Microsoft Entra ID (Azure AD)
Overview
**Microsoft Entra ID (Azure AD) ** is a cloud-based Identity and Rights management service. The service is developed and managed by Microsoft Corp.
- Vendor: Microsoft
- Supported environment: SaaS
- Detection based on: Telemetry
- Supported application or feature: Application logs, Authentication logs
- Supported events:
- User sign-in events
- Non-interactive user sign-in events
- Service principal sign-in events
- Managed identity sign-in events
- Provisioning events
- ADFS sign-in events
- Risky users
- User risk events
- Risky service principals
- Service principal risk events
- Network access traffic logs
- Audit logs
- Enriched Office 365 audit logs
- Microsoft Graph Activity logs
Configure
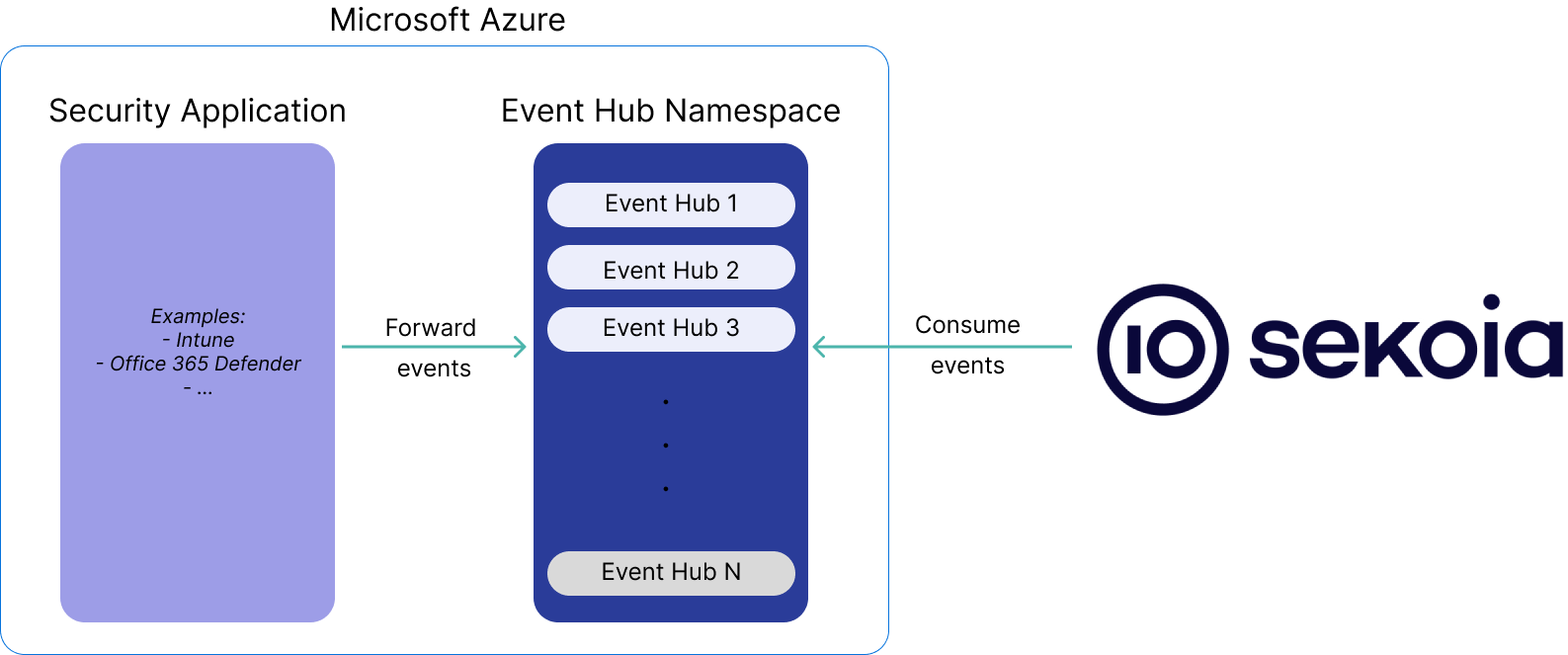
To forward Microsoft Entra ID (Azure AD) ** events from Azure to Sekoia.io you need to send your event to an Azure Event Hub** where Sekoia.io will collect the events.
Prerequisite
You must have Contributor write on Azure to perform the following installation.
Azure Event Hubs is a cloud-based event streaming platform and event ingestion service provided by Microsoft Azure. It is designed to handle large amounts of event data generated by various applications, devices, and services in real-time. Event Hubs enables you to ingest, process, and store events, logs, telemetry data, and other streaming data for further analysis, monitoring, and processing. Two ways are suggested in order to set up everything you need to forward your events on Sekoia.io.
If you are not an expert and want an easy way to configure the ressources on Azure, we recommend to use to Automatic way as it is easier to set up.
These two ways will create an Azure Event Hub and a Storage Account.
** Use the template to create the ressources**
To get started, click on the button below and fill the form on Azure to set up the required environment for Sekoia
Some fields must be filled in.
Project details
- Subscription: select the Azure subscription you want to use
- Resource Group: select or create a new Resource Group. A Resource Group is a container that holds related resources
Instance details
- Region: select the appropriated region
- Project Name: give a name for this project. Here is how the names of the resources will be affected by this project name
| Ressource | Name |
|---|---|
| Event Hub Namespace | <project_name>ehns |
| Event Hub | <project_name>eh |
| Shared Access Policy | <project_name>ap |
| Consumer Group | <project_name>cp |
| Storage Account | <project_name>sa |
- Event Hub Sku: Select the messaging tier for Event Hub Namespace between
Basic,StandardorPremium. We do not recommendBasicmodel due to its limitation. Please follow this Microsoft web page to get more information avec the different messaging tier. - Troughput Unit: A unit gives you up to 1 MB/s or 1,000 events per second (whichever comes first) per Event Hub Namespace. Please adapt it to your need.
- Enable Auto Inflate: When checked, the Auto-inflate feature of Event Hubs automatically scales up by increasing the number of troughput units, to meet usage needs.
- Auto Inflate Maximum Throughput Unit: When Enable Auto Inflate is checked, you can specify the maximum throughput units you allow.
- Partition Count: The number of event hub partitions. Microsoft recommends a maximum throughput of 1 MB/s per partition. Unless you plan to add more Event hubs to the Event Hub Namespace, the Partition Count and Throughput Unit variables should have the same values.
- Retention Time: How long you will keep events in the Event hub in days.
** Use the output variables to create a Sekoia playbook**
When the message Your deployment is complete is displayed, click on Outputs.

Keep these 5 pieces of information displayed carefully, it will used to configure the Trigger Configuration of the Sekoia playbook.
Overview
This setup guide will show you how to create an Event Hub manually.
Theses changes have to be made from the Azure Web Portal.
Some resources created during this procedure are needed to connect Sekoia.io to the Event Hub, you can complete the following table to save all the useful informations for later use.
| Name | Value | Description | Example |
|---|---|---|---|
| hub_name | To be completed at step 3 | Name of the Event Hub | sekoia_event_hub |
| hub_connection_string | To be completed at step 5 | Connection string–primary key | Endpoint=sb://company-eventhub.servicebus.windows.net/;SharedAccessKeyName=sekoiaio;SharedAccessKey=XXXXXX;EntityPath=sekoia_event_hub |
| hub_consumer_group | To be completed at step 6 | Name of the comsumer group | consumergroup_sekoiaio |
| storage_container_name | To be completed at step 7 | Name of your container | sekoiaio |
| storage_connection_string | To be completed at step 8 | Storage connection string | DefaultEndpointsProtocol=https;AccountName=sekoiaiocheckpoint;AccountKey=XXXXX |
As a prerequisite, you need to choose an existing Resource group, or create a new one (e.g. company-resource-group).
Step 1: Find your Subscription ID
- Go to: Home > Cost Management + Billing > Subscriptions.
- From there, keep the relevant “Subscription ID” that will be used along the process.

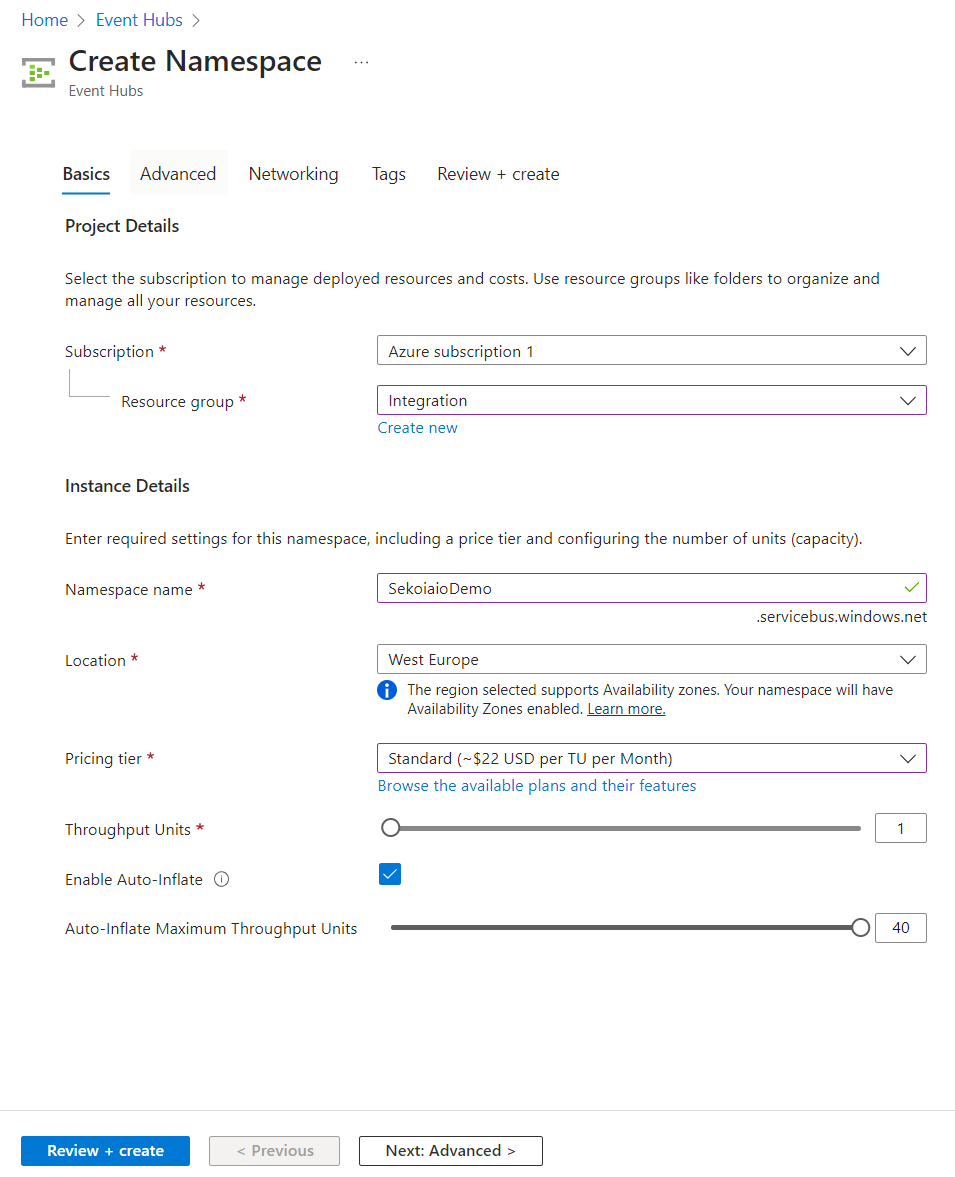
Step 2: Create Event Hub Namespace
- Navigate to Home > Event Hubs.
- Create an Event Hub Namespace.
- Select your Subscription and your Resource group. Click on create new if you want your Event Hub Namespace in a new Resource group.
- Choose a namespace name.
- Select a location based on your events location.
- Select the pricing tier plan based on your utilisation: Standard or Premimum (We don't recommend to choose the Basic plan due to its limitations.)
- Select the throughput units number based on your events, or enable the auto inflate mode:
1 throughput unit can process up to 1 MB per second or 1000 events per second (whichever comes first).
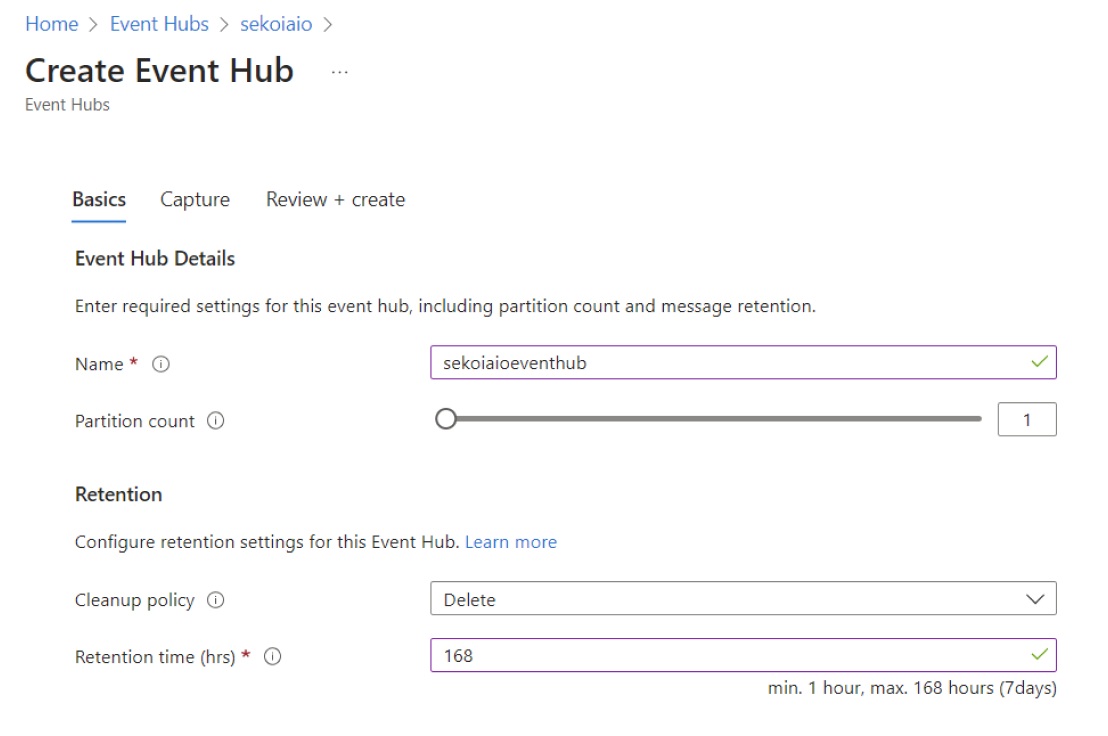
Step 3: Create Event Hub Instance
When your Event Hub Namespace is created you can create an Event Hub inside:
- Navigate to Home > Event Hubs > company-eventhubnamespace.
- Create an Event Hub.
- Select 4 as default partition count
- Select
Deleteas cleanup policy - Type 168h (7 days) as retention time
- Click
Create
Info
Carefully store the Event Hub name that will be used for sekoia playbook configuration.
Step 4: Create “Shared Access Policies” for the Event Hub
- Navigate to Home > Event Hubs > company-eventhubnamespace > eventhubname | Shared access policies.
-
Create a policy (e.g.
sekoiaio) with the claimsListen.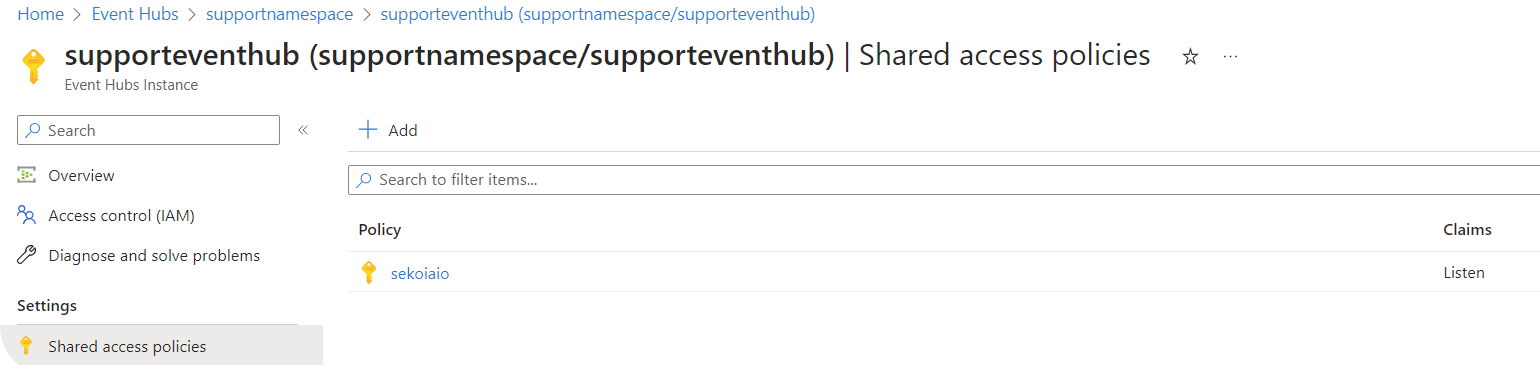
-
Once created, click on the policy.
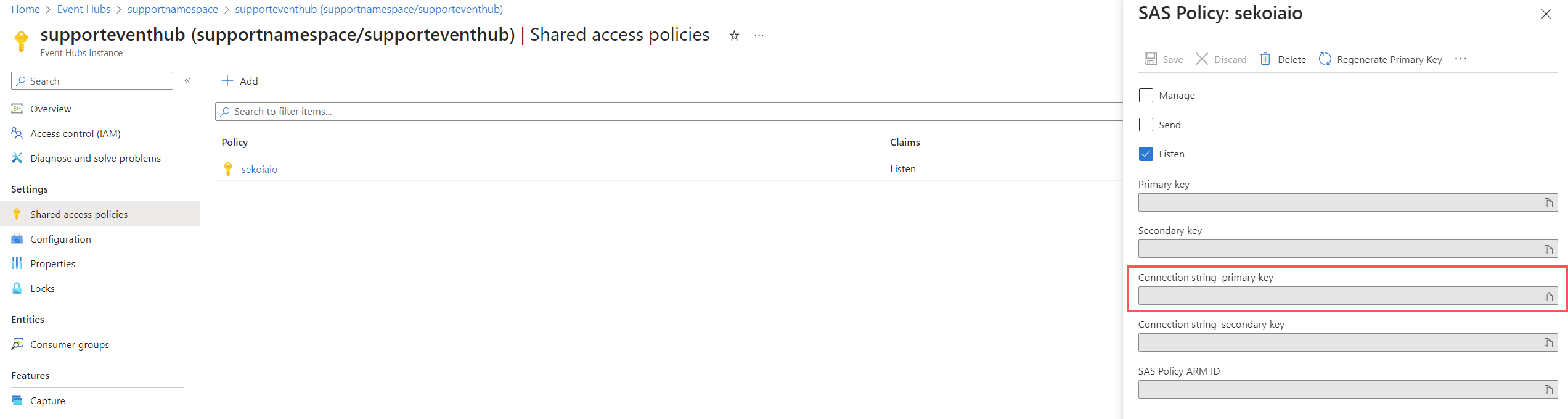
Info
Carefully store the connection string–primary key that will be used for sekoia playbook configuration.
Step 5: Create a Consumer group
- Navigate to Home > Event Hubs > company-eventhubnamespace > eventhubname | Consumer groups.
- Create a Consumer group (e.g.
consumergroup_sekoiaio).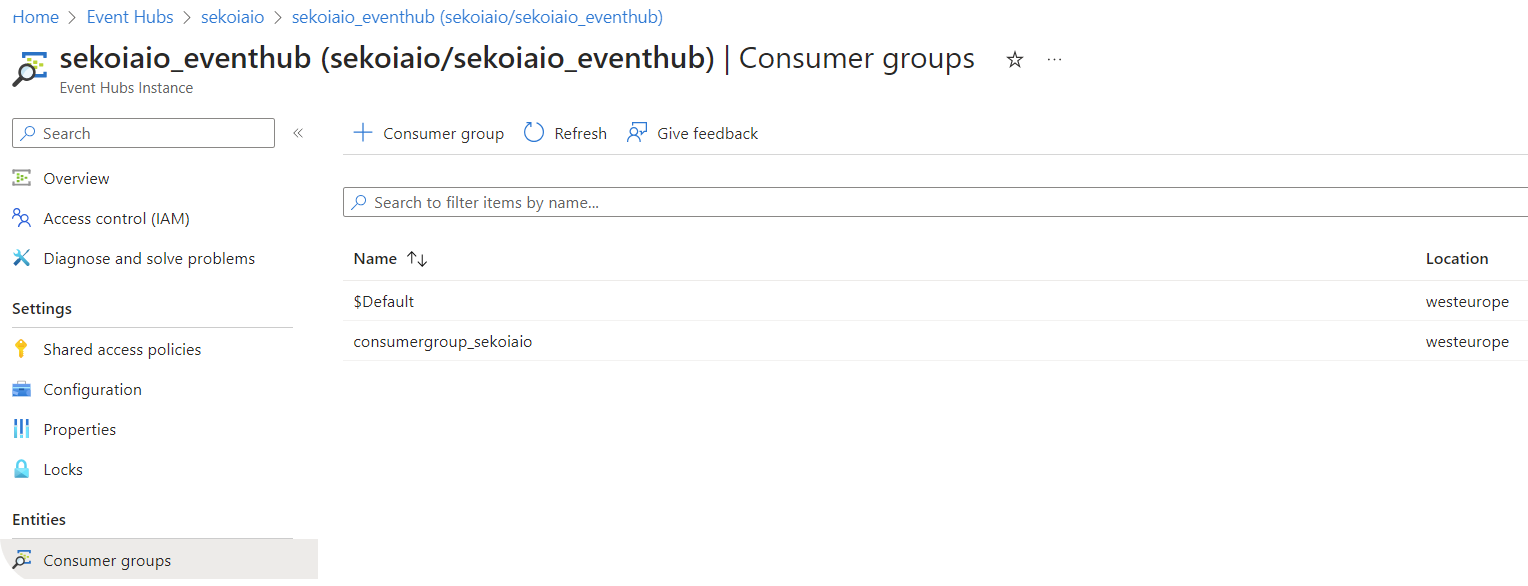
Info
Carefully store the Consumer group name that will be used for sekoia playbook configuration.
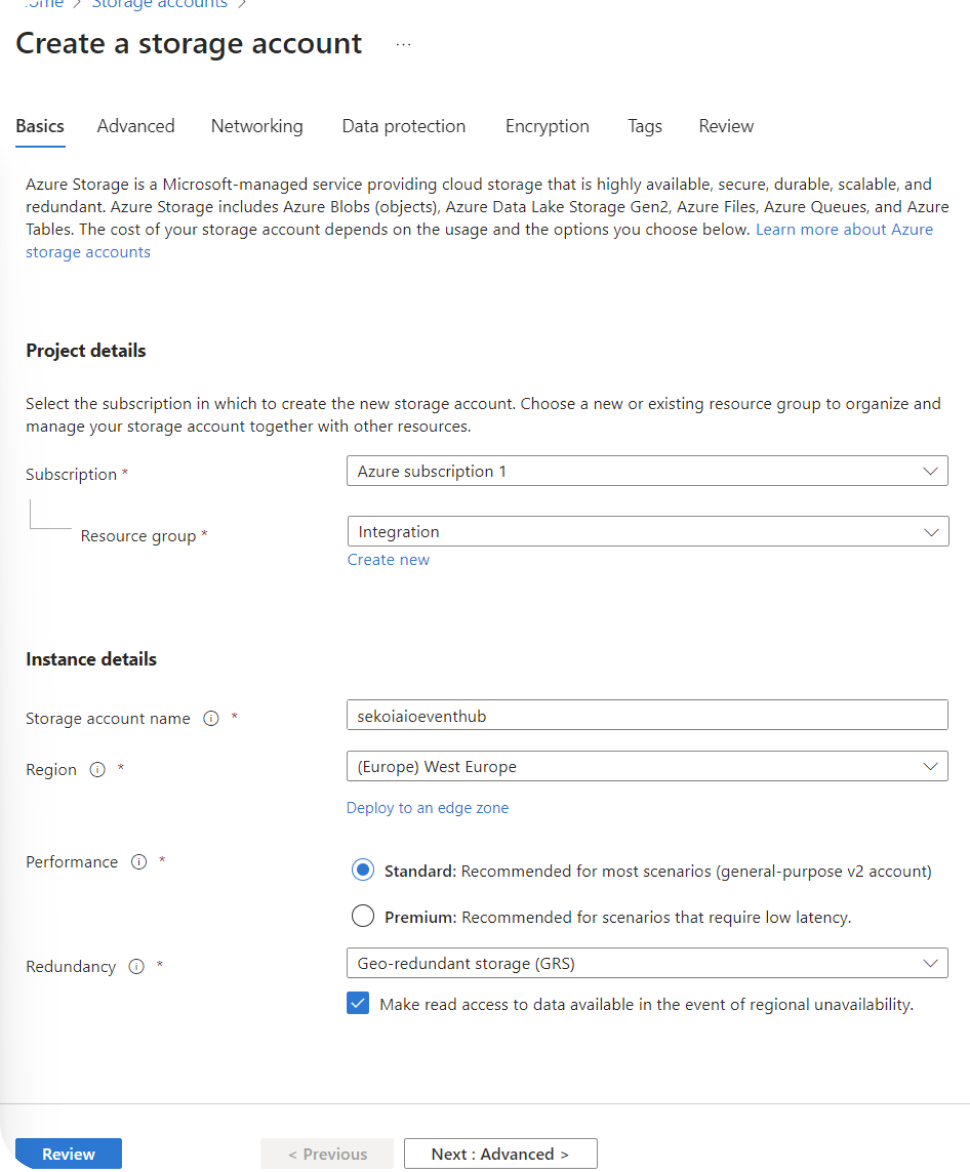
Step 6: Create a Storage Account with a container
In order to allow Sekoia.io keep track of the consumed events, the next step consists in creating a dedicated Storage account.
