event Hub and a Storage Account.
** Use the template to create the ressources**
To get started, click on the button below and fill the form on Azure to set up the required environment for Sekoia
Some fields must be filled in.
Project details
- Subscription: select the Azure subscription you want to use
- Resource Group: select or create a new Resource Group. A Resource Group is a container that holds related resources
Instance details
- Region: select the appropriated region
- Project Name: give a name for this project. Here is how the names of the resources will be affected by this project name
| Ressource | Name |
|---|---|
| Event Hub Namespace | <project_name>ehns |
| Event Hub | <project_name>eh |
| Shared Access Policy | <project_name>ap |
| Consumer Group | <project_name>cp |
| Storage Account | <project_name>sa |
- Event Hub Sku: Select the messaging tier for Event Hub Namespace between
Basic,StandardorPremium. We do not recommendBasicmodel due to its limitation. Please follow this Microsoft web page to get more information avec the different messaging tier. - Troughput Unit: A unit gives you up to 1 MB/s or 1,000 events per second (whichever comes first) per Event Hub Namespace. Please adapt it to your need.
- Enable Auto Inflate: When checked, the Auto-inflate feature of Event Hubs automatically scales up by increasing the number of troughput units, to meet usage needs.
- Auto Inflate Maximum Throughput Unit: When Enable Auto Inflate is checked, you can specify the maximum throughput units you allow.
- Partition Count: The number of event hub partitions. Microsoft recommends a maximum throughput of 1 MB/s per partition. Unless you plan to add more Event hubs to the Event Hub Namespace, the Partition Count and Throughput Unit variables should have the same values.
- Retention Time: How long you will keep events in the Event hub in days.
** Use the output variables to create a Sekoia playbook**
When the message Your deployment is complete is displayed, click on Outputs.

Keep these 5 pieces of information displayed carefully, it will used to configure the Trigger Configuration of the Sekoia playbook.
Overview
This setup guide will show you how to create an Event Hub manually.
Theses changes have to be made from the Azure Web Portal.
Some resources created during this procedure are needed to connect Sekoia.io to the Event Hub, you can complete the following table to save all the useful informations for later use.
| Name | Value | Description | Example |
|---|---|---|---|
| hub_name | To be completed at step 3 | Name of the Event Hub | sekoia_event_hub |
| hub_connection_string | To be completed at step 5 | Connection string–primary key | Endpoint=sb://company-eventhub.servicebus.windows.net/;SharedAccessKeyName=sekoiaio;SharedAccessKey=XXXXXX;EntityPath=sekoia_event_hub |
| hub_consumer_group | To be completed at step 6 | Name of the comsumer group | consumergroup_sekoiaio |
| storage_container_name | To be completed at step 7 | Name of your container | sekoiaio |
| storage_connection_string | To be completed at step 8 | Storage connection string | DefaultEndpointsProtocol=https;AccountName=sekoiaiocheckpoint;AccountKey=XXXXX |
As a prerequisite, you need to choose an existing Resource group, or create a new one (e.g. company-resource-group).
Step 1: Find your Subscription ID
- Go to: Home > Cost Management + Billing > Subscriptions.
- From there, keep the relevant “Subscription ID” that will be used along the process.

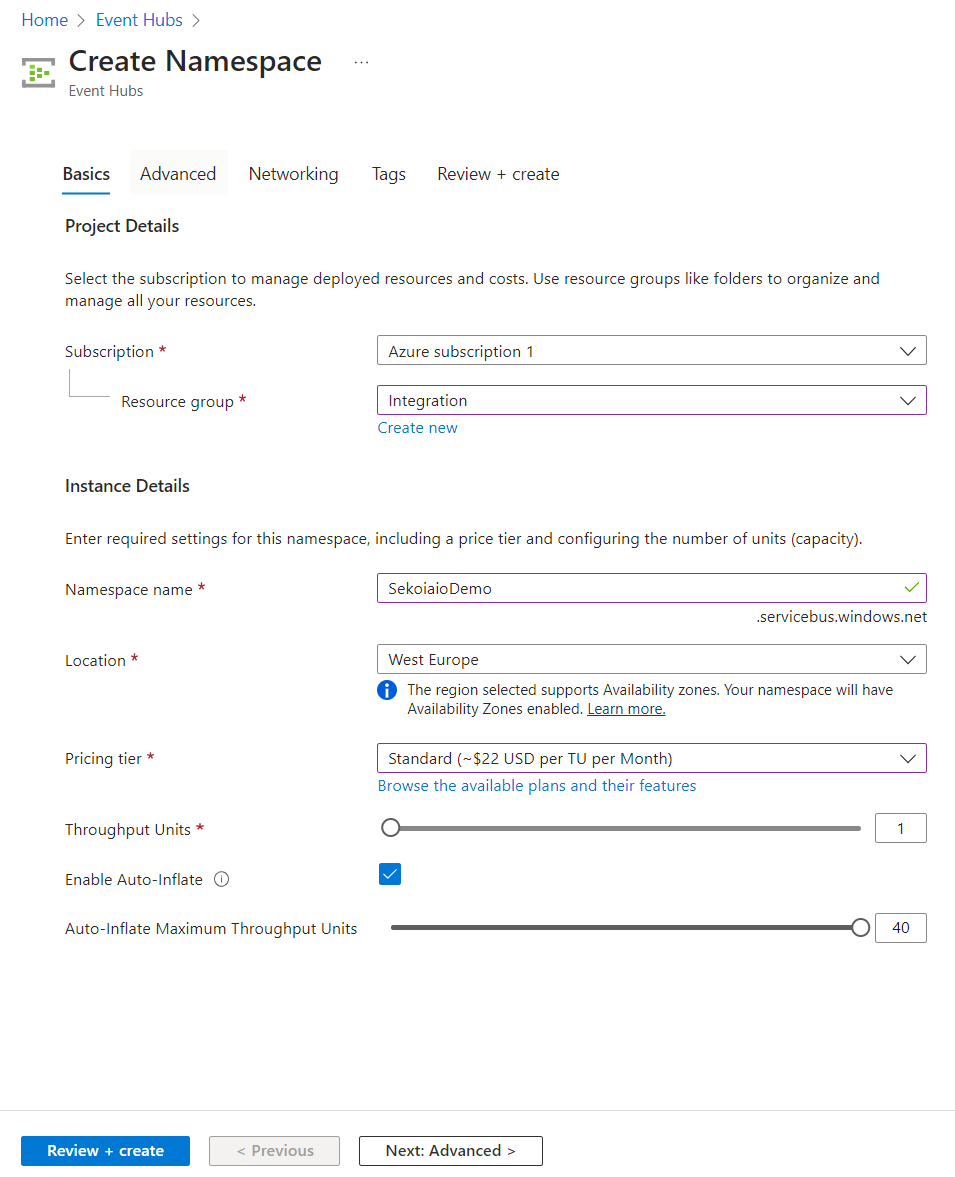
Step 2: Create Event Hub Namespace
- Navigate to Home > Event Hubs.
- Create an Event Hub Namespace.
- Select your Subscription and your Resource group. Click on create new if you want your Event Hub Namespace in a new Resource group.
- Choose a namespace name.
- Select a location based on your events location.
- Select the pricing tier plan based on your utilisation: Standard or Premimum (We don't recommend to choose the Basic plan due to its limitations.)
- Select the throughput units number based on your events, or enable the auto inflate mode:
1 throughput unit can process up to 1 MB per second or 1000 events per second (whichever comes first).
Step 3: Create Event Hub Instance
When your Event Hub Namespace is created you can create an Event Hub inside:
- Navigate to Home > Event Hubs > company-eventhubnamespace.
- Create an Event Hub.
- Select 4 as default partition count
- Select
Deleteas cleanup policy - Type 168h (7 days) as retention time
- Click
Create
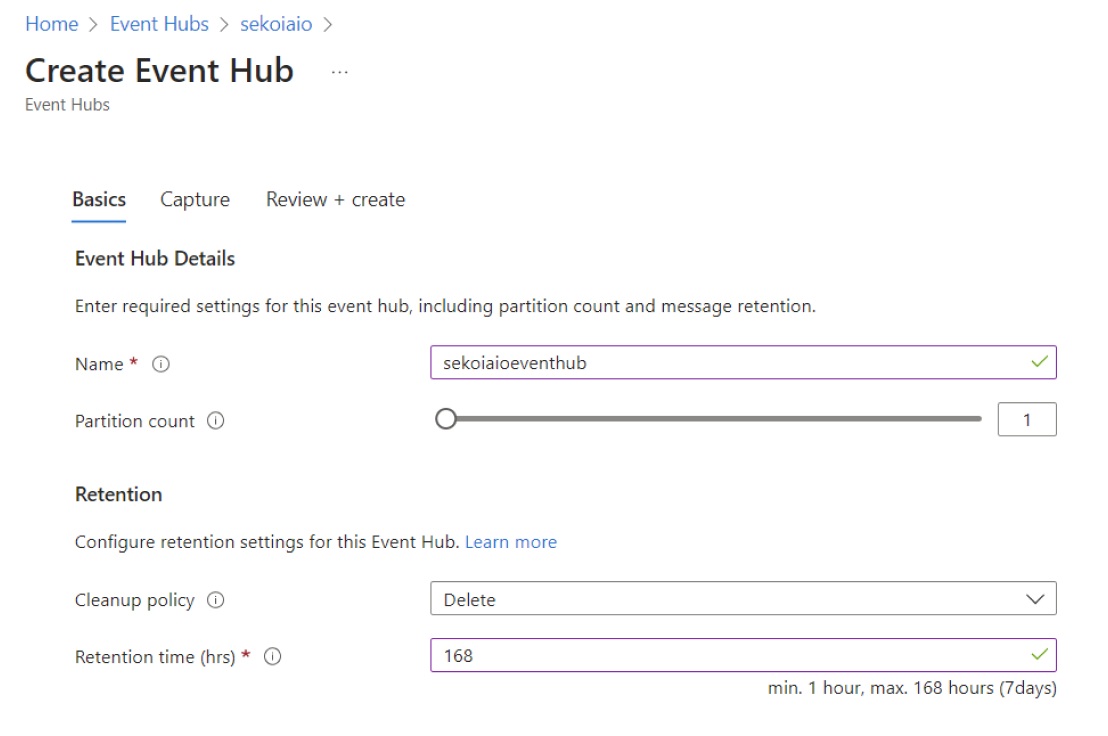
Info
Carefully store the Event Hub name that will be used for sekoia playbook configuration.
