SentinelOne Singularity Identity
Overview
SentinelOne Singularity Identity is a cybersecurity solution that provides identity protection and zero-trust security by continuously monitoring and analyzing user behaviors to detect and prevent potential threats.
- Vendor: SentinelOne
- Supported environment: Cloud
- Detection based on: Telemetry
- Detection based on: Alert
Configure
This setup guide will show you how to pull events produced by SentinelOne Singularity Identity on Sekoia.io.
Generate API token
- Log in the SentinelOne Singularity console
-
On the left panel, click
Settings
-
Click
Users
-
On the left, click
Service Users
-
Click
Actions, then clickCreate New Service User
-
Type a name, a description and Select the expiration duration for the Service User
-
Click
Next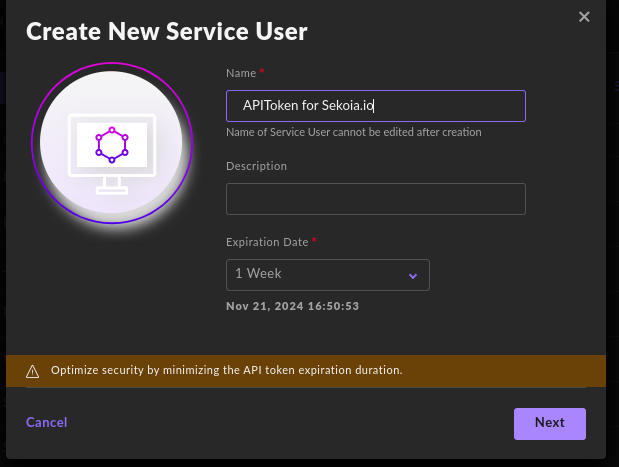
-
Select the scope of the access with the
viewerrole. We recommend using thesitescope. -
Click
Create User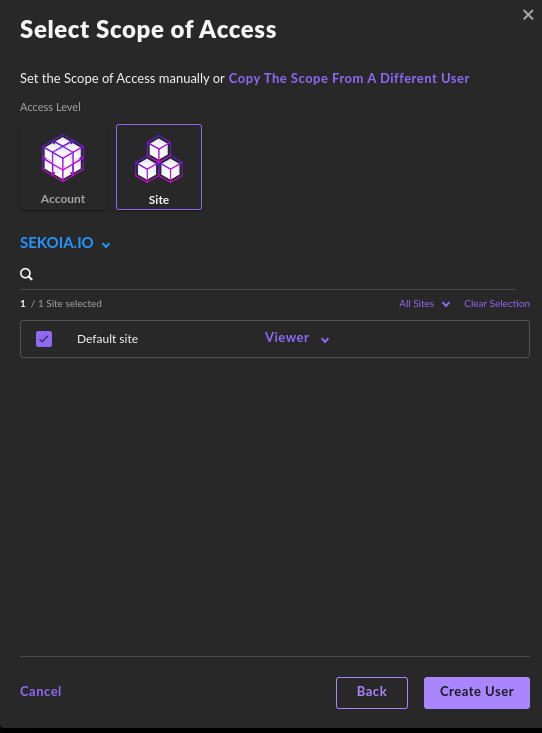
-
Copy and save the APIToken then click
Close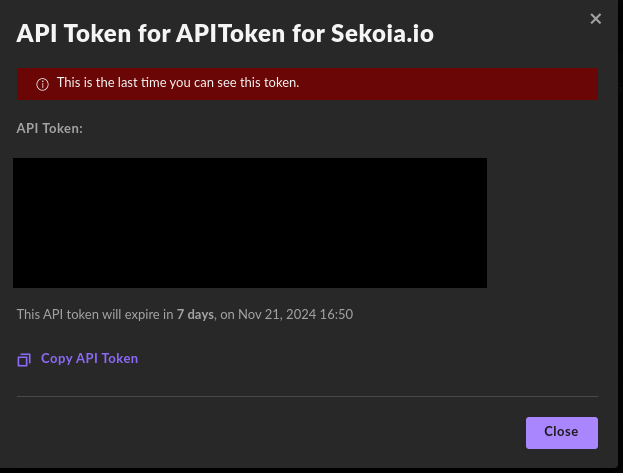
Create the intake in Sekoia.io
Go to the intake page and create a new intake from the format SentinelOne Identity. Copy the intake key.
Event Categories
The following table lists the data source offered by this integration.
| Data Source | Description |
|---|---|
Application logs |
activites performed on SentinelOne infrastructure are logged |
In details, the following table denotes the type of events produced by this integration.
| Name | Values |
|---|---|
| Kind | alert |
| Category | intrusion_detection |
| Type | info |
Transformed Events Samples after Ingestion
This section demonstrates how the raw logs will be transformed by our parsers. It shows the extracted fields that will be available for use in the built-in detection rules and hunting activities in the events page. Understanding these transformations is essential for analysts to create effective detection mechanisms with custom detection rules and to leverage the full potential of the collected data.
{
"message": "{\n \"id\": \"ba485919-e4c1-4496-9e2f-feb320f6841a\",\n \"name\": \"Domain Controller Discovery Detected\",\n \"description\": \"This event is raised when there is a query from an endpoint to find the domain controllers or AD Servers in the Active Directory Domain.\",\n \"detectedAt\": \"2024-11-22T05:35:09.000Z\",\n \"attackSurfaces\": [\n \"IDENTITY\"\n ],\n \"detectionSource\": {\n \"product\": \"Identity\"\n },\n \"status\": \"NEW\",\n \"assignee\": null,\n \"classification\": \"ENUMERATION\",\n \"confidenceLevel\": \"MALICIOUS\",\n \"firstSeenAt\": \"2024-11-22T05:35:09.000Z\",\n \"lastSeenAt\": \"2024-11-22T05:35:09.000Z\",\n \"process\": {\n \"cmdLine\": \"C:\\\\Windows\\\\system32\\\\net1 group \\\"Domain Controllers\\\" /domain\",\n \"file\": {\n \"path\": \"c:\\\\windows\\\\system32\\\\net1.exe\",\n \"sha1\": null,\n \"sha256\": \"18F76BC1F02A161EBDEDF3142273C186D05A836ADDCAAEE599194089FD59F398\",\n \"md5\": null\n },\n \"parentName\": null\n },\n \"result\": null,\n \"storylineId\": null\n}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T05:35:09Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when there is a query from an endpoint to find the domain controllers or AD Servers in the Active Directory Domain.",
"start": "2024-11-22T05:35:09Z",
"type": "info"
},
"@timestamp": "2024-11-22T05:35:09Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "C:\\Windows\\system32\\net1 group \"Domain Controllers\" /domain",
"executable": "c:\\windows\\system32\\net1.exe",
"hash": {
"sha256": "18F76BC1F02A161EBDEDF3142273C186D05A836ADDCAAEE599194089FD59F398"
},
"name": "net1.exe"
},
"related": {
"hash": [
"18F76BC1F02A161EBDEDF3142273C186D05A836ADDCAAEE599194089FD59F398"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "ba485919-e4c1-4496-9e2f-feb320f6841a",
"name": "Domain Controller Discovery Detected",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935322-7b49-71f0-89e0-f52562c26e53\", \"name\": \"Brute force attack - Mass Account Lockout\", \"description\": \"This event is raised when ADAssessor detects lockout of multiple accounts, which could be due to brute-force attempts or a password spray.\", \"detectedAt\": \"2024-11-22T09:09:48.731Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"UNKNOWN\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T09:09:48.731Z\", \"lastSeenAt\": \"2024-11-22T09:09:48.731Z\", \"process\": null, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T09:09:48.731000Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when ADAssessor detects lockout of multiple accounts, which could be due to brute-force attempts or a password spray.",
"start": "2024-11-22T09:09:48.731000Z",
"type": "info"
},
"@timestamp": "2024-11-22T09:09:48.731000Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "UNKNOWN",
"confidenceLevel": "MALICIOUS",
"id": "01935322-7b49-71f0-89e0-f52562c26e53",
"name": "Brute force attack - Mass Account Lockout",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935310-d00e-7616-81b9-fcb227ebb13d\", \"name\": \"Domain Controller Discovery Detected\", \"description\": \"This event is raised when there is a query from an endpoint to find the domain controllers or AD Servers in the Active Directory Domain.\", \"detectedAt\": \"2024-11-22T08:45:51.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T08:45:51.000Z\", \"lastSeenAt\": \"2024-11-22T08:45:51.000Z\", \"process\": {\"cmdLine\": \"Sharphound.exe\", \"file\": {\"path\": \"c:\\\\users\\\\administrator\\\\desktop\\\\ad_recon\\\\sharphound.exe\", \"sha1\": null, \"sha256\": \"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T08:45:51Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when there is a query from an endpoint to find the domain controllers or AD Servers in the Active Directory Domain.",
"start": "2024-11-22T08:45:51Z",
"type": "info"
},
"@timestamp": "2024-11-22T08:45:51Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "Sharphound.exe",
"executable": "c:\\users\\administrator\\desktop\\ad_recon\\sharphound.exe",
"hash": {
"sha256": "61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
},
"name": "sharphound.exe"
},
"related": {
"hash": [
"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "01935310-d00e-7616-81b9-fcb227ebb13d",
"name": "Domain Controller Discovery Detected",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935310-eb28-7a57-9c27-87843b2cec61\", \"name\": \"AD Service Account Enumeration Detected\", \"description\": \"This event is generated when LDAP queries for enumerating service accounts are detected from an endpoint.\", \"detectedAt\": \"2024-11-22T08:45:51.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T08:45:51.000Z\", \"lastSeenAt\": \"2024-11-22T08:45:51.000Z\", \"process\": {\"cmdLine\": \"Sharphound.exe\", \"file\": {\"path\": \"c:\\\\users\\\\administrator\\\\desktop\\\\ad_recon\\\\sharphound.exe\", \"sha1\": null, \"sha256\": \"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T08:45:51Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is generated when LDAP queries for enumerating service accounts are detected from an endpoint.",
"start": "2024-11-22T08:45:51Z",
"type": "info"
},
"@timestamp": "2024-11-22T08:45:51Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "Sharphound.exe",
"executable": "c:\\users\\administrator\\desktop\\ad_recon\\sharphound.exe",
"hash": {
"sha256": "61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
},
"name": "sharphound.exe"
},
"related": {
"hash": [
"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "01935310-eb28-7a57-9c27-87843b2cec61",
"name": "AD Service Account Enumeration Detected",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935310-c715-72c9-bbd9-dc1ff6a7ff1e\", \"name\": \"AD Domain Computer Enumeration Detected\", \"description\": \"This event is raised when there is a query from an endpoint to dump all the computers in the Active Directory Domain.\", \"detectedAt\": \"2024-11-22T08:45:50.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T08:45:50.000Z\", \"lastSeenAt\": \"2024-11-22T08:45:50.000Z\", \"process\": {\"cmdLine\": \"Sharphound.exe\", \"file\": {\"path\": \"c:\\\\users\\\\administrator\\\\desktop\\\\ad_recon\\\\sharphound.exe\", \"sha1\": null, \"sha256\": \"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T08:45:50Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when there is a query from an endpoint to dump all the computers in the Active Directory Domain.",
"start": "2024-11-22T08:45:50Z",
"type": "info"
},
"@timestamp": "2024-11-22T08:45:50Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "Sharphound.exe",
"executable": "c:\\users\\administrator\\desktop\\ad_recon\\sharphound.exe",
"hash": {
"sha256": "61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
},
"name": "sharphound.exe"
},
"related": {
"hash": [
"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "01935310-c715-72c9-bbd9-dc1ff6a7ff1e",
"name": "AD Domain Computer Enumeration Detected",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935310-cb9b-770e-96ee-632d4d21520b\", \"name\": \"AD ACL Enumeration\", \"description\": \"This event is generated when a command used to query or read the ACL's\\\\ Permission of any object in Active Directory.\", \"detectedAt\": \"2024-11-22T08:45:50.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T08:45:50.000Z\", \"lastSeenAt\": \"2024-11-22T08:45:50.000Z\", \"process\": {\"cmdLine\": \"Sharphound.exe\", \"file\": {\"path\": \"c:\\\\users\\\\administrator\\\\desktop\\\\ad_recon\\\\sharphound.exe\", \"sha1\": null, \"sha256\": \"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T08:45:50Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is generated when a command used to query or read the ACL's\\ Permission of any object in Active Directory.",
"start": "2024-11-22T08:45:50Z",
"type": "info"
},
"@timestamp": "2024-11-22T08:45:50Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "Sharphound.exe",
"executable": "c:\\users\\administrator\\desktop\\ad_recon\\sharphound.exe",
"hash": {
"sha256": "61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
},
"name": "sharphound.exe"
},
"related": {
"hash": [
"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "01935310-cb9b-770e-96ee-632d4d21520b",
"name": "AD ACL Enumeration",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935310-d4ba-7131-9e08-defa8b3aeb52\", \"name\": \"Domain Users Enumeration Detected\", \"description\": \"This event is raised when there is a query from an endpoint to dump all the users in the Active Directory Domain.\", \"detectedAt\": \"2024-11-22T08:45:50.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T08:45:50.000Z\", \"lastSeenAt\": \"2024-11-22T08:45:50.000Z\", \"process\": {\"cmdLine\": \"Sharphound.exe\", \"file\": {\"path\": \"c:\\\\users\\\\administrator\\\\desktop\\\\ad_recon\\\\sharphound.exe\", \"sha1\": null, \"sha256\": \"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T08:45:50Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when there is a query from an endpoint to dump all the users in the Active Directory Domain.",
"start": "2024-11-22T08:45:50Z",
"type": "info"
},
"@timestamp": "2024-11-22T08:45:50Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "Sharphound.exe",
"executable": "c:\\users\\administrator\\desktop\\ad_recon\\sharphound.exe",
"hash": {
"sha256": "61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
},
"name": "sharphound.exe"
},
"related": {
"hash": [
"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "01935310-d4ba-7131-9e08-defa8b3aeb52",
"name": "Domain Users Enumeration Detected",
"status": "NEW"
}
}
}
{