- Navigate to Home > Storage accounts.
- Create a Storage account.
- Select your Subscription and your Resource group.
- Choose a Storage account name.
-
Select a Region.
Info
You must choose the Region used during the Event Hub Namespace creation.
-
Select your perfomance and redundancy parameters.
Info
We advise at least the following values: - performance: standard - redundancy: Geo-Redundancy storage (GRS)
When your storage account is created you can create an container inside. 1. Navigate to Home > Storage accounts > storageaccoutname | containers. 2. Create an container.
Keep the Public Acces Level to Private.
Info
The container name should be the same as the Event Hub name. Carefully store that container name that will be used for sekoia playbook configuration.
Step 7: Retrieve Connection String
You have to retrieve the connection string from Azure Web Portal.
- Go to Home > Storage accounts > storageaccoutname | Access Keys.
- Click on "Show Keys" on the first Connection String.
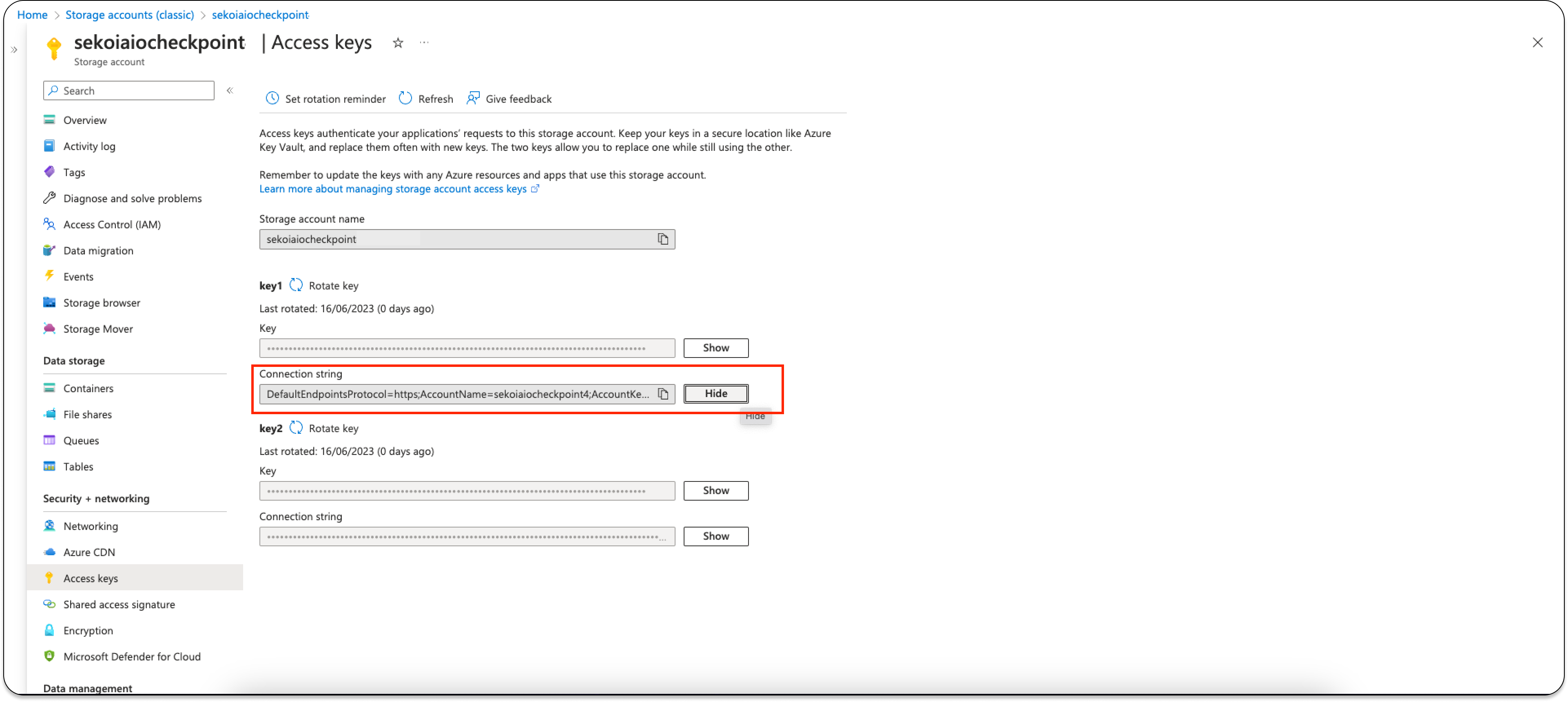
Info
Carefully store the Connection String that will be used for sekoia playbook configuration.
Further Readings
Send logs from Microsoft Entra ID (Azure AD) to Azure Event Hub
When you have an Event Hub follow this guide to send your Microsoft Entra ID (Azure AD) ** events from Azure to the Event Hub**:
You need to activate and configure the Microsoft Entra ID (Azure AD) ** diagnostic settings (e.g. company-ad),
to receive logs from the Microsoft Entra ID (Azure AD) ** into your Event Hub.
Navigate to Home > Microsoft Entra ID (Azure AD) (e.g. company-ad) > Monitoring > Diagnostic settings:
- Add a new diagnostic setting, and select “Stream to an event hub” and click on configure.
- Select the previously created “Event hubs”, “Event Hub” and “SharedAccessKey” (see step 3 of the event hub guide).
- In the log section, select all log categories (as shown below).
- Choose a name for this configuration and click on “Save”.
Create your intake
- Go to the intake page and create a new intake from the
Microsoft Entra ID / Azure AD. - To fill the form, use the table completed during the creation of the Event Hub.
Enjoy your events on the Events page
Detection section
The following section provides information for those who wish to learn more about the detection capabilities enabled by collecting this intake. It includes details about the built-in rule catalog, event categories, and ECS fields extracted from raw events. This is essential for users aiming to create custom detection rules, perform hunting activities, or pivot in the events page.
Related Built-in Rules
The following Sekoia.io built-in rules match the intake Microsoft Entra ID / Azure AD. This documentation is updated automatically and is based solely on the fields used by the intake which are checked against our rules. This means that some rules will be listed but might not be relevant with the intake.
SEKOIA.IO x Microsoft Entra ID / Azure AD on ATT&CK Navigator
Burp Suite Tool Detected
Burp Suite is a cybersecurity tool. When used as a proxy service, its purpose is to intercept packets and modify them to send them to the server. Burp Collaborator is a network service that Burp Suite uses to help discover many kinds of vulnerabilities (vulnerabilities scanner).
- Effort: intermediate
CVE-2018-11776 Apache Struts2
Apache Struts versions 2.3 to 2.3.34 and 2.5 to 2.5.16 suffer from possible Remote Code Execution when alwaysSelectFullNamespace is true (either by user or a plugin like Convention Plugin) and then: results are used with no namespace and in same time, its upper package have no or wildcard namespace and similar to results, same possibility when using url tag which doesn't have value and action set and in same time, its upper package have no or wildcard namespace.
- Effort: intermediate
CVE-2018-13379 Fortinet Exploit
Detects the successful exploitation of the Fortinet FortiOS CVE-2018-13379. This CVE is one of the most exploited CVEs since 2018. It is exploited by APT threat actors as well as cybercriminals. The exploitation of this CVE lead an unauthenticated user to get full access to FortiOS system file through SSL VPN via specially crafted HTTP resource requests. The exploit read /dev/cmdb/sslvpn_websession file, that contains login and passwords in (clear/text). An HTTP response status code = 200, means the file was successfully accessed. This vulnerability affects FortiOS 5.6.3 to 5.6.7 and FortiOS 6.0.0 to 6.0.4.
- Effort: advanced
CVE-2019-0604 SharePoint
Detects the exploitation of the SharePoint vulnerability (CVE-2019-0604).
- Effort: advanced
CVE-2019-11510 Pulse Secure Exploit
Detects the successful exploitation of the Pulse Secure vulnerability CVE-2019-11510. This CVE is one of the most exploited CVEs since 2019. It is exploited by diverse threat actors, leading sometimes in ransomware deployement among these groups: Maze, Conti, Egregor, DoppelPaymer, NetWalker and REvil. But also APT actors such as APT29. The exploitation of this CVE allows a remote, unauthenticated attacker to compromise a vulnerable VPN server. The attacker may be able to gain access to all active users and their plain-text credentials. It may also be possible for the attacker to execute arbitrary commands on each VPN client as it successfully connects to the VPN server. The exploit reads /etc/passwd file to get access to login and passwords in (clear/text). An HTTP response status code = 200, means the file was successfully accessed. This vulnerability affects 8.1R15.1, 8.2 before 8.2R12.1, 8.3 before 8.3R7.1, and 9.0 before 9.0R3.4 products.
- Effort: elementary
CVE-2019-19781 Citrix NetScaler (ADC)
Detects CVE-2019-19781 exploitation attempt against Citrix NetScaler (ADC), Application Delivery Controller and Citrix Gateway Attack.
- Effort: elementary
CVE-2019-2725 Oracle Weblogic Exploit
Detects the successful exploitation of a deserialization vulnerability in Oracle Weblogic Server, CVE-2019-2725. This vulnerability affects versions 10.X and 12.1.3 of WebLogic that have the components wls9_async_response.war and wls-wsat.war enabled. It is a remote code execution which can be exploited without authentication via HTTP. An HTTP response status code = 202, means the target is vulnerable, the analyst then has to look in depth to check if a webshell has been uploaded or something else has been done.
- Effort: elementary
CVE-2020-0688 Microsoft Exchange Server Exploit
Detects the exploitation of CVE-2020-0688. The POC exploit a .NET serialization vulnerability in the Exchange Control Panel (ECP) web page. The vulnerability is due to Microsoft Exchange Server not randomizing the keys on a per-installation basis resulting in them using the same validationKey and decryptionKey values. With knowledge of these, values an attacker can craft a special viewstate to use an OS command to be executed by NT_AUTHORITY\SYSTEM using .NET deserialization. To exploit this vulnerability, an attacker needs to leverage the credentials of an account it had already compromised to authenticate to OWA.
- Effort: elementary
CVE-2020-1147 SharePoint
Detection of SharePoint vulnerability CVE-2020-1147.
- Effort: advanced
CVE-2020-14882 Oracle WebLogic Server
Detects the exploitation of the Oracle WebLogic Server vulnerability (CVE-2020-16952).
- Effort: advanced
CVE-2020-17530 Apache Struts RCE
Detects the exploitation of the Apache Struts RCE vulnerability (CVE-2020-17530).
- Effort: intermediate
CVE-2020-5902 F5 BIG-IP Exploitation Attempts
Detects the exploitation attempt of the vulnerability found in F5 BIG-IP and described in CVE-2020-5902.
- Effort: elementary
CVE-2021-20021 SonicWall Unauthenticated Administrator Access
Detects the exploitation of SonicWall Unauthenticated Admin Access.
- Effort: advanced
CVE-2021-20023 SonicWall Arbitrary File Read
Detects Arbitrary File Read, which can be used with other vulnerabilities as a mean to obtain outputs generated by attackers, or sensitive data.
- Effort: advanced
CVE-2021-21972 VMware vCenter
The vSphere Client (HTML5) contains a remote code execution vulnerability in a vCenter Server plugin. A malicious actor with network access to port 443 may exploit this issue to execute commands with unrestricted privileges on the underlying operating system that hosts vCenter Server. This affects VMware vCenter Server (7.x before 7.0 U1c, 6.7 before 6.7 U3l and 6.5 before 6.5 U3n) and VMware Cloud Foundation (4.x before 4.2 and 3.x before 3.10.1.2). POST request on the following PATH "/ui/vropspluginui/rest/services/uploadova". If in response body (500) the words it has "uploadFile", that means the vCenter is available to accept files via POST without any restrictions.
- Effort: intermediate
CVE-2021-21985 VMware vCenter
The VMware vSphere Client (HTML5) contains a remote code execution vulnerability due to lack of input validation in the Virtual SAN Health Check plug-in which is enabled by default in vCenter Server. A malicious actor with network access to port 443 may exploit this issue to execute commands with unrestricted privileges on the underlying operating system that hosts vCenter Server. This affects VMware vCenter Server (7.0 before 7.0 U2b, 6.7 before 6.7 U3n and 6.5 before 6.5 U3p) and VMware Cloud Foundation (4.x before 4.2.1 and 3.x before 3.10.2.1).
- Effort: advanced
CVE-2021-22123 Fortinet FortiWeb OS Command Injection
Detects Fortinet FortiWeb OS Command Injection (August 2021) vulnerability exploitation attempt. A remote, authenticated attacker can execute arbitrary commands on the system hosting a vulnerable FortiWeb WAF by sending a POST request with the command in the name field. At the time of writing this rule, it would appear that the request would respond in code 500 for a successful exploitation attempt.
- Effort: advanced
CVE-2021-22893 Pulse Connect Secure RCE Vulnerability
Detects potential exploitation of the authentication by-pass vulnerability that can allow an unauthenticated user to perform remote arbitrary file execution on the Pulse Connect Secure gateway. It is highly recommended to apply the Pulse Secure mitigations and seach for indicators of compromise on affected servers if you are in doubt over the integrity of your Pulse Connect Secure product.
- Effort: intermediate
CVE-2021-26855 Exchange SSRF
Detects the exploitation of ProyxLogon vulerability on Exchange servers.
- Effort: advanced
CVE-2021-34473 ProxyShell Attempt
Detects CVE-2021-34473 ProxyShell attempt against Microsoft Exchange Server, Remote Code Execution Vulnerability.
- Effort: advanced
CVE-2021-41773 Apache 2.4.49 Path Traversal
Detects successful exploitation of the Apache Path Traversal CVE-2021-41773.
- Effort: advanced
CVE-2021-43798 Grafana Directory Traversal
Grafana version 8.x has a 0day arbitrary file read (with no fix yet) based on a directory traversal vulnerability
- Effort: intermediate
Covenant Default HTTP Beaconing
Detects potential Covenant communications through the user-agent and specific urls
- Effort: intermediate
Cryptomining
Detection of domain names potentially related to cryptomining activities.
- Effort: master
Detect requests to Konni C2 servers
This rule detects requests to Konni C2 servers. These patterns come from an analysis done in 2022, September.
- Effort: elementary
Discord Suspicious Download
Discord is a messaging application. It allows users to create their own communities to share messages and attachments. Those attachments have little to no overview and can be downloaded by almost anyone, which has been abused by attackers to host malicious payloads.
- Effort: advanced
Dynamic DNS Contacted
Detect communication with dynamic dns domain. This kind of domain is often used by attackers. This rule can trigger false positive in non-controlled environment because dynamic dns is not always malicious.
- Effort: master
Entra ID Consent Attempt to Suspicious OAuth Application
Detects an attempt to authorize account access to an OAuth application commonly used in business email compromise (BEC) attacks. Investigate the source IP address: unusual countries, RDP hosts and VPN providers are likely indicators of malicious activity.
- Effort: elementary
Entra ID Password Compromised By Known Credential Testing Tool
Detects a sign-in that has a correlation ID known to be used by malicious credential testing scripts. Note that even if the sign-in was blocked by MFA (error 50074) or device authentication (error 50097), these verifications only occur after the correct password was submitted. The account's password must still be considered compromised, and be changed.
- Effort: elementary
Entra ID Sign-In Via Known AiTM Phishing Kit (CEPHAS 2FA)
Detects a sign-in attempt with known characteristics of the adversary-in-the-middle phishing kit CEPHAS 2FA.
- Effort: elementary
Entra ID Sign-In Via Known AiTM Phishing Kit (Gabagool)
Detects a sign-in attempt with known characteristics of the adversary-in-the-middle phishing kit Gabagool. The filter_password_spraying exclusion corresponds to a password spraying tool which is already detected by the rule Entra ID Password Compromised By Known Credential Testing Tool.
- Effort: elementary
Entra ID Sign-In Via Known AiTM Phishing Kit (Greatness)
Detects a sign-in attempt with known characteristics of the adversary-in-the-middle phishing kit Greatness.
- Effort: elementary
Entra ID Sign-In Via Known AiTM Phishing Kit (Mamba 2FA)
Detects a sign-in attempt with known characteristics of the adversary-in-the-middle phishing kit tracked by Sekoia.io as Mamba 2FA.
- Effort: elementary
Entra ID Sign-In Via Known AiTM Phishing Kit (Rockstar 2FA)
Detects a sign-in attempt with known characteristics of the adversary-in-the-middle phishing kit Rockstar 2FA.
- Effort: elementary
Entra ID Sign-In Via Known AiTM Phishing Kit (Sneaky 2FA)
Detects a sign-in attempt with an impossible device shift characteristic of the adversary-in-the-middle phishing kit Sneaky 2FA.
- Effort: elementary
Entra ID Sign-In Via Known AiTM Phishing Kit (Tycoon 2FA)
Detects a sign-in attempt with known characteristics of the adversary-in-the-middle phishing kit Tycoon 2FA.
- Effort: elementary
Exfiltration Domain
Detects traffic toward a domain flagged as a possible exfiltration vector.
- Effort: master
FoggyWeb HTTP Default GET/POST Requests
Detects GET or POST request pattern observed within the first FoggyWeb campaign detected by Microsoft.
- Effort: advanced
GitLab CVE-2021-22205
Detects GitLab vulnerability CVE-2021-22205 exploitation success. It allows an attacker to do some remote code execution with user git. The HTTP return code 422 indicates a successfull exploitation.
- Effort: intermediate
Koadic MSHTML Command
Detects Koadic payload using MSHTML module
- Effort: intermediate
Login Brute-Force Successful On AzureAD From Single IP Address
A user has attempted to login several times (brute-force) on AzureAD and succeeded to login, all from the same source IP address and in a timerange of 5 minutes.
- Effort: advanced
Login Brute-Force Successful On SentinelOne EDR Management Console
A user has attempted to login several times (brute-force) on the SentinelOne EDR Management Console and succeeded to login.
- Effort: master
LokiBot Default C2 URL
Detects default C2 URL for trojan LokiBot
- Effort: elementary
Microsoft Entra ID (Azure AD) Abnormal Token
Detects when Microsoft Entra ID (Azure AD) indicates that there are abnormal characteristics in the token such as an unusual token lifetime or a token that is played from an unfamiliar location. To use this feature, you must have an Microsoft Entra ID (Azure AD) Premium P2 license (https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection).
- Effort: intermediate
Microsoft Entra ID (Azure AD) Anonymous IP
Detects when Microsoft Entra ID (Azure AD) identifies sign-ins from a risky IP address, for example, using an anonymous browser or VPN. To use this feature, you must have an Microsoft Entra ID (Azure AD) Premium P2 license (https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection).
- Effort: advanced
Microsoft Entra ID (Azure AD) Device Code Authentication
Authentication via a device code is designed for use with input constrained devices. This method can however be abused, particularly in social engineering attacks. Whitelisting based on the organisation's practices is likely required to make this rule useful (e.g. excluding the public IP ranges of the organisation, excluding authentications attempt from managed devices, etc.)
- Effort: master
Microsoft Entra ID (Azure AD) Domain Trust Modification
Adversaries may add new domain trusts or modify the properties of existing domain trusts to evade defenses and/or elevate privileges. Confirm the added or modified target domain/URL is legitimate administrator behavior.
- Effort: elementary
Microsoft Entra ID (Azure AD) Impossible Travel
Detects when Microsoft Entra ID (Azure AD) identifies two user activities (a single or multiple sessions) originating from geographically distant locations within a time period shorter than the time it would have taken the user to travel from the first location to the second. To use this feature, you must have an Microsoft Entra ID (Azure AD) Premium P2 license (https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection).
- Effort: master
Microsoft Entra ID (Azure AD) Leaked Credentials
Detects when Microsoft Entra ID (Azure AD) identifies that the user's valid credentials have been leaked. This sharing is typically done by posting publicly on the dark web, paste sites, or by trading and selling the credentials on the black market. To use this feature, you must have an Microsoft Entra ID (Azure AD) Premium P2 license (https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection).
- Effort: master
Microsoft Entra ID (Azure AD) Login Failed Brute-Force From Single IP Address
A user has attempted to login several times (brute-force) on AzureAD and failed every time, all from the same source IP address and in a timerange of 5 minutes.
- Effort: advanced
Microsoft Entra ID (Azure AD) MFA Method Change
This rule detects when an user makes a change to the multifactor authentication methods for their account. In environments where this rule is too noisy, alert filters should be applied, e.g. to focus on privileged accounts, or unusual source network locations.
- Effort: master
Microsoft Entra ID (Azure AD) Malicious IP
Detects when Microsoft Entra ID (Azure AD) identifies a malicious IP address. An IP address is considered malicious based on high failure rates because of invalid credentials received from the IP address or other IP reputation sources. To use this feature, you must have an Microsoft Entra ID (Azure AD) Premium P2 license (https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection).
- Effort: intermediate
Microsoft Entra ID (Azure AD) Password Spray
Detects when Microsoft Entra ID (Azure AD) indicates that multiple usernames are attacked using common passwords in a unified brute force manner to gain unauthorized access. To use this feature, you must have an Microsoft Entra ID (Azure AD) Premium P2 license (https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection).
- Effort: intermediate
Microsoft Entra ID (Azure AD) Sign-in From Unlikely Country
Detects when Microsoft Entra ID (Azure AD) identifies sign-ins originating from geographically distant locations, where at least one of the locations may also be atypical for the user, given past behavior. To use this feature, you must have an Microsoft Entra ID (Azure AD) Premium P2 license (https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection).
- Effort: master
Microsoft Entra ID (Azure AD) Successful Password Spraying From Single IP Address
An IP address performed several failed logins on multiple users to then have a successful login on one of them. Note that even if the sign-in was blocked by MFA (error 50074/50076/50158) or conditional access (error 50097/53003), these verifications only occur after the correct password was submitted. The account's password must still be considered compromised, and be changed.
- Effort: advanced
Microsoft Entra ID (Azure AD) Suspicious Browser
Detects when Microsoft Entra ID (Azure AD) identifies suspicious sign-in activity across multiple tenants from different countries in the same browser. To use this feature, you must have an Microsoft Entra ID (Azure AD) Premium P2 license (https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection).
- Effort: master
Microsoft Entra ID (Azure AD) Suspicious IP
Detects when Microsoft Entra ID (Azure AD) identifies a suspicious IP address. An IP address is considered suspicious based on high failure rates because of invalid credentials received from the IP address or other IP reputation sources. To use this feature, you must have an Microsoft Entra ID (Azure AD) Premium P2 license (https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection).
- Effort: intermediate
Microsoft Entra ID (Azure AD) Suspicious Inbox Forwarding
Detects when Microsoft Entra ID (Azure AD) identifies suspicious email forwarding rules, for example, if a user created an inbox rule that forwards a copy of all emails to an external address. To use this feature, you must have an Microsoft Entra ID (Azure AD) Premium P2 license (https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection).
- Effort: master
Microsoft Entra ID (Azure AD) Threat Intelligence
Detects when Microsoft Entra ID (Azure AD) identifies a sign-in activity that is unusual for the given user or is consistent with known attack patterns based on Microsoft's internal and external threat intelligence sources. To use this feature, you must have an Microsoft Entra ID (Azure AD) Premium P2 license (https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection).
- Effort: intermediate
Microsoft Entra ID (Azure AD) Token Issuer Anomaly
Detects when Microsoft Entra ID (Azure AD) indicates that The SAML token issuer for the associated SAML token is potentially compromised. The claims included in the token are unusual or match known attacker patterns. To use this feature, you must have an Microsoft Entra ID (Azure AD) Premium P2 license (https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection).
- Effort: advanced
Microsoft Entra ID (Azure AD) Unfamiliar Features
Detects when Microsoft Entra ID (Azure AD) identifies sign-ins with characteristics that deviate from past sign-in properties. To use this feature, you must have an Microsoft Entra ID (Azure AD) Premium P2 license (https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection).
- Effort: master
Nimbo-C2 User Agent
Nimbo-C2 Uses an unusual User-Agent format in its implants.
- Effort: intermediate
Password Change Brute-Force On AzureAD
A change of password has failed on Azure Active Directory, 5 times for the same user
- Effort: intermediate
Possible Malicious File Double Extension
Detects request to potential malicious file with double extension
- Effort: elementary
Potential Bazar Loader User-Agents
Detects potential Bazar loader communications through the user-agent
- Effort: elementary
Potential Lemon Duck User-Agent
Detects LemonDuck user agent. The format used two sets of alphabetical characters separated by dashes, for example "User-Agent: Lemon-Duck-[A-Z]-[A-Z]".
- Effort: elementary
Potential LokiBot User-Agent
Detects potential LokiBot communications through the user-agent
- Effort: intermediate
Privilege Escalation Awesome Scripts (PEAS)
Detect PEAS privileges escalation scripts and binaries
- Effort: elementary
ProxyShell Microsoft Exchange Suspicious Paths
Detects suspicious calls to Microsoft Exchange resources, in locations related to webshells observed in campaigns using this vulnerability.
- Effort: elementary
Raccoon Stealer 2.0 Legitimate Third-Party DLL Download URL
Detects Raccoon Stealer 2.0 malware downloading legitimate third-party DLLs from its C2 server. These legitimate DLLs are used by the information stealer to collect data on the compromised hosts.
- Effort: elementary
Remote Access Tool Domain
Detects traffic toward a domain flagged as a Remote Administration Tool (RAT).
- Effort: master
Remote Monitoring and Management Software - AnyDesk
Detect artifacts related to the installation or execution of the Remote Monitoring and Management tool AnyDesk.