Step 4: Create “Shared Access Policies” for the Event Hub
- Navigate to Home > Event Hubs > company-eventhubnamespace > eventhubname | Shared access policies.
-
Create a policy (e.g.
sekoiaio) with the claimsListen.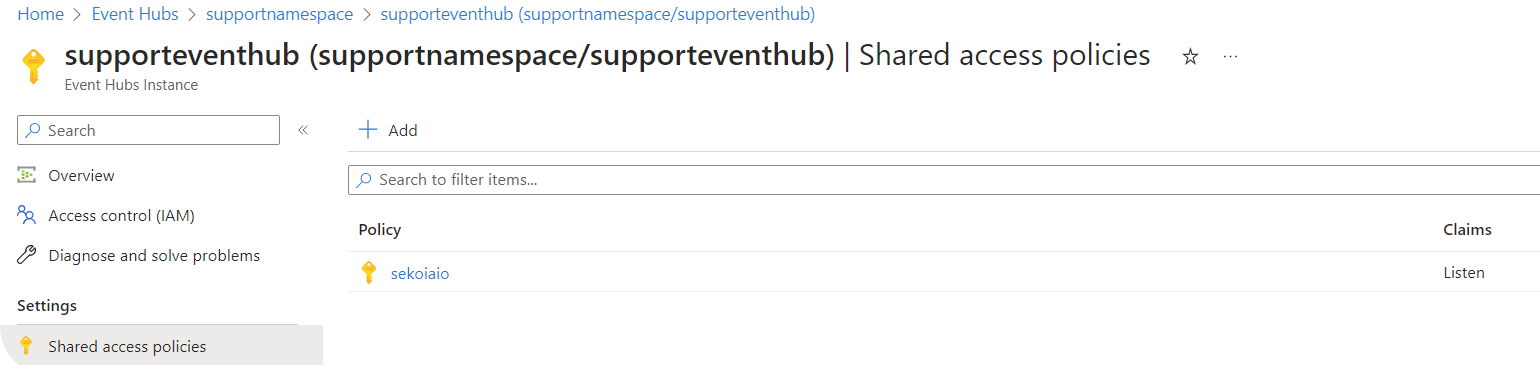
-
Once created, click on the policy.
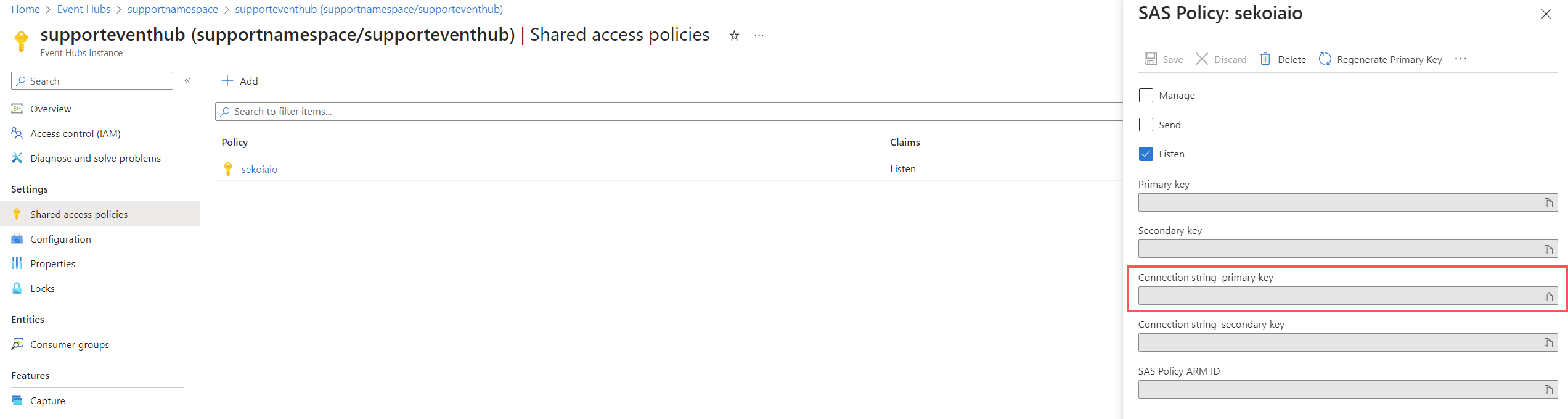
Info
Carefully store the connection string–primary key that will be used for sekoia playbook configuration.
Step 5: Create a Consumer group
- Navigate to Home > Event Hubs > company-eventhubnamespace > eventhubname | Consumer groups.
- Create a Consumer group (e.g.
consumergroup_sekoiaio).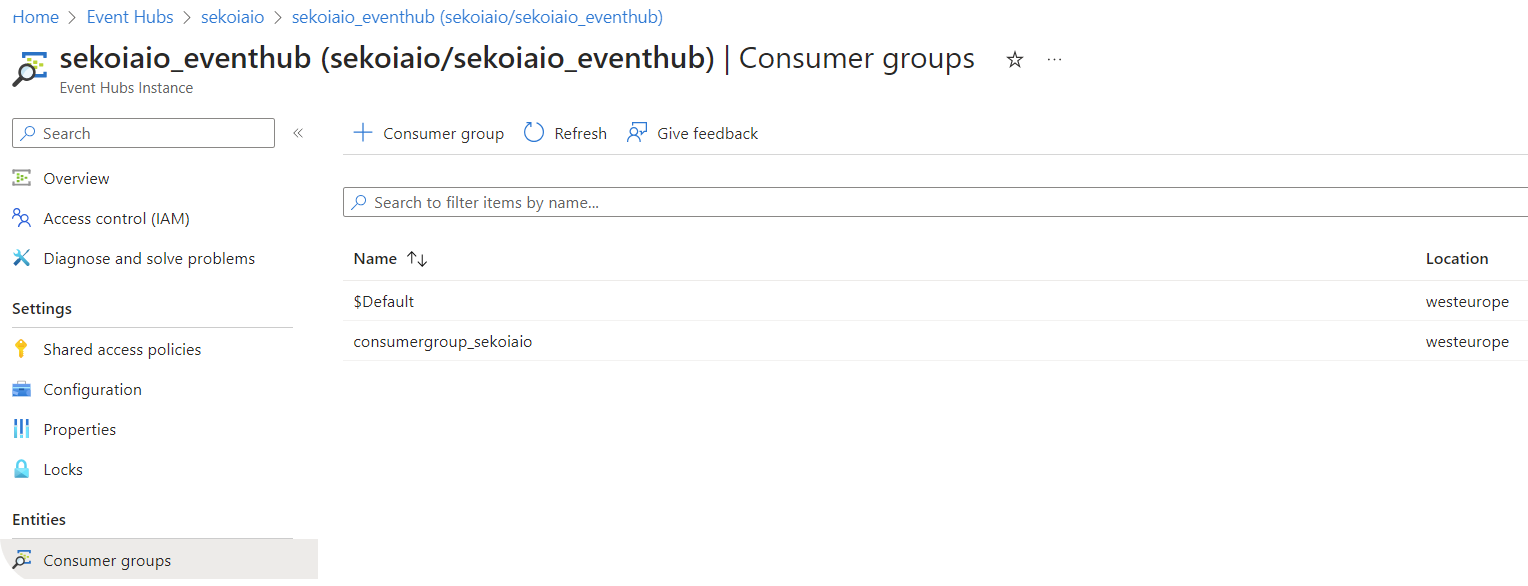
Info
Carefully store the Consumer group name that will be used for sekoia playbook configuration.
Step 6: Create a Storage Account with a container
In order to allow Sekoia.io keep track of the consumed events, the next step consists in creating a dedicated Storage account.