"message": "{\"id\":\"11111111-1111-1111-1111-111111111111\",\"name\":\"Compromised Password Detected\",\"description\":\"Current passwords of your users are exposed in a public breach database or are banned in your network. If left unchanged, attackers can use these passwords to start Dictionary, Password Spray, and Credential Stuffing attacks.\",\"detectedAt\":\"2025-04-03T14:43:16.805Z\",\"attackSurfaces\":[\"IDENTITY\"],\"detectionSource\":{\"product\":\"Identity\"},\"status\":\"NEW\",\"assignee\":null,\"classification\":\"UNKNOWN\",\"confidenceLevel\":null,\"firstSeenAt\":null,\"lastSeenAt\":null,\"process\":null,\"result\":\"UNMITIGATED\",\"storylineId\":null,\"analystVerdict\":\"UNDEFINED\",\"analytics\":{\"category\":\"BreachDetect\"},\"asset\":{\"agentUuid\":null,\"agentVersion\":null,\"category\":\"Identity\",\"name\":\"name_test\",\"osType\":null,\"osVersion\":\"\",\"type\":\"UNKNOWN\",\"subcategory\":\"Users and Groups\"},\"rawData\":{\"activity_id\":2,\"activity_name\":\"Update\",\"category_uid\":2,\"class_uid\":11111111,\"enrichments\":[{\"data\":{\"source\":\"\",\"Source URL\":\"\",\"Breach Publish Time\":0.0},\"name\":\"Source of Breach Details\",\"value\":\"\"}],\"finding_info\":{\"analytic\":{\"category\":\"BreachDetect\",\"type_id\":0},\"desc\":\"Current passwords of your users are exposed in a public breach database or are banned in your network. If left unchanged, attackers can use these passwords to start Dictionary, Password Spray, and Credential Stuffing attacks.\",\"title\":\"Compromised Password Detected\",\"uid\":\"22222222-2222-2222-2222-222222222222\",\"internal_uid\":\"11111111-1111-1111-1111-111111111111\"},\"metadata\":{\"product\":{\"name\":\"Identity\",\"vendor_name\":\"SentinelOne\"},\"version\":\"1.1.0-dev\"},\"remediation\":{\"result_id\":2},\"resources\":[{\"name\":\"name_test\",\"owner\":{\"domain\":\"domain.name\",\"name\":\"name_test\",\"org\":{\"name\":\"domain\"}},\"type\":\"identity::users_and_groups::ad_user\",\"uid\":\"33333333-3333-3333-3333-333333333333\",\"s1_metadata\":{\"group_name\":\"Default Group\",\"account_id\":\"1234567890123456789\",\"account_name\":\"Account Name\",\"group_id\":\"5555555555555555555\",\"mgmt_id\":19789,\"scope_id\":\"5555555555555555555\",\"scope_level\":\"Group\",\"site_id\":\"6666666666666666666\",\"site_name\":\"Default site\"},\"internal_uid\":\"aaaaaaaaaaaaaaaaaaaaaaaaaa\"}],\"severity_id\":3,\"status_id\":1,\"time\":\"1743691396805\",\"type_uid\":\"1111111101\",\"evidences\":[{\"actor\":{\"user\":{\"domain\":\"domain.name\",\"name\":\"name_test\",\"uid\":\"33333333-3333-3333-3333-333333333333\"}}}],\"verdict_id\":0,\"attack_surface_ids\":[4],\"s1_classification_id\":0,\"verdict_detail_id\":0,\"verdict_fidelity_id\":0}}",
"event": {
"category": "intrusion_detection",
"kind": "alert",
"provider": "Identity",
"reason": "Current passwords of your users are exposed in a public breach database or are banned in your network. If left unchanged, attackers can use these passwords to start Dictionary, Password Spray, and Credential Stuffing attacks.",
"type": "info"
},
"@timestamp": "2025-04-03T14:43:16.805000Z",
"host": {
"name": "name_test"
},
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"organization": {
"id": "1234567890123456789",
"name": "Account Name"
},
"related": {
"user": [
"name_test"
]
},
"sentinelone": {
"identity": {
"analystVerdict": "UNDEFINED",
"analyticsCategory": "BreachDetect",
"attackSurfaces": [
"IDENTITY"
],
"classification": "UNKNOWN",
"id": "11111111-1111-1111-1111-111111111111",
"name": "Compromised Password Detected",
"result": "UNMITIGATED",
"siteId": "6666666666666666666",
"siteName": "Default site",
"status": "NEW"
}
},
"user": {
"domain": "domain.name",
"name": "name_test"
}
}
{
"message": "{\n \"analystVerdict\": \"UNDEFINED\",\n \"analytics\": {\n \"category\": \"ADSecure-DC\"\n },\n \"asset\": {\n \"agentUuid\": \"123123123123123\",\n \"agentVersion\": \"AgentVersion1\",\n \"category\": \"Server\",\n \"name\": \"VM0001.LAB\",\n \"osType\": \"UNKNOWN\",\n \"osVersion\": \"1.1\",\n \"subcategory\": \"Other Server\",\n \"type\": \"UNKNOWN\"\n },\n \"assignee\": null,\n \"attackSurfaces\": [\n \"IDENTITY\"\n ],\n \"classification\": \"UNKNOWN\",\n \"confidenceLevel\": \"MALICIOUS\",\n \"description\": \"This event is generated when a DCSync attack is detected.\",\n \"detectedAt\": \"2024-12-11T13:11:48.487Z\",\n \"detectionSource\": {\n \"product\": \"Identity\"\n },\n \"firstSeenAt\": \"2024-12-11T13:11:48.487Z\",\n \"id\": \"19b5cab4-9fdc-49f9-9641-dae9ed9b1c3b\",\n \"lastSeenAt\": \"2024-12-11T13:11:48.487Z\",\n \"name\": \"DCSync Attack Detected\",\n \"process\": null,\n \"rawData\": {\n \"activity_id\": 2,\n \"activity_name\": \"Update\",\n \"attack_surface_ids\": [\n 4\n ],\n \"category_uid\": 2,\n \"class_uid\": 99602001,\n \"confidence_id\": 3,\n \"evidences\": [\n {\n \"actor\": {\n \"user\": {\n\"name\":\"test_user\", \"domain\": \"LAB\"\n }\n },\n \"dst_endpoint\": {\n \"hostname\": \"VM0001\",\n \"ip\": \"5.6.7.8\",\n \"uid\": \"xxxxx-xxxxx-xxxxx-xxxxxxxxxxx\"\n },\n \"src_endpoint\": {\n \"hostname\":\"tes.test\", \"ip\": \"1.2.3.4\"\n }\n }\n ],\n \"finding_info\": {\n \"analytic\": {\n \"category\": \"ADSecure-DC\",\n \"type_id\": 1,\n \"uid\": \"ADSecure-DC\"\n },\n \"attacks\": [\n {\n \"tactics\": [\n {\n \"name\": \"Credential Access\",\n \"uid\": \"TA006\"\n }\n ],\n \"technique\": {\n \"name\": \"OS Credential Dumping\",\n \"uid\": \"T1003\"\n },\n \"version\": \"ATT&CK v11\"\n }\n ],\n \"desc\": \"This event is generated when a DCSync attack is detected.\",\n \"first_seen_time\": \"1733922708487\",\n \"internal_uid\": \"d2dfca23-c7c7-409d-840c-cc0702ef7eb7\",\n \"kill_chain\": [\n {\n \"phase_id\": 2\n }\n ],\n \"last_seen_time\": \"1733922708487\",\n \"related_events\": [\n {\n \"message\": \"An authorized session has been detected with a certain privilege which could be result of an privilege escalation.\",\n \"severity_id\": 5,\n \"time\": \"1733922708487\",\n \"type\": \"Authorize Session: Other\",\n \"uid\": \"xxxxx-xxxxx-xxxxx-xxxxxxxxxxx\"\n }\n ],\n \"title\": \"DCSync Attack Detected\",\n \"uid\": \"xxxxx-xxxxx-xxxxx-xxxxxxxxxxx\"\n },\n \"message\": \"This event is generated when a DCSync attack is detected.\",\n \"metadata\": {\n \"extension\": {\n \"name\": \"s1\",\n \"uid\": \"996\",\n \"version\": \"0.1.0\"\n },\n \"product\": {\n \"name\": \"Identity\",\n \"vendor_name\": \"SentinelOne\"\n },\n \"uid\": \"xxxxx-xxxxx-xxxxx-xxxxxxxxxxx\",\n \"version\": \"1.1.0-dev\"\n },\n \"raw_data\": \"5001802:Attacker IP=1.2.3.4 Source Port=49970 Target IP=5.6.7.8 Target Port=49155 Severity=14 Domain=LAB userName=john.doe dc_host=VM00001 CA_STATUS=ALERT client_id=xxxxxxx-xxxxxx-xxxx-xxxxxxx subscriberId:6666\",\n \"resources\": [\n {\n \"internal_uid\": \"11111111111111111111111111\",\n \"name\": \"VM0001.LAB\",\n \"s1_metadata\": {\n \"account_id\": \"123123123123123123\",\n \"account_name\": \"EXAMPLE CORP\",\n \"group_id\": \"1234567890\",\n \"group_name\": \"Default Group\",\n \"mgmt_id\": 123123,\n \"scope_id\": \"1234567890\",\n \"scope_level\": \"Group\",\n \"site_id\": \"1234567890\",\n \"site_name\": \"Sekoia.io\"\n },\n \"type\": \"server::other_server::windows_server\",\n \"uid\": \"xxxxx-xxxxx-xxxxx-xxxxxxxxxxx\",\n \"version\": \"Microsoft Windows Server 2012 R2 Standard 64-bit\"\n }\n ],\n \"s1_classification_id\": 0,\n \"severity_id\": 5,\n \"status_id\": 1,\n \"time\": \"1733922708487\",\n \"type_name\": \"\",\n \"type_uid\": \"9960200101\",\n \"unmapped\": {},\n \"verdict_detail_id\": 0,\n \"verdict_id\": 0\n },\n \"result\": null,\n \"status\": \"NEW\",\n \"storylineId\": null\n}",
"event": {
"category": "intrusion_detection",
"end": "2024-12-11T13:11:48.487000Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is generated when a DCSync attack is detected.",
"start": "2024-12-11T13:11:48.487000Z",
"type": "info"
},
"@timestamp": "2024-12-11T13:11:48.487000Z",
"agent": {
"id": "123123123123123",
"version": "AgentVersion1"
},
"destination": {
"address": "VM0001",
"domain": "VM0001",
"ip": "5.6.7.8"
},
"host": {
"name": "VM0001.LAB",
"os": {
"family": "UNKNOWN",
"version": "1.1"
}
},
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"organization": {
"id": "123123123123123123",
"name": "EXAMPLE CORP"
},
"related": {
"hosts": [
"VM0001",
"tes.test"
],
"ip": [
"1.2.3.4",
"5.6.7.8"
],
"user": [
"test_user"
]
},
"sentinelone": {
"identity": {
"analystVerdict": "UNDEFINED",
"analyticsCategory": "ADSecure-DC",
"attackSurfaces": [
"IDENTITY"
],
"classification": "UNKNOWN",
"confidenceLevel": "MALICIOUS",
"id": "19b5cab4-9fdc-49f9-9641-dae9ed9b1c3b",
"name": "DCSync Attack Detected",
"siteId": "1234567890",
"siteName": "Sekoia.io",
"status": "NEW"
}
},
"source": {
"address": "tes.test",
"domain": "tes.test",
"ip": "1.2.3.4",
"subdomain": "tes"
},
"threat": {
"tactic": {
"id": [
"TA006"
],
"name": [
"Credential Access"
]
}
},
"user": {
"domain": "LAB",
"name": "test_user"
}
}
{
"message": "{\"id\": \"01935310-dc47-75de-8925-5f026bd5a705\", \"name\": \"LDAP Search Detected\", \"description\": \"This events is raised when a LDAP search Query is detected from the endpoint.\", \"detectedAt\": \"2024-11-22T08:45:50.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T08:45:50.000Z\", \"lastSeenAt\": \"2024-11-22T08:45:50.000Z\", \"process\": {\"cmdLine\": \"Sharphound.exe\", \"file\": {\"path\": \"c:\\\\users\\\\administrator\\\\desktop\\\\ad_recon\\\\sharphound.exe\", \"sha1\": null, \"sha256\": \"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T08:45:50Z",
"kind": "alert",
"provider": "Identity",
"reason": "This events is raised when a LDAP search Query is detected from the endpoint.",
"start": "2024-11-22T08:45:50Z",
"type": "info"
},
"@timestamp": "2024-11-22T08:45:50Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "Sharphound.exe",
"executable": "c:\\users\\administrator\\desktop\\ad_recon\\sharphound.exe",
"hash": {
"sha256": "61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
},
"name": "sharphound.exe"
},
"related": {
"hash": [
"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "01935310-dc47-75de-8925-5f026bd5a705",
"name": "LDAP Search Detected",
"status": "NEW"
}
}
}
{
"message": "{\n \"analystVerdict\": \"UNDEFINED\",\n \"analytics\": {\n \"category\": \"ThreatPath\"\n },\n \"asset\": {\n \"agentUuid\": null,\n \"agentVersion\": null,\n \"category\": \"Workstation\",\n \"name\": \"Unknown\",\n \"osType\": \"UNKNOWN\",\n \"osVersion\": \"\",\n \"subcategory\": \"Other Workstation\",\n \"type\": \"UNKNOWN\"\n },\n \"assignee\": null,\n \"attackSurfaces\": [\n \"IDENTITY\"\n ],\n \"classification\": \"UNKNOWN\",\n \"confidenceLevel\": \"MALICIOUS\",\n \"description\": \"This event is triggered when a new Privilege Account has been detected in the Active Directory.\",\n \"detectedAt\": \"2024-12-24T05:47:33.726Z\",\n \"detectionSource\": {\n \"product\": \"Identity\"\n },\n \"firstSeenAt\": \"2024-12-24T05:47:33.726Z\",\n \"id\": \"0193f734-d130-773a-815c-fbfe892a2635\",\n \"lastSeenAt\": \"2024-12-24T05:47:33.726Z\",\n \"name\": \"New AD Privilege Accounts Detected\",\n \"process\": null,\n \"rawData\": {\n \"activity_id\": 2,\n \"activity_name\": \"Update\",\n \"attack_surface_ids\": [\n 4\n ],\n \"category_uid\": 2,\n \"class_uid\": 99602001,\n \"confidence_id\": 3,\n \"evidences\": [\n {\n \"actor\": {\n \"user\": {}\n },\n \"dst_endpoint\": {},\n \"src_endpoint\": {}\n }\n ],\n \"finding_info\": {\n \"analytic\": {\n \"category\": \"ThreatPath\",\n \"type_id\": 1,\n \"uid\": \"ThreatPath\"\n },\n \"attacks\": [\n {\n \"tactics\": [\n {\n \"id\": \"xxx-xxx-xxxx\", \"name\": \"Credential Access\",\n \"uid\": \"TA006\"\n }\n ],\n \"technique\": {\n \"name\": \"Exploitation for Credential Access\",\n \"uid\": \"T1212\"\n },\n \"version\": \"ATT&CK v11\"\n }\n ],\n \"desc\": \"This event is triggered when a new Privilege Account has been detected in the Active Directory.\",\n \"first_seen_time\": \"1735026290990\",\n \"internal_uid\": \"316e8d31-9bc5-49b6-a0e2-49f9795bf9e9\",\n \"kill_chain\": [\n {\n \"phase_id\": 0\n }\n ],\n \"last_seen_time\": \"1735026290990\",\n \"title\": \"New AD Privilege Accounts Detected\",\n \"uid\": \"316e8d31-9bc5-49b6-a0e2-49f9795bf9e9\"\n },\n \"message\": \"This event is triggered when a new Privilege Account has been detected in the Active Directory.\",\n \"metadata\": {\n \"extension\": {\n \"name\": \"s1\",\n \"uid\": \"996\",\n \"version\": \"0.1.0\"\n },\n \"product\": {\n \"name\": \"Identity\",\n \"vendor_name\": \"SentinelOne\"\n },\n \"uid\": \"316e8d31-9bc5-49b6-a0e2-49f9795bf9e9\",\n \"version\": \"1.1.0-dev\"\n },\n \"raw_data\": \"5006406:AD Privilege Accounts credentials(S1-Local-Admin) detected in domain:LAB, ip:vm00001.lab at timestamp:1733309067716 of severity:8 subscriberId:6666\",\n \"resources\": [\n {\n \"internal_uid\": \"11111111111111111111111111\",\n \"name\": \"VM0001.LAB\",\n \"s1_metadata\": {\n \"account_id\": \"617755838952421242\",\n \"account_name\": \"EXAMPLE CORP\",\n \"group_id\": \"1107851598374945694\",\n \"group_name\": \"Default Group\",\n \"mgmt_id\": 86061,\n \"scope_id\": \"1107851598374945694\",\n \"scope_level\": \"Group\",\n \"site_id\": \"1107851598374945694\",\n \"site_name\": \"Sekoia.io\"\n },\n \"type\": \"server::other_server::windows_server\",\n \"uid\": \"70629f7d-e514-4a71-b88d-28a466d0fa02VM0001\",\n \"version\": \"Microsoft Windows Server 2012 R2 Standard 64-bit\"\n }\n ],\n \"s1_classification_id\": 0,\n \"severity_id\": 3,\n \"status_id\": 1,\n \"time\": \"1735026290990\",\n \"type_name\": \"\",\n \"type_uid\": \"9960200101\",\n \"unmapped\": {},\n \"verdict_detail_id\": 0,\n \"verdict_id\": 0\n },\n \"result\": null,\n \"status\": \"NEW\",\n \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-12-24T05:47:33.726000Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is triggered when a new Privilege Account has been detected in the Active Directory.",