- Effort: master
SEKOIA.IO Intelligence Feed
Detect threats based on indicators of compromise (IOCs) collected by SEKOIA's Threat and Detection Research team.
- Effort: elementary
Sekoia.io EICAR Detection
Detects observables in Sekoia.io CTI tagged as EICAR, which are fake samples meant to test detection.
- Effort: master
SharePoint Authenticated SSRF
Detects succesful SSRF from an authenticated SharePoint user.
- Effort: elementary
Sign-In Via Known AiTM Phishing Kit
Detects a sign-in attempt from an IP address belonging to a known adversary-in-the-middle phishing kit.
- Effort: elementary
Suspicious Download Links From Legitimate Services
Detects users clicking on Google docs links to download suspicious files. This technique was used a lot by Bazar Loader in the past.
- Effort: intermediate
Suspicious TOR Gateway
Detects suspicious TOR gateways. Gateways are often used by the victim to pay and decrypt the encrypted files without installing TOR. Tor intercepts the network traffic from one or more apps on user’s computer, usually the user web browser, and shuffles it through a number of randomly-chosen computers before passing it on to its destination. This disguises user location, and makes it harder for servers to pick him/her out on repeat visits, or to tie together separate visits to different sites, this making tracking and surveillance more difficult. Before a network packet starts its journey, user’s computer chooses a random list of relays and repeatedly encrypts the data in multiple layers, like an onion. Each relay knows only enough to strip off the outermost layer of encryption, before passing what’s left on to the next relay in the list.
- Effort: advanced
Suspicious URI Used In A Lazarus Campaign
Detects suspicious requests to a specific URI, usually on an .asp page. The website is often compromised.
- Effort: intermediate
TOR Usage Generic Rule
Detects TOR usage globally, whether the IP is a destination or source. TOR is short for The Onion Router, and it gets its name from how it works. TOR intercepts the network traffic from one or more apps on user’s computer, usually the user web browser, and shuffles it through a number of randomly-chosen computers before passing it on to its destination. This disguises user location, and makes it harder for servers to pick him/her out on repeat visits, or to tie together separate visits to different sites, this making tracking and surveillance more difficult. Before a network packet starts its journey, user’s computer chooses a random list of relays and repeatedly encrypts the data in multiple layers, like an onion. Each relay knows only enough to strip off the outermost layer of encryption, before passing what’s left on to the next relay in the list.
- Effort: master
TrevorC2 HTTP Communication
Detects TrevorC2 HTTP communication based on the HTTP request URI and the user-agent.
- Effort: elementary
Event Categories
The following table lists the data source offered by this integration.
| Data Source | Description |
|---|---|
Application logs |
information on AD activities are collected: domain/user/group creation, password change, token update |
Authentication logs |
Azure AD logs provide details on authentication: status, user, IP address |
In details, the following table denotes the type of events produced by this integration.
| Name | Values |
|---|---|
| Kind | `` |
| Category | authentication |
| Type | connection, start |
Transformed Events Samples after Ingestion
This section demonstrates how the raw logs will be transformed by our parsers. It shows the extracted fields that will be available for use in the built-in detection rules and hunting activities in the events page. Understanding these transformations is essential for analysts to create effective detection mechanisms with custom detection rules and to leverage the full potential of the collected data.
{
"message": "{\"time\": \"2019-06-24T09:21:27.3694184Z\", \"resourceId\": \"/tenants/22222222-2222-2222-2222-222222222222/providers/Microsoft.aadiam\", \"operationName\": \"Add unverified domain\", \"operationVersion\": \"1.0\", \"category\": \"AuditLogs\", \"tenantId\": \"22222222-2222-2222-2222-222222222222\", \"resultSignature\": \"None\", \"durationMs\": 0, \"callerIpAddress\": \"<null>\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"level\": \"Informational\", \"properties\": {\"id\": \"Directory_5P1YA_52883815\", \"category\": \"DirectoryManagement\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"result\": \"success\", \"resultReason\": \"\", \"activityDisplayName\": \"Add unverified domain\", \"activityDateTime\": \"2019-06-24T09:21:27.3694184+00:00\", \"loggedByService\": \"Core Directory\", \"operationType\": \"Add\", \"initiatedBy\": {\"user\": {\"id\": \"user1\", \"displayName\": null, \"userPrincipalName\": \"user1\", \"ipAddress\": \"<null>\"}}, \"targetResources\": [{\"id\": null, \"displayName\": \"examplecorp.onmicrosoft.com\", \"modifiedProperties\": [{\"displayName\": \"Name\", \"oldValue\": \"[\\\"\\\"]\", \"newValue\": \"[\\\"examplecorp.onmicrosoft.com\\\"]\"}, {\"displayName\": \"LiveType\", \"oldValue\": \"[\\\"None\\\"]\", \"newValue\": \"[\\\"Managed\\\"]\"}, {\"displayName\": \"Included Updated Properties\", \"oldValue\": null, \"newValue\": \"\\\"Name,LiveType\\\"\"}]}], \"additionalDetails\": []}}",
"event": {
"action": "Add unverified domain",
"category": [
"iam"
],
"outcome": "success"
},
"@timestamp": "2019-06-24T09:21:27.369418Z",
"action": {
"name": "Add unverified domain",
"outcome": "success",
"properties": [
{
"name": "Name",
"newValue": "[\"examplecorp.onmicrosoft.com\"]",
"oldValue": "[\"\"]"
},
{
"name": "LiveType",
"newValue": "[\"Managed\"]",
"oldValue": "[\"None\"]"
}
],
"target": "user",
"type": "add"
},
"azuread": {
"category": "AuditLogs",
"correlationId": "11111111-1111-1111-1111-111111111111",
"durationMs": 0,
"operationName": "Add unverified domain",
"operationVersion": "1.0",
"properties": {
"correlationId": "11111111-1111-1111-1111-111111111111",
"id": "Directory_5P1YA_52883815"
},
"resourceId": "/tenants/22222222-2222-2222-2222-222222222222/providers/Microsoft.aadiam",
"tenantId": "22222222-2222-2222-2222-222222222222"
},
"related": {
"user": [
"user1"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"user": {
"id": "user1",
"name": "user1"
}
}
{
"message": "{\"category\": \"AuditLogs\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"durationMs\": 0, \"identity\": \"user1\", \"level\": \"Informational\", \"operationName\": \"Add member to group\", \"operationVersion\": \"1.0\", \"properties\": {\"activityDateTime\": \"2020-01-02T13:36:37.9515687+00:00\", \"activityDisplayName\": \"Add member to group\", \"additionalDetails\": [{\"key\": \"User-Agent\", \"value\": \"SkypeSpaces/1.0a$*+\"}], \"category\": \"GroupManagement\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"id\": \"Directory_FI4U8_64698073\", \"initiatedBy\": {\"app\": {\"appId\": null, \"displayName\": \"user1\", \"servicePrincipalId\": \"user1\", \"servicePrincipalName\": null}}, \"loggedByService\": \"Core Directory\", \"operationType\": \"Assign\", \"result\": \"success\", \"resultReason\": \"\", \"targetResources\": [{\"displayName\": null, \"id\": \"user1\", \"modifiedProperties\": [{\"displayName\": \"Group.ObjectID\", \"newValue\": \"\\\"33333333-3333-3333-3333-333333333333\\\"\", \"oldValue\": null}, {\"displayName\": \"Group.DisplayName\", \"newValue\": \"\\\"NEWCORP\\\"\", \"oldValue\": null}, {\"displayName\": \"Group.WellKnownObjectName\", \"newValue\": null, \"oldValue\": null}], \"type\": \"User\", \"userPrincipalName\": \"user1\"}, {\"displayName\": null, \"groupType\": \"azureAD\", \"id\": \"user1\", \"modifiedProperties\": [], \"type\": \"Group\"}]}, \"resourceId\": \"/tenants/22222222-2222-2222-2222-222222222222/providers/Microsoft.aadiam\", \"resultSignature\": \"None\", \"tenantId\": \"22222222-2222-2222-2222-222222222222\", \"time\": \"2020-01-02T13:36:37.9515687Z\"}",
"event": {
"action": "Add member to group",
"category": [
"iam"
],
"outcome": "success"
},
"@timestamp": "2020-01-02T13:36:37.951568Z",
"action": {
"name": "Add member to group",
"outcome": "success",
"properties": [
{
"name": "Group.ObjectID",
"newValue": "\"33333333-3333-3333-3333-333333333333\"",
"oldValue": ""
},
{
"name": "Group.DisplayName",
"newValue": "\"NEWCORP\"",
"oldValue": ""
},
{
"name": "Group.WellKnownObjectName",
"newValue": "",
"oldValue": ""
},
{
"id": "user1",
"name": "user1",
"type": "targetedUser"
}
],
"target": "application",
"type": "assign"
},
"azuread": {
"category": "AuditLogs",
"correlationId": "11111111-1111-1111-1111-111111111111",
"durationMs": 0,
"identity": "user1",
"operationName": "Add member to group",
"operationVersion": "1.0",
"properties": {
"correlationId": "11111111-1111-1111-1111-111111111111",
"id": "Directory_FI4U8_64698073"
},
"resourceId": "/tenants/22222222-2222-2222-2222-222222222222/providers/Microsoft.aadiam",
"tenantId": "22222222-2222-2222-2222-222222222222"
},
"related": {
"user": [
"user1"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"user": {
"changes": {
"group": {
"id": "33333333-3333-3333-3333-333333333333",
"name": "NEWCORP"
}
},
"id": "user1",
"name": "user1",
"target": {
"group": {
"id": "null",
"name": "null"
},
"id": "user1",
"name": "user1"
}
}
}
{
"message": "{\"time\": \"2025-01-29T17:07:02.5863957Z\", \"resourceId\": \"/tenants/22222222-2222-2222-2222-222222222222/providers/Microsoft.aadiam\", \"operationName\": \"Add member to group\", \"operationVersion\": \"1.0\", \"category\": \"AuditLogs\", \"tenantId\": \"22222222-2222-2222-2222-222222222222\", \"resultSignature\": \"None\", \"durationMs\": 0, \"callerIpAddress\": \"1.2.3.4\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"identity\": \"Microsoft Teams Services\", \"Level\": 4, \"properties\": {\"tenantId\": \"33333333-3333-3333-3333-333333333333\", \"resultType\": \"\", \"resultDescription\": \"\", \"operationName\": \"Add member to group\", \"identity\": \"Microsoft Teams Services\", \"tenantGeo\": \"EU\", \"id\": \"Directory_11111111-1111-1111-1111-111111111111_66666_77777777\", \"category\": \"GroupManagement\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"result\": \"success\", \"resultReason\": \"\", \"activityDisplayName\": \"Add member to group\", \"activityDateTime\": \"2025-01-29T17:07:02.5863957+00:00\", \"loggedByService\": \"Core Directory\", \"operationType\": \"Assign\", \"userAgent\": null, \"initiatedBy\": {\"user\": {\"id\": \"user1\", \"displayName\": \"Microsoft Teams Services\", \"userPrincipalName\": \"user1\", \"ipAddress\": \"1.2.3.4\", \"roles\": []}}, \"targetResources\": [{\"id\": \"user1\", \"displayName\": null, \"type\": \"User\", \"userPrincipalName\": \"user1\", \"modifiedProperties\": [{\"displayName\": \"Group.ObjectID\", \"oldValue\": null, \"newValue\": \"\\\"44444444-4444-4444-4444-444444444444\\\"\"}, {\"displayName\": \"Group.DisplayName\", \"oldValue\": null, \"newValue\": \"\\\"PRODUCT Marketing Effectiveness - Test ABC\\\"\"}, {\"displayName\": \"Group.WellKnownObjectName\", \"oldValue\": null, \"newValue\": null}], \"administrativeUnits\": []}, {\"id\": \"user1\", \"displayName\": null, \"type\": \"Group\", \"groupType\": \"unknownFutureValue\", \"modifiedProperties\": [], \"administrativeUnits\": []}], \"additionalDetails\": [{\"key\": \"User-Agent\", \"value\": \"TeamsMiddleTier/1.0a$*+\"}]}}",
"event": {
"action": "Add member to group",
"category": [
"iam"
],
"outcome": "success"
},
"@timestamp": "2025-01-29T17:07:02.586395Z",
"action": {
"name": "Add member to group",
"outcome": "success",
"properties": [
{
"name": "Group.ObjectID",
"newValue": "\"44444444-4444-4444-4444-444444444444\"",
"oldValue": ""
},
{
"name": "Group.DisplayName",
"newValue": "\"PRODUCT Marketing Effectiveness - Test ABC\"",
"oldValue": ""
},
{
"name": "Group.WellKnownObjectName",
"newValue": "",
"oldValue": ""
},
{
"id": "user1",
"name": "user1",
"type": "targetedUser"
}
],
"target": "user",
"type": "assign"
},
"azuread": {
"callerIpAddress": "1.2.3.4",
"category": "AuditLogs",
"correlationId": "11111111-1111-1111-1111-111111111111",
"durationMs": 0,
"identity": "Microsoft Teams Services",
"operationName": "Add member to group",
"operationVersion": "1.0",
"properties": {
"correlationId": "11111111-1111-1111-1111-111111111111",
"id": "Directory_11111111-1111-1111-1111-111111111111_66666_77777777"
},
"resourceId": "/tenants/22222222-2222-2222-2222-222222222222/providers/Microsoft.aadiam",
"tenantId": "22222222-2222-2222-2222-222222222222"
},
"log": {
"level": "4"
},
"related": {
"ip": [
"1.2.3.4"
],
"user": [
"user1"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"source": {
"address": "1.2.3.4",
"ip": "1.2.3.4"
},
"user": {
"changes": {
"group": {
"id": "44444444-4444-4444-4444-444444444444",
"name": "PRODUCT Marketing Effectiveness - Test ABC"
}
},
"id": "user1",
"name": "user1",
"target": {
"group": {
"id": "null",
"name": "null"
},
"id": "user1",
"name": "user1"
}
}
}
{
"message": "{\"time\": \"2019-06-24T09:18:23.5860200Z\", \"resourceId\": \"/tenants/33333333-3333-3333-3333-333333333333/providers/Microsoft.aadiam\", \"operationName\": \"Add service principal\", \"operationVersion\": \"1.0\", \"category\": \"AuditLogs\", \"tenantId\": \"33333333-3333-3333-3333-333333333333\", \"resultSignature\": \"None\", \"resultDescription\": \"Microsoft.Online.Workflows.SpnValidationException\", \"durationMs\": 0, \"callerIpAddress\": \"<null>\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"identity\": \"Microsoft Azure AD Internal - Jit Provisioning\", \"level\": \"Informational\", \"properties\": {\"id\": \"Directory_GMR7H_185505965\", \"category\": \"ApplicationManagement\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"result\": \"failure\", \"resultReason\": \"Microsoft.Online.Workflows.SpnValidationException\", \"activityDisplayName\": \"Add service principal\", \"activityDateTime\": \"2019-06-24T09:18:23.58602+00:00\", \"loggedByService\": \"Core Directory\", \"operationType\": \"Add\", \"initiatedBy\": {}, \"targetResources\": [{\"id\": \"44444444-4444-4444-4444-444444444444\", \"displayName\": \"Azure AD Identity Protection\", \"type\": \"ServicePrincipal\", \"modifiedProperties\": [{\"displayName\": \"AccountEnabled\", \"oldValue\": \"[]\", \"newValue\": \"[true]\"}, {\"displayName\": \"AppAddress\", \"oldValue\": \"[]\", \"newValue\": \"[{\\\"AddressType\\\":0,\\\"Address\\\":\\\"https://main.protectioncenter.ext.azure.com\\\",\\\"ReplyAddressClientType\\\":0},{\\\"AddressType\\\":0,\\\"Address\\\":\\\"https://s2.cloudappdiscovery.ext.azure.com/\\\",\\\"ReplyAddressClientType\\\":0}]\"}, {\"displayName\": \"AppPrincipalId\", \"oldValue\": \"[]\", \"newValue\": \"[\\\"66666666-6666-6666-6666-666666666666\\\"]\"}, {\"displayName\": \"DisplayName\", \"oldValue\": \"[]\", \"newValue\": \"[\\\"Azure AD Identity Protection\\\"]\"}, {\"displayName\": \"ServicePrincipalName\", \"oldValue\": \"[]\", \"newValue\": \"[\\\"https://s2.cloudappdiscovery.ext.azure.com/\\\",\\\"https://main.protectioncenter.ext.azure.com\\\",\\\"66666666-6666-6666-6666-666666666666\\\"]\"}, {\"displayName\": \"Credential\", \"oldValue\": \"[]\", \"newValue\": \"[{\\\"CredentialType\\\":2,\\\"KeyStoreId\\\":\\\"55555555-5555-5555-5555-555555555555\\\",\\\"KeyGroupId\\\":\\\"22222222-2222-2222-2222-222222222222\\\"}]\"}, {\"displayName\": \"Included Updated Properties\", \"oldValue\": null, \"newValue\": \"\\\"AccountEnabled, AppAddress, AppPrincipalId, DisplayName, ServicePrincipalName, Credential\\\"\"}, {\"displayName\": \"MethodExecutionResult.\", \"oldValue\": null, \"newValue\": \"\\\"Microsoft.Online.Workflows.SpnValidationException\\\"\"}, {\"displayName\": \"TargetId.ServicePrincipalNames\", \"oldValue\": null, \"newValue\": \"\\\"https://s2.cloudappdiscovery.ext.azure.com/;https://main.protectioncenter.ext.azure.com;66666666-6666-6666-6666-666666666666\\\"\"}]}], \"additionalDetails\": []}}",
"event": {
"action": "Add service principal",
"category": [
"iam"
],
"outcome": "failure",
"reason": "Microsoft.Online.Workflows.SpnValidationException"
},
"@timestamp": "2019-06-24T09:18:23.586020Z",
"action": {
"name": "Add service principal",
"outcome": "failure",
"outcome_reason": "Microsoft.Online.Workflows.SpnValidationException",
"properties": [
{
"name": "AccountEnabled",
"newValue": "[true]",
"oldValue": "[]"
},
{
"name": "AppAddress",
"newValue": "[{\"AddressType\":0,\"Address\":\"https://main.protectioncenter.ext.azure.com\",\"ReplyAddressClientType\":0},{\"AddressType\":0,\"Address\":\"https://s2.cloudappdiscovery.ext.azure.com/\",\"ReplyAddressClientType\":0}]",
"oldValue": "[]"
},
{
"name": "AppPrincipalId",
"newValue": "[\"66666666-6666-6666-6666-666666666666\"]",
"oldValue": "[]"
},
{
"name": "DisplayName",
"newValue": "[\"Azure AD Identity Protection\"]",
"oldValue": "[]"
},
{
"name": "ServicePrincipalName",
"newValue": "[\"https://s2.cloudappdiscovery.ext.azure.com/\",\"https://main.protectioncenter.ext.azure.com\",\"66666666-6666-6666-6666-666666666666\"]",
"oldValue": "[]"
},
{
"name": "Credential",
"newValue": "[{\"CredentialType\":2,\"KeyStoreId\":\"55555555-5555-5555-5555-555555555555\",\"KeyGroupId\":\"22222222-2222-2222-2222-222222222222\"}]",
"oldValue": "[]"
},
{
"name": "MethodExecutionResult.",
"newValue": "\"Microsoft.Online.Workflows.SpnValidationException\"",
"oldValue": ""
},
{
"name": "TargetId.ServicePrincipalNames",
"newValue": "\"https://s2.cloudappdiscovery.ext.azure.com/;https://main.protectioncenter.ext.azure.com;66666666-6666-6666-6666-666666666666\"",
"oldValue": ""
}
],
"type": "add"
},
"azuread": {
"category": "AuditLogs",
"correlationId": "11111111-1111-1111-1111-111111111111",
"durationMs": 0,
"identity": "Microsoft Azure AD Internal - Jit Provisioning",
"operationName": "Add service principal",
"operationVersion": "1.0",
"properties": {
"correlationId": "11111111-1111-1111-1111-111111111111",
"id": "Directory_GMR7H_185505965",
"targetServicePrincipalDisplayName": "Azure AD Identity Protection"
},
"resourceId": "/tenants/33333333-3333-3333-3333-333333333333/providers/Microsoft.aadiam",
"resultDescription": "Microsoft.Online.Workflows.SpnValidationException",
"tenantId": "33333333-3333-3333-3333-333333333333"
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
}
}
{
"message": "{\"time\": \"2019-06-24T09:29:28.6242725Z\", \"resourceId\": \"/tenants/11111111-1111-1111-1111-111111111111/providers/Microsoft.aadiam\", \"operationName\": \"Add user\", \"operationVersion\": \"1.0\", \"category\": \"AuditLogs\", \"tenantId\": \"11111111-1111-1111-1111-111111111111\", \"resultSignature\": \"None\", \"durationMs\": 0, \"callerIpAddress\": \"<null>\", \"correlationId\": \"22222222-2222-2222-2222-222222222222\", \"level\": \"Informational\", \"properties\": {\"id\": \"Directory_HR9C4_45223131\", \"category\": \"UserManagement\", \"correlationId\": \"22222222-2222-2222-2222-222222222222\", \"result\": \"success\", \"resultReason\": \"\", \"activityDisplayName\": \"Add user\", \"activityDateTime\": \"2019-06-24T09:29:28.6242725+00:00\", \"loggedByService\": \"Core Directory\", \"operationType\": \"Add\", \"initiatedBy\": {\"user\": {\"id\": \"user1\", \"displayName\": null, \"userPrincipalName\": \"user1\", \"ipAddress\": \"<null>\"}}, \"targetResources\": [{\"id\": \"user1\", \"displayName\": null, \"type\": \"User\", \"userPrincipalName\": \"user1\", \"modifiedProperties\": [{\"displayName\": \"AccountEnabled\", \"oldValue\": \"[]\", \"newValue\": \"[true]\"}, {\"displayName\": \"StsRefreshTokensValidFrom\", \"oldValue\": \"[]\", \"newValue\": \"[\\\"2019-06-24T09:29:28Z\\\"]\"}, {\"displayName\": \"UserPrincipalName\", \"oldValue\": \"[]\", \"newValue\": \"[\\\"jean.dupont@usergmail.onmicrosoft.com\\\"]\"}, {\"displayName\": \"UserType\", \"oldValue\": \"[]\", \"newValue\": \"[\\\"Member\\\"]\"}, {\"displayName\": \"Included Updated Properties\", \"oldValue\": null, \"newValue\": \"\\\"AccountEnabled, StsRefreshTokensValidFrom, UserPrincipalName, UserType\\\"\"}]}], \"additionalDetails\": []}}",
"event": {
"action": "Add user",
"category": [
"iam"
],
"outcome": "success"
},
"@timestamp": "2019-06-24T09:29:28.624272Z",
"action": {
"name": "Add user",
"outcome": "success",
"properties": [
{
"name": "AccountEnabled",
"newValue": "[true]",
"oldValue": "[]"
},
{
"name": "StsRefreshTokensValidFrom",
"newValue": "[\"2019-06-24T09:29:28Z\"]",
"oldValue": "[]"
},
{
"name": "UserPrincipalName",
"newValue": "[\"jean.dupont@usergmail.onmicrosoft.com\"]",
"oldValue": "[]"
},
{
"name": "UserType",
"newValue": "[\"Member\"]",
"oldValue": "[]"
},
{
"id": "user1",
"name": "user1",
"type": "targetedUser"
}
],
"target": "user",
"type": "add"
},
"azuread": {
"category": "AuditLogs",
"correlationId": "22222222-2222-2222-2222-222222222222",
"durationMs": 0,
"operationName": "Add user",
"operationVersion": "1.0",
"properties": {
"correlationId": "22222222-2222-2222-2222-222222222222",
"id": "Directory_HR9C4_45223131",
"targetUserPrincipalName": "user1"
},
"resourceId": "/tenants/11111111-1111-1111-1111-111111111111/providers/Microsoft.aadiam",
"tenantId": "11111111-1111-1111-1111-111111111111"
},