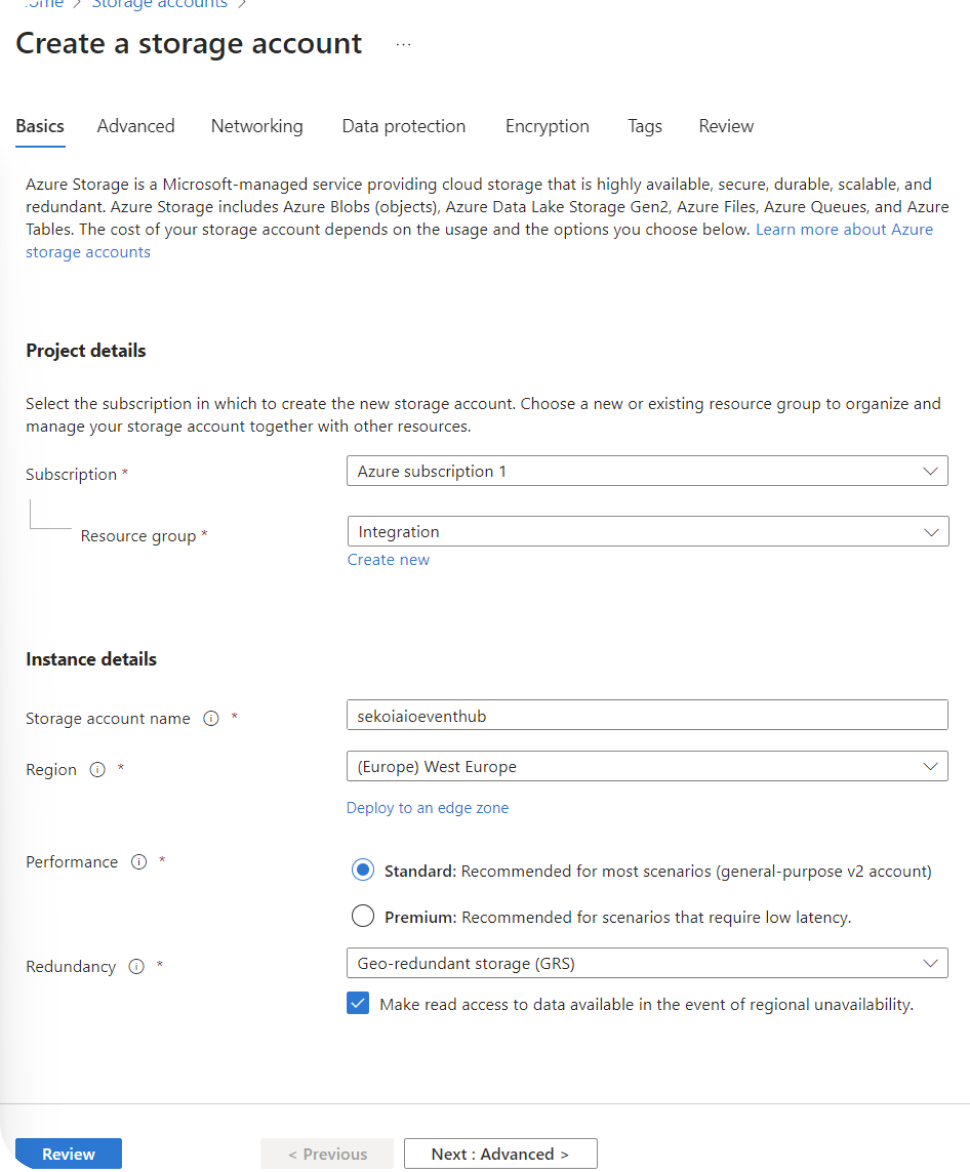
- Navigate to Home > Storage accounts.
- Create a Storage account.
- Select your Subscription and your Resource group.
- Choose a Storage account name.
-
Select a Region.
Info
You must choose the Region used during the Event Hub Namespace creation.
-
Select your perfomance and redundancy parameters.
Info
We advise at least the following values: - performance: standard - redundancy: Geo-Redundancy storage (GRS)
When your storage account is created you can create an container inside. 1. Navigate to Home > Storage accounts > storageaccoutname | containers. 2. Create an container.
Keep the Public Acces Level to Private.
Info
The container name should be the same as the Event Hub name. Carefully store that container name that will be used for sekoia playbook configuration.
Step 7: Retrieve Connection String
You have to retrieve the connection string from Azure Web Portal.
- Go to Home > Storage accounts > storageaccoutname | Access Keys.
- Click on "Show Keys" on the first Connection String.
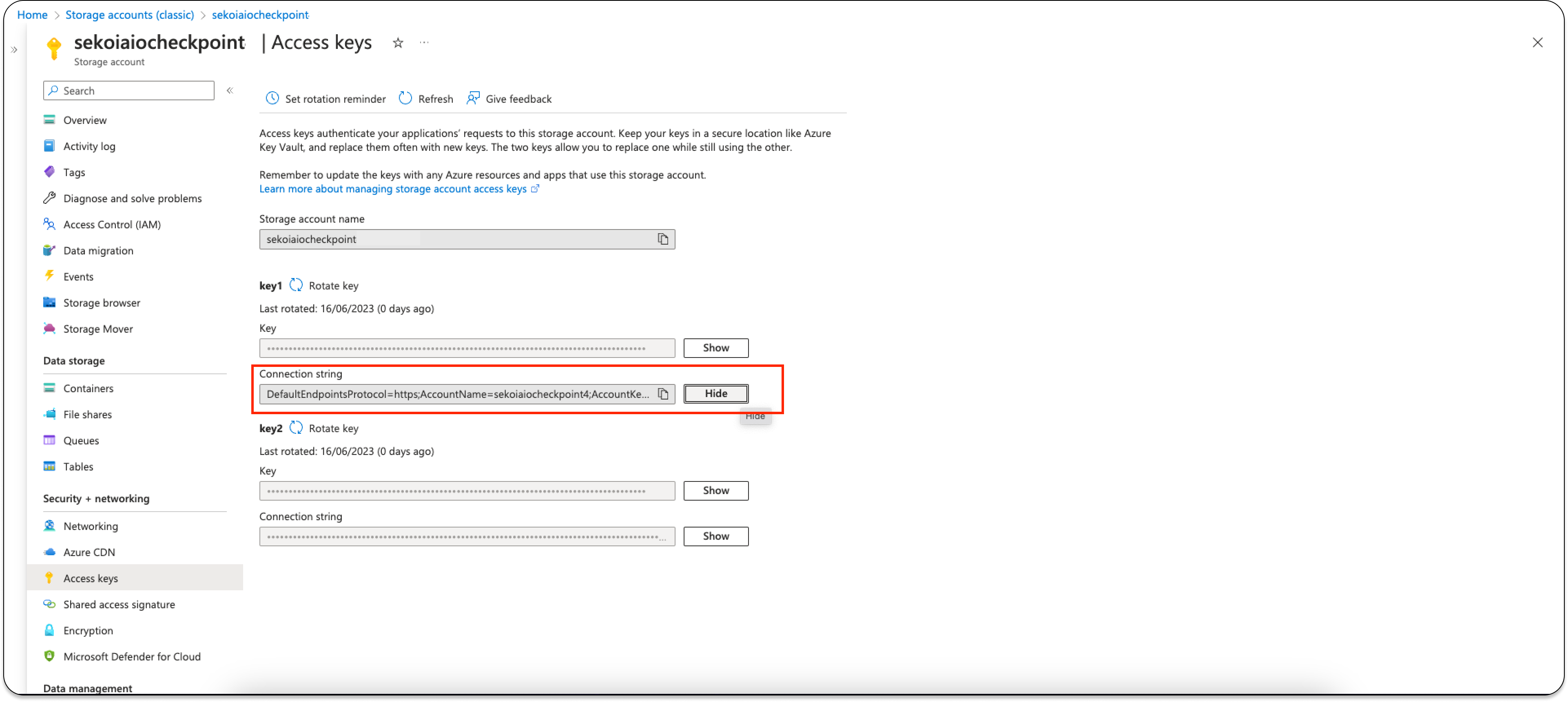
Info
Carefully store the Connection String that will be used for sekoia playbook configuration.
Further Readings
Send logs from Microsoft Intune to Azure Event Hub
When you have an Event Hub follow this guide to send your events from Microsoft Intune to the Event Hub.
Create your intake
- Go to the intake page and create a new intake from the
Microsoft Intune. - To fill the form, use the table completed during the creation of the Event Hub.
Enjoy your events on the Events page
Raw Events Samples
In this section, you will find examples of raw logs as generated natively by the source. These examples are provided to help integrators understand the data format before ingestion into Sekoia.io. It is crucial for setting up the correct parsing stages and ensuring that all relevant information is captured.