"start": "2024-12-24T05:47:33.726000Z",
"type": "info"
},
"@timestamp": "2024-12-24T05:47:33.726000Z",
"host": {
"name": "VM0001.LAB",
"os": {
"family": "UNKNOWN"
}
},
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"organization": {
"id": "617755838952421242",
"name": "EXAMPLE CORP"
},
"sentinelone": {
"identity": {
"analystVerdict": "UNDEFINED",
"analyticsCategory": "ThreatPath",
"attackSurfaces": [
"IDENTITY"
],
"classification": "UNKNOWN",
"confidenceLevel": "MALICIOUS",
"id": "0193f734-d130-773a-815c-fbfe892a2635",
"name": "New AD Privilege Accounts Detected",
"siteId": "1107851598374945694",
"siteName": "Sekoia.io",
"status": "NEW"
}
},
"threat": {
"tactic": {
"id": [
"TA006"
],
"name": [
"Credential Access"
]
}
}
}
{
"message": "{\"id\": \"01935359-3eda-7903-93fc-af6a0e5d0a8f\", \"name\": \"Brute force attack - Mass Account Lockout\", \"description\": \"This event is raised when ADAssessor detects lockout of multiple accounts, which could be due to brute-force attempts or a password spray.\", \"detectedAt\": \"2024-11-22T10:09:37.779Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"UNKNOWN\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T10:09:37.779Z\", \"lastSeenAt\": \"2024-11-22T10:09:37.779Z\", \"process\": null, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T10:09:37.779000Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when ADAssessor detects lockout of multiple accounts, which could be due to brute-force attempts or a password spray.",
"start": "2024-11-22T10:09:37.779000Z",
"type": "info"
},
"@timestamp": "2024-11-22T10:09:37.779000Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "UNKNOWN",
"confidenceLevel": "MALICIOUS",
"id": "01935359-3eda-7903-93fc-af6a0e5d0a8f",
"name": "Brute force attack - Mass Account Lockout",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935358-ee81-7eb7-b57f-022c6f0019a9\", \"name\": \"Brute force attack - Mass Account Lockout\", \"description\": \"This event is raised when ADAssessor detects lockout of multiple accounts, which could be due to brute-force attempts or a password spray.\", \"detectedAt\": \"2024-11-22T10:09:17.184Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"UNKNOWN\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T10:09:17.184Z\", \"lastSeenAt\": \"2024-11-22T10:09:17.184Z\", \"process\": null, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T10:09:17.184000Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when ADAssessor detects lockout of multiple accounts, which could be due to brute-force attempts or a password spray.",
"start": "2024-11-22T10:09:17.184000Z",
"type": "info"
},
"@timestamp": "2024-11-22T10:09:17.184000Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "UNKNOWN",
"confidenceLevel": "MALICIOUS",
"id": "01935358-ee81-7eb7-b57f-022c6f0019a9",
"name": "Brute force attack - Mass Account Lockout",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"0193534d-63c1-7497-b854-b883425af3f5\", \"name\": \"Domain Controller Discovery Detected\", \"description\": \"This event is raised when there is a query from an endpoint to find the domain controllers or AD Servers in the Active Directory Domain.\", \"detectedAt\": \"2024-11-22T09:54:58.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T09:54:58.000Z\", \"lastSeenAt\": \"2024-11-22T09:54:58.000Z\", \"process\": {\"cmdLine\": \"\\\"C:\\\\Windows\\\\system32\\\\cmd.exe\\\"\", \"file\": {\"path\": \"c:\\\\windows\\\\system32\\\\cmd.exe\", \"sha1\": null, \"sha256\": \"4D89FC34D5F0F9BABD022271C585A9477BF41E834E46B991DEAA0530FDB25E22\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T09:54:58Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when there is a query from an endpoint to find the domain controllers or AD Servers in the Active Directory Domain.",
"start": "2024-11-22T09:54:58Z",
"type": "info"
},
"@timestamp": "2024-11-22T09:54:58Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "\"C:\\Windows\\system32\\cmd.exe\"",
"executable": "c:\\windows\\system32\\cmd.exe",
"hash": {
"sha256": "4D89FC34D5F0F9BABD022271C585A9477BF41E834E46B991DEAA0530FDB25E22"
},
"name": "cmd.exe"
},
"related": {
"hash": [
"4D89FC34D5F0F9BABD022271C585A9477BF41E834E46B991DEAA0530FDB25E22"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "0193534d-63c1-7497-b854-b883425af3f5",
"name": "Domain Controller Discovery Detected",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935347-abf7-7457-8467-e3443470e6f3\", \"name\": \"AD Domain Computer Enumeration Detected\", \"description\": \"This event is raised when there is a query from an endpoint to dump all the computers in the Active Directory Domain.\", \"detectedAt\": \"2024-11-22T09:45:51.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T09:45:51.000Z\", \"lastSeenAt\": \"2024-11-22T09:45:51.000Z\", \"process\": {\"cmdLine\": \"Sharphound.exe\", \"file\": {\"path\": \"c:\\\\users\\\\administrator\\\\desktop\\\\ad_recon\\\\sharphound.exe\", \"sha1\": null, \"sha256\": \"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T09:45:51Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when there is a query from an endpoint to dump all the computers in the Active Directory Domain.",
"start": "2024-11-22T09:45:51Z",
"type": "info"
},
"@timestamp": "2024-11-22T09:45:51Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "Sharphound.exe",
"executable": "c:\\users\\administrator\\desktop\\ad_recon\\sharphound.exe",
"hash": {
"sha256": "61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
},
"name": "sharphound.exe"
},
"related": {
"hash": [
"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "01935347-abf7-7457-8467-e3443470e6f3",
"name": "AD Domain Computer Enumeration Detected",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935347-b05a-7d28-a929-5294ee16628a\", \"name\": \"Domain Controller Discovery Detected\", \"description\": \"This event is raised when there is a query from an endpoint to find the domain controllers or AD Servers in the Active Directory Domain.\", \"detectedAt\": \"2024-11-22T09:45:51.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T09:45:51.000Z\", \"lastSeenAt\": \"2024-11-22T09:45:51.000Z\", \"process\": {\"cmdLine\": \"Sharphound.exe\", \"file\": {\"path\": \"c:\\\\users\\\\administrator\\\\desktop\\\\ad_recon\\\\sharphound.exe\", \"sha1\": null, \"sha256\": \"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T09:45:51Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when there is a query from an endpoint to find the domain controllers or AD Servers in the Active Directory Domain.",
"start": "2024-11-22T09:45:51Z",
"type": "info"
},
"@timestamp": "2024-11-22T09:45:51Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "Sharphound.exe",
"executable": "c:\\users\\administrator\\desktop\\ad_recon\\sharphound.exe",
"hash": {
"sha256": "61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
},
"name": "sharphound.exe"
},
"related": {
"hash": [
"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "01935347-b05a-7d28-a929-5294ee16628a",
"name": "Domain Controller Discovery Detected",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935342-d073-7ed0-8c5e-2373fc013310\", \"name\": \"Default Admin Account Usage\", \"description\": \"This event is raised for default administrator account logon anywhere in the domain.\", \"detectedAt\": \"2024-11-22T09:45:07.655Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"UNKNOWN\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T09:45:07.655Z\", \"lastSeenAt\": \"2024-11-22T09:45:07.655Z\", \"process\": null, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T09:45:07.655000Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised for default administrator account logon anywhere in the domain.",
"start": "2024-11-22T09:45:07.655000Z",
"type": "info"
},
"@timestamp": "2024-11-22T09:45:07.655000Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "UNKNOWN",
"confidenceLevel": "MALICIOUS",
"id": "01935342-d073-7ed0-8c5e-2373fc013310",
"name": "Default Admin Account Usage",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935322-cc3a-76cc-890b-a1c2d1b815d4\", \"name\": \"Brute force attack - Mass Account Lockout\", \"description\": \"This event is raised when ADAssessor detects lockout of multiple accounts, which could be due to brute-force attempts or a password spray.\", \"detectedAt\": \"2024-11-22T09:10:09.467Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"UNKNOWN\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T09:10:09.467Z\", \"lastSeenAt\": \"2024-11-22T09:10:09.467Z\", \"process\": null, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T09:10:09.467000Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when ADAssessor detects lockout of multiple accounts, which could be due to brute-force attempts or a password spray.",
"start": "2024-11-22T09:10:09.467000Z",
"type": "info"
},
"@timestamp": "2024-11-22T09:10:09.467000Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "UNKNOWN",
"confidenceLevel": "MALICIOUS",
"id": "01935322-cc3a-76cc-890b-a1c2d1b815d4",
"name": "Brute force attack - Mass Account Lockout",
"status": "NEW"
}
}
}
Extracted Fields
The following table lists the fields that are extracted, normalized under the ECS format, analyzed and indexed by the parser. It should be noted that infered fields are not listed.
| Name | Type | Description |
|---|---|---|
@timestamp |
date |
Date/time when the event originated. |
agent.id |
keyword |
Unique identifier of this agent. |
agent.version |
keyword |
Version of the agent. |
destination.domain |
keyword |
The domain name of the destination. |
destination.ip |
ip |
IP address of the destination. |
event.category |
keyword |
Event category. The second categorization field in the hierarchy. |
event.end |
date |
event.end contains the date when the event ended or when the activity was last observed. |
event.kind |
keyword |
The kind of the event. The highest categorization field in the hierarchy. |
event.provider |
keyword |
Source of the event. |
event.reason |
keyword |
Reason why this event happened, according to the source |
event.start |
date |
event.start contains the date when the event started or when the activity was first observed. |
event.type |
keyword |
Event type. The third categorization field in the hierarchy. |
host.name |
keyword |
Name of the host. |
host.os.family |
keyword |
OS family (such as redhat, debian, freebsd, windows). |
host.os.version |
keyword |
Operating system version as a raw string. |
observer.product |
keyword |
The product name of the observer. |
observer.vendor |
keyword |
Vendor name of the observer. |
organization.id |
keyword |
Unique identifier for the organization. |
organization.name |
keyword |
Organization name. |
process.command_line |
wildcard |
Full command line that started the process. |
process.executable |
keyword |
Absolute path to the process executable. |
process.hash.md5 |
keyword |
MD5 hash. |
process.hash.sha1 |
keyword |
SHA1 hash. |
process.hash.sha256 |
keyword |
SHA256 hash. |
process.name |
keyword |
Process name. |
process.parent.name |
keyword |
Process name. |
sentinelone.identity.analystVerdict |
keyword |
|
sentinelone.identity.analyticsCategory |
keyword |
|
sentinelone.identity.attackSurfaces |
keyword |
|
sentinelone.identity.classification |
keyword |
|
sentinelone.identity.confidenceLevel |
keyword |
|
sentinelone.identity.id |
keyword |
|
sentinelone.identity.name |
keyword |
|
sentinelone.identity.result |
keyword |
|
sentinelone.identity.siteId |
keyword |
|
sentinelone.identity.siteName |
keyword |
|
sentinelone.identity.status |
keyword |
|
sentinelone.identity.storyLineId |
keyword |
|
source.domain |
keyword |
The domain name of the source. |
source.ip |
ip |
IP address of the source. |
threat.tactic.id |
keyword |
Threat tactic id. |
threat.tactic.name |
keyword |
Threat tactic. |
user.domain |
keyword |
Name of the directory the user is a member of. |
user.name |
keyword |
Short name or login of the user. |
For more information on the Intake Format, please find the code of the Parser, Smart Descriptions, and Supported Events here.