"related": {
"user": [
"user1"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"user": {
"id": "user1",
"name": "user1",
"target": {
"id": "user1",
"name": "user1"
}
}
}
{
"message": "{\"time\": \"2025-10-27T10:15:15.8442646Z\", \"resourceId\": \"/tenants/55555555-5555-5555-5555-555555555555/providers/Microsoft.aadiam\", \"operationName\": \"Add app role assignment to service principal\", \"operationVersion\": \"1.0\", \"category\": \"AuditLogs\", \"tenantId\": \"55555555-5555-5555-5555-555555555555\", \"resultSignature\": \"None\", \"durationMs\": 0, \"callerIpAddress\": \"5.6.7.8\", \"correlationId\": \"88888888-8888-8888-8888-888888888888\", \"Level\": 4, \"properties\": {\"tenantId\": \"55555555-5555-5555-5555-555555555555\", \"resultType\": \"\", \"resultDescription\": \"\", \"operationName\": \"Add app role assignment to service principal\", \"identity\": \"\", \"tenantGeo\": \"EU\", \"id\": \"Directory_88888888-8888-8888-8888-888888888888_SAMPLE_123456\", \"category\": \"ApplicationManagement\", \"correlationId\": \"88888888-8888-8888-8888-888888888888\", \"result\": \"success\", \"resultReason\": \"\", \"activityDisplayName\": \"Add app role assignment to service principal\", \"activityDateTime\": \"2025-10-27T10:15:15.8442646+00:00\", \"loggedByService\": \"Core Directory\", \"operationType\": \"Assign\", \"userAgent\": null, \"initiatedBy\": {\"user\": {\"id\": \"66666666-6666-6666-6666-666666666666\", \"displayName\": null, \"userPrincipalName\": \"JDOE-AAD@example.onmicrosoft.com\", \"ipAddress\": \"5.6.7.8\", \"roles\": []}}, \"performedBy\": null, \"targetResources\": [{\"id\": \"88888888-8888-8888-8888-888888888888\", \"displayName\": \"Office 365 Exchange Online\", \"type\": \"ServicePrincipal\", \"modifiedProperties\": [{\"displayName\": \"AppRole.Id\", \"oldValue\": null, \"newValue\": \"\\\"55555555-5555-5555-5555-555555555555\\\"\"}, {\"displayName\": \"AppRole.Value\", \"oldValue\": null, \"newValue\": \"\\\"SMTP.SendAsApp\\\"\"}, {\"displayName\": \"AppRole.DisplayName\", \"oldValue\": null, \"newValue\": \"\\\"Application access for sending emails via SMTP AUTH\\\"\"}, {\"displayName\": \"AppRoleAssignment.CreatedDateTime\", \"oldValue\": null, \"newValue\": \"\\\"2025-10-27T10:15:15.7952638Z\\\"\"}, {\"displayName\": \"AppRoleAssignment.LastModifiedDateTime\", \"oldValue\": null, \"newValue\": \"\\\"2025-10-27T10:15:15.7952638Z\\\"\"}, {\"displayName\": \"ServicePrincipal.ObjectID\", \"oldValue\": null, \"newValue\": \"\\\"66666666-6666-6666-6666-666666666666\\\"\"}, {\"displayName\": \"ServicePrincipal.DisplayName\", \"oldValue\": null, \"newValue\": \"\\\"Apps_Test_SOC\\\"\"}, {\"displayName\": \"ServicePrincipal.AppId\", \"oldValue\": null, \"newValue\": \"\\\"77777777-7777-7777-7777-777777777777\\\"\"}, {\"displayName\": \"ServicePrincipal.Name\", \"oldValue\": null, \"newValue\": \"\\\"77777777-7777-7777-7777-777777777777\\\"\"}, {\"displayName\": \"TargetId.ServicePrincipalNames\", \"oldValue\": null, \"newValue\": \"\\\"https://outlook.office.com;https://ps.outlook.com;https://outlook-tdf-2.office.com/;https://outlook-tdf.office.com/;https://ps.compliance.protection.outlook.com;https://autodiscover-s.office365.us/;https://outlook.office365.us/;https://outlook-sdf.office.com/;https://outlook-sdf.office365.com/;https://outlook.office365.com:443/;https://outlook.office.com/;https://outlook.office365.com/;https://outlook.com/;https://outlook-dod.office365.us/;https://ps.protection.outlook.com/;https://webmail.apps.mil/;Office 365 Exchange Online;Microsoft.Exchange\\\"\"}], \"administrativeUnits\": []}, {\"id\": \"66666666-6666-6666-6666-666666666666\", \"displayName\": \"77777777-7777-7777-7777-777777777777\", \"type\": \"ServicePrincipal\", \"modifiedProperties\": [], \"administrativeUnits\": []}], \"additionalDetails\": [{\"key\": \"User-Agent\", \"value\": \"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/1.2.3.4 Safari/537.36 Edg/1.2.3.4\"}, {\"key\": \"AppId\", \"value\": \"77777777-7777-7777-7777-777777777777\"}]}}",
"event": {
"action": "Add app role assignment to service principal",
"category": [
"iam"
],
"outcome": "success"
},
"@timestamp": "2025-10-27T10:15:15.844264Z",
"action": {
"name": "Add app role assignment to service principal",
"outcome": "success",
"properties": [
{
"name": "AppRole.Id",
"newValue": "\"55555555-5555-5555-5555-555555555555\"",
"oldValue": ""
},
{
"name": "AppRole.Value",
"newValue": "\"SMTP.SendAsApp\"",
"oldValue": ""
},
{
"name": "AppRole.DisplayName",
"newValue": "\"Application access for sending emails via SMTP AUTH\"",
"oldValue": ""
},
{
"name": "AppRoleAssignment.CreatedDateTime",
"newValue": "\"2025-10-27T10:15:15.7952638Z\"",
"oldValue": ""
},
{
"name": "AppRoleAssignment.LastModifiedDateTime",
"newValue": "\"2025-10-27T10:15:15.7952638Z\"",
"oldValue": ""
},
{
"name": "ServicePrincipal.ObjectID",
"newValue": "\"66666666-6666-6666-6666-666666666666\"",
"oldValue": ""
},
{
"name": "ServicePrincipal.DisplayName",
"newValue": "\"Apps_Test_SOC\"",
"oldValue": ""
},
{
"name": "ServicePrincipal.AppId",
"newValue": "\"77777777-7777-7777-7777-777777777777\"",
"oldValue": ""
},
{
"name": "ServicePrincipal.Name",
"newValue": "\"77777777-7777-7777-7777-777777777777\"",
"oldValue": ""
},
{
"name": "TargetId.ServicePrincipalNames",
"newValue": "\"https://outlook.office.com;https://ps.outlook.com;https://outlook-tdf-2.office.com/;https://outlook-tdf.office.com/;https://ps.compliance.protection.outlook.com;https://autodiscover-s.office365.us/;https://outlook.office365.us/;https://outlook-sdf.office.com/;https://outlook-sdf.office365.com/;https://outlook.office365.com:443/;https://outlook.office.com/;https://outlook.office365.com/;https://outlook.com/;https://outlook-dod.office365.us/;https://ps.protection.outlook.com/;https://webmail.apps.mil/;Office 365 Exchange Online;Microsoft.Exchange\"",
"oldValue": ""
}
],
"target": "user",
"type": "assign"
},
"azuread": {
"callerIpAddress": "5.6.7.8",
"category": "AuditLogs",
"correlationId": "88888888-8888-8888-8888-888888888888",
"durationMs": 0,
"operationName": "Add app role assignment to service principal",
"operationVersion": "1.0",
"properties": {
"appId": "77777777-7777-7777-7777-777777777777",
"correlationId": "88888888-8888-8888-8888-888888888888",
"id": "Directory_88888888-8888-8888-8888-888888888888_SAMPLE_123456",
"targetServicePrincipalAppRoleNewDisplayValue": "Application access for sending emails via SMTP AUTH",
"targetServicePrincipalDisplayName": "Office 365 Exchange Online"
},
"resourceId": "/tenants/55555555-5555-5555-5555-555555555555/providers/Microsoft.aadiam",
"tenantId": "55555555-5555-5555-5555-555555555555"
},
"log": {
"level": "4"
},
"related": {
"ip": [
"5.6.7.8"
],
"user": [
"JDOE-AAD@example.onmicrosoft.com"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"source": {
"address": "5.6.7.8",
"ip": "5.6.7.8"
},
"user": {
"id": "66666666-6666-6666-6666-666666666666",
"name": "JDOE-AAD@example.onmicrosoft.com"
}
}
{
"message": "{\"time\": \"2019-06-24T09:32:07.4637225Z\", \"resourceId\": \"/tenants/22222222-2222-2222-2222-222222222222/providers/Microsoft.aadiam\", \"operationName\": \"Change user password\", \"operationVersion\": \"1.0\", \"category\": \"AuditLogs\", \"tenantId\": \"22222222-2222-2222-2222-222222222222\", \"resultSignature\": \"None\", \"durationMs\": 0, \"callerIpAddress\": \"<null>\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"level\": \"Informational\", \"properties\": {\"id\": \"Directory_1PF86_84995790\", \"category\": \"UserManagement\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"result\": \"success\", \"resultReason\": \"\", \"activityDisplayName\": \"Change user password\", \"activityDateTime\": \"2019-06-24T09:32:07.4637225+00:00\", \"loggedByService\": \"Core Directory\", \"operationType\": \"Update\", \"initiatedBy\": {\"user\": {\"id\": \"user1\", \"displayName\": null, \"userPrincipalName\": \"user1\", \"ipAddress\": \"<null>\"}}, \"targetResources\": [{\"id\": \"user1\", \"displayName\": null, \"type\": \"User\", \"userPrincipalName\": \"user1\", \"modifiedProperties\": []}], \"additionalDetails\": []}}",
"event": {
"action": "Change user password",
"category": [
"iam"
],
"outcome": "success"
},
"@timestamp": "2019-06-24T09:32:07.463722Z",
"action": {
"name": "Change user password",
"outcome": "success",
"properties": [
{
"id": "user1",
"name": "user1",
"type": "targetedUser"
}
],
"target": "user",
"type": "update"
},
"azuread": {
"category": "AuditLogs",
"correlationId": "11111111-1111-1111-1111-111111111111",
"durationMs": 0,
"operationName": "Change user password",
"operationVersion": "1.0",
"properties": {
"correlationId": "11111111-1111-1111-1111-111111111111",
"id": "Directory_1PF86_84995790",
"targetUserPrincipalName": "user1"
},
"resourceId": "/tenants/22222222-2222-2222-2222-222222222222/providers/Microsoft.aadiam",
"tenantId": "22222222-2222-2222-2222-222222222222"
},
"related": {
"user": [
"user1"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"user": {
"id": "user1",
"name": "user1"
}
}
{
"message": "{\"time\": \"2022-04-05T13:07:16.7796535Z\", \"resourceId\": \"/tenants/22222222-2222-2222-2222-222222222222/providers/Microsoft.aadiam\", \"operationName\": \"Sign-in activity\", \"operationVersion\": \"1.0\", \"category\": \"SignInLogs\", \"tenantId\": \"22222222-2222-2222-2222-222222222222\", \"resultType\": \"0\", \"resultSignature\": \"None\", \"durationMs\": 0, \"callerIpAddress\": \"2001:0db8:85a3:0000:0000:8a2e:0370:7334\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"identity\": \"DUPONT Jean\", \"Level\": 4, \"properties\": {\"id\": \"88888888-8888-8888-8888-888888888888\", \"createdDateTime\": \"2022-04-05T13:07:16.7796535+00:00\", \"userDisplayName\": \"DUPONT Jean\", \"userPrincipalName\": \"ANONYMIZED\", \"userId\": \"user1\", \"appId\": \"66666666-6666-6666-6666-666666666666\", \"appDisplayName\": \"Office 365 Exchange Online\", \"ipAddress\": \"2001:0db8:85a3:0000:0000:8a2e:0370:7334\", \"status\": {\"errorCode\": 0}, \"clientAppUsed\": \"Exchange Web Services\", \"userAgent\": \"Microsoft Office/16.0 (Windows NT 10.0; Microsoft Outlook 16.0.14326; Pro)\", \"deviceDetail\": {\"deviceId\": \"\", \"operatingSystem\": \"Windows 10\", \"browser\": \"Microsoft Office 16.0\"}, \"location\": {\"geoCoordinates\": {}}, \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"conditionalAccessStatus\": \"notApplied\", \"appliedConditionalAccessPolicies\": [{\"id\": \"77777777-7777-7777-7777-777777777777\", \"displayName\": \"MFA conditionnel BE\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"55555555-5555-5555-5555-555555555555\", \"displayName\": \"MFA-Office365-Test\", \"enforcedGrantControls\": [], \"enforcedSessionControls\": [], \"result\": \"notEnabled\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 0}, {\"id\": \"33333333-3333-3333-3333-333333333333\", \"displayName\": \"MFA-Docusign-Test\", \"enforcedGrantControls\": [], \"enforcedSessionControls\": [], \"result\": \"notEnabled\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 0}], \"authenticationContextClassReferences\": [], \"originalRequestId\": \"88888888-8888-8888-8888-888888888888\", \"isInteractive\": true, \"tokenIssuerName\": \"\", \"tokenIssuerType\": \"AzureAD\", \"authenticationProcessingDetails\": [{\"key\": \"Legacy TLS (TLS 1.0, 1.1, 3DES)\", \"value\": \"False\"}, {\"key\": \"Oauth Scope Info\", \"value\": \"[\\\"AuditLog.Create\\\",\\\"Chat.Read\\\",\\\"DataLossPreventionPolicy.Evaluate\\\",\\\"Directory.Read.All\\\",\\\"EduRoster.ReadBasic\\\",\\\"Files.ReadWrite.All\\\",\\\"Group.ReadWrite.All\\\",\\\"InformationProtectionPolicy.Read\\\",\\\"Notes.Create\\\",\\\"OnlineMeetings.Read\\\",\\\"OnlineMeetings.ReadWrite\\\",\\\"People.Read\\\",\\\"SensitiveInfoType.Detect\\\",\\\"SensitiveInfoType.Read.All\\\",\\\"SensitivityLabel.Evaluate\\\",\\\"User.Invite.All\\\",\\\"User.Read\\\",\\\"User.ReadBasic.All\\\"]\"}, {\"key\": \"Is CAE Token\", \"value\": \"False\"}], \"networkLocationDetails\": [], \"processingTimeInMilliseconds\": 143, \"riskDetail\": \"none\", \"riskLevelAggregated\": \"none\", \"riskLevelDuringSignIn\": \"none\", \"riskState\": \"none\", \"riskEventTypes\": [], \"riskEventTypes_v2\": [], \"resourceDisplayName\": \"Office 365 Exchange Online\", \"resourceId\": \"66666666-6666-6666-6666-666666666666\", \"resourceTenantId\": \"66666666-6666-6666-6666-666666666666\", \"homeTenantId\": \"66666666-6666-6666-6666-666666666666\", \"authenticationDetails\": [{\"authenticationStepDateTime\": \"2022-04-05T13:07:16.7796535+00:00\", \"authenticationMethod\": \"Password\", \"authenticationMethodDetail\": \"Password Hash Sync\", \"succeeded\": true, \"authenticationStepRequirement\": \"Primary authentication\", \"StatusSequence\": 0, \"RequestSequence\": 1}], \"authenticationRequirementPolicies\": [], \"authenticationRequirement\": \"singleFactorAuthentication\", \"alternateSignInName\": \"ANONYMIZED\", \"signInIdentifier\": \"ANONYMIZED\", \"servicePrincipalId\": \"\", \"userType\": \"Member\", \"flaggedForReview\": false, \"isTenantRestricted\": false, \"crossTenantAccessType\": \"none\", \"privateLinkDetails\": {}, \"ssoExtensionVersion\": \"\", \"uniqueTokenIdentifier\": \"11111111111111111111111111\", \"incomingTokenType\": \"none\", \"authenticationProtocol\": \"ropc\", \"appServicePrincipalId\": null, \"resourceServicePrincipalId\": \"44444444-4444-4444-4444-444444444444\"}}",
"event": {
"action": "Sign-in activity",
"category": [
"authentication"
],
"outcome": "success",
"type": [
"start"
]
},
"@timestamp": "2022-04-05T13:07:16.779653Z",
"action": {
"name": "Sign-in activity",
"outcome": "success"
},
"azuread": {
"authenticationDetails": [
{
"RequestSequence": 1,
"StatusSequence": 0,
"authenticationMethod": "Password",
"authenticationMethodDetail": "Password Hash Sync",
"authenticationStepDateTime": "2022-04-05T13:07:16.7796535+00:00",
"authenticationStepRequirement": "Primary authentication",
"succeeded": true
}
],
"callerIpAddress": "2001:0db8:85a3:0000:0000:8a2e:0370:7334",
"category": "SignInLogs",
"correlationId": "11111111-1111-1111-1111-111111111111",
"durationMs": 0,
"identity": "DUPONT Jean",
"operationName": "Sign-in activity",
"operationVersion": "1.0",
"properties": {
"appDisplayName": "Office 365 Exchange Online",
"appId": "66666666-6666-6666-6666-666666666666",
"authenticationProtocol": "ropc",
"authenticationRequirement": "singleFactorAuthentication",
"conditionalAccessStatus": "notApplied",
"correlationId": "11111111-1111-1111-1111-111111111111",
"id": "88888888-8888-8888-8888-888888888888",
"incomingTokenType": "none",
"oauth_scope_info": [
"AuditLog.Create",
"Chat.Read",
"DataLossPreventionPolicy.Evaluate",
"Directory.Read.All",
"EduRoster.ReadBasic",
"Files.ReadWrite.All",
"Group.ReadWrite.All",
"InformationProtectionPolicy.Read",
"Notes.Create",
"OnlineMeetings.Read",
"OnlineMeetings.ReadWrite",
"People.Read",
"SensitiveInfoType.Detect",
"SensitiveInfoType.Read.All",
"SensitivityLabel.Evaluate",
"User.Invite.All",
"User.Read",
"User.ReadBasic.All"
],
"resourceId": "66666666-6666-6666-6666-666666666666",
"riskDetail": "none",
"riskEventTypes": [],
"riskEventTypes_v2": [],
"riskLevelAggregated": "none",
"riskLevelDuringSignIn": "none",
"riskState": "none",
"status": {
"errorCode": "0"
},
"tokenIssuerType": "AzureAD",
"uniqueTokenIdentifier": "11111111111111111111111111",
"userType": "Member"
},
"resourceId": "/tenants/22222222-2222-2222-2222-222222222222/providers/Microsoft.aadiam",
"tenantId": "22222222-2222-2222-2222-222222222222"
},
"error": {
"code": "0"
},
"host": {
"os": {
"type": "Windows 10"
}
},
"log": {
"level": "4"
},
"related": {
"ip": [
"2001:db8:85a3::8a2e:370:7334"
]
},
"service": {
"name": "Office 365 Exchange Online",
"type": "ldap"
},
"source": {
"address": "2001:db8:85a3::8a2e:370:7334",
"ip": "2001:db8:85a3::8a2e:370:7334"
},
"user": {
"email": "ANONYMIZED",
"full_name": "DUPONT Jean",
"id": "user1"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Outlook",
"original": "Microsoft Office/16.0 (Windows NT 10.0; Microsoft Outlook 16.0.14326; Pro)",
"os": {
"name": "Windows",
"version": "10"
},
"version": "2016"
}
}
{
"message": "{\"time\": \"2025-02-18T10:25:12.2779144Z\", \"resourceId\": \"/TENANTS/11111111-1111-1111-1111-111111111111/PROVIDERS/MICROSOFT.AADIAM\", \"operationName\": \"Microsoft Graph Activity\", \"operationVersion\": \"v1.0\", \"category\": \"MicrosoftGraphActivityLogs\", \"resultSignature\": \"403\", \"durationMs\": \"2693631\", \"callerIpAddress\": \"1.2.3.4\", \"correlationId\": \"TEST_CORRELATION_UNIQUE_ID\", \"level\": \"Informational\", \"location\": \"North Europe\", \"properties\": {\"__UDI_RequiredFields_TenantId\": \"33333333-3333-3333-3333-333333333333\", \"__UDI_RequiredFields_UniqueId\": \"TEST_CORRELATION_UNIQUE_ID\", \"__UDI_RequiredFields_EventTime\": 638754711120000000, \"__UDI_RequiredFields_RegionScope\": \"EU\", \"timeGenerated\": \"2025-02-18T10:25:12.2779144Z\", \"location\": \"North Europe\", \"requestId\": \"TEST_CORRELATION_UNIQUE_ID\", \"operationId\": \"TEST_CORRELATION_UNIQUE_ID\", \"clientRequestId\": \"TEST_CLIENT_REQUEST_ID\", \"apiVersion\": \"v1.0\", \"requestMethod\": \"GET\", \"responseStatusCode\": 403, \"tenantId\": \"33333333-3333-3333-3333-333333333333\", \"durationMs\": 2693631, \"responseSizeBytes\": 324, \"signInActivityId\": \"JgW9XEOQM0WNakyHMghCAA\", \"roles\": \"\", \"appId\": \"TEST_APP_ID\", \"UserPrincipalObjectID\": \"user1\", \"scopes\": \"email openid profile Team.ReadBasic.All User.Read.All\", \"identityProvider\": \"\", \"clientAuthMethod\": \"2\", \"wids\": \"22222222-2222-2222-2222-222222222222\", \"C_Idtyp\": \"user\", \"C_Iat\": \"1739874011\", \"ipAddress\": \"1.2.3.4\", \"userAgent\": \"MruService/16.0.18604.40126\", \"requestUri\": \"https://example.com/\", \"atContentP\": \"\", \"atContentH\": \"\", \"userId\": \"user1\", \"tokenIssuedAt\": \"2025-02-18T10:20:11.0000000Z\"}, \"tenantId\": \"11111111-1111-1111-1111-111111111111\"}",
"event": {
"action": "Microsoft Graph Activity",
"category": [
"iam"
]
},
"@timestamp": "2025-02-18T10:25:12.277914Z",
"action": {
"name": "Microsoft Graph Activity"
},
"azuread": {
"callerIpAddress": "1.2.3.4",
"category": "MicrosoftGraphActivityLogs",
"correlationId": "TEST_CORRELATION_UNIQUE_ID",
"durationMs": 2693631,
"operationName": "Microsoft Graph Activity",
"operationVersion": "v1.0",
"properties": {
"appId": "TEST_APP_ID",
"requestId": "TEST_CORRELATION_UNIQUE_ID",
"scopes": [
"Team.ReadBasic.All",
"User.Read.All",
"email",
"openid",
"profile"
],
"uniqueTokenIdentifier": "JgW9XEOQM0WNakyHMghCAA",
"userPrincipalObjectID": "user1"
},
"resourceId": "/TENANTS/11111111-1111-1111-1111-111111111111/PROVIDERS/MICROSOFT.AADIAM",
"resultSignature": "403",
"tenantId": "11111111-1111-1111-1111-111111111111"
},
"http": {
"request": {
"method": "GET"
},
"response": {
"status_code": 403
}
},
"related": {
"ip": [
"1.2.3.4"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"source": {
"address": "1.2.3.4",
"ip": "1.2.3.4"
},
"url": {
"domain": "example.com",
"full": "https://example.com/",
"original": "https://example.com/",
"path": "/",
"port": 443,
"registered_domain": "example.com",
"scheme": "https",
"top_level_domain": "com"
},
"user": {
"id": "user1"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Other",
"original": "MruService/16.0.18604.40126",
"os": {
"name": "Other"
}
}
}
{
"message": "{\"time\": \"2025-02-18T10:25:12.2779144Z\", \"resourceId\": \"/TENANTS/44444444-4444-4444-4444-444444444444/PROVIDERS/MICROSOFT.AADIAM\", \"operationName\": \"Microsoft Graph Activity\", \"operationVersion\": \"v1.0\", \"category\": \"MicrosoftGraphActivityLogs\", \"resultSignature\": \"403\", \"durationMs\": \"2693631\", \"callerIpAddress\": \"1.2.3.4\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"level\": \"Informational\", \"location\": \"North Europe\", \"properties\": {\"__UDI_RequiredFields_TenantId\": \"55555555-5555-5555-5555-555555555555\", \"__UDI_RequiredFields_UniqueId\": \"11111111-1111-1111-1111-111111111111\", \"__UDI_RequiredFields_EventTime\": 638754711120000000, \"__UDI_RequiredFields_RegionScope\": \"EU\", \"timeGenerated\": \"2025-02-18T10:25:12.2779144Z\", \"location\": \"North Europe\", \"requestId\": \"11111111-1111-1111-1111-111111111111\", \"operationId\": \"11111111-1111-1111-1111-111111111111\", \"clientRequestId\": \"33333333-3333-3333-3333-333333333333\", \"apiVersion\": \"v1.0\", \"requestMethod\": \"GET\", \"responseStatusCode\": 403, \"tenantId\": \"55555555-5555-5555-5555-555555555555\", \"durationMs\": 2693631, \"responseSizeBytes\": 324, \"signInActivityId\": \"activityId\", \"roles\": \"\", \"appId\": \"testAppId\", \"UserPrincipalObjectID\": \"user1\", \"scopes\": \"email openid profile Team.ReadBasic.All User.Read.All\", \"identityProvider\": \"\", \"clientAuthMethod\": \"2\", \"wids\": \"22222222-2222-2222-2222-222222222222\", \"C_Idtyp\": \"user\", \"C_Iat\": \"1739874011\", \"ipAddress\": \"1.2.3.4\", \"userAgent\": \"MruService/16.0.18604.40126\", \"requestUri\": \"https://example.com/\", \"atContentP\": \"\", \"atContentH\": \"\", \"userId\": \"user1\", \"tokenIssuedAt\": \"2025-02-18T10:20:11.0000000Z\"}, \"tenantId\": \"44444444-4444-4444-4444-444444444444\"}",