{
"time": "2022-11-16T09:35:22.0835000Z",
"tenantId": "163381f4-6b9c-43c2-8b57-bfc16b7354f2",
"category": "AuditLogs",
"operationName": "Rename device ManagedDevice",
"properties": {
"ActivityDate": "11/16/2022 9:35:22 AM",
"ActivityResultStatus": 1,
"ActivityType": 3,
"Actor": {
"ActorType": 1,
"Application": "5926fc8e-304e-4f59-8bed-58ca97cc39a4",
"ApplicationName": "Microsoft Intune portal extension",
"IsDelegatedAdmin": false,
"Name": null,
"ObjectId": "d9851461-2e64-43b5-bc4d-a3b3c115c19e",
"PartnerTenantId": "00000000-0000-0000-0000-000000000000",
"UserPermissions": [
"*"
],
"UPN": "Pipin.Saquet@theShire.com"
},
"AdditionalDetails": "",
"AuditEventId": "6f3dfd87-3320-41a1-88ff-672a7e731162",
"Category": 4,
"RelationId": null,
"TargetDisplayNames": [
"<null>"
],
"TargetObjectIds": [
"fee80c12-4b53-4196-ac97-8e249e749ab3"
],
"Targets": [
{
"ModifiedProperties": [
{
"Name": "DeviceManagementAPIVersion",
"Old": null,
"New": "5022-09-16"
}
],
"Name": null
}
]
},
"resultType": "Success",
"resultDescription": "None",
"correlationId": "1012dc54-3990-42a6-854e-15b93f707cd3",
"identity": "Pipin.Saquet@theShire.com"
}
{
"time": "2022-11-21T14:09:13.8152000Z",
"tenantId": "163381f4-6b9c-43c2-8b57-bfc16b7354f2",
"category": "AuditLogs",
"operationName": "Delete MobileAppAssignment",
"properties": {
"ActivityDate": "11/21/2022 2:09:13 PM",
"ActivityResultStatus": 1,
"ActivityType": 1,
"Actor": {
"ActorType": 1,
"Application": "5926fc8e-304e-4f59-8bed-58ca97cc39a4",
"ApplicationName": "Microsoft Intune portal extension",
"IsDelegatedAdmin": false,
"Name": null,
"ObjectId": "d9851461-2e64-43b5-bc4d-a3b3c115c19e",
"PartnerTenantId": "00000000-0000-0000-0000-000000000000",
"UserPermissions": [
"*"
],
"UPN": "Pipin@TheShire.com"
},
"AdditionalDetails": "Key = GroupPropertyNamesValue = Target.GroupId Key = IgnoreTruncatePropertyNamesValue = Target.GroupId ",
"AuditEventId": "59fa433c-2f2b-4ac6-a2c5-4c88ed70fce6",
"Category": 5,
"RelationId": null,
"TargetDisplayNames": [
"Remove-HPbloatware.ps1",
"<null>"
],
"TargetObjectIds": [
"a7c6992d-0260-4d73-8c4c-13b16c0d7638",
"38b059fb-6e7c-494d-99a9-0f51e6c3cfaa_1_0"
],
"Targets": [
{
"ModifiedProperties": [],
"Name": "Remove-HPbloatware.ps1"
},
{
"ModifiedProperties": [
{
"Name": "Target.Type",
"Old": null,
"New": "GroupAssignmentTarget"
},
{
"Name": "Settings.Type",
"Old": null,
"New": "Win32LobAppAssignmentSettings"
},
{
"Name": "Id",
"Old": null,
"New": "38b059fb-6e7c-494d-99a9-0f51e6c3cfaa_1_0"
},
{
"Name": "Intent",
"Old": null,
"New": "Required"
},
{
"Name": "Target.GroupId",
"Old": null,
"New": "SDP_MDM_WINDOWSDEVICE(38b059fb-6e7c-494d-99a9-0f51e6c3cfaa) "
},
{
"Name": "Target.DeviceAndAppManagementAssignmentFilterId",
"Old": null,
"New": "<null>"
},
{
"Name": "Target.DeviceAndAppManagementAssignmentFilterType",
"Old": null,
"New": "None"
},
{
"Name": "Settings.Notifications",
"Old": null,
"New": "ShowAll"
},
{
"Name": "Settings.DeliveryOptimizationPriority",
"Old": null,
"New": "NotConfigured"
},
{
"Name": "Source",
"Old": null,
"New": "Direct"
},
{
"Name": "SourceId",
"Old": null,
"New": "<null>"
},
{
"Name": "DeviceManagementAPIVersion",
"Old": null,
"New": "5022-09-01"
}
],
"Name": "<null>"
}
]
},
"resultType": "Success",
"resultDescription": "None",
"correlationId": "23d7b643-115e-41ab-aa07-12800d21cdb5",
"identity": "Pipin@TheShire.com"
}
{
"time": "2025-08-04T11:49:01.7073000Z",
"tenantId": "f30e4506-34b7-44d4-b333-bdddeca23c30",
"category": "OperationalLogs",
"operationName": "Compliance",
"resultType": "None",
"properties": {
"IntuneAccountId": "11111111-1111-1111-1111-111111111111",
"AlertDisplayName": "Managed Device e2e143f1-03d1-4d37-8ac8-f72710cb4b50_Windows_6/16/2025_3:26 PM is not Compliant",
"AlertType": "Managed Device Not Compliant",
"AADTenantId": "f30e4506-34b7-44d4-b333-bdddeca23c30",
"Description": "Windows10CompliancePolicy.SignatureOutOfDate_IID_1b4ed153-830b-3a97-5ba7-ca6adb6d282b||||SignatureOutOfDate||Equals False||True||./Vendor/MSFT/Defender/Health/SignatureOutOfDate",
"DeviceDnsDomain": "",
"DeviceHostName": "HOSTNAME",
"IntuneDeviceId": "529f3b52-cc5f-42ef-85fe-1c2e9a112626",
"DeviceName": "e2e143f1-03d1-4d37-8ac8-f72710cb4b50_Windows_6/16/2025_3:26 PM",
"DeviceNetBiosName": "HOSTNAME",
"DeviceOperatingSystem": "Windows 10.0.22631.5624",
"ScaleUnit": "AMSUB0101",
"ScenarioName": "Microsoft.Management.Services.Diagnostics.SLAEvents.DeviceNotInComplianceSecurityAlert",
"StartTimeUtc": "2025-08-04T11:49:01.7073Z",
"UserName": "USER",
"UPNSuffix": "domain-name.com",
"UserDisplayName": "John Doe",
"IntuneUserId": "8c8cc01e-968d-427f-a4da-bfd2fe66c8af",
"OperationalLogCategory": "DeviceCompliance"
}
}
{
"time": "2025-08-04T13:01:33.1511000Z",
"tenantId": "f30e4506-34b7-44d4-b333-bdddeca23c30",
"category": "AuditLogs",
"operationName": "Create ClientCertificate",
"properties": {
"ActivityDate": "8/4/2025 1:01:33 PM",
"ActivityResultStatus": 1,
"ActivityType": 0,
"Actor": {
"ActorType": 1,
"Application": null,
"ApplicationName": null,
"IsDelegatedAdmin": false,
"Name": null,
"ObjectId": null,
"PartnerTenantId": "00000000-0000-0000-0000-000000000000",
"UserPermissions": [
""
],
"UPN": null
},
"AdditionalDetails": "",
"AuditEventId": "1a900241-6545-4160-9ca4-add8955cb7a0",
"Category": 1,
"RelationId": null,
"TargetDisplayNames": [
"<null>"
],
"TargetObjectIds": [
"1ED5FB12AE659D662A14BEA196ACF2AD948FACF2"
],
"Targets": [
{
"ModifiedProperties": [
{
"Name": "AccountContextId",
"Old": null,
"New": "f30e4506-34b7-44d4-b333-bdddeca23c30"
},
{
"Name": "deviceID",
"Old": null,
"New": "631b6e3f-dff0-4b16-951f-b6484e656a29"
},
{
"Name": "DeviceEnrollmentType",
"Old": null,
"New": "31"
},
{
"Name": "Thumbprint",
"Old": null,
"New": "1ED5FB12AE659D662A14BEA196ACF2AD948FACF2"
}
],
"Name": null
}
]
},
"resultType": "Success",
"resultDescription": "None",
"correlationId": "1f4e9fbf-9c63-43c3-ae39-bedac8baa4ea",
"identity": "See Actor details in properties"
}
{
"time": "2022-11-02T15:50:50.9419000Z",
"tenantId": "163381f4-6b9c-43c2-8b57-bfc16b7354f2",
"category": "DeviceComplianceOrg",
"operationName": "DeviceCompliance",
"resultType": "None",
"properties": {
"DeviceName": "DESKTOP-086N6KI",
"UPN": "Pipin.Saquet@theShire.com",
"ComplianceState": "1",
"ComplianceState_loc": "Compliant",
"OSDescription": "Windows",
"OSVersion": "10.0.19044.2130",
"OS": "Windows",
"OS_loc": "Windows",
"OwnerType": 1,
"OwnerType_loc": "Company",
"DeviceId": "06334044-1a53-47d6-b6f8-ec9dcba8fa93",
"LastContact": "2022-10-28 08:27:37.0000000",
"UserId": "41ab6092-2435-4ed0-a28b-d638523d096e",
"IMEI": "",
"SerialNumber": "5CG21492VW",
"RetireAfterDatetime": "",
"ManagementAgents": 2,
"ManagementAgents_loc": "MDM",
"DeviceType": 1,
"UserName": "Saquet Pipin",
"InGracePeriodUntil": "9999-12-31 23:59:59.0000000",
"DeviceHealthThreatLevel": null,
"DeviceHealthThreatLevel_loc": "Unknown",
"UserEmail": "Pipin.Saquet@theShire.com",
"BatchId": "9ed4cac5-3d86-4760-980d-f1331dfc5ee9",
"IntuneAccountId": "2b9f48a7-75d9-4a72-9b2e-16fd38e121ef",
"AADTenantId": "163381f4-6b9c-43c2-8b57-bfc16b7354f2"
}
}
{
"time": "2022-11-17T07:39:02.4103000Z",
"tenantId": "163381f4-6b9c-43c2-8b57-bfc16b7354f2",
"category": "Devices",
"operationName": "Devices",
"resultType": "None",
"properties": {
"DeviceId": "a2f25343-1d87-4876-9e72-de6111b614e5",
"DeviceName": "Pipin.Saquet_AndroidForWork_10/17/2022_2:23 PM",
"UPN": "Pipin.Saquet@theShire.com",
"LastContact": "2022-11-17 07:03:14.6829201",
"OSVersion": "12.0",
"OS": "Android (Personally-Owned Work Profile)",
"CompliantState": "Compliant",
"Ownership": "Personal",
"ManagedBy": "Intune",
"Model": "SM-G996B",
"SerialNumber": "0",
"Manufacturer": "samsung",
"CreatedDate": "2022-10-17 14:23:27.0091131",
"DeviceState": "Managed",
"UserEmail": "Pipin.Saquet@theShire.com",
"UserName": "Pipin.Saquet",
"IMEI": "88888",
"PhoneNumber": "+*******0016",
"DeviceRegistrationState": "Registered",
"ReferenceId": "5f02959f-d014-4f53-a1be-892a7e7dd450",
"ManagedDeviceName": "Pipin.Saquet_AndroidForWork_10/17/2022_2:23 PM",
"GraphDeviceIsManaged": true,
"CategoryName": "",
"EncryptionStatusString": "True",
"SubscriberCarrierNetwork": "Orange F",
"JoinType": "Azure AD registered",
"SupervisedStatusString": "False",