Detection section
The following section provides information for those who wish to learn more about the detection capabilities enabled by collecting this intake. It includes details about the built-in rule catalog, event categories, and ECS fields extracted from raw events. This is essential for users aiming to create custom detection rules, perform hunting activities, or pivot in the events page.
Related Built-in Rules
The following Sekoia.io built-in rules match the intake SentinelOne Singularity Identity. This documentation is updated automatically and is based solely on the fields used by the intake which are checked against our rules. This means that some rules will be listed but might not be relevant with the intake.
SEKOIA.IO x SentinelOne Singularity Identity on ATT&CK Navigator
ACLight Discovering Privileged Accounts
Detects use of ACLight tool. This tool aims to discover privileged accounts by scanning the network.
- Effort: advanced
AMSI Deactivation Using Registry Key
The rule detects attempts to deactivate/disable the AMSI provider by deleting the associated registry key.
- Effort: master
AccCheckConsole Executing Dll
Detects suspicious LOLBIN AccCheckConsole execution with parameters as used to load an arbitrary DLL.
- Effort: advanced
Active Directory Data Export Using Csvde
Detects the use of Csvde, a command-line tool from Windows Server that can be used to export Active Directory data to CSV files. This export doesn't include password hashes, but can be used as a discovery tool to enumerate users, machines and group memberships.
- Effort: elementary
AdFind Usage
Detects the usage of the AdFind tool. AdFind.exe is a free tool that extracts information from Active Directory. Wizard Spider (Bazar, TrickBot, Ryuk), FIN6 and MAZE operators have used AdFind.exe to collect information about Active Directory organizational units and trust objects
- Effort: elementary
Add User to Privileged Group
Add user in a potential privileged group which can be used to elevate privileges on the system.
- Effort: advanced
Address Space Layout Randomization (ASLR) Alteration
ASLR is a security feature used by the Operating System to mitigate memory exploit, attacker might want to disable it
- Effort: intermediate
Adexplorer Usage
Detects the usage of Adexplorer, a legitimate tool from the Sysinternals suite that could be abused by attackers as it can saves snapshots of the Active Directory Database.
- Effort: advanced
Adidnsdump Enumeration
Detects use of the tool adidnsdump for enumeration and discovering DNS records.
- Effort: advanced
Advanced IP Scanner
Detects the use of Advanced IP Scanner. Seems to be a popular tool for ransomware groups.
- Effort: master
AppleScript Password Prompt
Detects when a prompt is displayed to gain credentials. This technique is used by MacOS malware to obtain the user's password.
- Effort: advanced
Attempt to Disable Gatekeeper Execution Control
Detects attempts to disable Gatekeeper through the command line. Gatekeeper is a macOS feature designed to ensure that only trusted, signed software can be executed.
- Effort: elementary
Audio Capture via PowerShell
Detects audio capture via PowerShell Cmdlet
- Effort: intermediate
AutoIt3 Execution From Suspicious Folder
Detects AutoIt3 execution from an unusual/suspicious folder. Legitimate folders are "Program Files" and "AppData\Local". AutoIt3.exe is a legitimate process used to execute AutoIt program files, which are used by legitimate software, custom scripts, but also malware. Finding AutoIt3 execution from unusual/suspicious folder can help detect malware activities, such as DarkGate execution. The detection rule can be tailored to your environment and your use of AutoIt3 by filtering out folder's execution of legitimate applications or scripts.
- Effort: advanced
Autorun Keys Modification
Detects modification of autostart extensibility point (ASEP) in registry. Prerequisites are Logging for Registry events in the Sysmon configuration (events 12 and 13).
- Effort: master
AzureEdge in Command Line
Detects use of azureedge in the command line.
- Effort: advanced
BITSAdmin Download
Detects command to download file using BITSAdmin, a built-in tool in Windows. This technique is used by several threat actors to download scripts or payloads on infected system.
- Effort: advanced
BazarLoader Persistence Using Schtasks
Detects possible BazarLoader persistence using schtasks. BazarLoader will create a Scheduled Task using a specific command line to establish its persistence.
- Effort: intermediate
Bloodhound and Sharphound Tools Usage
Detects default process names and default command line parameters used by Bloodhound and Sharphound tools.
- Effort: intermediate
Blue Mockingbird Malware
Attempts to detect system changes made by Blue Mockingbird
- Effort: elementary
Burp Suite Tool Detected
Burp Suite is a cybersecurity tool. When used as a proxy service, its purpose is to intercept packets and modify them to send them to the server. Burp Collaborator is a network service that Burp Suite uses to help discover many kinds of vulnerabilities (vulnerabilities scanner).
- Effort: intermediate
CMSTP Execution
Detects various indicators of Microsoft Connection Manager Profile Installer execution
- Effort: intermediate
COM Hijack Via Sdclt
Detects changes to 'HKCU\Software\Classes\Folder\shell\open\command\DelegateExecute', to bypass UAC using 'sdclt.exe'.
- Effort: intermediate
Capture a network trace with netsh.exe
Detects capture a network trace via netsh.exe trace functionality
- Effort: advanced
CertOC Loading Dll
Detects when a user installs certificates by using CertOC.exe to loads the target DLL file.
- Effort: intermediate
Certificate Authority Modification
Installation of new certificate(s) in the Certificate Authority can be used to trick user when spoofing website or to add trusted destinations.
- Effort: master
Certify Or Certipy
Detects the use of certify and certipy which are two different tools used to enumerate and abuse Active Directory Certificate Services.
- Effort: advanced
Change Default File Association
When a file is opened, the default program used to open the file (also called the file association or handler) is checked. File association selections are stored in the Windows Registry and can be edited by users, administrators, or programs that have Registry access or by administrators using the built-in assoc utility. Applications can modify the file association for a given file extension to call an arbitrary program when a file with the given extension is opened.
- Effort: advanced
Chflags Hidden
Detects the use of the hidden flag by the utility chflags to hide files and directories.
- Effort: advanced
Clear EventLogs Through CommandLine
Detects a command that clears event logs which could indicate an attempt from an attacker to erase its previous traces.
- Effort: intermediate
Cmd.exe Used To Run Reconnaissance Commands
Detects command lines with suspicious args
- Effort: advanced
Cmdkey Cached Credentials Recon
Detects usage of cmdkey to look for cached credentials.
- Effort: intermediate
Cobalt Strike Default Beacons Names
Detects the default names of Cobalt Strike beacons / payloads.
- Effort: intermediate
Commonly Used Commands To Stop Services And Remove Backups
Detects specific commands used regularly by ransomwares to stop services or remove backups
- Effort: master
Component Object Model Hijacking
Detects component object model hijacking. An attacker can establish persistence with COM objects.
- Effort: advanced
Compress Data for Exfiltration via Archiver
Detects data compressed by specific tools.
- Effort: master
Compression Followed By Suppression
Detects when a file is compressed and deleted.
- Effort: advanced
Container Credential Access
Adversaries could abuse containers tools to obtain credential like Kubernetes secret or Kubernetes service account access token
- Effort: intermediate
Control Panel Items
Detects the malicious use of a control panel item
- Effort: advanced
Copy Of Legitimate System32 Executable
A script has copied a System32 executable.
- Effort: intermediate
Copying Browser Files With Credentials
Detects copy of sensitive data (passwords, cookies, credit cards) included in web browsers files.
- Effort: elementary
Copying Sensitive Files With Credential Data
Detects copy of files with well-known filenames (sensitive files with credential data) using esentutl. This requires Windows Security event log with the Detailed File Share logging policy enabled.
- Effort: elementary
Correlation Multi Service Disable
The rule detects a high number of services stopped or de-activated in a short period of time.
- Effort: master
Correlation Netcat Infection Chain
Detect netcat connection to download et execute payload via piped bash
- Effort: elementary
Correlation Potential DNS Tunnel
Detects domain name which is longer than 62 characters and requested at least 50 times in a 10 minutes range time. Long domain names are distinctive of DNS tunnels.
- Effort: advanced
Correlation PowerShell Suspicious DLL Loading
Detect some suspicious Windows DLL Loading where some PowerShell activity from the binary itself, followed by the same DLL process spawning other process. This is related to the usage of a PowerShell Named Pipe IPC from the DLL.
- Effort: intermediate
Correlation Priv Esc Via Remote Thread
Detect a process that obtains system privilege via a remote thread
- Effort: intermediate
Credential Harvesting Via Vaultcmd.exe
Detects when the process vaultcmd is used for credential harvesting.
- Effort: advanced
Cryptomining
Detection of domain names potentially related to cryptomining activities.
- Effort: master
Csrss Wrong Parent
The csrss.exe process (csrss stands for Client / Server Runtime Subsystem) is a generic Windows process used to manage windows and Windows graphics. This rule analyse if the parent of this process is a legitimate one or not.
- Effort: master
DHCP Callout DLL Installation
Detects the installation of a Callout DLL via CalloutDlls and CalloutEnabled parameter in Registry, which can be used to execute code in context of the DHCP server (restart required).
- Effort: intermediate
DNS Exfiltration and Tunneling Tools Execution
Well-known DNS exfiltration tools execution
- Effort: intermediate
DNS Query For Iplookup
Detects dns query of observables tagged as iplookup.
- Effort: master
DNS ServerLevelPluginDll Installation
Detects the installation of a plugin DLL via ServerLevelPluginDll parameter in Windows Registry or in command line, which can be used to execute code in context of the DNS server (restart required). To fully use this rule, prerequesites are logging for Registry events in the Sysmon configuration (events 12, 13 and 14).
- Effort: master
DNS Tunnel Technique From MuddyWater
Detecting DNS Tunnel Activity For Muddywater intrusion set. This is the loading of a specific DLL from an Excel macro which is detected.
- Effort: elementary
Data Compressed With Rar
An adversary may compress data in order to make it portable and minimize the amount of data sent over the network, this could be done the popular rar command line program.
- Effort: master
Data Compressed With Rar With Password
An adversary may compress data in order to make it portable and minimize the amount of data sent over the network, this could be done the popular rar command line program. This is a more specific one for rar where the arguments allow to encrypt both file data and headers with a given password.
- Effort: intermediate
Debugging Software Deactivation
Deactivation of some debugging softwares using taskkill command. It was observed being used by Ransomware operators.
- Effort: elementary
Default Encoding To UTF-8 PowerShell
Detects PowerShell encoding to UTF-8, which is used by Sliver implants. The command line just sets the default encoding to UTF-8 in PowerShell.
- Effort: advanced
Disable .NET ETW Through COMPlus_ETWEnabled
Detects potential adversaries stopping ETW providers recording loaded .NET assemblies. Prerequisites are logging for Registry events or logging command line parameters (both is better). Careful for registry events, if SwiftOnSecurity's SYSMON default configuration is used, you will need to update the configuration to include the .NETFramework registry key path. Same issue with Windows 4657 EventID logging, the registry path must be specified.
- Effort: intermediate
Disable Task Manager Through Registry Key
Detects commands used to disable the Windows Task Manager by modifying the proper registry key in order to impair security tools. This technique is used by the Agent Tesla RAT, among others.
- Effort: elementary
Disable Windows Defender Credential Guard
Detects registry keys being changed to disable Windows Defender Credential Guard. The rule requires to log Registry Keys modifications or creations, which can be done using Sysmon Event IDs 12,13 and 14.
- Effort: master
Disabled IE Security Features
Detects from the command lines or the registry, changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features. This has been used by attackers during Operation Ke3chang.
- Effort: advanced
Discovery Commands Correlation
Detects some frequent discovery commands used by some ransomware operators.
- Effort: intermediate
Dism Disabling Windows Defender
Detects windows defender disabled by dism.
- Effort: advanced
Dllhost Wrong Parent
Dllhost.exe is a process belonging to Microsoft Windows Operating System. The dllhost.exe file manages DLL based applications. This rule analyse if the parent of this process is a legitimate one or not.
- Effort: master
Docker Escape Bind Mount
Catch Docker escape via mount escape followed by chroot
- Effort: intermediate
Domain Group And Permission Enumeration
Detects adversaries attempts to find domain-level groups and permission settings. Commands such as net group /domain of the Net utility can list domain-level groups The knowledge of domain-level permission groups can help adversaries determine which groups exist and which users belong to a particular group. Adversaries may use this information to determine which users have elevated permissions, such as domain administrators. Wizard Spider, FIN6, and other groups used net in their campaigns.
- Effort: advanced
Domain Trust Discovery Through LDAP
Detects attempts to gather information on domain trust relationships that may be used to identify lateral movement opportunities. "trustedDomain" which is detected here is a Microsoft Active Directory ObjectClass Type that represents a domain that is trusted by, or trusting, the local AD DOMAIN. Several tools are using LDAP queries in the end to get the information (DSQuery, sometimes ADFind as well, etc.)
- Effort: elementary
Dscl Authonly
Detects the use of the command dscl with authonly used to verify the password of a user and for authentification. An attacker can abuse this command to gain credentials.
- Effort: advanced
Dynamic DNS Contacted
Detect communication with dynamic dns domain. This kind of domain is often used by attackers. This rule can trigger false positive in non-controlled environment because dynamic dns is not always malicious.
- Effort: master
Dynamic Linker Hijacking From Environment Variable
LD_PRELOAD and LD_LIBRARY_PATH are environment variables used by the Operating System at the runtime to load shared objects (library.ies) when executing a new process, attacker can overwrite this variable to attempts a privileges escalation.
- Effort: master
ETW Tampering
Detects a command that clears or disables any ETW Trace log which could indicate a logging evasion
- Effort: intermediate
Elevated Msiexec Via Repair Functionality
Detects when msiexec.exe is used with the repair functionality. The process gains elevated privileges. Attackers can use this to exploit the CVE-2024-38014.
- Effort: master
Elevated Shell Launched By Browser
Detects when openwith.exe is launched with privileges followed by a browser launching an elevated shell. Related to the CVE-2024-38014.
- Effort: master
Elise Backdoor
Detects Elise backdoor activity as used by Lotus Blossom
- Effort: elementary
Empire Monkey Activity
Detects EmpireMonkey APT reported Activity
- Effort: elementary
Enable Root Account With Dsenableroot
Detects when root is enabled. Attackers can use this as a mean of persistence since root is disabled by default.
- Effort: elementary
Enabling Restricted Admin Mode
Detects when the restricted admin mode is enabled.
- Effort: elementary
Equation Group DLL_U Load
Detects a specific tool and export used by EquationGroup
- Effort: elementary
Erase Shell History
Malware and attacker try to reduce their fingerprints on compromised host by deleting shell history.