"event": {
"action": "Microsoft Graph Activity",
"category": [
"iam"
]
},
"@timestamp": "2025-02-18T10:25:12.277914Z",
"action": {
"name": "Microsoft Graph Activity"
},
"azuread": {
"callerIpAddress": "1.2.3.4",
"category": "MicrosoftGraphActivityLogs",
"correlationId": "11111111-1111-1111-1111-111111111111",
"durationMs": 2693631,
"operationName": "Microsoft Graph Activity",
"operationVersion": "v1.0",
"properties": {
"appId": "testAppId",
"requestId": "11111111-1111-1111-1111-111111111111",
"scopes": [
"Team.ReadBasic.All",
"User.Read.All",
"email",
"openid",
"profile"
],
"uniqueTokenIdentifier": "activityId",
"userPrincipalObjectID": "user1"
},
"resourceId": "/TENANTS/44444444-4444-4444-4444-444444444444/PROVIDERS/MICROSOFT.AADIAM",
"resultSignature": "403",
"tenantId": "44444444-4444-4444-4444-444444444444"
},
"http": {
"request": {
"method": "GET"
},
"response": {
"status_code": 403
}
},
"related": {
"ip": [
"1.2.3.4"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"source": {
"address": "1.2.3.4",
"ip": "1.2.3.4"
},
"url": {
"domain": "example.com",
"full": "https://example.com/",
"original": "https://example.com/",
"path": "/",
"port": 443,
"registered_domain": "example.com",
"scheme": "https",
"top_level_domain": "com"
},
"user": {
"id": "user1"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Other",
"original": "MruService/16.0.18604.40126",
"os": {
"name": "Other"
}
}
}
{
"message": "{\"time\": \"2025-10-02T08:56:25.0717730Z\", \"resourceId\": \"/TENANTS/66666666-6666-6666-6666-666666666666/PROVIDERS/MICROSOFT.AADIAM\", \"operationName\": \"Microsoft Graph Activity\", \"operationVersion\": \"v1.0\", \"category\": \"MicrosoftGraphActivityLogs\", \"resultSignature\": \"200\", \"durationMs\": \"1748376\", \"callerIpAddress\": \"1.2.3.4\", \"correlationId\": \"33333333-3333-3333-3333-333333333333\", \"level\": \"Informational\", \"location\": \"France Central\", \"properties\": {\"__UDI_RequiredFields_TenantId\": \"55555555-5555-5555-5555-555555555555\", \"__UDI_RequiredFields_UniqueId\": \"33333333-3333-3333-3333-333333333333\", \"__UDI_RequiredFields_EventTime\": 638949921850717730, \"__UDI_RequiredFields_RegionScope\": \"EU\", \"timeGenerated\": \"2025-10-02T08:56:25.071773Z\", \"location\": \"France Central\", \"requestId\": \"33333333-3333-3333-3333-333333333333\", \"operationId\": \"33333333-3333-3333-3333-333333333333\", \"clientRequestId\": \"33333333-3333-3333-3333-333333333333\", \"apiVersion\": \"v1.0\", \"requestMethod\": \"GET\", \"responseStatusCode\": 200, \"tenantId\": \"55555555-5555-5555-5555-555555555555\", \"durationMs\": 1748376, \"responseSizeBytes\": 4088, \"signInActivityId\": \"nCIzipjKBXc87y9rpX8dAA\", \"roles\": \"\", \"appId\": \"22222222-2222-2222-2222-222222222222\", \"UserPrincipalObjectID\": \"user1\", \"scopes\": \"AppCatalog.Read.All Channel.ReadBasic.All Contacts.ReadWrite.Shared email Files.ReadWrite.All FileStorageContainer.Selected InformationProtectionPolicy.Read Mail.ReadWrite Mail.Send MailboxSettings.ReadWrite Notes.ReadWrite.All openid Organization.Read.All People.Read Place.Read.All profile Sites.ReadWrite.All Tasks.ReadWrite Team.ReadBasic.All TeamsAppInstallation.ReadForTeam TeamsTab.Create User.ReadBasic.All\", \"identityProvider\": \"\", \"clientAuthMethod\": \"0\", \"wids\": \"44444444-4444-4444-4444-444444444444\", \"C_Idtyp\": \"user\", \"C_Iat\": \"1759394725\", \"ipAddress\": \"1.2.3.4\", \"userAgent\": \"python-requests/2.32.5\", \"requestUri\": \"https://example.com/\", \"atContentP\": \"\", \"atContentH\": \"\", \"C_Sid\": \"11111111-1111-1111-1111-111111111111\", \"C_DeviceId\": \"\", \"userId\": \"user1\", \"tokenIssuedAt\": \"2025-10-02T08:45:25.0000000Z\"}, \"tenantId\": \"66666666-6666-6666-6666-666666666666\"}",
"event": {
"action": "Microsoft Graph Activity",
"category": [
"iam"
]
},
"@timestamp": "2025-10-02T08:56:25.071773Z",
"action": {
"name": "Microsoft Graph Activity"
},
"azuread": {
"callerIpAddress": "1.2.3.4",
"category": "MicrosoftGraphActivityLogs",
"correlationId": "33333333-3333-3333-3333-333333333333",
"durationMs": 1748376,
"operationName": "Microsoft Graph Activity",
"operationVersion": "v1.0",
"properties": {
"appId": "22222222-2222-2222-2222-222222222222",
"requestId": "33333333-3333-3333-3333-333333333333",
"scopes": [
"AppCatalog.Read.All",
"Channel.ReadBasic.All",
"Contacts.ReadWrite.Shared",
"FileStorageContainer.Selected",
"Files.ReadWrite.All",
"InformationProtectionPolicy.Read",
"Mail.ReadWrite",
"Mail.Send",
"MailboxSettings.ReadWrite",
"Notes.ReadWrite.All",
"Organization.Read.All",
"People.Read",
"Place.Read.All",
"Sites.ReadWrite.All",
"Tasks.ReadWrite",
"Team.ReadBasic.All",
"TeamsAppInstallation.ReadForTeam",
"TeamsTab.Create",
"User.ReadBasic.All",
"email",
"openid",
"profile"
],
"session_id": "11111111-1111-1111-1111-111111111111",
"uniqueTokenIdentifier": "nCIzipjKBXc87y9rpX8dAA",
"userPrincipalObjectID": "user1"
},
"resourceId": "/TENANTS/66666666-6666-6666-6666-666666666666/PROVIDERS/MICROSOFT.AADIAM",
"resultSignature": "200",
"tenantId": "66666666-6666-6666-6666-666666666666"
},
"http": {
"request": {
"method": "GET"
},
"response": {
"status_code": 200
}
},
"related": {
"ip": [
"1.2.3.4"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"source": {
"address": "1.2.3.4",
"ip": "1.2.3.4"
},
"url": {
"domain": "example.com",
"full": "https://example.com/",
"original": "https://example.com/",
"path": "/",
"port": 443,
"registered_domain": "example.com",
"scheme": "https",
"top_level_domain": "com"
},
"user": {
"id": "user1"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Python Requests",
"original": "python-requests/2.32.5",
"os": {
"name": "Other"
},
"version": "2.32"
}
}
{
"message": "{\"time\": \"2025-05-07T01:42:40.2828208Z\", \"resourceId\": \"/tenants/55555555-5555-5555-5555-555555555555/providers/Microsoft.aadiam\", \"operationName\": \"Recover device local administrator password\", \"operationVersion\": \"1.0\", \"category\": \"AuditLogs\", \"tenantId\": \"55555555-5555-5555-5555-555555555555\", \"resultSignature\": \"None\", \"durationMs\": 0, \"callerIpAddress\": \"1.2.3.4\", \"correlationId\": \"44444444-4444-4444-4444-444444444444\", \"Level\": 4, \"properties\": {\"tenantId\": \"33333333-3333-3333-3333-333333333333\", \"resultType\": \"\", \"resultDescription\": \"\", \"operationName\": \"Recover device local administrator password\", \"identity\": \"\", \"tenantGeo\": \"EU\", \"id\": \"Device Registration Service_44444444-4444-4444-4444-444444444444_DEVSERV_1234567890\", \"category\": \"Device\", \"correlationId\": \"44444444-4444-4444-4444-444444444444\", \"result\": \"success\", \"resultReason\": null, \"activityDisplayName\": \"Recover device local administrator password\", \"activityDateTime\": \"2025-05-07T01:42:40.2828208+00:00\", \"loggedByService\": \"Device Registration Service\", \"operationType\": \"Get\", \"userAgent\": null, \"initiatedBy\": {\"user\": {\"id\": \"user1\", \"displayName\": null, \"userPrincipalName\": \"user1\", \"ipAddress\": \"1.2.3.4\", \"roles\": []}}, \"targetResources\": [{\"id\": \"11111111-1111-1111-1111-111111111111\", \"displayName\": \"DEVICE123456\", \"type\": \"Device\", \"modifiedProperties\": [], \"administrativeUnits\": []}], \"additionalDetails\": [{\"key\": \"AdditionalInfo\", \"value\": \"Successfully recovered local credential by device id\"}, {\"key\": \"Device Id\", \"value\": \"22222222-2222-2222-2222-222222222222\"}]}}",
"event": {
"action": "Recover device local administrator password",
"category": [
"iam"
],
"outcome": "success"
},
"@timestamp": "2025-05-07T01:42:40.282820Z",
"action": {
"name": "Recover device local administrator password",
"outcome": "success",
"properties": [],
"target": "user",
"type": "get"
},
"azuread": {
"callerIpAddress": "1.2.3.4",
"category": "AuditLogs",
"correlationId": "44444444-4444-4444-4444-444444444444",
"durationMs": 0,
"operationName": "Recover device local administrator password",
"operationVersion": "1.0",
"properties": {
"correlationId": "44444444-4444-4444-4444-444444444444",
"id": "Device Registration Service_44444444-4444-4444-4444-444444444444_DEVSERV_1234567890",
"targetDeviceDisplayName": "DEVICE123456"
},
"resourceId": "/tenants/55555555-5555-5555-5555-555555555555/providers/Microsoft.aadiam",
"tenantId": "55555555-5555-5555-5555-555555555555"
},
"log": {
"level": "4"
},
"related": {
"ip": [
"1.2.3.4"
],
"user": [
"user1"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"source": {
"address": "1.2.3.4",
"ip": "1.2.3.4"
},
"user": {
"id": "user1",
"name": "user1"
}
}
{
"message": "{\"time\": \"2019-06-24T09:21:50.0418907Z\", \"resourceId\": \"/tenants/22222222-2222-2222-2222-222222222222/providers/Microsoft.aadiam\", \"operationName\": \"Remove unverified domain\", \"operationVersion\": \"1.0\", \"category\": \"AuditLogs\", \"tenantId\": \"22222222-2222-2222-2222-222222222222\", \"resultSignature\": \"None\", \"durationMs\": 0, \"callerIpAddress\": \"<null>\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"level\": \"Informational\", \"properties\": {\"id\": \"Directory_NFSWZ_16832133\", \"category\": \"DirectoryManagement\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"result\": \"success\", \"resultReason\": \"\", \"activityDisplayName\": \"Remove unverified domain\", \"activityDateTime\": \"2019-06-24T09:21:50.0418907+00:00\", \"loggedByService\": \"Core Directory\", \"operationType\": \"Delete\", \"initiatedBy\": {\"user\": {\"id\": \"user1\", \"displayName\": null, \"userPrincipalName\": \"user1\", \"ipAddress\": \"<null>\"}}, \"targetResources\": [{\"id\": null, \"displayName\": \"sekoiacorp.onmicrosoft.com\", \"modifiedProperties\": []}], \"additionalDetails\": []}}",
"event": {
"action": "Remove unverified domain",
"category": [
"iam"
],
"outcome": "success"
},
"@timestamp": "2019-06-24T09:21:50.041890Z",
"action": {
"name": "Remove unverified domain",
"outcome": "success",
"properties": [],
"target": "user",
"type": "delete"
},
"azuread": {
"category": "AuditLogs",
"correlationId": "11111111-1111-1111-1111-111111111111",
"durationMs": 0,
"operationName": "Remove unverified domain",
"operationVersion": "1.0",
"properties": {
"correlationId": "11111111-1111-1111-1111-111111111111",
"id": "Directory_NFSWZ_16832133"
},
"resourceId": "/tenants/22222222-2222-2222-2222-222222222222/providers/Microsoft.aadiam",
"tenantId": "22222222-2222-2222-2222-222222222222"
},
"related": {
"user": [
"user1"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"user": {
"id": "user1",
"name": "user1"
}
}
{
"message": "{\"time\": \"2025-01-29T16:53:43.2764438Z\", \"resourceId\": \"/tenants/44444444-4444-4444-4444-444444444444/providers/Microsoft.aadiam\", \"operationName\": \"Remove member from group\", \"operationVersion\": \"1.0\", \"category\": \"AuditLogs\", \"tenantId\": \"44444444-4444-4444-4444-444444444444\", \"resultSignature\": \"None\", \"durationMs\": 0, \"callerIpAddress\": \"1.2.3.4\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"identity\": \"user1\", \"Level\": 4, \"properties\": {\"tenantId\": \"33333333-3333-3333-3333-333333333333\", \"resultType\": \"\", \"resultDescription\": \"\", \"operationName\": \"Remove member from group\", \"identity\": \"user1\", \"tenantGeo\": \"EU\", \"id\": \"Directory_11111111-1111-1111-1111-111111111111_66666_777777777\", \"category\": \"GroupManagement\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"result\": \"success\", \"resultReason\": \"\", \"activityDisplayName\": \"Remove member from group\", \"activityDateTime\": \"2025-01-29T16:53:43.2764438+00:00\", \"loggedByService\": \"Core Directory\", \"operationType\": \"Unassign\", \"userAgent\": null, \"initiatedBy\": {\"app\": {\"appId\": null, \"displayName\": \"user1\", \"servicePrincipalId\": \"user1\", \"servicePrincipalName\": null}}, \"targetResources\": [{\"id\": \"user1\", \"displayName\": null, \"type\": \"User\", \"userPrincipalName\": \"user1\", \"modifiedProperties\": [{\"displayName\": \"Group.ObjectID\", \"oldValue\": \"\\\"44444444-4444-4444-4444-444444444444\\\"\", \"newValue\": null}, {\"displayName\": \"Group.DisplayName\", \"oldValue\": \"\\\"REDACTED\\\"\", \"newValue\": null}, {\"displayName\": \"Group.WellKnownObjectName\", \"oldValue\": null, \"newValue\": null}], \"administrativeUnits\": []}, {\"id\": \"user1\", \"displayName\": null, \"type\": \"Group\", \"groupType\": \"unknownFutureValue\", \"modifiedProperties\": [], \"administrativeUnits\": []}], \"additionalDetails\": []}}",
"event": {
"action": "Remove member from group",
"category": [
"iam"
],
"outcome": "success"
},
"@timestamp": "2025-01-29T16:53:43.276443Z",
"action": {
"name": "Remove member from group",
"outcome": "success",
"properties": [
{
"name": "Group.ObjectID",
"newValue": "",
"oldValue": "\"44444444-4444-4444-4444-444444444444\""
},
{
"name": "Group.DisplayName",
"newValue": "",
"oldValue": "\"REDACTED\""
},
{
"name": "Group.WellKnownObjectName",
"newValue": "",
"oldValue": ""
},
{
"id": "user1",
"name": "user1",
"type": "targetedUser"
}
],
"target": "application",
"type": "unassign"
},
"azuread": {
"callerIpAddress": "1.2.3.4",
"category": "AuditLogs",
"correlationId": "11111111-1111-1111-1111-111111111111",
"durationMs": 0,
"identity": "user1",
"operationName": "Remove member from group",
"operationVersion": "1.0",
"properties": {
"correlationId": "11111111-1111-1111-1111-111111111111",
"id": "Directory_11111111-1111-1111-1111-111111111111_66666_777777777"
},
"resourceId": "/tenants/44444444-4444-4444-4444-444444444444/providers/Microsoft.aadiam",
"tenantId": "44444444-4444-4444-4444-444444444444"
},
"log": {
"level": "4"
},
"related": {
"ip": [
"1.2.3.4"
],
"user": [
"user1"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"source": {
"address": "1.2.3.4",
"ip": "1.2.3.4"
},
"user": {
"changes": {
"group": {
"id": "null",
"name": "null"
}
},
"id": "user1",
"name": "user1",
"target": {
"group": {
"id": "44444444-4444-4444-4444-444444444444",
"name": "REDACTED"
},
"id": "user1",
"name": "user1"
}
}
}
{
"message": "{\"time\": \"2022-03-30T14:52:21.7062186Z\", \"resourceId\": \"/tenants/11111111-1111-1111-1111-222222222222/providers/Microsoft.aadiam\", \"operationName\": \"Sign-in activity\", \"operationVersion\": \"1.0\", \"category\": \"SignInLogs\", \"tenantId\": \"11111111-1111-1111-1111-222222222222\", \"resultType\": \"50158\", \"resultSignature\": \"None\", \"resultDescription\": \"External security challenge was not satisfied.\", \"durationMs\": 0, \"callerIpAddress\": \"1.2.3.4\", \"correlationId\": \"88888888-8888-8888-8888-888888888888\", \"identity\": \"User Name\", \"Level\": 4, \"location\": \"FR\", \"properties\": {\"id\": \"77777777-7777-7777-7777-777777777777\", \"createdDateTime\": \"2022-03-30T14:52:21.7062186+00:00\", \"userDisplayName\": \"User Name\", \"userPrincipalName\": \"ANONYMIZED\", \"userId\": \"user1\", \"appId\": \"11111111-1111-1111-1111-444444444444\", \"appDisplayName\": \"Office365 Shell WCSS-Client\", \"ipAddress\": \"1.2.3.4\", \"status\": {\"errorCode\": 50158, \"failureReason\": \"External security challenge was not satisfied.\"}, \"clientAppUsed\": \"Browser\", \"userAgent\": \"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.84 Safari/537.36\", \"deviceDetail\": {\"deviceId\": \"\", \"operatingSystem\": \"Windows 10\", \"browser\": \"Chrome 99.0.4844\"}, \"location\": {\"city\": \"Bordeaux\", \"state\": \"Gironde\", \"countryOrRegion\": \"FR\", \"geoCoordinates\": {\"latitude\": 44.84040069580078, \"longitude\": -0.5805000066757202}}, \"correlationId\": \"88888888-8888-8888-8888-888888888888\", \"conditionalAccessStatus\": \"failure\", \"appliedConditionalAccessPolicies\": [{\"id\": \"55555555-5555-5555-5555-555555555555\", \"displayName\": \"Check Point Harmony MFA\", \"enforcedGrantControls\": [\"Checkpoint Custom Control\"], \"enforcedSessionControls\": [], \"result\": \"failure\", \"conditionsSatisfied\": 3, \"conditionsNotSatisfied\": 0}, {\"id\": \"22222222-2222-2222-2222-222222222222\", \"displayName\": \"Access Control Nine Work for Android\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"44444444-4444-4444-4444-444444444444\", \"displayName\": \"Access Control PowerBI (Poste de travail)\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-1111-111111111111\", \"displayName\": \"Access Control Snowflake\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-1111-666666666666\", \"displayName\": \"Access Control PowerBI (Mobile)\", \"enforcedGrantControls\": [], \"enforcedSessionControls\": [], \"result\": \"notEnabled\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 0}, {\"id\": \"11111111-1111-1111-1111-333333333333\", \"displayName\": \"Access Control Gmail\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"99999999-9999-9999-9999-999999999999\", \"displayName\": \"MFA Cycloid\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"33333333-3333-3333-3333-333333333333\", \"displayName\": \"Block - Webmail Exchange Online\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"66666666-6666-6666-6666-666666666666\", \"displayName\": \"Require MFA - Privileged accounts\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}], \"originalRequestId\": \"77777777-7777-7777-7777-777777777777\", \"isInteractive\": true, \"tokenIssuerName\": \"\", \"tokenIssuerType\": \"AzureAD\", \"authenticationProcessingDetails\": [{\"key\": \"Login Hint Present\", \"value\": \"True\"}, {\"key\": \"Legacy TLS (TLS 1.0, 1.1, 3DES)\", \"value\": \"False\"}, {\"key\": \"Oauth Scope Info\", \"value\": \"\"}, {\"key\": \"Is CAE Token\", \"value\": \"False\"}], \"networkLocationDetails\": [{\"networkType\": \"trustedNamedLocation\", \"networkNames\": [\"IP corp\"]}], \"processingTimeInMilliseconds\": 91, \"riskDetail\": \"none\", \"riskLevelAggregated\": \"none\", \"riskLevelDuringSignIn\": \"none\", \"riskState\": \"none\", \"riskEventTypes\": [], \"riskEventTypes_v2\": [], \"resourceDisplayName\": \"Office365 Shell WCSS-Server\", \"resourceId\": \"11111111-1111-1111-1111-555555555555\", \"resourceTenantId\": \"11111111-1111-1111-1111-555555555555\", \"homeTenantId\": \"11111111-1111-1111-1111-555555555555\", \"authenticationDetails\": [{\"authenticationStepDateTime\": \"2022-03-30T14:52:21.7062186+00:00\", \"authenticationMethod\": \"Previously satisfied\", \"succeeded\": true, \"authenticationStepResultDetail\": \"First factor requirement satisfied by claim in the token\", \"authenticationStepRequirement\": \"Primary authentication\", \"StatusSequence\": 0, \"RequestSequence\": 0}], \"authenticationRequirementPolicies\": [], \"authenticationRequirement\": \"singleFactorAuthentication\", \"servicePrincipalId\": \"\", \"userType\": \"Member\", \"flaggedForReview\": false, \"isTenantRestricted\": false, \"autonomousSystemNumber\": 48744, \"crossTenantAccessType\": \"none\", \"privateLinkDetails\": {}, \"ssoExtensionVersion\": \"\", \"uniqueTokenIdentifier\": \"aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa\", \"incomingTokenType\": \"none\", \"authenticationProtocol\": \"none\"}}",
"event": {
"action": "Sign-in activity",
"category": [
"authentication"
],
"outcome": "failure",
"reason": "External security challenge was not satisfied.",
"type": [
"start"
]
},
"@timestamp": "2022-03-30T14:52:21.706218Z",
"action": {
"name": "Sign-in activity",
"outcome": "failure"
},
"azuread": {
"authenticationDetails": [
{
"RequestSequence": 0,
"StatusSequence": 0,
"authenticationMethod": "Previously satisfied",
"authenticationStepDateTime": "2022-03-30T14:52:21.7062186+00:00",
"authenticationStepRequirement": "Primary authentication",
"authenticationStepResultDetail": "First factor requirement satisfied by claim in the token",
"succeeded": true
}
],
"callerIpAddress": "1.2.3.4",
"category": "SignInLogs",
"correlationId": "88888888-8888-8888-8888-888888888888",
"durationMs": 0,
"identity": "User Name",
"operationName": "Sign-in activity",
"operationVersion": "1.0",
"properties": {
"appDisplayName": "Office365 Shell WCSS-Client",
"appId": "11111111-1111-1111-1111-444444444444",
"authenticationProtocol": "none",
"authenticationRequirement": "singleFactorAuthentication",
"conditionalAccessStatus": "failure",
"correlationId": "88888888-8888-8888-8888-888888888888",
"id": "77777777-7777-7777-7777-777777777777",
"incomingTokenType": "none",
"network_location": {
"network_names": [
"IP corp"
],
"network_type": "trustedNamedLocation"
},
"resourceId": "11111111-1111-1111-1111-555555555555",
"riskDetail": "none",
"riskEventTypes": [],
"riskEventTypes_v2": [],
"riskLevelAggregated": "none",
"riskLevelDuringSignIn": "none",
"riskState": "none",
"status": {
"errorCode": "50158",
"failureReason": "External security challenge was not satisfied."
},
"tokenIssuerType": "AzureAD",
"uniqueTokenIdentifier": "aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",
"userType": "Member"
},
"resourceId": "/tenants/11111111-1111-1111-1111-222222222222/providers/Microsoft.aadiam",
"resultDescription": "External security challenge was not satisfied.",
"tenantId": "11111111-1111-1111-1111-222222222222"
},
"error": {
"code": "50158",
"message": "External security challenge was not satisfied."