"WifiMacAddress": "aaa:ffff",
"StorageTotal": 0,
"StorageFree": 0,
"AndroidPatchLevel": "2022-10-01",
"MEID": "",
"InGracePeriodUntil": "9999-12-31 23:59:59.9999999",
"JailBroken": "false",
"SkuFamily": "",
"EasID": "afw72216560A482C5F77A4E4A9E38E58",
"PrimaryUser": "a7b9fde1-d8d5-438b-9516-7ef639dfe244",
"BatchId": "3068a7ce-6e3a-438f-a943-634dd1412bc5",
"IntuneAccountId": "2b9f48a7-75d9-4a72-9b2e-16fd38e121ef",
"AADTenantId": "163381f4-6b9c-43c2-8b57-bfc16b7354f2"
}
}
{
"time": "2025-08-04T12:16:24.0714000Z",
"tenantId": "f30e4506-34b7-44d4-b333-bdddeca23c30",
"category": "OperationalLogs",
"operationName": "Enrollment",
"resultType": "Success",
"properties": {
"AADDeviceId": "3cb66e38-5a5d-4a85-9944-e9c7e9da6bc9",
"IntuneDeviceId": "6bf91e32-ee7b-454a-866a-76941550cced",
"IntuneAccountId": "11111111-1111-1111-1111-111111111111",
"IntuneUserId": "00000000-0000-0000-0000-000000000000",
"MessageId": "e45b735a-8793-4e37-8e0f-a1ee14e38940",
"AADTenantId": "f30e4506-34b7-44d4-b333-bdddeca23c30",
"OperationalLogCategory": "DeviceEnrollment",
"EnrollmentTimeUTC": "2025-08-04T12:16:24.0714Z",
"ScenarioName": "Microsoft.Management.Services.Diagnostics.SLAEvents.EnrollmentSLAEvent",
"OsVersion": "10.0.17763.0",
"ScaleUnit": "AMSUB0101",
"Os": "Windows",
"EnrollmentType": "Unknown",
"FailureReason": "Unknown",
"FailureCategory": "Not Applicable"
}
}
{
"time": "2022-11-18T09:04:24.7065000Z",
"tenantId": "163381f4-6b9c-43c2-8b57-bfc16b7354f2",
"category": "OperationalLogs",
"operationName": "Compliance",
"resultType": "None",
"properties": {
"IntuneAccountId": "2b9f48a7-75d9-4a72-9b2e-16fd38e121ef",
"AlertDisplayName": "Managed Device Pipin.Saquet_Windows_10/4/2022_12:43 PM is not Compliant",
"AlertType": "Managed Device Not Compliant",
"AADTenantId": "163381f4-6b9c-43c2-8b57-bfc16b7354f2",
"Description": "Windows10CompliancePolicy.AntivirusRequired_IID_aae45eb0-5edb-fc0b-7adf-47a5d6b12208||||Windows10CompliancePolicy.AntivirusRequired||Equals 0||2||./Vendor/MSFT/DeviceStatus/Antivirus/Status",
"DeviceDnsDomain": "",
"DeviceHostName": "TheShire-W744",
"IntuneDeviceId": "45241578-2168-4649-9edc-2e9025b699ac",
"DeviceName": "Pipin.Saquet_Windows_10/4/2022_12:43 PM",
"DeviceNetBiosName": "TheShire-W744",
"DeviceOperatingSystem": "Windows 10.0.19044.2251",
"ScaleUnit": "AMSUB0502",
"ScenarioName": "Microsoft.Management.Services.Diagnostics.SLAEvents.DeviceNotInComplianceSecurityAlert",
"StartTimeUtc": "2022-11-18T09:04:24.7065Z",
"UserName": "Pipin.Saquet",
"UPNSuffix": "TheShire.com",
"UserDisplayName": "Saquet Saquet",
"IntuneUserId": "7d5c7f0f-8740-4e9d-96a9-5c2d4baf1d70",
"OperationalLogCategory": "DeviceCompliance"
}
}
{
"time": "2025-08-04T12:27:18.7592000Z",
"tenantId": "f30e4506-34b7-44d4-b333-bdddeca23c30",
"category": "AuditLogs",
"operationName": "SetReference ManagedDevice",
"properties": {
"ActivityDate": "8/4/2025 12:27:18 PM",
"ActivityResultStatus": 1,
"ActivityType": 4,
"Actor": {
"ActorType": 5,
"Application": "e2872b38-adf3-4d8a-9c10-c5fbd565e4d6",
"ApplicationName": "DeviceChassisInfo",
"IsDelegatedAdmin": false,
"Name": null,
"ObjectId": null,
"PartnerTenantId": "00000000-0000-0000-0000-000000000000",
"UserPermissions": [
"DeviceManagementManagedDevices.ReadWrite.All DeviceManagementConfiguration.ReadWrite.All"
],
"UPN": null
},
"AdditionalDetails": "",
"AuditEventId": "5264c630-a1fb-46cf-b2a8-c72daf04d855",
"Category": 4,
"RelationId": null,
"TargetDisplayNames": [
"<null>"
],
"TargetObjectIds": [
"5ef4a298-6273-4398-9367-0725705583e8"
],
"Targets": [
{
"ModifiedProperties": [
{
"Name": "referenceProperty",
"Old": null,
"New": "DeviceCategory"
},
{
"Name": "referenceValue",
"Old": null,
"New": "67c0a48b-6755-496b-84e9-4e7603037c5d"
},
{
"Name": "DeviceManagementAPIVersion",
"Old": null,
"New": "5025-05-19"
}
],
"Name": null
}
]
},
"resultType": "Success",
"resultDescription": "None",
"correlationId": "0a67d96e-5422-4126-be0b-f4d217736211",
"identity": "See Actor details in properties"
}
Detection section
The following section provides information for those who wish to learn more about the detection capabilities enabled by collecting this intake. It includes details about the built-in rule catalog, event categories, and ECS fields extracted from raw events. This is essential for users aiming to create custom detection rules, perform hunting activities, or pivot in the events page.
Related Built-in Rules
The following Sekoia.io built-in rules match the intake Microsoft Intune. This documentation is updated automatically and is based solely on the fields used by the intake which are checked against our rules. This means that some rules will be listed but might not be relevant with the intake.
SEKOIA.IO x Microsoft Intune on ATT&CK Navigator
Cryptomining
Detection of domain names potentially related to cryptomining activities.
- Effort: master
Dynamic DNS Contacted
Detect communication with dynamic dns domain. This kind of domain is often used by attackers. This rule can trigger false positive in non-controlled environment because dynamic dns is not always malicious.
- Effort: master
Exfiltration Domain
Detects traffic toward a domain flagged as a possible exfiltration vector.
- Effort: master
Login Brute-Force Successful On SentinelOne EDR Management Console
A user has attempted to login several times (brute-force) on the SentinelOne EDR Management Console and succeeded to login.
- Effort: master
Microsoft Intune Non-Compliant Device
Detects Microsoft Intune reporting a device in a non-compliant state. This can indicate either a misconfiguration in Intune or a change of configuration on said device.
- Effort: advanced
Microsoft Intune Policy Change
Detects edits, deletions or creations made to an organization Microsoft Intune policies.
- Effort: intermediate
Remote Access Tool Domain
Detects traffic toward a domain flagged as a Remote Administration Tool (RAT).
- Effort: master
Remote Monitoring and Management Software - AnyDesk
Detect artifacts related to the installation or execution of the Remote Monitoring and Management tool AnyDesk.
- Effort: master
SEKOIA.IO Intelligence Feed
Detect threats based on indicators of compromise (IOCs) collected by SEKOIA's Threat and Detection Research team.
- Effort: elementary
Sekoia.io EICAR Detection
Detects observables in Sekoia.io CTI tagged as EICAR, which are fake samples meant to test detection.
- Effort: master
TOR Usage Generic Rule
Detects TOR usage globally, whether the IP is a destination or source. TOR is short for The Onion Router, and it gets its name from how it works. TOR intercepts the network traffic from one or more apps on user’s computer, usually the user web browser, and shuffles it through a number of randomly-chosen computers before passing it on to its destination. This disguises user location, and makes it harder for servers to pick him/her out on repeat visits, or to tie together separate visits to different sites, this making tracking and surveillance more difficult. Before a network packet starts its journey, user’s computer chooses a random list of relays and repeatedly encrypts the data in multiple layers, like an onion. Each relay knows only enough to strip off the outermost layer of encryption, before passing what’s left on to the next relay in the list.
- Effort: master
Event Categories
The following table lists the data source offered by this integration.
| Data Source | Description |
|---|---|
Asset management |
Information about the set of devices found within the network, along with their current software and configurations |
In details, the following table denotes the type of events produced by this integration.
| Name | Values |
|---|---|
| Kind | `` |
| Category | `` |
| Type | info |
Transformed Events Samples after Ingestion
This section demonstrates how the raw logs will be transformed by our parsers. It shows the extracted fields that will be available for use in the built-in detection rules and hunting activities in the events page. Understanding these transformations is essential for analysts to create effective detection mechanisms with custom detection rules and to leverage the full potential of the collected data.