- Effort: advanced
EvilProxy Phishing Domain
Detects subdomains potentially generated by the EvilProxy adversary-in-the-middle phishing platform. Inspect the other subdomains of the domain to identify the landing page, and determine if the user submitted credentials. This rule has a small percentage of false positives on legitimate domains.
- Effort: intermediate
Exchange Mailbox Export
Detection of a standard Exchange Mailbox export, which stores all mails from a user in a pst file, from command line or PowerShell script.
- Effort: intermediate
Exchange Server Spawning Suspicious Processes
Look for Microsoft Exchange Server’s Unified Messaging service spawning suspicious sub-processes, suggesting exploitation of CVE-2021-26857 vulnerability.
- Effort: intermediate
Exfiltration And Tunneling Tools Execution
Execution of well known tools for data exfiltration and tunneling
- Effort: advanced
Exfiltration Domain
Detects traffic toward a domain flagged as a possible exfiltration vector.
- Effort: master
Exfiltration Domain In Command Line
Detects commands containing a domain linked to http exfiltration.
- Effort: intermediate
Exfiltration Via Pscp
Detects the use of pscp which is a file sharing services.
- Effort: advanced
Exploit For CVE-2015-1641
Detects Winword process starting uncommon sub process MicroScMgmt.exe as used in exploits for CVE-2015-1641
- Effort: elementary
Exploit For CVE-2017-0261 Or CVE-2017-0262
Detects Winword starting uncommon sub process FLTLDR.exe as used in exploits for CVE-2017-0261 and CVE-2017-0262 through command line or PowerShell script. This is a very basic detection method relying on the rare usage of EPS files from Winword.
- Effort: advanced
Explorer Process Executing HTA File
Detects a suspicious execution of an HTA file by the explorer.exe process. This unusual activity was observed when running IcedID malspam.
- Effort: intermediate
FLTMC command usage
Detects the use of fltmc to list and load/unload a filter driver.
- Effort: advanced
Fail2ban Unban IP
An IP was ubaned by Fail2ban. It could be use to allow malicous traffic.
- Effort: advanced
File Or Folder Permissions Modifications
Adversaries may modify file or directory permissions/attributes to evade access control lists (ACLs) and access protected files.
- Effort: master
Formbook Hijacked Process Command
Detects process hijacked by Formbook malware which executes specific commands to delete the dropper or copy browser credentials to the database before sending them to the C2.
- Effort: intermediate
FromBase64String Command Line
Detects suspicious FromBase64String expressions in command line arguments.
- Effort: master
Generic Password Discovery
Detects when the security utility is used to access passwords in a keychain.
- Effort: advanced
Generic-reverse-shell-oneliner
To bypass some security equipement or for a sack of simplicity attackers can open raw reverse shell using shell commands
- Effort: intermediate
Gpresult Usage
Detects when an account uses gpresult to get information on gpo.
- Effort: advanced
Gpscript Suspicious Parent
Gpscript defines GPO scripts for users and applies them to login / logout sessions. This rule checks if the parent of this process is the supposed one (svchost) or not.
- Effort: intermediate
Grabbing Sensitive Hives Via Reg Utility
Detects dump of SAM, System or Security hives using reg.exe utility. Adversaries may attempt to dump these Windows Registry to retrieve password hashes and access credentials.
- Effort: master
HTA Infection Chains
Detect the creation of a ZIP file and an HTA file as it is often used in infection chains. Furthermore it also detects the use of suspicious processes launched by explorer.exe combined with the creation of an HTA file, since it is also often used in infection chains (LNK - HTA for instance).
- Effort: advanced
HTML Smuggling Suspicious Usage
Based on several samples from different botnets, this rule aims at detecting HTML infection chain by looking for HTML created files followed by suspicious files being executed.
- Effort: advanced
HackTools Suspicious Names
Quick-win rule to detect the default process names or file names of several HackTools.
- Effort: advanced
HackTools Suspicious Process Names In Command Line
Detects the default process name of several HackTools and also check in command line. This rule is here for quickwins as it obviously has many blind spots.
- Effort: intermediate
Hiding Files With Attrib.exe
Detects usage of attrib.exe to hide files from users.
- Effort: advanced
High Privileges Network Share Removal
Detects high privileges shares being deleted with the net share command.
- Effort: intermediate
ICacls Granting Access To All
Detects suspicious icacls command granting access to all, used by the ransomware Ryuk to delete every access-based restrictions on files and directories. ICacls is a built-in Windows command to interact with the Discretionary Access Control Lists (DACLs) which can grand adversaries higher permissions on specific files and folders.
- Effort: elementary
ISO LNK Infection Chain
Detection of an ISO (or any other similar archive file) downloaded file, followed by a child-process of explorer, which is characteristic of an infection using an ISO containing an LNK file. For events with host.name.
- Effort: master
IcedID Execution Using Excel
Detects Excel spawning a process (rundll32 or wmic) running suspicious command-line. This behaviour could correspond to IcedID activity.
- Effort: elementary
Impacket Wmiexec Module
Detection of impacket's wmiexec example, used by attackers to execute commands remotely.
- Effort: elementary
Inhibit System Recovery Deleting Backups
Detects adversaries attempts to delete backups or inhibit system recovery. This rule relies on differents known techniques using Windows events logs from Sysmon (ID 1), and PowerShell (ID 4103, 4104).
- Effort: intermediate
Interactive Terminal Spawned via Python
Identifies when a terminal (tty) is spawned via Python. Attackers may upgrade a simple reverse shell to a fully interactive tty after obtaining initial access to a host.
- Effort: advanced
Invoke-TheHash Commandlets
Detects suspicious Invoke-TheHash PowerShell commandlet used for performing pass the hash WMI and SMB tasks.
- Effort: elementary
KeePass Config XML In Command-Line
Detects a command-line interaction with the KeePass Config XML file. It could be used to retrieve informations or to be abused for persistence.
- Effort: intermediate
Kernel Module Alteration
Kernel module installation can be used to configure system settings to automatically execute a program during system boot or logon to maintain persistence or gain higher-level privileges on compromised systems. The prerequisites are to enable monitoring of the finit_module, init_module, delete_module syscalls using Auditbeat.
- Effort: advanced
Lazarus Loaders
Detects different loaders used by the Lazarus Group APT
- Effort: elementary
Legitimate Process Execution From Unusual Folder
Detects the execution of a legitimate, windows built-in process name from an unusual / suspicious folder. Legitimate folders are c:\windows\system32\, \SystemRoot\system32\, c:\windows\syswow64\ and c:\windows\winsxs. Many malwares/attackers use legitimate names to masquerade but if they are not Administrator yet, they often can't write file into these legitimate folders.
- Effort: advanced
Leviathan Registry Key Activity
Detects registry key used by Leviathan APT in Malaysian focused campaign.
- Effort: elementary
Linux Bash Reverse Shell
To bypass some security equipement or for a sack of simplicity attackers can open raw reverse shell using shell commands
- Effort: intermediate
Linux Masquerading Space After Name
This detection rule identifies a process created from an executable with a space appended to the end of the name.
- Effort: intermediate
Linux Remove Immutable Attribute
Adversaries may used chattr utility to alter file and folder attributes to control sudden operations like the deletion and modification of files.
- Effort: intermediate
Linux Shared Lib Injection Via Ldso Preload
Detect ld.so.preload modification for shared lib injection, technique used by attackers to load arbitrary code into process
- Effort: intermediate
Linux Suspicious Nohup Exec
Detects suspicious usage of nohup which could be leveraged by an attacker to keep a process running or break out from restricted environments
- Effort: intermediate
Linux Suspicious Search
Adversaries may search for private key on compromised systems
- Effort: intermediate
Listing Systemd Environment
Detects a listing of systemd environment variables. This command could be used to do reconnaissance on a compromised host.
- Effort: advanced
Logon Scripts (UserInitMprLogonScript)
Detects creation or execution of UserInitMprLogonScript persistence method. The rule requires to log for process command lines and registry creations or update, which can be done using Sysmon Event IDs 1, 12, 13 and 14.
- Effort: advanced
Logonui Wrong Parent
Logonui.exe is a file associated with the Logon user interface. The login user interface is an essential part of the Windows operating system. It doesn't only make it easy for the user to log in to the PC but also determines whether the user has logged in and logged out correctly and makes it easy to switch between users. This rule checks if the parent of this process is a legitimate one or not.
- Effort: master
Lsass Wrong Parent
Lsass ensures the identification of users (domain users or local users). Domain users are identified based on information in the Active Directory. Local users are identified based on information from the Security Account Manager (SAM) local database. This rule checks if the parent of this process is a legitimate one or not.
- Effort: master
MMC Spawning Windows Shell
Detects a Windows command line executable started from MMC process
- Effort: master
MMC20 Lateral Movement
Detects MMC20.Application Lateral Movement; specifically looks for the spawning of the parent MMC.exe with a command line of "-Embedding" as a child of svchost.exe.
- Effort: intermediate
MOFComp Execution
Detects rare usage of the Managed Object Format (MOF) compiler on Microsoft Windows. This could be abused by some attackers to load WMI classes.
- Effort: intermediate
MS Office Product Spawning Exe in User Dir
Detects an executable in the users directory started from Microsoft Word, Excel, Powerpoint, Publisher or Visio. This is a common technique used by attackers with documents embedding macros. It requires Windows command line logging events.
- Effort: master
MSBuild Abuse
Detection of MSBuild uses by attackers to infect an host. Focuses on XML compilation which is a Metasploit payload.
- Effort: intermediate
Malicious Browser Extensions
Detects browser extensions being loaded with the --load-extension and -base-url options, which works on Chromium-based browsers. We are looking for potentially malicious browser extensions. These extensions can get access to informations.
- Effort: advanced
Malspam Execution Registering Malicious DLL
Detects the creation of a file in the C:\Datop folder, or DLL registering a file in the C:\Datop folder. Files located in the Datop folder are very characteristic of malspam execution related to Qakbot or SquirrelWaffle. Prerequisites are Logging for File Creation events, which can be done in the Sysmon configuration (events 11), for the first part of the pattern (TargetFilename).
- Effort: elementary
Malware Persistence Registry Key
Detects registry key used by several malware, especially Formbook spyware in two ways, either the Sysmon registry events, or the commands line.
- Effort: master
MalwareBytes Uninstallation
Detects command line being used by attackers to uninstall Malwarebytes.
- Effort: intermediate
MavInject Process Injection
Detects process injection using the signed Windows tool Mavinject32.exe (which is a LOLBAS)
- Effort: intermediate
Meterpreter or Cobalt Strike Getsystem Service Installation
Detects the use of getsystem Meterpreter/Cobalt Strike command by detecting some of the techniques being used (technique 1,2 and 5).
- Effort: elementary
Microsoft Defender Antivirus Disable Scheduled Tasks
The rule detects attempts to deactivate/disable Windows Defender scheduled tasks via command line or PowerShell scripts.
- Effort: intermediate
Microsoft Defender Antivirus Disable SecurityHealth
The rule detects attempts to deactivate/disable Windows Defender SecurityHealth through command line, PowerShell scripts, and registry. To fully use this rule Windows Registry logging is recommended.
- Effort: intermediate
Microsoft Defender Antivirus Disable Services
The rule detects attempts to deactivate/disable Windows Defender through command line and registry.
- Effort: intermediate
Microsoft Defender Antivirus Disable Using Registry
The rule detects attempts to deactivate/disable Microsoft Defender Antivirus using registry modification via command line or PowerShell scripts.
- Effort: master
Microsoft Defender Antivirus Disabled Base64 Encoded
Detects attempts to deactivate/disable Windows Defender through base64 encoded PowerShell command line or scripts.
- Effort: intermediate
Microsoft Defender Antivirus History Directory Deleted
Windows Defender history directory has been deleted. This could be an attempt by an attacker to remove its traces.
- Effort: elementary
Microsoft Defender Antivirus Restoration Abuse
The rule detects attempts to abuse Windows Defender file restoration tool. The Windows Defender process is allowed to write files in its own protected directory. This functionality can be used by a threat actor to overwrite Windows Defender files in order to prevent it from running correctly or use Windows Defender to execute a malicious DLL.
- Effort: intermediate
Microsoft Defender Antivirus Set-MpPreference Base64 Encoded
Detects changes of preferences for Windows Defender through command line or PowerShell scripts. Configure Windows Defender using base64-encoded commands is suspicious and could be related to malicious activities.
- Effort: intermediate
Microsoft Defender Antivirus Signatures Removed With MpCmdRun
Detects attempts to remove Windows Defender Signatures using MpCmdRun legitimate Windows Defender executable. No signatures mean Windows Defender will be less effective (or completely useless depending on the option used).
- Effort: elementary
Microsoft Exchange PowerShell Snap-Ins To Export Exchange Mailbox Data
Detects PowerShell SnapIn command line or PowerShell script, often used with Get-Mailbox to export Exchange mailbox data.
- Effort: intermediate
Microsoft IIS Module Installation
Detects the installation of a new IIS module from the command line. It can used used to backdoor an IIS/OWA/Sharepoint server.
- Effort: advanced
Microsoft Office Macro Security Registry Modifications
Detects registry changes allowing an attacker to make Microsoft Office products runs Macros without warning. Events are collected either from ETW/Sysmon/EDR depending of the integration.
- Effort: master
Microsoft Office Product Spawning Windows Shell
Detects a Windows command or scripting interpreter executable started from Microsoft Word, Excel, Powerpoint, Publisher and Visio. This typically indicates the parent process launched a malicious macro, or run an exploit. This infection vector is very common and could lead to the deployment of harmful malware.
- Effort: master
Microsoft Office Spawning Script
Detects Microsoft Office process (word, excel, powerpoint) spawning wscript.exe or cscript.exe. This typically indicates the parent process launched a malicious macro, or run an exploit. This infection vector is very common and could lead to the deployment of harmful malware.
- Effort: intermediate
Mimikatz Basic Commands
Detects Mimikatz most popular commands.
- Effort: elementary
Msdt (Follina) File Browse Process Execution
Detects various Follina vulnerability exploitation techniques. This is based on the Compatability Troubleshooter which is abused to do code execution.
- Effort: elementary
Mshta JavaScript Execution
Identifies suspicious mshta.exe commands that execute JavaScript supplied as a command line argument.