},
"host": {
"os": {
"type": "Windows 10"
}
},
"log": {
"level": "4"
},
"related": {
"ip": [
"1.2.3.4"
]
},
"service": {
"name": "Office365 Shell WCSS-Server",
"type": "ldap"
},
"source": {
"address": "1.2.3.4",
"geo": {
"city_name": "Bordeaux",
"location": {
"lat": 44.84040069580078,
"lon": -0.5805000066757202
},
"region_name": "Gironde"
},
"ip": "1.2.3.4"
},
"user": {
"email": "ANONYMIZED",
"full_name": "User Name",
"id": "user1"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Chrome",
"original": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.84 Safari/537.36",
"os": {
"name": "Windows",
"version": "10"
},
"version": "99.0.4844"
}
}
{
"message": "{\"time\": \"2022-03-31T12:26:46.0190957Z\", \"resourceId\": \"/tenants/99999999-9999-9999-9999-999999999999/providers/Microsoft.aadiam\", \"operationName\": \"Sign-in activity\", \"operationVersion\": \"1.0\", \"category\": \"SignInLogs\", \"tenantId\": \"99999999-9999-9999-9999-999999999999\", \"resultType\": \"0\", \"resultSignature\": \"None\", \"durationMs\": 0, \"callerIpAddress\": \"1.2.3.4\", \"correlationId\": \"11111111-1111-1111-1111-222222222222\", \"identity\": \"Admin Jean Dupont\", \"Level\": 4, \"location\": \"FR\", \"properties\": {\"id\": \"11111111-1111-1111-1111-111111111111\", \"createdDateTime\": \"2022-03-31T12:26:46.0190957+00:00\", \"userDisplayName\": \"Admin Jean Dupont\", \"userPrincipalName\": \"ANONYMIZED\", \"userId\": \"user1\", \"appId\": \"55555555-5555-5555-5555-555555555555\", \"appDisplayName\": \"Microsoft App Access Panel\", \"ipAddress\": \"1.2.3.4\", \"status\": {\"errorCode\": 0, \"additionalDetails\": \"MFA requirement satisfied by claim in the token\"}, \"clientAppUsed\": \"Browser\", \"userAgent\": \"Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0\", \"deviceDetail\": {\"deviceId\": \"\", \"operatingSystem\": \"Windows 10\", \"browser\": \"Firefox 98.0\"}, \"location\": {\"city\": \"Bordeaux\", \"state\": \"Gironde\", \"countryOrRegion\": \"FR\", \"geoCoordinates\": {\"latitude\": 44.84040069580078, \"longitude\": -0.5805000066757202}}, \"mfaDetail\": {}, \"correlationId\": \"11111111-1111-1111-1111-222222222222\", \"conditionalAccessStatus\": \"success\", \"appliedConditionalAccessPolicies\": [{\"id\": \"33333333-3333-3333-3333-333333333333\", \"displayName\": \"Access Control Nine Work for Android\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"66666666-6666-6666-6666-666666666666\", \"displayName\": \"Access Control PowerBI (Poste de travail)\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"22222222-2222-2222-2222-222222222222\", \"displayName\": \"Access Control Snowflake\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-1111-666666666666\", \"displayName\": \"Access Control PowerBI (Mobile)\", \"enforcedGrantControls\": [], \"enforcedSessionControls\": [], \"result\": \"notEnabled\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 0}, {\"id\": \"11111111-1111-1111-1111-333333333333\", \"displayName\": \"Access Control Gmail\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-1111-444444444444\", \"displayName\": \"MFA Cycloid\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"77777777-7777-7777-7777-777777777777\", \"displayName\": \"Check Point Harmony MFA\", \"enforcedGrantControls\": [\"Checkpoint Custom Control\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"44444444-4444-4444-4444-444444444444\", \"displayName\": \"Block - Webmail Exchange Online\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"88888888-8888-8888-8888-888888888888\", \"displayName\": \"Require MFA - Privileged accounts\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 3, \"conditionsNotSatisfied\": 8}], \"originalRequestId\": \"11111111-1111-1111-1111-111111111111\", \"isInteractive\": true, \"tokenIssuerName\": \"\", \"tokenIssuerType\": \"AzureAD\", \"authenticationProcessingDetails\": [{\"key\": \"Legacy TLS (TLS 1.0, 1.1, 3DES)\", \"value\": \"False\"}, {\"key\": \"Oauth Scope Info\", \"value\": \"\"}, {\"key\": \"Is CAE Token\", \"value\": \"False\"}], \"networkLocationDetails\": [{\"networkType\": \"trustedNamedLocation\", \"networkNames\": [\"IP network\"]}], \"processingTimeInMilliseconds\": 80, \"riskDetail\": \"none\", \"riskLevelAggregated\": \"none\", \"riskLevelDuringSignIn\": \"none\", \"riskState\": \"none\", \"riskEventTypes\": [], \"riskEventTypes_v2\": [], \"resourceDisplayName\": \"Windows Azure Active Directory\", \"resourceId\": \"11111111-1111-1111-1111-555555555555\", \"resourceTenantId\": \"11111111-1111-1111-1111-555555555555\", \"homeTenantId\": \"11111111-1111-1111-1111-555555555555\", \"authenticationDetails\": [{\"authenticationStepDateTime\": \"2022-03-31T12:26:46.0190957+00:00\", \"authenticationMethod\": \"Previously satisfied\", \"succeeded\": true, \"authenticationStepResultDetail\": \"First factor requirement satisfied by claim in the token\", \"authenticationStepRequirement\": \"Primary authentication\", \"StatusSequence\": 0, \"RequestSequence\": 0}], \"authenticationRequirementPolicies\": [], \"authenticationRequirement\": \"singleFactorAuthentication\", \"servicePrincipalId\": \"\", \"userType\": \"Member\", \"flaggedForReview\": false, \"isTenantRestricted\": false, \"autonomousSystemNumber\": 48744, \"crossTenantAccessType\": \"none\", \"privateLinkDetails\": {}, \"ssoExtensionVersion\": \"\", \"uniqueTokenIdentifier\": \"ODc5NTk5NGYtMGJiOC00NmQ3LTg3OTctOGM5YzM4NWQ1OTAw\", \"incomingTokenType\": \"none\", \"authenticationProtocol\": \"none\"}}",
"event": {
"action": "Sign-in activity",
"category": [
"authentication"
],
"outcome": "success",
"type": [
"start"
]
},
"@timestamp": "2022-03-31T12:26:46.019095Z",
"action": {
"name": "Sign-in activity",
"outcome": "success"
},
"azuread": {
"authenticationDetails": [
{
"RequestSequence": 0,
"StatusSequence": 0,
"authenticationMethod": "Previously satisfied",
"authenticationStepDateTime": "2022-03-31T12:26:46.0190957+00:00",
"authenticationStepRequirement": "Primary authentication",
"authenticationStepResultDetail": "First factor requirement satisfied by claim in the token",
"succeeded": true
}
],
"callerIpAddress": "1.2.3.4",
"category": "SignInLogs",
"correlationId": "11111111-1111-1111-1111-222222222222",
"durationMs": 0,
"identity": "Admin Jean Dupont",
"operationName": "Sign-in activity",
"operationVersion": "1.0",
"properties": {
"appDisplayName": "Microsoft App Access Panel",
"appId": "55555555-5555-5555-5555-555555555555",
"authenticationProtocol": "none",
"authenticationRequirement": "singleFactorAuthentication",
"conditionalAccessStatus": "success",
"correlationId": "11111111-1111-1111-1111-222222222222",
"id": "11111111-1111-1111-1111-111111111111",
"incomingTokenType": "none",
"network_location": {
"network_names": [
"IP network"
],
"network_type": "trustedNamedLocation"
},
"resourceId": "11111111-1111-1111-1111-555555555555",
"riskDetail": "none",
"riskEventTypes": [],
"riskEventTypes_v2": [],
"riskLevelAggregated": "none",
"riskLevelDuringSignIn": "none",
"riskState": "none",
"status": {
"additionalDetails": "MFA requirement satisfied by claim in the token",
"errorCode": "0"
},
"tokenIssuerType": "AzureAD",
"uniqueTokenIdentifier": "ODc5NTk5NGYtMGJiOC00NmQ3LTg3OTctOGM5YzM4NWQ1OTAw",
"userType": "Member"
},
"resourceId": "/tenants/99999999-9999-9999-9999-999999999999/providers/Microsoft.aadiam",
"tenantId": "99999999-9999-9999-9999-999999999999"
},
"error": {
"code": "0",
"message": "MFA requirement satisfied by claim in the token"
},
"host": {
"os": {
"type": "Windows 10"
}
},
"log": {
"level": "4"
},
"related": {
"ip": [
"1.2.3.4"
]
},
"service": {
"name": "Windows Azure Active Directory",
"type": "ldap"
},
"source": {
"address": "1.2.3.4",
"geo": {
"city_name": "Bordeaux",
"location": {
"lat": 44.84040069580078,
"lon": -0.5805000066757202
},
"region_name": "Gironde"
},
"ip": "1.2.3.4"
},
"user": {
"email": "ANONYMIZED",
"full_name": "Admin Jean Dupont",
"id": "user1"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Firefox",
"original": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0",
"os": {
"name": "Windows",
"version": "10"
},
"version": "98.0"
}
}
{
"message": "{\"time\": \"2023-08-16T15:32:05.5772601Z\", \"resourceId\": \"/tenants/11111111-1111-1111-1111-111111111111/providers/Microsoft.aadiam\", \"operationName\": \"Sign-in activity\", \"operationVersion\": \"1.0\", \"category\": \"SignInLogs\", \"tenantId\": \"11111111-1111-1111-1111-111111111111\", \"resultType\": \"0\", \"resultSignature\": \"None\", \"durationMs\": 0, \"callerIpAddress\": \"1.2.3.4\", \"correlationId\": \"user1\", \"identity\": \"John DOE\", \"Level\": 4, \"location\": \"FR\", \"properties\": {\"id\": \"user1\", \"createdDateTime\": \"2023-08-16T15:28:23.3045933+00:00\", \"userDisplayName\": \"John DOE\", \"userPrincipalName\": \"john.doe@example.org\", \"userId\": \"user1\", \"appId\": \"user1\", \"appDisplayName\": \"Microsoft Authentication Broker\", \"ipAddress\": \"1.2.3.4\", \"status\": {\"errorCode\": 0, \"additionalDetails\": \"MFA completed in Azure AD\"}, \"clientAppUsed\": \"Mobile Apps and Desktop clients\", \"userAgent\": \"Mozilla/5.0 (iPhone; CPU iPhone OS 16_6 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Mobile/15E148\", \"deviceDetail\": {\"deviceId\": \"\", \"operatingSystem\": \"Ios\", \"browser\": \"Mobile Safari 16.6\"}, \"location\": {\"city\": \"Paris\", \"state\": \"Paris\", \"countryOrRegion\": \"FR\", \"geoCoordinates\": {\"latitude\": 48.856578, \"longitude\": 2.351828}}, \"mfaDetail\": {\"authMethod\": \"Mobile app notification\"}, \"correlationId\": \"user1\", \"conditionalAccessStatus\": \"notApplied\", \"appliedConditionalAccessPolicies\": [], \"authenticationContextClassReferences\": [], \"originalRequestId\": \"user1\", \"isInteractive\": true, \"tokenIssuerName\": \"\", \"tokenIssuerType\": \"AzureAD\", \"authenticationProcessingDetails\": [{\"key\": \"Domain Hint Present\", \"value\": \"True\"}, {\"key\": \"Login Hint Present\", \"value\": \"True\"}, {\"key\": \"Legacy TLS (TLS 1.0, 1.1, 3DES)\", \"value\": \"False\"}, {\"key\": \"Is CAE Token\", \"value\": \"False\"}], \"networkLocationDetails\": [{\"networkType\": \"namedNetwork\", \"networkNames\": [\"Fra\"]}], \"clientCredentialType\": \"none\", \"processingTimeInMilliseconds\": 77, \"riskDetail\": \"none\", \"riskLevelAggregated\": \"none\", \"riskLevelDuringSignIn\": \"none\", \"riskState\": \"none\", \"riskEventTypes\": [], \"riskEventTypes_v2\": [], \"resourceId\": \"user1\", \"resourceTenantId\": \"user1\", \"homeTenantId\": \"user1\", \"tenantId\": \"user1\", \"authenticationDetails\": [{\"authenticationStepDateTime\": \"2023-08-16T15:28:23.3045933+00:00\", \"authenticationMethod\": \"Password\", \"authenticationMethodDetail\": \"Pass-through Authentication\", \"succeeded\": true, \"authenticationStepRequirement\": \"Primary authentication\", \"StatusSequence\": 0, \"RequestSequence\": 1}, {\"authenticationStepDateTime\": \"2023-08-16T15:28:22+00:00\", \"authenticationMethod\": \"Mobile app notification\", \"succeeded\": true, \"authenticationStepResultDetail\": \"MFA successfully completed\", \"authenticationStepRequirement\": \"Primary authentication\", \"StatusSequence\": 1692199702901, \"RequestSequence\": 1692199690724}], \"authenticationRequirementPolicies\": [{\"requirementProvider\": \"user\", \"detail\": \"Per-user MFA\"}], \"sessionLifetimePolicies\": [{\"expirationRequirement\": \"rememberMultifactorAuthenticationOnTrustedDevices\", \"detail\": \"Remember MFA\"}], \"authenticationRequirement\": \"multiFactorAuthentication\", \"alternateSignInName\": \"john.doe@example.org\", \"signInIdentifier\": \"john.doe@example.org\", \"servicePrincipalId\": \"\", \"userType\": \"Member\", \"flaggedForReview\": false, \"isTenantRestricted\": false, \"autonomousSystemNumber\": 1111, \"crossTenantAccessType\": \"none\", \"privateLinkDetails\": {}, \"ssoExtensionVersion\": \"\", \"uniqueTokenIdentifier\": \"5555555555555555555555\", \"authenticationStrengths\": [], \"incomingTokenType\": \"none\", \"authenticationProtocol\": \"none\", \"appServicePrincipalId\": null, \"resourceServicePrincipalId\": \"user1\", \"rngcStatus\": 0}}",
"event": {
"action": "Sign-in activity",
"category": [
"authentication"
],
"outcome": "success",
"type": [
"start"
]
},
"@timestamp": "2023-08-16T15:32:05.577260Z",
"action": {
"name": "Sign-in activity",
"outcome": "success"
},
"azuread": {
"authenticationDetails": [
{
"RequestSequence": 1,
"StatusSequence": 0,
"authenticationMethod": "Password",
"authenticationMethodDetail": "Pass-through Authentication",
"authenticationStepDateTime": "2023-08-16T15:28:23.3045933+00:00",
"authenticationStepRequirement": "Primary authentication",
"succeeded": true
},
{
"RequestSequence": 1692199690724,
"StatusSequence": 1692199702901,
"authenticationMethod": "Mobile app notification",
"authenticationStepDateTime": "2023-08-16T15:28:22+00:00",
"authenticationStepRequirement": "Primary authentication",
"authenticationStepResultDetail": "MFA successfully completed",
"succeeded": true
}
],
"callerIpAddress": "1.2.3.4",
"category": "SignInLogs",
"correlationId": "user1",
"durationMs": 0,
"identity": "John DOE",
"operationName": "Sign-in activity",
"operationVersion": "1.0",
"properties": {
"appDisplayName": "Microsoft Authentication Broker",
"appId": "user1",
"authenticationProtocol": "none",
"authenticationRequirement": "multiFactorAuthentication",
"conditionalAccessStatus": "notApplied",
"correlationId": "user1",
"id": "user1",
"incomingTokenType": "none",
"network_location": {
"network_names": [
"Fra"
],
"network_type": "namedNetwork"
},
"resourceId": "user1",
"riskDetail": "none",
"riskEventTypes": [],
"riskEventTypes_v2": [],
"riskLevelAggregated": "none",
"riskLevelDuringSignIn": "none",
"riskState": "none",
"status": {
"additionalDetails": "MFA completed in Azure AD",
"errorCode": "0"
},
"tokenIssuerType": "AzureAD",
"uniqueTokenIdentifier": "5555555555555555555555",
"userType": "Member"
},
"resourceId": "/tenants/11111111-1111-1111-1111-111111111111/providers/Microsoft.aadiam",
"tenantId": "11111111-1111-1111-1111-111111111111"
},
"error": {
"code": "0",
"message": "MFA completed in Azure AD"
},
"host": {
"os": {
"type": "Ios"
}
},
"log": {
"level": "4"
},
"related": {
"ip": [
"1.2.3.4"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"source": {
"address": "1.2.3.4",
"geo": {
"city_name": "Paris",
"location": {
"lat": 48.856578,
"lon": 2.351828
},
"region_name": "Paris"
},
"ip": "1.2.3.4"
},
"user": {
"email": "john.doe@example.org",
"full_name": "John DOE",
"id": "user1"
},
"user_agent": {
"device": {
"name": "iPhone"
},
"name": "Mobile Safari UI/WKWebView",
"original": "Mozilla/5.0 (iPhone; CPU iPhone OS 16_6 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Mobile/15E148",
"os": {
"name": "iOS",
"version": "16.6"
}
}
}
{
"message": "{\"time\": \"2023-10-04T13:09:02.6799940Z\", \"resourceId\": \"/tenants/11111111-1111-1111-1111-111111111111/providers/Microsoft.aadiam\", \"operationName\": \"Sign-in activity\", \"operationVersion\": \"1.0\", \"category\": \"SignInLogs\", \"tenantId\": \"11111111-1111-1111-1111-111111111111\", \"resultType\": \"0\", \"resultSignature\": \"None\", \"durationMs\": 0, \"callerIpAddress\": \"5.6.7.8\", \"correlationId\": \"55555555-5555-5555-5555-555555555555\", \"identity\": \"DOE Jane\", \"Level\": 4, \"location\": \"FR\", \"properties\": {\"id\": \"44444444-4444-4444-4444-444444444444\", \"createdDateTime\": \"2023-10-04T13:06:18.9617194+00:00\", \"userDisplayName\": \"Jane DOE\", \"userPrincipalName\": \"jane.doe@example.org\", \"userId\": \"22222222-2222-2222-2222-222222222222\", \"appId\": \"66666666-6666-6666-6666-666666666666\", \"appDisplayName\": \"Microsoft Authentication Broker\", \"ipAddress\": \"5.6.7.8\", \"status\": {\"errorCode\": 0}, \"clientAppUsed\": \"Mobile Apps and Desktop clients\", \"userAgent\": \"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/1.2.3.4 Safari/537.36 Edg/116.0.1938.98\", \"deviceDetail\": {\"deviceId\": \"44444444-4444-4444-4444-444444444444\", \"displayName\": \"HOSTNAME\", \"operatingSystem\": \"Ios\", \"browser\": \"Edge 116.0.1938\", \"isCompliant\": true, \"isManaged\": true, \"trustType\": \"Azure AD joined\"}, \"location\": {\"city\": \"Bordeaux\", \"state\": \"Gironde\", \"countryOrRegion\": \"FR\", \"geoCoordinates\": {\"latitude\": 44.84040069580078, \"longitude\": -0.5805000066757202}}, \"correlationId\": \"77777777-7777-7777-7777-777777777777\", \"conditionalAccessStatus\": \"notApplied\", \"appliedConditionalAccessPolicies\": [], \"authenticationContextClassReferences\": [], \"originalRequestId\": \"77777777-7777-7777-7777-777777777777\", \"isInteractive\": true, \"tokenIssuerName\": \"\", \"tokenIssuerType\": \"AzureAD\", \"authenticationProcessingDetails\": [{\"key\": \"Legacy TLS (TLS 1.0, 1.1, 3DES)\", \"value\": \"False\"}, {\"key\": \"Is CAE Token\", \"value\": \"False\"}], \"networkLocationDetails\": [], \"clientCredentialType\": \"none\", \"processingTimeInMilliseconds\": 300, \"riskDetail\": \"none\", \"riskLevelAggregated\": \"none\", \"riskLevelDuringSignIn\": \"none\", \"riskState\": \"none\", \"riskEventTypes\": [], \"riskEventTypes_v2\": [], \"resourceId\": \"77777777-7777-7777-7777-777777777777\", \"resourceTenantId\": \"11111111-1111-1111-1111-111111111111\", \"homeTenantId\": \"11111111-1111-1111-1111-111111111111\", \"tenantId\": \"11111111-1111-1111-1111-111111111111\", \"authenticationDetails\": [], \"authenticationRequirementPolicies\": [], \"sessionLifetimePolicies\": [], \"authenticationRequirement\": \"singleFactorAuthentication\", \"alternateSignInName\": \"jane.doe@example.org\", \"signInIdentifier\": \"jane.doe@example.org\", \"servicePrincipalId\": \"\", \"userType\": \"Member\", \"flaggedForReview\": false, \"isTenantRestricted\": false, \"autonomousSystemNumber\": 5410, \"crossTenantAccessType\": \"none\", \"privateLinkDetails\": {}, \"ssoExtensionVersion\": \"\", \"uniqueTokenIdentifier\": \"aaaaaaaaaaaaaaaaaaaaaa\", \"authenticationStrengths\": [], \"incomingTokenType\": \"primaryRefreshToken\", \"authenticationProtocol\": \"deviceCode\", \"appServicePrincipalId\": null, \"resourceServicePrincipalId\": \"33333333-3333-3333-3333-333333333333\", \"rngcStatus\": 0, \"signInTokenProtectionStatus\": \"none\", \"originalTransferMethod\": \"none\"}}",
"event": {
"action": "Sign-in activity",
"category": [
"authentication"
],
"outcome": "success",
"type": [
"start"
]
},
"@timestamp": "2023-10-04T13:09:02.679994Z",
"action": {
"name": "Sign-in activity",
"outcome": "success"
},
"azuread": {
"authenticationDetails": [],
"callerIpAddress": "5.6.7.8",
"category": "SignInLogs",
"correlationId": "55555555-5555-5555-5555-555555555555",
"durationMs": 0,
"identity": "DOE Jane",
"operationName": "Sign-in activity",
"operationVersion": "1.0",
"properties": {
"appDisplayName": "Microsoft Authentication Broker",
"appId": "66666666-6666-6666-6666-666666666666",
"authenticationProtocol": "deviceCode",
"authenticationRequirement": "singleFactorAuthentication",
"conditionalAccessStatus": "notApplied",
"correlationId": "77777777-7777-7777-7777-777777777777",
"deviceDetail": {
"isCompliant": true,
"isManaged": true,
"trustType": "Azure AD joined"
},
"id": "44444444-4444-4444-4444-444444444444",
"incomingTokenType": "primaryRefreshToken",
"original_transfer_method": "none",
"resourceId": "77777777-7777-7777-7777-777777777777",
"riskDetail": "none",
"riskEventTypes": [],
"riskEventTypes_v2": [],
"riskLevelAggregated": "none",
"riskLevelDuringSignIn": "none",
"riskState": "none",
"status": {
"errorCode": "0"
},
"tokenIssuerType": "AzureAD",
"uniqueTokenIdentifier": "aaaaaaaaaaaaaaaaaaaaaa",
"userType": "Member"
},
"resourceId": "/tenants/11111111-1111-1111-1111-111111111111/providers/Microsoft.aadiam",
"tenantId": "11111111-1111-1111-1111-111111111111"
},
"error": {
"code": "0"
},
"host": {
"hostname": "HOSTNAME",
"id": "44444444-4444-4444-4444-444444444444",
"name": "HOSTNAME",
"os": {
"type": "Ios"
}
},
"log": {
"level": "4"
},
"related": {
"hosts": [
"HOSTNAME"
],
"ip": [
"5.6.7.8"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"source": {
"address": "5.6.7.8",
"geo": {
"city_name": "Bordeaux",
"location": {
"lat": 44.84040069580078,
"lon": -0.5805000066757202
},
"region_name": "Gironde"
},
"ip": "5.6.7.8"
},
"user": {
"email": "jane.doe@example.org",
"full_name": "Jane DOE",
"id": "22222222-2222-2222-2222-222222222222"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Edge",
"original": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/1.2.3.4 Safari/537.36 Edg/116.0.1938.98",
"os": {
"name": "Windows",
"version": "10"
},
"version": "116.0.1938"
}
}
{