{
"message": "{\"time\":\"2022-11-16T09:35:22.0835000Z\",\"tenantId\":\"163381f4-6b9c-43c2-8b57-bfc16b7354f2\",\"category\":\"AuditLogs\",\"operationName\":\"Rename device ManagedDevice\",\"properties\":{\"ActivityDate\":\"11/16/2022 9:35:22 AM\",\"ActivityResultStatus\":1,\"ActivityType\":3,\"Actor\":{\"ActorType\":1,\"Application\":\"5926fc8e-304e-4f59-8bed-58ca97cc39a4\",\"ApplicationName\":\"Microsoft Intune portal extension\",\"IsDelegatedAdmin\":false,\"Name\":null,\"ObjectId\":\"d9851461-2e64-43b5-bc4d-a3b3c115c19e\",\"PartnerTenantId\":\"00000000-0000-0000-0000-000000000000\",\"UserPermissions\":[\"*\"],\"UPN\":\"Pipin.Saquet@theShire.com\"},\"AdditionalDetails\":\"\",\"AuditEventId\":\"6f3dfd87-3320-41a1-88ff-672a7e731162\",\"Category\":4,\"RelationId\":null,\"TargetDisplayNames\":[\"<null>\"],\"TargetObjectIds\":[\"fee80c12-4b53-4196-ac97-8e249e749ab3\"],\"Targets\":[{\"ModifiedProperties\":[{\"Name\":\"DeviceManagementAPIVersion\",\"Old\":null,\"New\":\"5022-09-16\"}],\"Name\":null}]},\"resultType\":\"Success\",\"resultDescription\":\"None\",\"correlationId\":\"1012dc54-3990-42a6-854e-15b93f707cd3\",\"identity\":\"Pipin.Saquet@theShire.com\"}",
"event": {
"type": [
"info"
]
},
"@timestamp": "2022-11-16T09:35:22.083500Z",
"action": {
"name": "Rename device ManagedDevice",
"target": "user",
"type": "AuditLogs"
},
"microsoft": {
"intune": {
"correlation_id": "1012dc54-3990-42a6-854e-15b93f707cd3",
"target": {
"display_names": [
"<null>"
],
"modified_properties": [
{
"ModifiedProperties": [
{
"Name": "DeviceManagementAPIVersion",
"New": "5022-09-16",
"Old": null
}
],
"Name": null
}
],
"object_ids": [
"fee80c12-4b53-4196-ac97-8e249e749ab3"
]
},
"tenant_id": "163381f4-6b9c-43c2-8b57-bfc16b7354f2"
}
},
"network": {
"application": "Microsoft Intune portal extension"
},
"related": {
"user": [
"Pipin.Saquet@theShire.com"
]
},
"user": {
"name": "Pipin.Saquet@theShire.com",
"roles": [
"*"
]
}
}
{
"message": "{\"time\":\"2022-11-21T14:09:13.8152000Z\",\"tenantId\":\"163381f4-6b9c-43c2-8b57-bfc16b7354f2\",\"category\":\"AuditLogs\",\"operationName\":\"Delete MobileAppAssignment\",\"properties\":{\"ActivityDate\":\"11/21/2022 2:09:13 PM\",\"ActivityResultStatus\":1,\"ActivityType\":1,\"Actor\":{\"ActorType\":1,\"Application\":\"5926fc8e-304e-4f59-8bed-58ca97cc39a4\",\"ApplicationName\":\"Microsoft Intune portal extension\",\"IsDelegatedAdmin\":false,\"Name\":null,\"ObjectId\":\"d9851461-2e64-43b5-bc4d-a3b3c115c19e\",\"PartnerTenantId\":\"00000000-0000-0000-0000-000000000000\",\"UserPermissions\":[\"*\"],\"UPN\":\"Pipin@TheShire.com\"},\"AdditionalDetails\":\"Key = GroupPropertyNamesValue = Target.GroupId Key = IgnoreTruncatePropertyNamesValue = Target.GroupId \",\"AuditEventId\":\"59fa433c-2f2b-4ac6-a2c5-4c88ed70fce6\",\"Category\":5,\"RelationId\":null,\"TargetDisplayNames\":[\"Remove-HPbloatware.ps1\",\"<null>\"],\"TargetObjectIds\":[\"a7c6992d-0260-4d73-8c4c-13b16c0d7638\",\"38b059fb-6e7c-494d-99a9-0f51e6c3cfaa_1_0\"],\"Targets\":[{\"ModifiedProperties\":[],\"Name\":\"Remove-HPbloatware.ps1\"},{\"ModifiedProperties\":[{\"Name\":\"Target.Type\",\"Old\":null,\"New\":\"GroupAssignmentTarget\"},{\"Name\":\"Settings.Type\",\"Old\":null,\"New\":\"Win32LobAppAssignmentSettings\"},{\"Name\":\"Id\",\"Old\":null,\"New\":\"38b059fb-6e7c-494d-99a9-0f51e6c3cfaa_1_0\"},{\"Name\":\"Intent\",\"Old\":null,\"New\":\"Required\"},{\"Name\":\"Target.GroupId\",\"Old\":null,\"New\":\"SDP_MDM_WINDOWSDEVICE(38b059fb-6e7c-494d-99a9-0f51e6c3cfaa) \"},{\"Name\":\"Target.DeviceAndAppManagementAssignmentFilterId\",\"Old\":null,\"New\":\"<null>\"},{\"Name\":\"Target.DeviceAndAppManagementAssignmentFilterType\",\"Old\":null,\"New\":\"None\"},{\"Name\":\"Settings.Notifications\",\"Old\":null,\"New\":\"ShowAll\"},{\"Name\":\"Settings.DeliveryOptimizationPriority\",\"Old\":null,\"New\":\"NotConfigured\"},{\"Name\":\"Source\",\"Old\":null,\"New\":\"Direct\"},{\"Name\":\"SourceId\",\"Old\":null,\"New\":\"<null>\"},{\"Name\":\"DeviceManagementAPIVersion\",\"Old\":null,\"New\":\"5022-09-01\"}],\"Name\":\"<null>\"}]},\"resultType\":\"Success\",\"resultDescription\":\"None\",\"correlationId\":\"23d7b643-115e-41ab-aa07-12800d21cdb5\",\"identity\":\"Pipin@TheShire.com\"}",
"event": {
"type": [
"info"
]
},
"@timestamp": "2022-11-21T14:09:13.815200Z",
"action": {
"name": "Delete MobileAppAssignment",
"target": "user",
"type": "AuditLogs"
},
"microsoft": {
"intune": {
"correlation_id": "23d7b643-115e-41ab-aa07-12800d21cdb5",
"target": {
"display_names": [
"<null>",
"Remove-HPbloatware.ps1"
],
"modified_properties": [
{
"ModifiedProperties": [
{
"Name": "Target.Type",
"New": "GroupAssignmentTarget",
"Old": null
},
{
"Name": "Settings.Type",
"New": "Win32LobAppAssignmentSettings",
"Old": null
},
{
"Name": "Id",
"New": "38b059fb-6e7c-494d-99a9-0f51e6c3cfaa_1_0",
"Old": null
},
{
"Name": "Intent",
"New": "Required",
"Old": null
},
{
"Name": "Target.GroupId",
"New": "SDP_MDM_WINDOWSDEVICE(38b059fb-6e7c-494d-99a9-0f51e6c3cfaa) ",
"Old": null
},
{
"Name": "Target.DeviceAndAppManagementAssignmentFilterId",
"New": "<null>",
"Old": null
},
{
"Name": "Target.DeviceAndAppManagementAssignmentFilterType",
"New": "None",
"Old": null
},
{
"Name": "Settings.Notifications",
"New": "ShowAll",
"Old": null
},
{
"Name": "Settings.DeliveryOptimizationPriority",
"New": "NotConfigured",
"Old": null
},
{
"Name": "Source",
"New": "Direct",
"Old": null
},
{
"Name": "SourceId",
"New": "<null>",
"Old": null
},
{
"Name": "DeviceManagementAPIVersion",
"New": "5022-09-01",
"Old": null
}
],
"Name": "<null>"
}
],
"object_ids": [
"38b059fb-6e7c-494d-99a9-0f51e6c3cfaa_1_0",
"a7c6992d-0260-4d73-8c4c-13b16c0d7638"
]
},
"tenant_id": "163381f4-6b9c-43c2-8b57-bfc16b7354f2"
}
},
"network": {
"application": "Microsoft Intune portal extension"
},
"related": {
"user": [
"Pipin@TheShire.com"
]
},
"user": {
"name": "Pipin@TheShire.com",
"roles": [
"*"
]
}
}
{
"message": "{\"time\":\"2025-08-04T11:49:01.7073000Z\",\"tenantId\":\"f30e4506-34b7-44d4-b333-bdddeca23c30\",\"category\":\"OperationalLogs\",\"operationName\":\"Compliance\",\"resultType\":\"None\",\"properties\":{\"IntuneAccountId\":\"11111111-1111-1111-1111-111111111111\",\"AlertDisplayName\":\"Managed Device e2e143f1-03d1-4d37-8ac8-f72710cb4b50_Windows_6/16/2025_3:26 PM is not Compliant\",\"AlertType\":\"Managed Device Not Compliant\",\"AADTenantId\":\"f30e4506-34b7-44d4-b333-bdddeca23c30\",\"Description\":\"Windows10CompliancePolicy.SignatureOutOfDate_IID_1b4ed153-830b-3a97-5ba7-ca6adb6d282b||||SignatureOutOfDate||Equals False||True||./Vendor/MSFT/Defender/Health/SignatureOutOfDate\",\"DeviceDnsDomain\":\"\",\"DeviceHostName\":\"HOSTNAME\",\"IntuneDeviceId\":\"529f3b52-cc5f-42ef-85fe-1c2e9a112626\",\"DeviceName\":\"e2e143f1-03d1-4d37-8ac8-f72710cb4b50_Windows_6/16/2025_3:26 PM\",\"DeviceNetBiosName\":\"HOSTNAME\",\"DeviceOperatingSystem\":\"Windows 10.0.22631.5624\",\"ScaleUnit\":\"AMSUB0101\",\"ScenarioName\":\"Microsoft.Management.Services.Diagnostics.SLAEvents.DeviceNotInComplianceSecurityAlert\",\"StartTimeUtc\":\"2025-08-04T11:49:01.7073Z\",\"UserName\":\"USER\",\"UPNSuffix\":\"domain-name.com\",\"UserDisplayName\":\"John Doe\",\"IntuneUserId\":\"8c8cc01e-968d-427f-a4da-bfd2fe66c8af\",\"OperationalLogCategory\":\"DeviceCompliance\"}}",
"event": {
"reason": "Windows10CompliancePolicy.SignatureOutOfDate_IID_1b4ed153-830b-3a97-5ba7-ca6adb6d282b||||SignatureOutOfDate||Equals False||True||./Vendor/MSFT/Defender/Health/SignatureOutOfDate",