- Effort: elementary
Mustang Panda Dropper
Detects specific process parameters as used by Mustang Panda droppers
- Effort: elementary
NTDS.dit File Interaction Through Command Line
Detects interaction with the file NTDS.dit through command line. This is usually really suspicious and could indicate an attacker trying copy the file to then look for users password hashes.
- Effort: intermediate
Net.exe User Account Creation
Identifies creation of local users via the net.exe command
- Effort: master
NetSh Used To Disable Windows Firewall
Detects NetSh commands used to disable the Windows Firewall
- Effort: advanced
Netsh Allow Command
Netsh command line to allow a program to pass through firewall.
- Effort: advanced
Netsh Allowed Python Program
Detects netsh command that performs modification on Firewall rules to allow the program python.exe. This activity is most likely related to the deployment of a Python server or an application that needs to communicate over a network. Threat actors could use it for data extraction, hosting a webshell or else.
- Effort: intermediate
Netsh Port Forwarding
Detects netsh commands that enable a port forwarding between to hosts. This can be used by attackers to tunnel RDP or SMB shares for example.
- Effort: intermediate
Netsh Port Opening
Detects netsh commands that opens a specific port. Can be used by malware or attackers for lateralisation/exfiltration (e.g. SMB/RDP opening).
- Effort: master
Netsh RDP Port Forwarding
Detects netsh commands that configure a port forwarding of port 3389 used for RDP. This is commonly used by attackers during lateralization on windows environments.
- Effort: elementary
Netsh RDP Port Opening
Detects netsh commands that opens the port 3389 used for RDP, used in Sarwent Malware.
- Effort: intermediate
Network Connection Via Certutil
Identifies certutil.exe making a network connection. Adversaries could abuse certutil.exe to download a certificate, or malware, from a remote URL.
- Effort: intermediate
Network Scanning and Discovery
Tools and command lines used for network discovery from current system
- Effort: advanced
Network Share Discovery
Adversaries may look for folders and drives shared on remote systems as a means of identifying sources of information to gather as a precursor for Collection and to identify potential systems of interest for Lateral Movement. Networks often contain shared network drives and folders that enable users to access file directories on various systems across a network. File sharing over a Windows network occurs over the SMB protocol. This technique is frequently leveraged by threat actors such as APT32, APT41, Wizard Spider. But also, through the use of some malware such as Cobalt Strike, Empire, PlugX and Ramsay.
- Effort: master
Network Sniffing
List of common tools used for network packages sniffing
- Effort: advanced
Network Sniffing Windows
Network sniffing refers to using the network interface on a system to monitor or capture information sent over a wired or wireless connection. An adversary may place a network interface into promiscuous mode to passively access data in transit over the network, or use span ports to capture a larger amount of data.
- Effort: intermediate
New DLL Added To AppCertDlls Registry Key
Dynamic-link libraries (DLLs) that are specified in the AppCertDLLs value in the Registry key can be abused to obtain persistence and privilege escalation by causing a malicious DLL to be loaded and run in the context of separate processes on the computer. Logging for Registry events is needed in the Sysmon configuration (events 12 and 13).
- Effort: intermediate
New Service Creation
Detects creation of a new service from command line
- Effort: advanced
Ngrok Process Execution
Detects possible Ngrok execution, which can be used by attacker for RDP tunneling.
- Effort: intermediate
NjRat Registry Changes
Detects changes for the RUN registry key which happen when a victim is infected by NjRAT. Please note that even if NjRat is well-known for the behavior the rule catches, the rule is a bit larger and could catch other malwares.
- Effort: master
Njrat Registry Values
Detects specifis registry values that are related to njRat usage.
- Effort: intermediate
NlTest Usage
Detects attempts to gather information on domain trust relationships that may be used to identify lateral movement opportunities. These command lines were observed in numerous attacks, but also sometimes from legitimate administrators for debugging purposes. The rule does not cover very basics commands but rather the ones that are interesting for attackers to gather information on a domain.
- Effort: advanced
Non-Legitimate Executable Using AcceptEula Parameter
Detects accepteula in command line with non-legitimate executable name. Some attackers are masquerading SysInternals tools with decoy names to prevent detection.
- Effort: advanced
Ntfsinfo Usage
Detects when the command ntfsinfo is used. An attacker can access to information on the volume from NTFS and have a directory dump of NTFS files.
- Effort: advanced
Office Application Startup Office Test
Detects the addition of office test registry that allows a user to specify an arbitrary DLL that will be executed everytime an Office application is started. An adversaries may abuse the Microsoft Office "Office Test" Registry key to obtain persistence on a compromised system.
- Effort: elementary
OneNote Suspicious Children Process
In January 2023, a peak of attacks using .one files was observed in the wild. This rule tries to detect the effect of such attempts using this technique.
- Effort: advanced
Openfiles Usage
Detects when the command openfiles, to get information on files opened remotely, is used.
- Effort: advanced
Opening Of a Password File
Command line detection of common office software opening some password related file. It could be a security breach if an unauthorized user access it.
- Effort: master
Outlook Registry Access
Detection of accesses to Microsoft Outlook registry hive, which might contain sensitive information.
- Effort: master
Pandemic Windows Implant
Detects Pandemic Windows Implant through registry keys or specific command lines. Prerequisites: Logging for Registry events is needed, which can be done in the Sysmon configuration (events 12 and 13).
- Effort: master
PasswordDump SecurityXploded Tool
Detects the execution of the PasswordDump SecurityXploded Tool
- Effort: elementary
Permission Discovery Via Wmic
Detects discovery of permission on local groups via the tool wmic.
- Effort: advanced
Phorpiex DriveMgr Command
Detects specific command used by the Phorpiex botnet to execute a copy of the loader during its self-spreading stage. As described by Microsoft, this behavior is unique and easily identifiable due to the use of folders named with underscores "__" and the PE name "DriveMgr.exe".
- Effort: elementary
Phorpiex Process Masquerading
Detects specific process executable path used by the Phorpiex botnet to masquerade its system process network activity. It looks for a pattern of a system process executable name that is not legitimate and running from a folder that is created via a random algorithm 13-15 numbers long.
- Effort: elementary
Potential DNS Tunnel
Detects domain name which is longer than 62 characters. Long domain names are distinctive of DNS tunnels.
- Effort: advanced
PowerCat Function Loading
Detect a basic execution of PowerCat. PowerCat is a PowerShell function allowing to do basic connections, file transfer, shells, relays, generate payloads.
- Effort: intermediate
PowerShell AMSI Deactivation Bypass Using .NET Reflection
Detects Request to amsiInitFailed that can be used to disable AMSI (Antimalware Scan Interface) Scanning. More information about Antimalware Scan Interface https://docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal.
- Effort: advanced
PowerShell Commands Invocation
Detects the execution to invoke a powershell command. This was used in an intrusion using Gootloader to access Mimikatz.
- Effort: advanced
PowerShell Data Compressed
Detects data compression through a PowerShell command (could be used by an adversary for exfiltration).
- Effort: advanced
PowerShell Downgrade Attack
Detects PowerShell downgrade attack by comparing the host versions with the actually used engine version 2.0
- Effort: elementary
PowerShell Download From URL
Detects a Powershell process that contains download commands in its command line string.
- Effort: advanced
PowerShell EncodedCommand
Detects popular file extensions in commands obfuscated in base64 run through the EncodedCommand option.
- Effort: advanced
PowerShell Execution Via Rundll32
Detects PowerShell Strings applied to rundll as seen in PowerShdll.dll Rule modified
- Effort: intermediate
PowerShell Invoke Expression With Registry
Detects keywords from well-known PowerShell techniques to get registry key values
- Effort: advanced
PowerShell Malicious Nishang PowerShell Commandlets
Detects Commandlet names and arguments from the Nishang exploitation framework.
- Effort: advanced
PowerView commandlets 1
Detects PowerView commandlets which perform network and Windows domain enumeration and exploitation. It provides replaces for almost all Windows net commands, letting you query users, machines, domain controllers, user descriptions, share, sessions, and more.
- Effort: advanced
PowerView commandlets 2
Detects PowerView commandlets which perform network and Windows domain enumeration and exploitation. It provides replaces for almost all Windows net commands, letting you query users, machines, domain controllers, user descriptions, share, sessions, and more.
- Effort: master
Powershell AMSI Bypass
This rule aims to detect attempts to bypass AMSI in powershell using specific techniques.
- Effort: advanced
Powershell UploadString Function
Powershell's uploadXXX functions are a category of methods which can be used to exfiltrate data through native means on a Windows host.
- Effort: advanced
Powershell Web Request
Detects the use of various web request methods executed remotely via Windows PowerShell.
- Effort: master
Powershell Web Request And Windows Script
Detects the use of PowerShell web request method combined with Windows Script utilities. This has been observed being used by some malware loaders.
- Effort: intermediate
Privilege Escalation Awesome Scripts (PEAS)
Detect PEAS privileges escalation scripts and binaries
- Effort: elementary
Process Memory Dump Using Comsvcs
Detects the use of comsvcs in command line to dump a specific process memory. This technique is used by attackers for privilege escalation and pivot.
- Effort: intermediate
Process Memory Dump Using Createdump
Detects the use of createdump.exe in command line to dump the memory of a process. This technique is used by attackers for privilege escalation and pivot.
- Effort: elementary
Process Memory Dump Using Rdrleakdiag
Detects the use of rdrleakdiag.exe in command line to dump the memory of a process. This technique is used by attackers for privilege escalation and pivot.
- Effort: elementary
Process Trace Alteration
PTrace syscall provides a means by which one process ("tracer") may observe and control the execution of another process ("tracee") and examine and change the tracee's memory and registers. Attacker might want to abuse ptrace functionnality to analyse memory process. It requires to be admin or set ptrace_scope to 0 to allow all user to trace any process.
- Effort: advanced
PsExec Process
Detects PsExec execution, command line which contains pstools or installation of the PsExec service. PsExec is a SysInternals which can be used to execute a program on another computer. The tool is as much used by attackers as by administrators.
- Effort: advanced
Putty Sessions Listing
Detects attempts to list Putty sessions through registry. To fully work, this rule requires to log registry accesses, which can be done with the Windows Event ID 4656 or 4663 but for that specific configuration is needed.
- Effort: master
Python Exfiltration Tools
Python has some built-in modules or library that could be installed and later be used as exflitration tool by an attacker
- Effort: advanced
Python HTTP Server
Detects command used to start a Simple HTTP server in Python. Threat actors could use it for data extraction, hosting a webshell or else.
- Effort: intermediate
QakBot Process Creation
Detects QakBot like process executions
- Effort: intermediate
Qakbot Persistence Using Schtasks
Detects possible Qakbot persistence using schtasks.
- Effort: intermediate
RDP Configuration File From Mail Process
Detects RDP configuration file being created or executed by a Mail-related process like Outlook. RDP configuration file will allow, when opened, an user to connect to the configured server easily. Attackers use this to trick victims in order to get a shared drive and potentially retrieve the data from that drive, but also drop a malicious file on the drive to establish persistence. Using RDP can also expose the victim's credential and clipboard data on some cases.
- Effort: advanced
RDP Session Discovery
Detects use of RDP session discovery via qwinsta or quser. Used by some threat actors to know if someone is working via RDP on a server.
- Effort: advanced
RTLO Character
Detects RTLO (Right-To-Left character) in file and process names.
- Effort: elementary
Raccine Uninstall
Detects commands that indicate a Raccine removal from an end system. Raccine is a free ransomware protection tool.
- Effort: elementary
Rclone Process
Detects Rclone executable or Rclone execution by using the process name, the execution through a command obfuscated or not.
- Effort: advanced
Rebooting
Detects when forcing a computer to shutdown.
- Effort: master
Reconnaissance Commands Activities
Based on Cynet, Microsoft and Kaspersky analysis of Qakbot, this rule tries to detect some discovery TTPs.
- Effort: intermediate
RedMimicry Winnti Playbook Registry Manipulation
Detects actions caused by the RedMimicry Winnti playbook. Logging for Registry events is needed in the Sysmon configuration (events 12 and 13).
- Effort: elementary
Remote Access Tool Domain
Detects traffic toward a domain flagged as a Remote Administration Tool (RAT).
- Effort: master
Remote Monitoring and Management Software - AnyDesk
Detect artifacts related to the installation or execution of the Remote Monitoring and Management tool AnyDesk.
- Effort: master
Remote Monitoring and Management Software - Atera
Detect artifacts related to the installation or execution of the Remote Monitoring and Management tool Atera.
- Effort: master
Remote System Discovery Via Telnet
Detects use of the protocol telnet to access information.
- Effort: advanced
Rubeus Tool Command-line
Detects command line parameters used by Rubeus, a toolset to interact with Kerberos and abuse it.
- Effort: advanced
SEKOIA.IO Intelligence Feed
Detect threats based on indicators of compromise (IOCs) collected by SEKOIA's Threat and Detection Research team.
- Effort: elementary
SOCKS Tunneling Tool
Detects the usage of a SOCKS tunneling tool, often used by threat actors. These tools often use the socks5 commandline argument, however socks4 can sometimes be used as well. Unfortunately, socks alone (without any number) triggered too many false positives.
- Effort: intermediate
SSH Reverse Socks
Detects the usage of the -R option combined with StrictHostKeyChecking, which is an indication of using SSH for reverse socks.
- Effort: intermediate
STRRAT Scheduled Task
Detect STRRAT when it achieves persistence by creating a scheduled task. STRRAT is a Java-based stealer and remote backdoor, it establishes persistence using this specific command line: 'cmd /c schtasks /create /sc minute /mo 30 /tn Skype /tr "C:\Users\Admin\AppData\Roaming\SAMPLENAME.jar"'
- Effort: intermediate
Schtasks Persistence With High Privileges
Detection of scheduled task with high privileges used by attacker for persistence.
- Effort: elementary
Schtasks Suspicious Parent
Detects schtasks started from suspicious and/or unusual processes.
- Effort: intermediate
Screenconnect Remote Execution
Detect cmd or powershell remote execution cmdline via ScreenConnect
- Effort: intermediate
Searchindexer Wrong Parent
Detects if the Search Indexer was executed by a non-legitimate parent process. Search Indexer is the Windows service that handles indexing of your files for Windows Search.
- Effort: master
Searchprotocolhost Wrong Parent
Detects if the Search Protocol Host process was executed by a non-legitimate parent process. Search Protocol Host is part of the Windows Indexing Service, a service indexing files on the local drive making them easier to search.
- Effort: master
Sekoia.io EICAR Detection
Detects observables in Sekoia.io CTI tagged as EICAR, which are fake samples meant to test detection.