"message": "{\"time\": \"2025-02-17T08:38:07.5991020Z\", \"resourceId\": \"/tenants/11111111-1111-1111-6666-777777777777/providers/Microsoft.aadiam\", \"operationName\": \"Sign-in activity\", \"operationVersion\": \"1.0\", \"category\": \"SignInLogs\", \"tenantId\": \"11111111-1111-1111-6666-777777777777\", \"resultType\": \"0\", \"resultSignature\": \"None\", \"durationMs\": 0, \"callerIpAddress\": \"1.2.3.4\", \"correlationId\": \"11111111-1111-1111-4444-222222222222\", \"identity\": \"DOE John\", \"Level\": 4, \"location\": \"FR\", \"properties\": {\"id\": \"11111111-1111-1111-6666-111111111111\", \"createdDateTime\": \"2025-02-17T08:35:37.6544801+00:00\", \"userDisplayName\": \"DOE John\", \"userPrincipalName\": \"john.doe@example.com\", \"userId\": \"user1\", \"userAdministrativeUnits\": [{\"id\": \"11111111-1111-1111-5555-666666666666\"}], \"appId\": \"11111111-1111-1111-2222-999999999999\", \"appDisplayName\": \"Cortex xSOAR - New - Prod\", \"ipAddress\": \"1.2.3.4\", \"status\": {\"errorCode\": 0, \"additionalDetails\": \"MFA completed in Azure AD\"}, \"clientAppUsed\": \"Browser\", \"userAgent\": \"aaa\", \"deviceDetail\": {\"deviceId\": \"\", \"operatingSystem\": \"Windows10\", \"browser\": \"Chrome 132.0.0\"}, \"location\": {\"city\": \"Paris\", \"state\": \"Paris\", \"countryOrRegion\": \"FR\", \"geoCoordinates\": {\"latitude\": 48.861000061035156, \"longitude\": 2.3380000591278076}}, \"mfaDetail\": {\"authMethod\": \"Mobile app notification\", \"authDetail\": \"+XX XXXXXXX17\"}, \"correlationId\": \"11111111-1111-1111-4444-222222222222\", \"conditionalAccessStatus\": \"success\", \"appliedConditionalAccessPolicies\": [{\"id\": \"11111111-1111-1111-6666-888888888888\", \"displayName\": \"CA-REST-GRANT:MFA-SENSITIVE-SECURITY-TOOLS\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [\"SignInFrequency\"], \"result\": \"success\", \"conditionsSatisfied\": 3, \"conditionsNotSatisfied\": 0}, {\"id\": \"11111111-1111-1111-1111-999999999999\", \"displayName\": \"Baseline policy: Block-legacy-Auth\", \"enforcedGrantControls\": [], \"enforcedSessionControls\": [], \"result\": \"notEnabled\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 0}, {\"id\": \"11111111-1111-1111-3333-333333333333\", \"displayName\": \"ALL-MFA-AWS\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-6666-222222222222\", \"displayName\": \"Emergency_Block_OWA\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"33333333-3333-3333-3333-333333333333\", \"displayName\": \"TEMP policy for FORMS\", \"enforcedGrantControls\": [], \"enforcedSessionControls\": [\"CloudAppSecurity\"], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-3333-222222222222\", \"displayName\": \"Global-MFA-Azure_management_admins\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-1111-555555555555\", \"displayName\": \"ALL-MFA-AWS-SSO\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"55555555-5555-5555-5555-555555555555\", \"displayName\": \"ALL-MFA-PRIVILEGE-ROLE-ADMIN\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-6666-444444444444\", \"displayName\": \"CA-ATP-MFA-TEST\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}, {\"id\": \"11111111-1111-1111-2222-333333333333\", \"displayName\": \"CA001: Require multi-factor authentication for admins\", \"enforcedGrantControls\": [], \"enforcedSessionControls\": [], \"result\": \"notEnabled\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 0}, {\"id\": \"11111111-1111-1111-7777-222222222222\", \"displayName\": \"EMEA-Block-Access_from_Nigeria\", \"enforcedGrantControls\": [], \"enforcedSessionControls\": [], \"result\": \"notEnabled\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 0}, {\"id\": \"44444444-4444-4444-4444-444444444444\", \"displayName\": \"ALL-Block_BasicAuth_ActiveSync\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-4444-999999999999\", \"displayName\": \"ALL-GitHub-MFA\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-6666-333333333333\", \"displayName\": \"PY incident\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}, {\"id\": \"11111111-1111-1111-2222-666666666666\", \"displayName\": \"ALL-Block-undesired-IPs\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 19, \"conditionsNotSatisfied\": 1032}, {\"id\": \"11111111-1111-1111-2222-777777777777\", \"displayName\": \"MFA for Windows 365\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-3333-111111111111\", \"displayName\": \"MFA ON PAM \", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [\"SignInFrequency\"], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-2222-888888888888\", \"displayName\": \"CA-REST-BLOCK:MTR-WINDOWS\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}, {\"id\": \"11111111-1111-1111-4444-444444444444\", \"displayName\": \"CA-REST-GRANT:MFA-USER-AZURE-ADMINS\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [\"SignInFrequency\"], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-2222-111111111111\", \"displayName\": \"CA-REST-BLOCK:MTR-ANDROID\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}, {\"id\": \"66666666-6666-6666-6666-666666666666\", \"displayName\": \"ALL-MFA\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 23, \"conditionsNotSatisfied\": 1032}, {\"id\": \"11111111-1111-1111-3333-888888888888\", \"displayName\": \"Global-MFA-Global_and_Exchange_Administrators\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}, {\"id\": \"11111111-1111-1111-4444-666666666666\", \"displayName\": \"Office 365 - Terms of Use\", \"enforcedGrantControls\": [\"Office 365 -Acme End-User License Agreement\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-4444-555555555555\", \"displayName\": \"CA-REST-GRANT:COMPLIANT-DEVICE-APP-O365-S0-[TEST]_V3\", \"enforcedGrantControls\": [\"RequireCompliantDevice\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-6666-999999999999\", \"displayName\": \"CA-REST-GRANT:COMPLIANT-DEVICE-APP-TEAMS_v3\", \"enforcedGrantControls\": [\"RequireCompliantDevice\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"88888888-8888-8888-8888-888888888888\", \"displayName\": \"CA-REST-BLOCK:FUNCTIONAL-ACCOUNT-EXTERNAL-ACCESS\", \"enforcedGrantControls\": [\"RequireCompliantDevice\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}, {\"id\": \"99999999-9999-9999-9999-999999999999\", \"displayName\": \"eNutrimed SSO\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [\"SignInFrequency\"], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-4444-888888888888\", \"displayName\": \"CA-REST-GRANT:COMPLIANT-DEVICE-APP-CHECKPOINT-VPN-SNRU-AcmeRS\", \"enforcedGrantControls\": [\"Mfa\", \"RequireDomainJoinedDevice\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-2222-444444444444\", \"displayName\": \"CA-REST-GRANT:COMPLIANT-DEVICE-APP-CHECKPOINT-VPN-SNRU-PARTNERS\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-1111-888888888888\", \"displayName\": \"CA-REST-GRANT:MFA-USER-MHR-SIGN-IN-FREQUENCY-1D\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [\"SignInFrequency\"], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-7777-111111111111\", \"displayName\": \"CA-REST-GRANT:NETWORK-AAD-GAA-WW-On_premises_directory_synchronization_service_account\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}, {\"id\": \"11111111-1111-1111-5555-333333333333\", \"displayName\": \"CA-REST-GRANT:MFA-Users-ZTM-PRA-[TEST]\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [\"SignInFrequency\"], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-3333-777777777777\", \"displayName\": \"CA-REST-GRANT:MFA-USER-APPLICATION-ADMINS-USERS\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [\"SignInFrequency\"], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-4444-333333333333\", \"displayName\": \"CA-REST-GRANT:MFA-USER-FIDO2\", \"enforcedGrantControls\": [], \"enforcedSessionControls\": [\"SignInFrequency\"], \"result\": \"notApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-1111-333333333333\", \"displayName\": \"ALL MFA- MacOS and iOS only - User Experience Test\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"notApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}, {\"id\": \"11111111-1111-1111-5555-111111111111\", \"displayName\": \"TEST unmanged devices\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [\"CloudAppSecurity\"], \"result\": \"reportOnlyFailure\", \"conditionsSatisfied\": 279, \"conditionsNotSatisfied\": 0}, {\"id\": \"11111111-1111-1111-3333-999999999999\", \"displayName\": \"[TEST]Office365 - Windows & MacOS - Managed Device Access Only\", \"enforcedGrantControls\": [\"RequireCompliantDevice\"], \"enforcedSessionControls\": [\"AppEnforcedRestrictions\"], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-6666-666666666666\", \"displayName\": \"[TEST]Office 365 - Managed Device Access Only\", \"enforcedGrantControls\": [\"RequireCompliantDevice\"], \"enforcedSessionControls\": [], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-4444-111111111111\", \"displayName\": \"CyberSafe Policy\", \"enforcedGrantControls\": [\"CyberSafe Policy\"], \"enforcedSessionControls\": [], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-4444-777777777777\", \"displayName\": \"BlockRU\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}, {\"id\": \"22222222-2222-2222-2222-222222222222\", \"displayName\": \"[Proposal]Russia-UnTrustedDevices-Restriction\", \"enforcedGrantControls\": [\"RequireCompliantDevice\"], \"enforcedSessionControls\": [\"CloudAppSecurity\"], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}, {\"id\": \"11111111-1111-1111-2222-222222222222\", \"displayName\": \"CA-REST-GRANT:MFA-USER-INTUNE-ADMINS\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-5555-888888888888\", \"displayName\": \"CA-REST-BLOCK:GENERIC-ACCOUNTS\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}, {\"id\": \"11111111-1111-1111-1111-444444444444\", \"displayName\": \"CA-REST-GRANT:PROMPT-USERS-PASSWORDLESS-[TEST]\", \"enforcedGrantControls\": [], \"enforcedSessionControls\": [], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}, {\"id\": \"11111111-1111-1111-5555-222222222222\", \"displayName\": \"CA-REST-GRANT:MFA-USER-AZURE-ADMINS [TEST]\", \"enforcedGrantControls\": [], \"enforcedSessionControls\": [], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}, {\"id\": \"11111111-1111-1111-5555-777777777777\", \"displayName\": \"CA-REST-BLOCK:COMPROMISE-ACCOUNTS\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}, {\"id\": \"11111111-1111-1111-6666-555555555555\", \"displayName\": \"\", \"enforcedGrantControls\": [], \"enforcedSessionControls\": [], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}, {\"id\": \"11111111-1111-1111-3333-444444444444\", \"displayName\": \"Microsoft-managed: Multifactor authentication for admins accessing Microsoft Admin Portals\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-1111-111111111111\", \"displayName\": \"CA-REST-GRANT:COMPLIANT-DEVICE-APP-DANPT-[TEST]\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-5555-999999999999\", \"displayName\": \"CA002 Test Windows signin MFA\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-2222-555555555555\", \"displayName\": \"CA-REST-GRANT:MFA-USER-APP-Critical-[TEST]\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [\"SignInFrequency\"], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"77777777-7777-7777-7777-777777777777\", \"displayName\": \"CA-REST-BLOCK:FUNCTIONAL-ACCOUNT-EXTERNAL-ACCESS [EXCEPTIONS REPORT ONLY]\", \"enforcedGrantControls\": [\"Block\"], \"enforcedSessionControls\": [], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}, {\"id\": \"11111111-1111-1111-5555-444444444444\", \"displayName\": \"CA-REST-GRANT:MFA-Users-ZTM-GlobalProtect-[TEST]\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [\"SignInFrequency\"], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 0, \"conditionsNotSatisfied\": 1}, {\"id\": \"11111111-1111-1111-5555-555555555555\", \"displayName\": \"ALL MFA - MacOS and iOS only\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 19, \"conditionsNotSatisfied\": 1036}, {\"id\": \"11111111-1111-1111-3333-555555555555\", \"displayName\": \"ALL-MFA - macOS fix\", \"enforcedGrantControls\": [\"Mfa\"], \"enforcedSessionControls\": [], \"result\": \"reportOnlyNotApplied\", \"conditionsSatisfied\": 1, \"conditionsNotSatisfied\": 2}], \"authenticationContextClassReferences\": [], \"originalRequestId\": \"11111111-1111-1111-6666-111111111111\", \"isInteractive\": true, \"tokenIssuerName\": \"\", \"tokenIssuerType\": \"AzureAD\", \"authenticationProcessingDetails\": [{\"key\": \"Legacy TLS (TLS 1.0, 1.1, 3DES)\", \"value\": \"False\"}, {\"key\": \"Is CAE Token\", \"value\": \"False\"}], \"networkLocationDetails\": [{\"networkType\": \"trustedNamedLocation\", \"networkNames\": [\"Acme_Public_IPs (FR)\"]}], \"clientCredentialType\": \"none\", \"processingTimeInMilliseconds\": 158, \"riskDetail\": \"none\", \"riskLevelAggregated\": \"none\", \"riskLevelDuringSignIn\": \"none\", \"riskState\": \"none\", \"riskEventTypes\": [], \"riskEventTypes_v2\": [], \"resourceDisplayName\": \"Windows Azure Active Directory\", \"resourceId\": \"11111111-1111-1111-1111-222222222222\", \"resourceTenantId\": \"11111111-1111-1111-1111-222222222222\", \"homeTenantId\": \"11111111-1111-1111-1111-222222222222\", \"tenantId\": \"11111111-1111-1111-1111-222222222222\", \"authenticationDetails\": [{\"authenticationStepDateTime\": \"2025-02-17T08:35:37.6544801+00:00\", \"authenticationMethod\": \"Password\", \"authenticationMethodDetail\": \"Password Hash Sync\", \"succeeded\": true, \"authenticationStepRequirement\": \"Primary authentication\", \"StatusSequence\": 0, \"RequestSequence\": 1}, {\"authenticationStepDateTime\": \"2025-02-17T08:35:27+00:00\", \"authenticationMethod\": \"Mobile app notification\", \"succeeded\": false, \"authenticationStepResultDetail\": \"Authentication in progress\", \"authenticationStepRequirement\": \"Primary authentication\", \"StatusSequence\": 1739781327622, \"RequestSequence\": 1739781325380}], \"authenticationRequirementPolicies\": [{\"requirementProvider\": \"multiConditionalAccess\", \"detail\": \"Conditional Access\"}], \"sessionLifetimePolicies\": [{\"expirationRequirement\": \"rememberMultifactorAuthenticationOnTrustedDevices\", \"detail\": \"Remember MFA\"}, {\"expirationRequirement\": \"signInFrequencyPeriodicReauthentication\", \"detail\": \"Sign-in frequency (periodic re-authentication)\"}], \"authenticationRequirement\": \"multiFactorAuthentication\", \"alternateSignInName\": \"john.doe@example.com\", \"signInIdentifier\": \"john.doe@example.com\", \"servicePrincipalId\": \"\", \"userType\": \"Member\", \"flaggedForReview\": false, \"isTenantRestricted\": false, \"autonomousSystemNumber\": 16509, \"crossTenantAccessType\": \"none\", \"privateLinkDetails\": {}, \"ssoExtensionVersion\": \"\", \"uniqueTokenIdentifier\": \"aEQ2qLOsqkS86zz3OHIeAA\", \"authenticationStrengths\": [], \"incomingTokenType\": \"none\", \"authenticationProtocol\": \"none\", \"appServicePrincipalId\": null, \"resourceServicePrincipalId\": \"11111111-1111-1111-3333-666666666666\", \"rngcStatus\": 0, \"signInTokenProtectionStatus\": \"none\", \"tokenProtectionStatusDetails\": {\"signInSessionStatus\": \"unbound\", \"signInSessionStatusCode\": 1002}, \"originalTransferMethod\": \"none\", \"isThroughGlobalSecureAccess\": false, \"conditionalAccessAudiences\": [{\"applicationId\": \"11111111-1111-1111-2222-999999999999\", \"audienceReasons\": \"none\"}], \"sessionId\": \"11111111-1111-1111-1111-666666666666\", \"appOwnerTenantId\": \"11111111-1111-1111-1111-222222222222\", \"resourceOwnerTenantId\": \"11111111-1111-1111-1111-777777777777\"}}",
"event": {
"action": "Sign-in activity",
"category": [
"authentication"
],
"outcome": "success",
"type": [
"start"
]
},
"@timestamp": "2025-02-17T08:38:07.599102Z",
"action": {
"name": "Sign-in activity",
"outcome": "success"
},
"azuread": {
"authenticationDetails": [
{
"RequestSequence": 1,
"StatusSequence": 0,
"authenticationMethod": "Password",
"authenticationMethodDetail": "Password Hash Sync",
"authenticationStepDateTime": "2025-02-17T08:35:37.6544801+00:00",
"authenticationStepRequirement": "Primary authentication",
"succeeded": true
},
{
"RequestSequence": 1739781325380,
"StatusSequence": 1739781327622,
"authenticationMethod": "Mobile app notification",
"authenticationStepDateTime": "2025-02-17T08:35:27+00:00",
"authenticationStepRequirement": "Primary authentication",
"authenticationStepResultDetail": "Authentication in progress",
"succeeded": false
}
],
"callerIpAddress": "1.2.3.4",
"category": "SignInLogs",
"correlationId": "11111111-1111-1111-4444-222222222222",
"durationMs": 0,
"identity": "DOE John",
"operationName": "Sign-in activity",
"operationVersion": "1.0",
"properties": {
"appDisplayName": "Cortex xSOAR - New - Prod",
"appId": "11111111-1111-1111-2222-999999999999",
"authenticationProtocol": "none",
"authenticationRequirement": "multiFactorAuthentication",
"conditionalAccessStatus": "success",
"correlationId": "11111111-1111-1111-4444-222222222222",
"id": "11111111-1111-1111-6666-111111111111",
"incomingTokenType": "none",
"network_location": {
"network_names": [
"Acme_Public_IPs (FR)"
],
"network_type": "trustedNamedLocation"
},
"original_transfer_method": "none",
"resourceId": "11111111-1111-1111-1111-222222222222",
"resourceOwnerTenantId": "11111111-1111-1111-1111-777777777777",
"riskDetail": "none",
"riskEventTypes": [],
"riskEventTypes_v2": [],
"riskLevelAggregated": "none",
"riskLevelDuringSignIn": "none",
"riskState": "none",
"session_id": "11111111-1111-1111-1111-666666666666",
"status": {
"additionalDetails": "MFA completed in Azure AD",
"errorCode": "0"
},
"tokenIssuerType": "AzureAD",
"uniqueTokenIdentifier": "aEQ2qLOsqkS86zz3OHIeAA",
"userType": "Member"
},
"resourceId": "/tenants/11111111-1111-1111-6666-777777777777/providers/Microsoft.aadiam",
"tenantId": "11111111-1111-1111-6666-777777777777"
},
"error": {
"code": "0",
"message": "MFA completed in Azure AD"
},
"host": {
"os": {
"type": "Windows10"
}
},
"log": {
"level": "4"
},
"related": {
"ip": [
"1.2.3.4"
]
},
"service": {
"name": "Windows Azure Active Directory",
"type": "ldap"
},
"source": {
"address": "1.2.3.4",
"geo": {
"city_name": "Paris",
"location": {
"lat": 48.861000061035156,
"lon": 2.3380000591278076
},
"region_name": "Paris"
},
"ip": "1.2.3.4"
},
"user": {
"email": "john.doe@example.com",
"full_name": "DOE John",
"id": "user1"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Other",
"original": "aaa",
"os": {
"name": "Other"
}
}
}
{
"message": "{\"time\": \"2025-07-24T15:32:44.2442191Z\", \"resourceId\": \"/tenants/22222222-1111-1111-1111-222222222222/providers/Microsoft.aadiam\", \"operationName\": \"Sign-in activity\", \"operationVersion\": \"1.0\", \"category\": \"NonInteractiveUserSignInLogs\", \"tenantId\": \"22222222-1111-1111-1111-222222222222\", \"resultType\": \"0\", \"resultSignature\": \"SUCCESS\", \"durationMs\": 0, \"callerIpAddress\": \"1.2.3.4\", \"correlationId\": \"44444444-4444-4444-4444-444444444444\", \"identity\": \"Doe John\", \"Level\": 4, \"location\": \"FR\", \"properties\": {\"id\": \"77777777-7777-7777-7777-777777777777\", \"createdDateTime\": \"2025-07-24T15:30:17.7974412+00:00\", \"userDisplayName\": \"Doe John\", \"userPrincipalName\": \"john.doe@company.com\", \"userId\": \"user1\", \"agent\": {\"agentType\": \"notAgentic\", \"parentAppId\": \"\"}, \"appId\": \"66666666-6666-6666-6666-666666666666\", \"appDisplayName\": \"Microsoft Intune Windows Agent\", \"ipAddress\": \"1.2.3.4\", \"status\": {\"errorCode\": 0, \"additionalDetails\": \"MFA requirement satisfied by claim in the token\"}, \"clientAppUsed\": \"Mobile Apps and Desktop clients\", \"userAgent\": \"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.102 Safari/537.36 Edge/18.22631\", \"deviceDetail\": {\"deviceId\": \"11111111-1111-1111-1111-111111111111\", \"displayName\": \"example.com\", \"operatingSystem\": \"Windows10\", \"browser\": \"Edge 18.22631\", \"isManaged\": true, \"trustType\": \"Hybrid Azure AD joined\"}, \"location\": {\"city\": \"Paris\", \"countryOrRegion\": \"FR\", \"geoCoordinates\": {\"latitude\": 48.85350036621094, \"longitude\": 2.348400115966797}}, \"mfaDetail\": {}, \"correlationId\": \"44444444-4444-4444-4444-444444444444\", \"conditionalAccessStatus\": \"notApplied\", \"appliedConditionalAccessPolicies\": [], \"authenticationContextClassReferences\": [], \"originalRequestId\": \"55555555-5555-5555-5555-555555555555\", \"isInteractive\": false, \"tokenIssuerName\": \"\", \"tokenIssuerType\": \"AzureAD\", \"authenticationProcessingDetails\": [{\"key\": \"Legacy TLS (TLS 1.0, 1.1, 3DES)\", \"value\": \"False\"}, {\"key\": \"Oauth Scope Info\", \"value\": \"[\\\"user_impersonation\\\"]\"}, {\"key\": \"Is CAE Token\", \"value\": \"False\"}], \"networkLocationDetails\": [{\"networkType\": \"trustedNamedLocation\", \"networkNames\": [\"Company-Zscaler TDF-Trusted Proxy IPs\"]}], \"clientCredentialType\": \"none\", \"processingTimeInMilliseconds\": 48, \"riskDetail\": \"none\", \"riskLevelAggregated\": \"none\", \"riskLevelDuringSignIn\": \"none\", \"riskState\": \"none\", \"riskEventTypes\": [], \"riskEventTypes_v2\": [], \"resourceDisplayName\": \"Microsoft Intune Checkin\", \"resourceId\": \"99999999-9999-9999-9999-999999999999\", \"resourceTenantId\": \"99999999-9999-9999-9999-999999999999\", \"homeTenantId\": \"99999999-9999-9999-9999-999999999999\", \"tenantId\": \"99999999-9999-9999-9999-999999999999\", \"authenticationDetails\": [], \"authenticationRequirementPolicies\": [], \"sessionLifetimePolicies\": [], \"authenticationRequirement\": \"singleFactorAuthentication\", \"servicePrincipalId\": \"\", \"userType\": \"Member\", \"flaggedForReview\": false, \"isTenantRestricted\": false, \"autonomousSystemNumber\": 62044, \"crossTenantAccessType\": \"none\", \"privateLinkDetails\": {}, \"ssoExtensionVersion\": \"\", \"uniqueTokenIdentifier\": \"URB3vEvKUUuClWlFhN4gAA\", \"authenticationStrengths\": [], \"incomingTokenType\": \"primaryRefreshToken\", \"authenticationProtocol\": \"none\", \"appServicePrincipalId\": null, \"resourceServicePrincipalId\": \"33333333-3333-3333-3333-333333333333\", \"rngcStatus\": 0, \"signInTokenProtectionStatus\": \"none\", \"tokenProtectionStatusDetails\": {\"signInSessionStatus\": \"bound\", \"signInSessionStatusCode\": 0}, \"originalTransferMethod\": \"none\", \"isThroughGlobalSecureAccess\": false, \"globalSecureAccessIpAddress\": \"\", \"conditionalAccessAudiences\": [\"99999999-9999-9999-9999-999999999999\"], \"sessionId\": \"22222222-2222-2222-2222-222222222222\", \"appOwnerTenantId\": \"88888888-8888-8888-8888-888888888888\", \"resourceOwnerTenantId\": \"88888888-8888-8888-8888-888888888888\"}}",
"event": {
"action": "Sign-in activity",
"category": [
"authentication"
],
"outcome": "success",
"type": [
"start"
]
},
"@timestamp": "2025-07-24T15:32:44.244219Z",
"action": {
"name": "Sign-in activity",
"outcome": "success"
},
"azuread": {
"authenticationDetails": [],
"callerIpAddress": "1.2.3.4",
"category": "NonInteractiveUserSignInLogs",
"correlationId": "44444444-4444-4444-4444-444444444444",
"durationMs": 0,
"identity": "Doe John",
"operationName": "Sign-in activity",
"operationVersion": "1.0",
"properties": {
"appDisplayName": "Microsoft Intune Windows Agent",
"appId": "66666666-6666-6666-6666-666666666666",
"authenticationProtocol": "none",
"authenticationRequirement": "singleFactorAuthentication",
"conditionalAccessStatus": "notApplied",
"correlationId": "44444444-4444-4444-4444-444444444444",
"deviceDetail": {
"isManaged": true,
"trustType": "Hybrid Azure AD joined"
},
"id": "77777777-7777-7777-7777-777777777777",
"incomingTokenType": "primaryRefreshToken",
"network_location": {
"network_names": [
"Company-Zscaler TDF-Trusted Proxy IPs"
],
"network_type": "trustedNamedLocation"
},
"oauth_scope_info": [
"user_impersonation"
],
"original_transfer_method": "none",
"resourceId": "99999999-9999-9999-9999-999999999999",
"resourceOwnerTenantId": "88888888-8888-8888-8888-888888888888",
"riskDetail": "none",
"riskEventTypes": [],
"riskEventTypes_v2": [],
"riskLevelAggregated": "none",
"riskLevelDuringSignIn": "none",
"riskState": "none",
"session_id": "22222222-2222-2222-2222-222222222222",
"status": {
"additionalDetails": "MFA requirement satisfied by claim in the token",
"errorCode": "0"
},
"tokenIssuerType": "AzureAD",
"uniqueTokenIdentifier": "URB3vEvKUUuClWlFhN4gAA",
"userType": "Member"
},
"resourceId": "/tenants/22222222-1111-1111-1111-222222222222/providers/Microsoft.aadiam",
"resultSignature": "SUCCESS",
"tenantId": "22222222-1111-1111-1111-222222222222"
},
"error": {
"code": "0",
"message": "MFA requirement satisfied by claim in the token"
},
"host": {
"hostname": "example.com",
"id": "11111111-1111-1111-1111-111111111111",
"name": "example.com",
"os": {
"type": "Windows10"
}
},
"log": {
"level": "4"
},
"related": {
"hosts": [
"example.com"
],
"ip": [
"1.2.3.4"
]
},
"service": {
"name": "Microsoft Intune Checkin",
"type": "ldap"
},
"source": {
"address": "1.2.3.4",
"geo": {
"city_name": "Paris",
"location": {
"lat": 48.85350036621094,
"lon": 2.348400115966797
}
},
"ip": "1.2.3.4"
},
"user": {
"email": "john.doe@company.com",
"full_name": "Doe John",
"id": "user1"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Edge",
"original": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.102 Safari/537.36 Edge/18.22631",
"os": {
"name": "Windows",
"version": "10"
},
"version": "18.22631"
}
}
{