"type": [
"info"
]
},
"@timestamp": "2025-08-04T11:49:01.707300Z",
"action": {
"name": "Compliance",
"target": "user",
"type": "OperationalLogs"
},
"host": {
"id": "529f3b52-cc5f-42ef-85fe-1c2e9a112626",
"name": "HOSTNAME",
"os": {
"full": "Windows 10.0.22631.5624",
"version": "10.0.22631.5624"
}
},
"microsoft": {
"intune": {
"tenant_id": "f30e4506-34b7-44d4-b333-bdddeca23c30"
}
},
"related": {
"user": [
"USER"
]
},
"user": {
"domain": "domain-name.com",
"full_name": "John Doe",
"id": "11111111-1111-1111-1111-111111111111",
"name": "USER"
}
}
{
"message": "{\"time\":\"2025-08-04T13:01:33.1511000Z\",\"tenantId\":\"f30e4506-34b7-44d4-b333-bdddeca23c30\",\"category\":\"AuditLogs\",\"operationName\":\"Create ClientCertificate\",\"properties\":{\"ActivityDate\":\"8/4/2025 1:01:33 PM\",\"ActivityResultStatus\":1,\"ActivityType\":0,\"Actor\":{\"ActorType\":1,\"Application\":null,\"ApplicationName\":null,\"IsDelegatedAdmin\":false,\"Name\":null,\"ObjectId\":null,\"PartnerTenantId\":\"00000000-0000-0000-0000-000000000000\",\"UserPermissions\":[\"\"],\"UPN\":null},\"AdditionalDetails\":\"\",\"AuditEventId\":\"1a900241-6545-4160-9ca4-add8955cb7a0\",\"Category\":1,\"RelationId\":null,\"TargetDisplayNames\":[\"<null>\"],\"TargetObjectIds\":[\"1ED5FB12AE659D662A14BEA196ACF2AD948FACF2\"],\"Targets\":[{\"ModifiedProperties\":[{\"Name\":\"AccountContextId\",\"Old\":null,\"New\":\"f30e4506-34b7-44d4-b333-bdddeca23c30\"},{\"Name\":\"deviceID\",\"Old\":null,\"New\":\"631b6e3f-dff0-4b16-951f-b6484e656a29\"},{\"Name\":\"DeviceEnrollmentType\",\"Old\":null,\"New\":\"31\"},{\"Name\":\"Thumbprint\",\"Old\":null,\"New\":\"1ED5FB12AE659D662A14BEA196ACF2AD948FACF2\"}],\"Name\":null}]},\"resultType\":\"Success\",\"resultDescription\":\"None\",\"correlationId\":\"1f4e9fbf-9c63-43c3-ae39-bedac8baa4ea\",\"identity\":\"See Actor details in properties\"}",
"event": {
"type": [
"info"
]
},
"@timestamp": "2025-08-04T13:01:33.151100Z",
"action": {
"name": "Create ClientCertificate",
"target": "user",
"type": "AuditLogs"
},
"microsoft": {
"intune": {
"correlation_id": "1f4e9fbf-9c63-43c3-ae39-bedac8baa4ea",
"target": {
"display_names": [
"<null>"
],
"modified_properties": [
{
"ModifiedProperties": [
{
"Name": "AccountContextId",
"New": "f30e4506-34b7-44d4-b333-bdddeca23c30",
"Old": null
},
{
"Name": "deviceID",
"New": "631b6e3f-dff0-4b16-951f-b6484e656a29",
"Old": null
},
{
"Name": "DeviceEnrollmentType",
"New": "31",
"Old": null
},
{
"Name": "Thumbprint",
"New": "1ED5FB12AE659D662A14BEA196ACF2AD948FACF2",
"Old": null
}
],
"Name": null
}
],
"object_ids": [
"1ED5FB12AE659D662A14BEA196ACF2AD948FACF2"
]
},
"tenant_id": "f30e4506-34b7-44d4-b333-bdddeca23c30"
}
}
}
{
"message": "{\"time\":\"2022-11-02T15:50:50.9419000Z\",\"tenantId\":\"163381f4-6b9c-43c2-8b57-bfc16b7354f2\",\"category\":\"DeviceComplianceOrg\",\"operationName\":\"DeviceCompliance\",\"resultType\":\"None\",\"properties\":{\"DeviceName\":\"DESKTOP-086N6KI\",\"UPN\":\"Pipin.Saquet@theShire.com\",\"ComplianceState\":\"1\",\"ComplianceState_loc\":\"Compliant\",\"OSDescription\":\"Windows\",\"OSVersion\":\"10.0.19044.2130\",\"OS\":\"Windows\",\"OS_loc\":\"Windows\",\"OwnerType\":1,\"OwnerType_loc\":\"Company\",\"DeviceId\":\"06334044-1a53-47d6-b6f8-ec9dcba8fa93\",\"LastContact\":\"2022-10-28 08:27:37.0000000\",\"UserId\":\"41ab6092-2435-4ed0-a28b-d638523d096e\",\"IMEI\":\"\",\"SerialNumber\":\"5CG21492VW\",\"RetireAfterDatetime\":\"\",\"ManagementAgents\":2,\"ManagementAgents_loc\":\"MDM\",\"DeviceType\":1,\"UserName\":\"Saquet Pipin\",\"InGracePeriodUntil\":\"9999-12-31 23:59:59.0000000\",\"DeviceHealthThreatLevel\":null,\"DeviceHealthThreatLevel_loc\":\"Unknown\",\"UserEmail\":\"Pipin.Saquet@theShire.com\",\"BatchId\":\"9ed4cac5-3d86-4760-980d-f1331dfc5ee9\",\"IntuneAccountId\":\"2b9f48a7-75d9-4a72-9b2e-16fd38e121ef\",\"AADTenantId\":\"163381f4-6b9c-43c2-8b57-bfc16b7354f2\"}}",
"event": {
"type": [
"info"
]
},
"@timestamp": "2022-11-02T15:50:50.941900Z",
"action": {
"name": "DeviceCompliance",
"target": "user",
"type": "DeviceComplianceOrg"
},
"host": {
"id": "06334044-1a53-47d6-b6f8-ec9dcba8fa93",
"name": "DESKTOP-086N6KI",
"os": {
"full": "Windows",
"version": "10.0.19044.2130"
}
},
"microsoft": {
"intune": {
"tenant_id": "163381f4-6b9c-43c2-8b57-bfc16b7354f2"
}
},
"related": {
"user": [
"Saquet Pipin"
]
},
"user": {
"email": "Pipin.Saquet@theShire.com",
"id": "2b9f48a7-75d9-4a72-9b2e-16fd38e121ef",
"name": "Saquet Pipin"
}
}
{
"message": "{\"time\":\"2022-11-17T07:39:02.4103000Z\",\"tenantId\":\"163381f4-6b9c-43c2-8b57-bfc16b7354f2\",\"category\":\"Devices\",\"operationName\":\"Devices\",\"resultType\":\"None\",\"properties\":{\"DeviceId\":\"a2f25343-1d87-4876-9e72-de6111b614e5\",\"DeviceName\":\"Pipin.Saquet_AndroidForWork_10/17/2022_2:23 PM\",\"UPN\":\"Pipin.Saquet@theShire.com\",\"LastContact\":\"2022-11-17 07:03:14.6829201\",\"OSVersion\":\"12.0\",\"OS\":\"Android (Personally-Owned Work Profile)\",\"CompliantState\":\"Compliant\",\"Ownership\":\"Personal\",\"ManagedBy\":\"Intune\",\"Model\":\"SM-G996B\",\"SerialNumber\":\"0\",\"Manufacturer\":\"samsung\",\"CreatedDate\":\"2022-10-17 14:23:27.0091131\",\"DeviceState\":\"Managed\",\"UserEmail\":\"Pipin.Saquet@theShire.com\",\"UserName\":\"Pipin.Saquet\",\"IMEI\":\"88888\",\"PhoneNumber\":\"+*******0016\",\"DeviceRegistrationState\":\"Registered\",\"ReferenceId\":\"5f02959f-d014-4f53-a1be-892a7e7dd450\",\"ManagedDeviceName\":\"Pipin.Saquet_AndroidForWork_10/17/2022_2:23 PM\",\"GraphDeviceIsManaged\":true,\"CategoryName\":\"\",\"EncryptionStatusString\":\"True\",\"SubscriberCarrierNetwork\":\"Orange F\",\"JoinType\":\"Azure AD registered\",\"SupervisedStatusString\":\"False\",\"WifiMacAddress\":\"aaa:ffff\",\"StorageTotal\":0,\"StorageFree\":0,\"AndroidPatchLevel\":\"2022-10-01\",\"MEID\":\"\",\"InGracePeriodUntil\":\"9999-12-31 23:59:59.9999999\",\"JailBroken\":\"false\",\"SkuFamily\":\"\",\"EasID\":\"afw72216560A482C5F77A4E4A9E38E58\",\"PrimaryUser\":\"a7b9fde1-d8d5-438b-9516-7ef639dfe244\",\"BatchId\":\"3068a7ce-6e3a-438f-a943-634dd1412bc5\",\"IntuneAccountId\":\"2b9f48a7-75d9-4a72-9b2e-16fd38e121ef\",\"AADTenantId\":\"163381f4-6b9c-43c2-8b57-bfc16b7354f2\"}}",
"event": {
"type": [
"info"
]
},
"@timestamp": "2022-11-17T07:39:02.410300Z",
"action": {
"name": "Devices",
"target": "user",
"type": "Devices"
},
"host": {
"id": "a2f25343-1d87-4876-9e72-de6111b614e5",
"mac": [
"aaa:ffff"
],
"name": "Pipin.Saquet_AndroidForWork_10/17/2022_2:23 PM",
"os": {
"full": "Android (Personally-Owned Work Profile)",
"version": "12.0"
},
"type": "SM-G996B"
},
"microsoft": {
"intune": {
"compliant_state": "Compliant",
"tenant_id": "163381f4-6b9c-43c2-8b57-bfc16b7354f2"
}
},
"related": {
"user": [
"Pipin.Saquet"
]
},
"service": {
"name": "Intune"
},
"source": {
"mac": "aaa:ffff"
},
"user": {
"email": "Pipin.Saquet@theShire.com",
"id": "2b9f48a7-75d9-4a72-9b2e-16fd38e121ef",
"name": "Pipin.Saquet"
}
}
{