- Effort: master
Shadow Copies
Detects command line used to create and list shadow copies. An adversary may attempt to get information on shadow volumes to perform deletion or extract password hashes from the ntds.dit file. This rule requires command line logging or Windows PowerShell events (4104).
- Effort: master
Shell PID Injection
Detects when shells PID are listed and injected in another process. It can be performed to reuse sudo token related to shell in order to elevate privilege and maintain persistence.
- Effort: intermediate
Smss Wrong Parent
Detects if the Smss process was executed by a non-legitimate parent process. Session Manager Subsystem (smss) process is a component of the Microsoft Windows NT family of operating systems.
- Effort: master
Socat Relaying Socket
Socat is a linux tool used to relay local socket or internal network connection, this technics is often used by attacker to bypass security equipment such as firewall
- Effort: advanced
Socat Reverse Shell Detection
Socat is a linux tool used to relay or open reverse shell that is often used by attacker to bypass security equipment.
- Effort: elementary
SolarWinds Wrong Child Process
Detects SolarWinds process starting an unusual child process. Process solarwinds.businesslayerhost.exe and solarwinds.businesslayerhostx64.exe created an unexepected child process which doesn't correspond to the legitimate ones.
- Effort: intermediate
Spyware Persistence Using Schtasks
Detects possible Agent Tesla or Formbook persistence using schtasks. The name of the scheduled task used by these malware is very specific (Updates/randomstring).
- Effort: intermediate
SquirrelWaffle Malspam Execution Loading DLL
Detects cscript running suspicious command to load a DLL. This behavior has been detected in SquirrelWaffle campaign.
- Effort: intermediate
Startup Item Created
Detects when a item is added to the startup directory. An attacker can use this establish persistence.
- Effort: intermediate
Stop Backup Services
Detects adversaries attempts to stop backups services or disable Windows previous files versions feature. This could be related to ransomware operators or legit administrators. This rule relies Windows command line logging and registry logging, and PowerShell (ID 4103, 4104).
- Effort: master
Suncrypt Parameters
Detects SunCrypt ransomware's parameters, most of which are unique.
- Effort: elementary
Suspicious Cmd File Copy Command To Network Share
Copy suspicious files through Windows cmd prompt to network share
- Effort: intermediate
Suspicious Cmd.exe Command Line
Detection on suspicious cmd.exe command line seen being used by some attackers (e.g. Lazarus with Word macros). This requires Windows process command line logging.
- Effort: master
Suspicious CodePage Switch with CHCP
Detects a code page switch in command line
- Effort: intermediate
Suspicious CommandLine Lsassy Pattern
Detects the characteristic lsassy loop used to identify lsass PIDs
- Effort: intermediate
Suspicious Control Process
Detects suspicious execution of control.exe process when used to execute a DLL file.
- Effort: advanced
Suspicious DLL Loading By Ordinal
Detects suspicious DLL Loading by ordinal number in a non legitimate or rare folders. For example, Sofacy (APT28) used this technique to load their Trojan in a campaign of 2018.
- Effort: intermediate
Suspicious DNS Child Process
Detects suspicious processes spawned by the dns.exe process. It could be a great indication of the exploitation of the DNS RCE bug reported in CVE-2020-1350 (SIGRED).
- Effort: intermediate
Suspicious Desktopimgdownldr Execution
Detects a suspicious Desktopimgdownldr execution. Desktopimgdownldr.exe is a Windows binary used to configure lockscreen/desktop image and can be abused to download malicious file.
- Effort: intermediate
Suspicious Double Extension
Detects suspicious use of an .exe extension after a non-executable file extension like .pdf.exe, a set of spaces or underlines to cloak the executable file in spearphishing campaigns
- Effort: advanced
Suspicious Finger Usage
Detects suspicious aged finger.exe tool execution often used in malware attacks nowadays. An attacker can use finger to silently retrieve a command, a script or a payload from a remote server. For example, the tool Darkfinger-C2 uses this technique to download files from the C2 channel.
- Effort: intermediate
Suspicious Hangul Word Processor Child Process
Detects suspicious Hangul Word Processor (HWP) child process that could indicate an exploitation as used by the Lazarus APT during the Operation Ghost Puppet (2018). This activity could correspond to a maldoc execution related to a .hwp file. Hangul is a proprietary word processing application that supports the Korean written language.
- Effort: elementary
Suspicious Headless Web Browser Execution To Download File
Detects a suspicious command used to execute a Chromium-based web browser (Chrome or Edge) using the headless mode, meaning that the browser window wouldn't be visible, and the dump mode to download a file. This technique can be used to fingerprint the compromised host, in particular by the Ducktail infostealer.
- Effort: elementary
Suspicious Microsoft Defender Antivirus Exclusion Command
Detects PowerShell commands aiming to exclude path, process, IP address, or extension from scheduled and real-time scanning. These commands can be used by attackers or malware to avoid being detected by Windows Defender. Depending on the environment and the installed software, this detection rule could raise false positives. We recommend customizing this rule by filtering legitimate processes that use Windows Defender exclusion command in your environment.
- Effort: master
Suspicious Mshta Execution
Detects suspicious mshta.exe execution patterns, either involving file polyglotism, remote file (http, ftp or ldap) or suspicious location. This technique is often used by threat actors.
- Effort: intermediate
Suspicious Mshta Execution From Wmi
Detects mshta executed by wmiprvse as parent. It has been used by TA505 with some malicious documents.
- Effort: intermediate
Suspicious Netsh DLL Persistence
Detects persitence via netsh helper. Netsh interacts with other operating system components using dynamic-link library (DLL) files. Adversaries may establish persistence by executing malicious content triggered by Netsh Helper DLLs.
- Effort: elementary
Suspicious Network Args In Command Line
Detection on some commonly observed suspicious processes command lines using HTTP schema with port 443.
- Effort: intermediate
Suspicious Outlook Child Process
Detects suspicious child processes of Microsoft Outlook. These child processes are often associated with spearphishing activity.
- Effort: intermediate
Suspicious PowerShell Invocations - Generic
Detects suspicious PowerShell invocation command parameters through command line logging or ScriptBlock Logging.
- Effort: advanced
Suspicious PowerShell Invocations - Specific
Detects suspicious PowerShell invocation command parameters.
- Effort: intermediate
Suspicious PowerShell Keywords
Detects keywords that could indicate the use of some PowerShell exploitation framework.
- Effort: advanced
Suspicious PrinterPorts Creation (CVE-2020-1048)
Detects new commands that add new printer port which point to suspicious file
- Effort: advanced
Suspicious Regasm Regsvcs Usage
catch abuse of regsvcs and regasm lolbin by attacker
- Effort: advanced
Suspicious Regsvr32 Execution
Detects suspicious regsvr32.exe executions, either regsvr32 registering a DLL in an unusual repository (temp/, appdata/ or public/), or regsvr32 executed by an unusual parent process, or regsvr32 executing an unusual process, or regsvr32 registering a media file and not a DLL (as seen in IcedID campaigns), or regsvr32 registering a ocx file in appdata/.
- Effort: advanced
Suspicious Rundll32.exe Executions
The process rundll32.exe executes a newly dropped DLL with update /i in the command line. This specific technic was observed at least being used by the IcedID loading mechanism dubbed Gziploader. Some other detections are related to LOLBAS (Living Off The Land Binaries, Scripts and Libraries) usages (like the COM registering).
- Effort: intermediate
Suspicious TOR Gateway
Detects suspicious TOR gateways. Gateways are often used by the victim to pay and decrypt the encrypted files without installing TOR. Tor intercepts the network traffic from one or more apps on user’s computer, usually the user web browser, and shuffles it through a number of randomly-chosen computers before passing it on to its destination. This disguises user location, and makes it harder for servers to pick him/her out on repeat visits, or to tie together separate visits to different sites, this making tracking and surveillance more difficult. Before a network packet starts its journey, user’s computer chooses a random list of relays and repeatedly encrypts the data in multiple layers, like an onion. Each relay knows only enough to strip off the outermost layer of encryption, before passing what’s left on to the next relay in the list.
- Effort: advanced
Suspicious Taskkill Command
Detects rare taskkill command being used. It could be related to Baby Shark malware.
- Effort: intermediate
Suspicious VBS Execution Parameter
Detects suspicious VBS file execution with a specific parameter by cscript. It was observed in the Operation CloudHopper.
- Effort: elementary
Suspicious Windows DNS Queries
Detects a suspicious Windows command-line process making a DNS query via known abuse text paste web services. This is based on Microsoft Windows Sysmon events (Event ID 22).
- Effort: advanced
Suspicious Windows Installer Execution
Detects suspicious execution of the Windows Installer service (msiexec.exe) which could be used to install a malicious MSI package hosted on a remote server.
- Effort: master
Suspicious Windows Script Execution
Detects wscript.exe or cscript.exe executing a script in user directories (C:\ProgramData or C:\Users) with a .txt extension, which is very suspicious. It could strongly correspond to a malware dropper, as seen during SquirrelWaffle maldoc campaign.
- Effort: intermediate
Suspicious XOR Encoded PowerShell Command Line
Detects suspicious powershell process which includes bxor command, alternative obfuscation method to b64 encoded commands.
- Effort: advanced
Suspicious certutil command
Detects suspicious certutil command which can be used by threat actors to download and/or decode payload.
- Effort: intermediate
Svchost Wrong Parent
Detects if the svchost.exe process was executed by a non-legitimate parent process. Svchost (Service Host Process) is a generic host process name for services that run from dynamic-link libraries (DLLs).
- Effort: master
Sysprep On AppData Folder
Detects suspicious Sysprep process start with AppData folder as target (as used by Trojan Syndicasec in Thrip report by Symantec). Sysprep is a Windows tool used to change Windows images from a generalized state to a specialized state, and then back to a generalized state. It can be used to remove all system-specific information and reset the computer.
- Effort: intermediate
System Info Discovery
System info discovery, attempt to detects basic command use to fingerprint a host.
- Effort: master
System Network Connections Discovery
Detects system network connections discovery via powershell and cmd.
- Effort: advanced
TOR Usage Generic Rule
Detects TOR usage globally, whether the IP is a destination or source. TOR is short for The Onion Router, and it gets its name from how it works. TOR intercepts the network traffic from one or more apps on user’s computer, usually the user web browser, and shuffles it through a number of randomly-chosen computers before passing it on to its destination. This disguises user location, and makes it harder for servers to pick him/her out on repeat visits, or to tie together separate visits to different sites, this making tracking and surveillance more difficult. Before a network packet starts its journey, user’s computer chooses a random list of relays and repeatedly encrypts the data in multiple layers, like an onion. Each relay knows only enough to strip off the outermost layer of encryption, before passing what’s left on to the next relay in the list.
- Effort: master
Tactical RMM Installation
Detection of common Tactical RMM installation arguments that could be abused by some attackers.
- Effort: elementary
Taskhost Wrong Parent
Detects if the Taskhost process was executed by a non-legitimate parent process. Taskhost is the process of the Windows Task Manager which lists the processes that are currently running on the computer system.
- Effort: master
Taskhostw Wrong Parent
Detects if the Taskhostw process was executed by a non-legitimate parent process. Taskhostw is a software component of Windows service start manager, it starts DLL-based Windows services when the computer boots up.
- Effort: master
Telegram Bot API Request
Detects suspicious DNS queries to api.telegram.org used by Telegram Bots of any kind
- Effort: advanced
Tmutil Delete Backups
Detects when the utility tmutil is used to delete backups. The Time Machine utility is used to restore data from backups, add or remove exclusions, and compare backups.
- Effort: elementary
Tmutil Disabled
Detects when the utility tmutil is disabled. The Time Machine utility is used to restore data from backups, add or remove exclusions, and compare backups.
- Effort: elementary
Tmutil Exclude File From Backups
Detects when the utility tmutil is used to exclude paths from backups.
- Effort: master
UAC Bypass Via Sdclt
Detects changes to HKCU\Software\Classes\exefile\shell\runas\command\isolatedCommand by an attacker in order to bypass User Account Control (UAC)
- Effort: elementary
Usage Of Procdump With Common Arguments
Detects the usage of Procdump sysinternals tool with some common arguments and followed by common patterns.
- Effort: advanced
Usage Of Sysinternals Tools
Detects the usage of Sysinternals Tools due to accepteula key being added to Registry. The rule detects it either from the command line usage or from the regsitry events. For the later prerequisite is logging for registry events in the Sysmon configuration (events 12 and 13).
- Effort: master
User Added To Admin Group Via Cmd
Detects the use of different commands to add a user to an admin group.
- Effort: advanced
Venom Multi-hop Proxy agent detection
Detects Venom Multi-hop Proxy agent.
- Effort: intermediate
WMI Fingerprint Commands
Detects attacker fingerprint activities based on the correlation of specific WMIC commands. This has been observed with Aurora malware.
- Effort: advanced
WMI Install Of Binary
Detection of WMI used to install a binary on the host. It is often used by attackers as a signed binary to infect an host.
- Effort: elementary
WMIC Command To Determine The Antivirus
Detects WMIC command to determine the antivirus on a system, characteristic of the ZLoader malware (and possibly others)
- Effort: advanced
WMIC Uninstall Product
Detects products being uninstalled using WMIC command.
- Effort: intermediate
WMImplant Hack Tool
WMImplant is a powershell framework used by attacker for reconnaissance and exfiltration, this rule attempts to detect WMimplant arguments and invokes commands.
- Effort: advanced
Wdigest Enable UseLogonCredential
Detects modification of the Windows Registry value of HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest\UseLogonCredential. This technique is used to extract passwords in clear-text using WDigest. The rule requires to log for Registry Events, which can be done using Sysmon Event IDs 12, 13 and 14.
- Effort: elementary
Web Application Launching Shell
Detects when a web application launches a shell.
- Effort: master
WerFaultSecure Abuse
Detect usage of the software vulnerability of WerFaultSecure to suspend the processes of EDRs, and bypass detection. It has been implemented in the tool EDR-Freeze.
- Effort: advanced
WiFi Credentials Harvesting Using Netsh
Detects the harvesting of WiFi credentials using netsh.exe.
- Effort: advanced
Windows Defender Logging Modification Via Registry
Detects when the logging for defender is disabled in the registry.
- Effort: elementary
Windows Firewall Changes
Detects changes on Windows Firewall configuration
- Effort: master
Windows Registry Persistence COM Key Linking
Detects COM object hijacking via TreatAs subkey. Logging for Registry events is needed in the Sysmon configuration with this kind of rule <TargetObject name="testr12" condition="end with">\TreatAs\(Default)</TargetObject>.