"message": "{\"time\": \"2025-10-14T07:34:57.9144897Z\", \"resourceId\": \"77777777-7777-7777-7777-777777777777\", \"operationName\": \"Sign-in activity\", \"operationVersion\": \"1.0\", \"category\": \"ServicePrincipalSignInLogs\", \"tenantId\": \"77777777-7777-7777-7777-777777777777\", \"resultType\": \"0\", \"resultSignature\": \"SUCCESS\", \"durationMs\": 0, \"callerIpAddress\": \"77777777-7777-7777-7777-777777777777\", \"correlationId\": \"22222222-2222-2222-2222-222222222222\", \"Level\": 4, \"properties\": {\"id\": \"66666666-6666-6666-6666-666666666666\", \"createdDateTime\": \"2025-10-14T07:33:50.1498978+00:00\", \"userId\": null, \"agent\": {\"agentType\": \"notAgentic\", \"parentAppId\": \"\"}, \"appId\": \"88888888-8888-8888-8888-888888888888\", \"ipAddress\": \"77777777-7777-7777-7777-777777777777\", \"status\": {\"errorCode\": 0}, \"userAgent\": \"okhttp/4.8.1\", \"location\": {\"city\": \"\", \"state\": \"\", \"countryOrRegion\": \"\", \"geoCoordinates\": {\"latitude\": 0.0, \"longitude\": 0.0}}, \"correlationId\": \"22222222-2222-2222-2222-222222222222\", \"conditionalAccessStatus\": \"notApplied\", \"appliedConditionalAccessPolicies\": [], \"isInteractive\": false, \"tokenIssuerType\": \"AzureAD\", \"authenticationProcessingDetails\": [{\"key\": \"Azure AD App Authentication Library\", \"value\": \"Family: MSAL Library: MSAL.Java 1.10.0 Platform: Java\"}], \"networkLocationDetails\": [], \"clientCredentialType\": \"clientSecret\", \"processingTimeInMilliseconds\": 0, \"riskDetail\": \"none\", \"riskLevelAggregated\": \"low\", \"riskLevelDuringSignIn\": \"low\", \"riskState\": \"none\", \"resourceDisplayName\": \"Azure Storage\", \"resourceId\": \"77777777-7777-7777-7777-777777777777\", \"servicePrincipalName\": \"ParseMe\", \"servicePrincipalId\": \"ParseMe\", \"flaggedForReview\": false, \"isTenantRestricted\": false, \"crossTenantAccessType\": \"none\", \"servicePrincipalCredentialKeyId\": \"55555555-5555-5555-5555-555555555555\", \"uniqueTokenIdentifier\": \"tOkEnIdEnTiFiEr123\", \"incomingTokenType\": \"none\", \"authenticationProtocol\": \"none\", \"appServicePrincipalId\": null, \"resourceServicePrincipalId\": \"33333333-3333-3333-3333-333333333333\", \"signInTokenProtectionStatus\": \"none\", \"originalTransferMethod\": \"none\", \"isThroughGlobalSecureAccess\": false, \"conditionalAccessAudiences\": [\"44444444-4444-4444-4444-444444444444\", \"11111111-1111-1111-1111-111111111111\"], \"sessionId\": \"99999999-9999-9999-9999-999999999999\", \"appOwnerTenantId\": \"77777777-7777-7777-7777-777777777777\", \"resourceOwnerTenantId\": \"ParseMe\"}}",
"event": {
"action": "Sign-in activity",
"category": [
"iam"
]
},
"@timestamp": "2025-10-14T07:34:57.914489Z",
"action": {
"name": "Sign-in activity"
},
"azuread": {
"category": "ServicePrincipalSignInLogs",
"correlationId": "22222222-2222-2222-2222-222222222222",
"durationMs": 0,
"operationName": "Sign-in activity",
"operationVersion": "1.0",
"properties": {
"appId": "88888888-8888-8888-8888-888888888888",
"authenticationProtocol": "none",
"correlationId": "22222222-2222-2222-2222-222222222222",
"id": "66666666-6666-6666-6666-666666666666",
"incomingTokenType": "none",
"original_transfer_method": "none",
"resourceId": "77777777-7777-7777-7777-777777777777",
"resourceOwnerTenantId": "ParseMe",
"riskDetail": "none",
"riskLevelAggregated": "low",
"riskLevelDuringSignIn": "low",
"riskState": "none",
"servicePrincipalId": "ParseMe",
"servicePrincipalName": "ParseMe",
"session_id": "99999999-9999-9999-9999-999999999999",
"status": {
"errorCode": "0"
},
"tokenIssuerType": "AzureAD",
"uniqueTokenIdentifier": "tOkEnIdEnTiFiEr123"
},
"resourceId": "77777777-7777-7777-7777-777777777777",
"resultSignature": "SUCCESS",
"tenantId": "77777777-7777-7777-7777-777777777777"
},
"error": {
"code": "0"
},
"log": {
"level": "4"
},
"service": {
"name": "Azure Storage",
"type": "ldap"
},
"source": {
"geo": {
"location": {
"lat": 0.0,
"lon": 0.0
}
}
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "okhttp",
"original": "okhttp/4.8.1",
"os": {
"name": "Other"
},
"version": "4.8.1"
}
}
{
"message": "{\"time\": \"2019-06-24T09:32:07.4637225Z\", \"resourceId\": \"/tenants/22222222-2222-2222-2222-222222222222/providers/Microsoft.aadiam\", \"operationName\": \"Update StsRefreshTokenValidFrom Timestamp\", \"operationVersion\": \"1.0\", \"category\": \"AuditLogs\", \"tenantId\": \"22222222-2222-2222-2222-222222222222\", \"resultSignature\": \"None\", \"durationMs\": 0, \"callerIpAddress\": \"<null>\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"level\": \"Informational\", \"properties\": {\"id\": \"Directory_1PF86_84995795\", \"category\": \"UserManagement\", \"correlationId\": \"11111111-1111-1111-1111-111111111111\", \"result\": \"success\", \"resultReason\": \"\", \"activityDisplayName\": \"Update StsRefreshTokenValidFrom Timestamp\", \"activityDateTime\": \"2019-06-24T09:32:07.4637225+00:00\", \"loggedByService\": \"Core Directory\", \"operationType\": \"Update\", \"initiatedBy\": {\"user\": {\"id\": \"user1\", \"displayName\": null, \"userPrincipalName\": \"user1\", \"ipAddress\": \"<null>\"}}, \"targetResources\": [{\"id\": \"user1\", \"displayName\": null, \"type\": \"User\", \"userPrincipalName\": \"user1\", \"modifiedProperties\": []}], \"additionalDetails\": []}}",
"event": {
"action": "Update StsRefreshTokenValidFrom Timestamp",
"category": [
"iam"
],
"outcome": "success"
},
"@timestamp": "2019-06-24T09:32:07.463722Z",
"action": {
"name": "Update StsRefreshTokenValidFrom Timestamp",
"outcome": "success",
"properties": [
{
"id": "user1",
"name": "user1",
"type": "targetedUser"
}
],
"target": "user",
"type": "update"
},
"azuread": {
"category": "AuditLogs",
"correlationId": "11111111-1111-1111-1111-111111111111",
"durationMs": 0,
"operationName": "Update StsRefreshTokenValidFrom Timestamp",
"operationVersion": "1.0",
"properties": {
"correlationId": "11111111-1111-1111-1111-111111111111",
"id": "Directory_1PF86_84995795",
"targetUserPrincipalName": "user1"
},
"resourceId": "/tenants/22222222-2222-2222-2222-222222222222/providers/Microsoft.aadiam",
"tenantId": "22222222-2222-2222-2222-222222222222"
},
"related": {
"user": [
"user1"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"user": {
"id": "user1",
"name": "user1"
}
}
{
"message": "{\"time\": \"3/24/2022 2:42:35 PM\", \"resourceId\": \"/tenants/11111111-1111-1111-1111-111111111111/providers/microsoft.aadiam\", \"operationName\": \"User Risk Detection\", \"operationVersion\": \"1.0\", \"category\": \"UserRiskEvents\", \"tenantId\": \"11111111-1111-1111-1111-111111111111\", \"resultSignature\": \"None\", \"durationMs\": 0, \"callerIpAddress\": \"1.2.3.4\", \"correlationId\": \"7c7668bf6b9324b33680508b470da8193ff9bb551d9b420f64111b1e3b257b7f\", \"identity\": \"bar foo\", \"Level\": 4, \"location\": \"fr\", \"properties\": {\"id\": \"7c7668bf6b9324b33680508b470da8193ff9bb551d9b420f64111b1e3b257b7f\", \"requestId\": \"33333333-3333-3333-3333-333333333333\", \"correlationId\": \"44444444-4444-4444-4444-444444444444\", \"riskType\": \"unfamiliarFeatures\", \"riskEventType\": \"unfamiliarFeatures\", \"riskState\": \"dismissed\", \"riskLevel\": \"low\", \"riskDetail\": \"aiConfirmedSigninSafe\", \"source\": \"IdentityProtection\", \"detectionTimingType\": \"realtime\", \"activity\": \"signin\", \"ipAddress\": \"1.2.3.4\", \"location\": {\"city\": \"La Guaiserie\", \"state\": \"Loir-Et-Cher\", \"countryOrRegion\": \"FR\", \"geoCoordinates\": {\"altitude\": 0.0, \"latitude\": 47.45919, \"longitude\": 2.21955}}, \"activityDateTime\": \"2022-03-24T14:40:04.234Z\", \"detectedDateTime\": \"2022-03-24T14:40:04.234Z\", \"lastUpdatedDateTime\": \"2022-03-24T14:42:35.066Z\", \"userId\": \"user1\", \"userDisplayName\": \"bar foo\", \"userPrincipalName\": \"ANONYMIZED\", \"additionalInfo\": \"[{\\\"Key\\\":\\\"userAgent\\\",\\\"Value\\\":\\\"Mozilla/5.0 (iPhone; CPU iPhone OS 14_4 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Mobile/15E148\\\"}]\", \"tokenIssuerType\": \"AzureAD\", \"resourceTenantId\": null, \"homeTenantId\": \"22222222-2222-2222-2222-222222222222\", \"userType\": \"member\", \"crossTenantAccessType\": \"none\"}}",
"event": {
"action": "User Risk Detection",
"category": [
"iam"
],
"reason": "unfamiliarFeatures",
"type": [
"connection"
]
},
"@timestamp": "2022-03-24T14:42:35Z",
"action": {
"name": "User Risk Detection"
},
"azuread": {
"callerIpAddress": "1.2.3.4",
"category": "UserRiskEvents",
"correlationId": "7c7668bf6b9324b33680508b470da8193ff9bb551d9b420f64111b1e3b257b7f",
"durationMs": 0,
"identity": "bar foo",
"operationName": "User Risk Detection",
"operationVersion": "1.0",
"properties": {
"activity": "signin",
"correlationId": "44444444-4444-4444-4444-444444444444",
"detectionTimingType": "realtime",
"id": "7c7668bf6b9324b33680508b470da8193ff9bb551d9b420f64111b1e3b257b7f",
"requestId": "33333333-3333-3333-3333-333333333333",
"riskDetail": "aiConfirmedSigninSafe",
"riskEventType": "unfamiliarFeatures",
"riskLevel": "low",
"riskState": "dismissed",
"source": "IdentityProtection",
"tokenIssuerType": "AzureAD",
"userType": "member"
},
"resourceId": "/tenants/11111111-1111-1111-1111-111111111111/providers/microsoft.aadiam",
"tenantId": "11111111-1111-1111-1111-111111111111"
},
"log": {
"level": "4"
},
"related": {
"ip": [
"1.2.3.4"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"source": {
"address": "1.2.3.4",
"geo": {
"city_name": "La Guaiserie",
"location": {
"lat": 47.45919,
"lon": 2.21955
},
"region_name": "Loir-Et-Cher"
},
"ip": "1.2.3.4"
},
"user": {
"email": "ANONYMIZED",
"full_name": "bar foo",
"id": "user1"
},
"user_agent": {
"device": {
"name": "iPhone"
},
"name": "Mobile Safari UI/WKWebView",
"original": "Mozilla/5.0 (iPhone; CPU iPhone OS 14_4 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Mobile/15E148",
"os": {
"name": "iOS",
"version": "14.4"
}
}
}
{
"message": "{\"time\": \"3/24/2022 2:42:35 PM\", \"resourceId\": \"/tenants/11111111-1111-1111-1111-111111111111/providers/microsoft.aadiam\", \"operationName\": \"User Risk Detection\", \"operationVersion\": \"1.0\", \"category\": \"UserRiskEvents\", \"tenantId\": \"11111111-1111-1111-1111-111111111111\", \"resultSignature\": \"None\", \"durationMs\": 0, \"callerIpAddress\": \"5.6.7.8\", \"correlationId\": \"527e981ab0f7ca8b686173c77337138107d8854ce5f7307b06f1edb19398d18b\", \"identity\": \"bar foo\", \"Level\": 4, \"location\": \"fr\", \"properties\": {\"id\": \"527e981ab0f7ca8b686173c77337138107d8854ce5f7307b06f1edb19398d18b\", \"requestId\": \"33333333-3333-3333-3333-333333333333\", \"correlationId\": \"44444444-4444-4444-4444-444444444444\", \"riskType\": \"unfamiliarFeatures\", \"riskEventType\": \"unfamiliarFeatures\", \"riskState\": \"atRisk\", \"riskLevel\": \"low\", \"riskDetail\": \"none\", \"source\": \"IdentityProtection\", \"detectionTimingType\": \"realtime\", \"activity\": \"signin\", \"ipAddress\": \"5.6.7.8\", \"location\": {\"city\": \"\", \"state\": \"\", \"countryOrRegion\": \"FR\", \"geoCoordinates\": {\"altitude\": 0, \"latitude\": 46, \"longitude\": 2}}, \"activityDateTime\": \"2023-10-26T5:32:08.107Z\", \"detectedDateTime\": \"2023-10-26T5:32:08.107Z\", \"lastUpdatedDateTime\": \"2023-10-26T5:35:05.938Z\", \"userId\": \"user1\", \"userDisplayName\": \"bar foo\", \"userPrincipalName\": \"ANONYMIZED\", \"additionalInfo\": \"[{\\\"Key\\\":\\\"riskReasons\\\",\\\"Value\\\":[\\\"UnfamiliarASN\\\",\\\"UnfamiliarBrowser\\\",\\\"UnfamiliarDevice\\\",\\\"UnfamiliarIP\\\",\\\"UnfamiliarLocation\\\",\\\"UnfamiliarEASId\\\",\\\"UnfamiliarTenantIPsubnet\\\"]},{\\\"Key\\\":\\\"userAgent\\\",\\\"Value\\\":\\\"Mozilla/5.0 (Linux; Android 12; CPH2005 Build/RKQ1.211103.002; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/1.2.3.4 Mobile Safari/537.36 PKeyAuth/1.0\\\"},{\\\"Key\\\":\\\"alertUrl\\\",\\\"Value\\\":null}]\", \"tokenIssuerType\": \"AzureAD\", \"resourceTenantId\": null, \"homeTenantId\": \"22222222-2222-2222-2222-222222222222\", \"userType\": \"member\", \"crossTenantAccessType\": \"none\"}}",
"event": {
"action": "User Risk Detection",
"category": [
"iam"
],
"reason": "unfamiliarFeatures",
"type": [
"connection"
]
},
"@timestamp": "2022-03-24T14:42:35Z",
"action": {
"name": "User Risk Detection"
},
"azuread": {
"callerIpAddress": "5.6.7.8",
"category": "UserRiskEvents",
"correlationId": "527e981ab0f7ca8b686173c77337138107d8854ce5f7307b06f1edb19398d18b",
"durationMs": 0,
"identity": "bar foo",
"operationName": "User Risk Detection",
"operationVersion": "1.0",
"properties": {
"activity": "signin",
"correlationId": "44444444-4444-4444-4444-444444444444",
"detectionTimingType": "realtime",
"id": "527e981ab0f7ca8b686173c77337138107d8854ce5f7307b06f1edb19398d18b",
"requestId": "33333333-3333-3333-3333-333333333333",
"riskDetail": "none",
"riskEventType": "unfamiliarFeatures",
"riskLevel": "low",
"riskReasons": [
"UnfamiliarASN",
"UnfamiliarBrowser",
"UnfamiliarDevice",
"UnfamiliarEASId",
"UnfamiliarIP",
"UnfamiliarLocation",
"UnfamiliarTenantIPsubnet"
],
"riskState": "atRisk",
"source": "IdentityProtection",
"tokenIssuerType": "AzureAD",
"userType": "member"
},
"resourceId": "/tenants/11111111-1111-1111-1111-111111111111/providers/microsoft.aadiam",
"tenantId": "11111111-1111-1111-1111-111111111111"
},
"log": {
"level": "4"
},
"related": {
"ip": [
"5.6.7.8"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"source": {
"address": "5.6.7.8",
"geo": {
"location": {
"lat": 46,
"lon": 2
}
},
"ip": "5.6.7.8"
},
"user": {
"email": "ANONYMIZED",
"full_name": "bar foo",
"id": "user1"
},
"user_agent": {
"device": {
"name": "Oppo CPH2005"
},
"name": "Chrome Mobile WebView",
"original": "Mozilla/5.0 (Linux; Android 12; CPH2005 Build/RKQ1.211103.002; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/1.2.3.4 Mobile Safari/537.36 PKeyAuth/1.0",
"os": {
"name": "Android",
"version": "12"
},
"version": "1.2.3"
}
}
{
"message": "{\"time\": \"12/13/2024 4:34:03 PM\", \"resourceId\": \"/tenants/22222222-2222-2222-2222-222222222222/providers/microsoft.aadiam\", \"operationName\": \"User Risk Detection\", \"operationVersion\": \"1.0\", \"category\": \"UserRiskEvents\", \"tenantId\": \"22222222-2222-2222-2222-222222222222\", \"resultSignature\": \"None\", \"durationMs\": 0, \"callerIpAddress\": \"1.2.3.4\", \"correlationId\": \"111111111111111111111111111111111111\", \"identity\": \"doe john\", \"Level\": \"Information\", \"location\": \"fr\", \"properties\": {\"id\": \"111111111111111111111111111111111111\", \"requestId\": \"11111111-1111-1111-1111-111111111111\", \"correlationId\": \"user1\", \"riskType\": \"unfamiliarFeatures\", \"riskEventType\": \"unfamiliarFeatures\", \"riskState\": \"dismissed\", \"riskLevel\": \"low\", \"riskDetail\": \"aiConfirmedSigninSafe\", \"source\": \"IdentityProtection\", \"detectionTimingType\": \"realtime\", \"activity\": \"signin\", \"ipAddress\": \"1.2.3.4\", \"location\": {\"city\": \"Rennes\", \"state\": \"Bretagne\", \"countryOrRegion\": \"FR\", \"geoCoordinates\": {\"altitude\": 0.0, \"latitude\": 0.0, \"longitude\": 0.0}}, \"activityDateTime\": \"2024-12-13T16:31:49.945Z\", \"detectedDateTime\": \"2024-12-13T16:31:49.945Z\", \"lastUpdatedDateTime\": \"2024-12-13T16:34:03.966Z\", \"userId\": \"user1\", \"userDisplayName\": \"DOE John\", \"userPrincipalName\": \"ANONYMIZED\", \"additionalInfo\": \"[{\\\"Key\\\":\\\"riskReasons\\\",\\\"Value\\\":[\\\"UnfamiliarBrowser\\\",\\\"UnfamiliarDevice\\\",\\\"UnfamiliarIP\\\",\\\"UnfamiliarLocation\\\",\\\"UnfamiliarEASId\\\",\\\"UnfamiliarTenantIPsubnet\\\"]},{\\\"Key\\\":\\\"userAgent\\\",\\\"Value\\\":\\\"Mozilla/5.0 (Linux; Android 14; SM-S911B Build/UP1A.231005.007; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/131.0.6778.105 Mobile Safari/537.36 PKeyAuth/1.0\\\"},{\\\"Key\\\":\\\"alertUrl\\\",\\\"Value\\\":null},{\\\"Key\\\":\\\"mitreTechniques\\\",\\\"Value\\\":\\\"T1078.004\\\"}]\", \"tokenIssuerType\": \"AzureAD\", \"resourceTenantId\": null, \"homeTenantId\": \"33333333-3333-3333-3333-333333333333\", \"userType\": \"member\", \"crossTenantAccessType\": \"none\", \"mitreTechniqueId\": \"T1078.004\"}}",
"event": {
"action": "User Risk Detection",
"category": [
"iam"
],
"reason": "unfamiliarFeatures",
"type": [
"connection"
]
},
"@timestamp": "2024-12-13T16:34:03Z",
"action": {
"name": "User Risk Detection"
},
"azuread": {
"callerIpAddress": "1.2.3.4",
"category": "UserRiskEvents",
"correlationId": "111111111111111111111111111111111111",
"durationMs": 0,
"identity": "doe john",
"operationName": "User Risk Detection",
"operationVersion": "1.0",
"properties": {
"activity": "signin",
"correlationId": "user1",
"detectionTimingType": "realtime",
"id": "111111111111111111111111111111111111",
"requestId": "11111111-1111-1111-1111-111111111111",
"riskDetail": "aiConfirmedSigninSafe",
"riskEventType": "unfamiliarFeatures",
"riskLevel": "low",
"riskReasons": [
"UnfamiliarBrowser",
"UnfamiliarDevice",
"UnfamiliarEASId",
"UnfamiliarIP",
"UnfamiliarLocation",
"UnfamiliarTenantIPsubnet"
],
"riskState": "dismissed",
"source": "IdentityProtection",
"tokenIssuerType": "AzureAD",
"userType": "member"
},
"resourceId": "/tenants/22222222-2222-2222-2222-222222222222/providers/microsoft.aadiam",
"tenantId": "22222222-2222-2222-2222-222222222222"
},
"log": {
"level": "Information"
},
"related": {
"ip": [
"1.2.3.4"
]
},
"service": {
"name": "Azure Active Directory",
"type": "ldap"
},
"source": {
"address": "1.2.3.4",
"geo": {
"city_name": "Rennes",
"location": {
"lat": 0.0,
"lon": 0.0
},
"region_name": "Bretagne"
},
"ip": "1.2.3.4"
},
"user": {
"email": "ANONYMIZED",
"full_name": "DOE John",
"id": "user1"
},
"user_agent": {
"device": {
"name": "Samsung SM-S911B"
},
"name": "Chrome Mobile WebView",
"original": "Mozilla/5.0 (Linux; Android 14; SM-S911B Build/UP1A.231005.007; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/131.0.6778.105 Mobile Safari/537.36 PKeyAuth/1.0",
"os": {
"name": "Android",
"version": "14"
},
"version": "131.0.6778"
}
}
Extracted Fields
The following table lists the fields that are extracted, normalized under the ECS format, analyzed and indexed by the parser. It should be noted that infered fields are not listed.
| Name | Type | Description |
|---|---|---|
@timestamp |
date |
Date/time when the event originated. |
action.properties |
array |
action.properties |
action.target |
keyword |
action.target |
azuread.activityDateTime |
keyword |
|
azuread.additionalInfo |
keyword |
|
azuread.authenticationDetails |
array |
|
azuread.authenticationRequirement |
keyword |
|
azuread.authenticationRequirementPolicies |
array |
|
azuread.autonomousSystemNumber |
long |
|
azuread.callerIpAddress |
keyword |
|
azuread.category |
keyword |
|
azuread.correlationId |
keyword |
|
azuread.crossTenantAccessType |
keyword |
|
azuread.detectedDateTime |
keyword |
|
azuread.durationMs |
long |
|
azuread.flaggedForReview |
bool |
|
azuread.homeTenantId |
keyword |
|
azuread.identity |
keyword |
|
azuread.isTenantRestricted |
bool |
|
azuread.lastUpdatedDateTime |
keyword |
|
azuread.operationName |
keyword |
|
azuread.operationVersion |
keyword |
|
azuread.privateLinkDetails |
list |
|
azuread.properties.activity |
keyword |
|
azuread.properties.appDisplayName |
keyword |
appDisplayName |
azuread.properties.appId |
keyword |
appId |
azuread.properties.authenticationProtocol |
keyword |
authenticationProtocol |
azuread.properties.authenticationRequirement |
keyword |
|
azuread.properties.conditionalAccessStatus |
keyword |
|
azuread.properties.correlationId |
keyword |
|
azuread.properties.detectionTimingType |
keyword |
|
azuread.properties.deviceDetail.isCompliant |
bool |
|
azuread.properties.deviceDetail.isManaged |
bool |
|
azuread.properties.deviceDetail.trustType |
keyword |
|
azuread.properties.id |
keyword |
|
azuread.properties.incomingTokenType |
keyword |
|
azuread.properties.network_location.network_names |
array |
|
azuread.properties.network_location.network_type |
keyword |
|
azuread.properties.oauth_scope_info |
keyword |
|
azuread.properties.original_transfer_method |
keyword |
|
azuread.properties.requestId |
keyword |
|
azuread.properties.resourceId |
keyword |
|
azuread.properties.resourceOwnerTenantId |
keyword |
|
azuread.properties.riskDetail |
keyword |
|
azuread.properties.riskEventType |
keyword |
|
azuread.properties.riskEventTypes |
keyword |
riskEventTypes |
azuread.properties.riskEventTypes_v2 |
keyword |
riskEventTypes_v2 |
azuread.properties.riskLevel |
keyword |
|
azuread.properties.riskLevelAggregated |
keyword |
riskLevelAggregated |
azuread.properties.riskLevelDuringSignIn |
keyword |
riskLevelDuringSignIn |
azuread.properties.riskReasons |
array |
|
azuread.properties.riskState |
keyword |
|
azuread.properties.scopes |
array |
|
azuread.properties.servicePrincipalId |
keyword |
|
azuread.properties.servicePrincipalName |
keyword |
|
azuread.properties.session_id |
keyword |
|
azuread.properties.source |
keyword |
|
azuread.properties.status.additionalDetails |
keyword |
|
azuread.properties.status.errorCode |
keyword |
|
azuread.properties.status.failureReason |
keyword |
|
azuread.properties.targetDeviceDisplayName |
keyword |
|
azuread.properties.targetDevicePrincipalName |
keyword |
|
azuread.properties.targetServicePrincipalAppRoleNewDisplayValue |
keyword |
|
azuread.properties.targetServicePrincipalDisplayName |
keyword |
|
azuread.properties.targetUserDisplayName |
keyword |
|
azuread.properties.targetUserPrincipalName |
keyword |
|
azuread.properties.tokenIssuerType |
keyword |
|
azuread.properties.uniqueTokenIdentifier |
keyword |
|
azuread.properties.userPrincipalObjectID |
keyword |
|
azuread.properties.userType |
keyword |
|
azuread.resourceId |
keyword |
|
azuread.resourceTenantId |
keyword |
|
azuread.resultDescription |
keyword |
|
azuread.resultSignature |
keyword |
|
azuread.servicePrincipalId |
keyword |
|
azuread.ssoExtensionVersion |
keyword |
|
azuread.tenantId |
keyword |
|
error.code |
keyword |
Error code describing the error. |
error.message |
match_only_text |
Error message. |
event.action |
keyword |
The action captured by the event. |
event.category |
keyword |
Event category. The second categorization field in the hierarchy. |
event.reason |
keyword |
Reason why this event happened, according to the source |
event.type |
keyword |
Event type. The third categorization field in the hierarchy. |
host.hostname |
keyword |
Hostname of the host. |
host.id |
keyword |
Unique host id. |
host.os.name |
keyword |
Operating system name, without the version. |
host.os.type |
keyword |
Which commercial OS family (one of: linux, macos, unix or windows). |
http.request.method |
keyword |
HTTP request method. |
http.response.status_code |
long |
HTTP response status code. |
log.level |
keyword |
Log level of the log event. |
service.name |
keyword |
Name of the service. |
service.type |
keyword |
The type of the service. |
source.geo.city_name |
keyword |
City name. |
source.geo.location |
geo_point |
Longitude and latitude. |
source.geo.region_name |
keyword |
Region name. |
source.ip |
ip |
IP address of the source. |
url.original |
wildcard |
Unmodified original url as seen in the event source. |
user.changes.group.id |
keyword |
Unique identifier for the group on the system/platform. |
user.changes.group.name |
keyword |
Name of the group. |
user.email |
keyword |
User email address. |
user.full_name |
keyword |
User's full name, if available. |
user.id |
keyword |
Unique identifier of the user. |
user.name |
keyword |
Short name or login of the user. |
user.target.group.id |
keyword |
Unique identifier for the group on the system/platform. |
user.target.group.name |
keyword |
Name of the group. |
user.target.id |
keyword |
Unique identifier of the user. |
user.target.name |
keyword |
Short name or login of the user. |
user_agent.name |
keyword |
Name of the user agent. |
user_agent.original |
keyword |
Unparsed user_agent string. |
For more information on the Intake Format, please find the code of the Parser, Smart Descriptions, and Supported Events here.