"message": "{\"time\":\"2025-08-04T12:16:24.0714000Z\",\"tenantId\":\"f30e4506-34b7-44d4-b333-bdddeca23c30\",\"category\":\"OperationalLogs\",\"operationName\":\"Enrollment\",\"resultType\":\"Success\",\"properties\":{\"AADDeviceId\":\"3cb66e38-5a5d-4a85-9944-e9c7e9da6bc9\",\"IntuneDeviceId\":\"6bf91e32-ee7b-454a-866a-76941550cced\",\"IntuneAccountId\":\"11111111-1111-1111-1111-111111111111\",\"IntuneUserId\":\"00000000-0000-0000-0000-000000000000\",\"MessageId\":\"e45b735a-8793-4e37-8e0f-a1ee14e38940\",\"AADTenantId\":\"f30e4506-34b7-44d4-b333-bdddeca23c30\",\"OperationalLogCategory\":\"DeviceEnrollment\",\"EnrollmentTimeUTC\":\"2025-08-04T12:16:24.0714Z\",\"ScenarioName\":\"Microsoft.Management.Services.Diagnostics.SLAEvents.EnrollmentSLAEvent\",\"OsVersion\":\"10.0.17763.0\",\"ScaleUnit\":\"AMSUB0101\",\"Os\":\"Windows\",\"EnrollmentType\":\"Unknown\",\"FailureReason\":\"Unknown\",\"FailureCategory\":\"Not Applicable\"}}",
"event": {
"type": [
"info"
]
},
"@timestamp": "2025-08-04T12:16:24.071400Z",
"action": {
"name": "Enrollment",
"target": "user",
"type": "OperationalLogs"
},
"host": {
"id": "6bf91e32-ee7b-454a-866a-76941550cced",
"os": {
"full": "Windows",
"version": "10.0.17763.0"
}
},
"microsoft": {
"intune": {
"tenant_id": "f30e4506-34b7-44d4-b333-bdddeca23c30"
}
},
"user": {
"id": "11111111-1111-1111-1111-111111111111"
}
}
{
"message": "{\"time\":\"2022-11-18T09:04:24.7065000Z\",\"tenantId\":\"163381f4-6b9c-43c2-8b57-bfc16b7354f2\",\"category\":\"OperationalLogs\",\"operationName\":\"Compliance\",\"resultType\":\"None\",\"properties\":{\"IntuneAccountId\":\"2b9f48a7-75d9-4a72-9b2e-16fd38e121ef\",\"AlertDisplayName\":\"Managed Device Pipin.Saquet_Windows_10/4/2022_12:43 PM is not Compliant\",\"AlertType\":\"Managed Device Not Compliant\",\"AADTenantId\":\"163381f4-6b9c-43c2-8b57-bfc16b7354f2\",\"Description\":\"Windows10CompliancePolicy.AntivirusRequired_IID_aae45eb0-5edb-fc0b-7adf-47a5d6b12208||||Windows10CompliancePolicy.AntivirusRequired||Equals 0||2||./Vendor/MSFT/DeviceStatus/Antivirus/Status\",\"DeviceDnsDomain\":\"\",\"DeviceHostName\":\"TheShire-W744\",\"IntuneDeviceId\":\"45241578-2168-4649-9edc-2e9025b699ac\",\"DeviceName\":\"Pipin.Saquet_Windows_10/4/2022_12:43 PM\",\"DeviceNetBiosName\":\"TheShire-W744\",\"DeviceOperatingSystem\":\"Windows 10.0.19044.2251\",\"ScaleUnit\":\"AMSUB0502\",\"ScenarioName\":\"Microsoft.Management.Services.Diagnostics.SLAEvents.DeviceNotInComplianceSecurityAlert\",\"StartTimeUtc\":\"2022-11-18T09:04:24.7065Z\",\"UserName\":\"Pipin.Saquet\",\"UPNSuffix\":\"TheShire.com\",\"UserDisplayName\":\"Saquet Saquet\",\"IntuneUserId\":\"7d5c7f0f-8740-4e9d-96a9-5c2d4baf1d70\",\"OperationalLogCategory\":\"DeviceCompliance\"}}",
"event": {
"reason": "Windows10CompliancePolicy.AntivirusRequired_IID_aae45eb0-5edb-fc0b-7adf-47a5d6b12208||||Windows10CompliancePolicy.AntivirusRequired||Equals 0||2||./Vendor/MSFT/DeviceStatus/Antivirus/Status",
"type": [
"info"
]
},
"@timestamp": "2022-11-18T09:04:24.706500Z",
"action": {
"name": "Compliance",
"target": "user",
"type": "OperationalLogs"
},
"host": {
"id": "45241578-2168-4649-9edc-2e9025b699ac",
"name": "TheShire-W744",
"os": {
"full": "Windows 10.0.19044.2251",
"version": "10.0.19044.2251"
}
},
"microsoft": {
"intune": {
"tenant_id": "163381f4-6b9c-43c2-8b57-bfc16b7354f2"
}
},
"related": {
"user": [
"Pipin.Saquet"
]
},
"user": {
"domain": "TheShire.com",
"full_name": "Saquet Saquet",
"id": "2b9f48a7-75d9-4a72-9b2e-16fd38e121ef",
"name": "Pipin.Saquet"
}
}
{
"message": "{\"time\":\"2025-08-04T12:27:18.7592000Z\",\"tenantId\":\"f30e4506-34b7-44d4-b333-bdddeca23c30\",\"category\":\"AuditLogs\",\"operationName\":\"SetReference ManagedDevice\",\"properties\":{\"ActivityDate\":\"8/4/2025 12:27:18 PM\",\"ActivityResultStatus\":1,\"ActivityType\":4,\"Actor\":{\"ActorType\":5,\"Application\":\"e2872b38-adf3-4d8a-9c10-c5fbd565e4d6\",\"ApplicationName\":\"DeviceChassisInfo\",\"IsDelegatedAdmin\":false,\"Name\":null,\"ObjectId\":null,\"PartnerTenantId\":\"00000000-0000-0000-0000-000000000000\",\"UserPermissions\":[\"DeviceManagementManagedDevices.ReadWrite.All DeviceManagementConfiguration.ReadWrite.All\"],\"UPN\":null},\"AdditionalDetails\":\"\",\"AuditEventId\":\"5264c630-a1fb-46cf-b2a8-c72daf04d855\",\"Category\":4,\"RelationId\":null,\"TargetDisplayNames\":[\"<null>\"],\"TargetObjectIds\":[\"5ef4a298-6273-4398-9367-0725705583e8\"],\"Targets\":[{\"ModifiedProperties\":[{\"Name\":\"referenceProperty\",\"Old\":null,\"New\":\"DeviceCategory\"},{\"Name\":\"referenceValue\",\"Old\":null,\"New\":\"67c0a48b-6755-496b-84e9-4e7603037c5d\"},{\"Name\":\"DeviceManagementAPIVersion\",\"Old\":null,\"New\":\"5025-05-19\"}],\"Name\":null}]},\"resultType\":\"Success\",\"resultDescription\":\"None\",\"correlationId\":\"0a67d96e-5422-4126-be0b-f4d217736211\",\"identity\":\"See Actor details in properties\"}",
"event": {
"type": [
"info"
]
},
"@timestamp": "2025-08-04T12:27:18.759200Z",
"action": {
"name": "SetReference ManagedDevice",
"target": "user",
"type": "AuditLogs"
},
"microsoft": {
"intune": {
"correlation_id": "0a67d96e-5422-4126-be0b-f4d217736211",
"target": {
"display_names": [
"<null>"
],
"modified_properties": [
{
"ModifiedProperties": [
{
"Name": "referenceProperty",
"New": "DeviceCategory",
"Old": null
},
{
"Name": "referenceValue",
"New": "67c0a48b-6755-496b-84e9-4e7603037c5d",
"Old": null
},
{
"Name": "DeviceManagementAPIVersion",
"New": "5025-05-19",
"Old": null
}
],
"Name": null
}
],
"object_ids": [
"5ef4a298-6273-4398-9367-0725705583e8"
]
},
"tenant_id": "f30e4506-34b7-44d4-b333-bdddeca23c30"
}
},
"network": {
"application": "DeviceChassisInfo"
},
"user": {
"roles": [
"DeviceManagementManagedDevices.ReadWrite.All DeviceManagementConfiguration.ReadWrite.All"
]
}
}
Extracted Fields
The following table lists the fields that are extracted, normalized under the ECS format, analyzed and indexed by the parser. It should be noted that infered fields are not listed.
| Name | Type | Description |
|---|---|---|
@timestamp |
date |
Date/time when the event originated. |
action.name |
keyword |
The name of the action |
action.target |
keyword |
The target of the action |
event.reason |
keyword |
Reason why this event happened, according to the source |
event.type |
keyword |
Event type. The third categorization field in the hierarchy. |
host.id |
keyword |
Unique host id. |
host.mac |
keyword |
Host MAC addresses. |
host.name |
keyword |
Name of the host. |
host.os.full |
keyword |
Operating system name, including the version or code name. |
host.os.version |
keyword |
Operating system version as a raw string. |
host.type |
keyword |
Type of host. |
microsoft.intune.compliant_state |
keyword |
Intune compliant status |
microsoft.intune.correlation_id |
keyword |
The correlation ID of the Intune event |
microsoft.intune.target.display_names |
array |
The display name of the Intune target |
microsoft.intune.target.modified_properties |
array |
The modified properties of the Intune target |
microsoft.intune.target.object_ids |
array |
The object IDs of the Intune target |
microsoft.intune.tenant_id |
keyword |
The tenant ID of the Intune event |
network.application |
keyword |
Application level protocol name. |
service.name |
keyword |
Name of the service. |
source.ip |
ip |
IP address of the source. |
source.mac |
keyword |
MAC address of the source. |
user.domain |
keyword |
Name of the directory the user is a member of. |
user.email |
keyword |
User email address. |
user.full_name |
keyword |
User's full name, if available. |
user.id |
keyword |
Unique identifier of the user. |
user.name |
keyword |
Short name or login of the user. |
user.roles |
keyword |
Array of user roles at the time of the event. |
For more information on the Intake Format, please find the code of the Parser, Smart Descriptions, and Supported Events here.