- Effort: master
Windows Sandbox Start
Detection of Windows Sandbox started from the command line with a config file or interactively using a WSB file.
- Effort: master
Windows Update LolBins
This rule try to detect a suspicious behavior of wuauclt.exe (windows update client) that could be a lolbins. Wuauctl.exe could be used to execute a malicious program.
- Effort: elementary
Winlogon wrong parent
Winlogon.exe is a process that performs the Windows login management function, handling user login and logout in Windows. You see this process in action whenever the operating system asks you for your username and password. It is also responsible for loading user profiles after login, this supports automated login (when relevant) and keyboard and mouse inactivity monitoring to decide when to invoke the screen saver. This rule analyse if the parent of this process is a legitimate one or not.
- Effort: master
Winword Document Droppers
Detects specific process characteristics of word document droppers. This techniques has been used by Maze ransomware operators.
- Effort: elementary
Wmic Process Call Creation
The WMI command-line (WMIC) utility provides a command-line interface for Windows Management Instrumentation (WMI). WMIC is compatible with existing shells and utility commands. Although WMI is supposed to be an administration tool, it is wildy abused by threat actors. One of the reasons is WMI is quite stealthy. This rule detects the wmic command line launching a process on a remote or local host.
- Effort: intermediate
Wmic Service Call
Detects either remote or local code execution using wmic tool.
- Effort: intermediate
Wmic Suspicious Commands
Detects suspicious commands used by the process wmic to get informations on the system.
- Effort: advanced
Wsmprovhost Wrong Parent
Detects if the Wsmprovhost process was executed by a non-legitimate parent process. The PowerShell host wsmprovhost.exe is a proxy process executed remotely through PowerShell when using Windows Remote Management (WinRM).
- Effort: master
XCopy Suspicious Usage
Detects the usage of xcopy with suspicious command line options (used by Judgment Panda APT in the past). The rule is based on command line only in case xcopy is renamed.
- Effort: advanced
XSL Script Processing And SquiblyTwo Attack
Detection of an attack where adversaries may bypass application control and obscure execution of code by embedding scripts inside XSL files. Another variation of this technique, dubbed "Squiblytwo", involves to invoke JScript or VBScript within an XSL file.
- Effort: intermediate
ZIP LNK Infection Chain
Detection of an ZIP download followed by a child-process of explorer, followed by multiple Windows processes.This is widely used as an infection chain mechanism.
- Effort: advanced
xWizard Execution
Detects the execution of Xwizard tool with specific arguments which utilized to run custom class properties.
- Effort: master
Event Categories
The following table lists the data source offered by this integration.
| Data Source | Description |
|---|---|
Application logs |
activites performed on SentinelOne infrastructure are logged |
In details, the following table denotes the type of events produced by this integration.
| Name | Values |
|---|---|
| Kind | alert |
| Category | intrusion_detection |
| Type | info |
Transformed Events Samples after Ingestion
This section demonstrates how the raw logs will be transformed by our parsers. It shows the extracted fields that will be available for use in the built-in detection rules and hunting activities in the events page. Understanding these transformations is essential for analysts to create effective detection mechanisms with custom detection rules and to leverage the full potential of the collected data.
{
"message": "{\n \"id\": \"ba485919-e4c1-4496-9e2f-feb320f6841a\",\n \"name\": \"Domain Controller Discovery Detected\",\n \"description\": \"This event is raised when there is a query from an endpoint to find the domain controllers or AD Servers in the Active Directory Domain.\",\n \"detectedAt\": \"2024-11-22T05:35:09.000Z\",\n \"attackSurfaces\": [\n \"IDENTITY\"\n ],\n \"detectionSource\": {\n \"product\": \"Identity\"\n },\n \"status\": \"NEW\",\n \"assignee\": null,\n \"classification\": \"ENUMERATION\",\n \"confidenceLevel\": \"MALICIOUS\",\n \"firstSeenAt\": \"2024-11-22T05:35:09.000Z\",\n \"lastSeenAt\": \"2024-11-22T05:35:09.000Z\",\n \"process\": {\n \"cmdLine\": \"C:\\\\Windows\\\\system32\\\\net1 group \\\"Domain Controllers\\\" /domain\",\n \"file\": {\n \"path\": \"c:\\\\windows\\\\system32\\\\net1.exe\",\n \"sha1\": null,\n \"sha256\": \"18F76BC1F02A161EBDEDF3142273C186D05A836ADDCAAEE599194089FD59F398\",\n \"md5\": null\n },\n \"parentName\": null\n },\n \"result\": null,\n \"storylineId\": null\n}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T05:35:09Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when there is a query from an endpoint to find the domain controllers or AD Servers in the Active Directory Domain.",
"start": "2024-11-22T05:35:09Z",
"type": "info"
},
"@timestamp": "2024-11-22T05:35:09Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "C:\\Windows\\system32\\net1 group \"Domain Controllers\" /domain",
"executable": "c:\\windows\\system32\\net1.exe",
"hash": {
"sha256": "18F76BC1F02A161EBDEDF3142273C186D05A836ADDCAAEE599194089FD59F398"
},
"name": "net1.exe"
},
"related": {
"hash": [
"18F76BC1F02A161EBDEDF3142273C186D05A836ADDCAAEE599194089FD59F398"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "ba485919-e4c1-4496-9e2f-feb320f6841a",
"name": "Domain Controller Discovery Detected",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935322-7b49-71f0-89e0-f52562c26e53\", \"name\": \"Brute force attack - Mass Account Lockout\", \"description\": \"This event is raised when ADAssessor detects lockout of multiple accounts, which could be due to brute-force attempts or a password spray.\", \"detectedAt\": \"2024-11-22T09:09:48.731Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"UNKNOWN\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T09:09:48.731Z\", \"lastSeenAt\": \"2024-11-22T09:09:48.731Z\", \"process\": null, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T09:09:48.731000Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when ADAssessor detects lockout of multiple accounts, which could be due to brute-force attempts or a password spray.",
"start": "2024-11-22T09:09:48.731000Z",
"type": "info"
},
"@timestamp": "2024-11-22T09:09:48.731000Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "UNKNOWN",
"confidenceLevel": "MALICIOUS",
"id": "01935322-7b49-71f0-89e0-f52562c26e53",
"name": "Brute force attack - Mass Account Lockout",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935310-d00e-7616-81b9-fcb227ebb13d\", \"name\": \"Domain Controller Discovery Detected\", \"description\": \"This event is raised when there is a query from an endpoint to find the domain controllers or AD Servers in the Active Directory Domain.\", \"detectedAt\": \"2024-11-22T08:45:51.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T08:45:51.000Z\", \"lastSeenAt\": \"2024-11-22T08:45:51.000Z\", \"process\": {\"cmdLine\": \"Sharphound.exe\", \"file\": {\"path\": \"c:\\\\users\\\\administrator\\\\desktop\\\\ad_recon\\\\sharphound.exe\", \"sha1\": null, \"sha256\": \"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T08:45:51Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when there is a query from an endpoint to find the domain controllers or AD Servers in the Active Directory Domain.",
"start": "2024-11-22T08:45:51Z",
"type": "info"
},
"@timestamp": "2024-11-22T08:45:51Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "Sharphound.exe",
"executable": "c:\\users\\administrator\\desktop\\ad_recon\\sharphound.exe",
"hash": {
"sha256": "61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
},
"name": "sharphound.exe"
},
"related": {
"hash": [
"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "01935310-d00e-7616-81b9-fcb227ebb13d",
"name": "Domain Controller Discovery Detected",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935310-eb28-7a57-9c27-87843b2cec61\", \"name\": \"AD Service Account Enumeration Detected\", \"description\": \"This event is generated when LDAP queries for enumerating service accounts are detected from an endpoint.\", \"detectedAt\": \"2024-11-22T08:45:51.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T08:45:51.000Z\", \"lastSeenAt\": \"2024-11-22T08:45:51.000Z\", \"process\": {\"cmdLine\": \"Sharphound.exe\", \"file\": {\"path\": \"c:\\\\users\\\\administrator\\\\desktop\\\\ad_recon\\\\sharphound.exe\", \"sha1\": null, \"sha256\": \"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T08:45:51Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is generated when LDAP queries for enumerating service accounts are detected from an endpoint.",
"start": "2024-11-22T08:45:51Z",
"type": "info"
},
"@timestamp": "2024-11-22T08:45:51Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "Sharphound.exe",
"executable": "c:\\users\\administrator\\desktop\\ad_recon\\sharphound.exe",
"hash": {
"sha256": "61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
},
"name": "sharphound.exe"
},
"related": {
"hash": [
"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "01935310-eb28-7a57-9c27-87843b2cec61",
"name": "AD Service Account Enumeration Detected",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935310-c715-72c9-bbd9-dc1ff6a7ff1e\", \"name\": \"AD Domain Computer Enumeration Detected\", \"description\": \"This event is raised when there is a query from an endpoint to dump all the computers in the Active Directory Domain.\", \"detectedAt\": \"2024-11-22T08:45:50.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T08:45:50.000Z\", \"lastSeenAt\": \"2024-11-22T08:45:50.000Z\", \"process\": {\"cmdLine\": \"Sharphound.exe\", \"file\": {\"path\": \"c:\\\\users\\\\administrator\\\\desktop\\\\ad_recon\\\\sharphound.exe\", \"sha1\": null, \"sha256\": \"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T08:45:50Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when there is a query from an endpoint to dump all the computers in the Active Directory Domain.",
"start": "2024-11-22T08:45:50Z",
"type": "info"
},
"@timestamp": "2024-11-22T08:45:50Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "Sharphound.exe",
"executable": "c:\\users\\administrator\\desktop\\ad_recon\\sharphound.exe",
"hash": {
"sha256": "61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
},
"name": "sharphound.exe"
},
"related": {
"hash": [
"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "01935310-c715-72c9-bbd9-dc1ff6a7ff1e",
"name": "AD Domain Computer Enumeration Detected",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935310-cb9b-770e-96ee-632d4d21520b\", \"name\": \"AD ACL Enumeration\", \"description\": \"This event is generated when a command used to query or read the ACL's\\\\ Permission of any object in Active Directory.\", \"detectedAt\": \"2024-11-22T08:45:50.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T08:45:50.000Z\", \"lastSeenAt\": \"2024-11-22T08:45:50.000Z\", \"process\": {\"cmdLine\": \"Sharphound.exe\", \"file\": {\"path\": \"c:\\\\users\\\\administrator\\\\desktop\\\\ad_recon\\\\sharphound.exe\", \"sha1\": null, \"sha256\": \"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T08:45:50Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is generated when a command used to query or read the ACL's\\ Permission of any object in Active Directory.",
"start": "2024-11-22T08:45:50Z",
"type": "info"
},
"@timestamp": "2024-11-22T08:45:50Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "Sharphound.exe",
"executable": "c:\\users\\administrator\\desktop\\ad_recon\\sharphound.exe",
"hash": {
"sha256": "61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
},
"name": "sharphound.exe"
},
"related": {
"hash": [
"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "01935310-cb9b-770e-96ee-632d4d21520b",
"name": "AD ACL Enumeration",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935310-d4ba-7131-9e08-defa8b3aeb52\", \"name\": \"Domain Users Enumeration Detected\", \"description\": \"This event is raised when there is a query from an endpoint to dump all the users in the Active Directory Domain.\", \"detectedAt\": \"2024-11-22T08:45:50.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T08:45:50.000Z\", \"lastSeenAt\": \"2024-11-22T08:45:50.000Z\", \"process\": {\"cmdLine\": \"Sharphound.exe\", \"file\": {\"path\": \"c:\\\\users\\\\administrator\\\\desktop\\\\ad_recon\\\\sharphound.exe\", \"sha1\": null, \"sha256\": \"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T08:45:50Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when there is a query from an endpoint to dump all the users in the Active Directory Domain.",
"start": "2024-11-22T08:45:50Z",
"type": "info"
},
"@timestamp": "2024-11-22T08:45:50Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "Sharphound.exe",
"executable": "c:\\users\\administrator\\desktop\\ad_recon\\sharphound.exe",
"hash": {
"sha256": "61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
},
"name": "sharphound.exe"
},
"related": {
"hash": [
"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "01935310-d4ba-7131-9e08-defa8b3aeb52",
"name": "Domain Users Enumeration Detected",
"status": "NEW"
}
}
}
{
"message": "{\"id\":\"11111111-1111-1111-1111-111111111111\",\"name\":\"Compromised Password Detected\",\"description\":\"Current passwords of your users are exposed in a public breach database or are banned in your network. If left unchanged, attackers can use these passwords to start Dictionary, Password Spray, and Credential Stuffing attacks.\",\"detectedAt\":\"2025-04-03T14:43:16.805Z\",\"attackSurfaces\":[\"IDENTITY\"],\"detectionSource\":{\"product\":\"Identity\"},\"status\":\"NEW\",\"assignee\":null,\"classification\":\"UNKNOWN\",\"confidenceLevel\":null,\"firstSeenAt\":null,\"lastSeenAt\":null,\"process\":null,\"result\":\"UNMITIGATED\",\"storylineId\":null,\"analystVerdict\":\"UNDEFINED\",\"analytics\":{\"category\":\"BreachDetect\"},\"asset\":{\"agentUuid\":null,\"agentVersion\":null,\"category\":\"Identity\",\"name\":\"name_test\",\"osType\":null,\"osVersion\":\"\",\"type\":\"UNKNOWN\",\"subcategory\":\"Users and Groups\"},\"rawData\":{\"activity_id\":2,\"activity_name\":\"Update\",\"category_uid\":2,\"class_uid\":11111111,\"enrichments\":[{\"data\":{\"source\":\"\",\"Source URL\":\"\",\"Breach Publish Time\":0.0},\"name\":\"Source of Breach Details\",\"value\":\"\"}],\"finding_info\":{\"analytic\":{\"category\":\"BreachDetect\",\"type_id\":0},\"desc\":\"Current passwords of your users are exposed in a public breach database or are banned in your network. If left unchanged, attackers can use these passwords to start Dictionary, Password Spray, and Credential Stuffing attacks.\",\"title\":\"Compromised Password Detected\",\"uid\":\"22222222-2222-2222-2222-222222222222\",\"internal_uid\":\"11111111-1111-1111-1111-111111111111\"},\"metadata\":{\"product\":{\"name\":\"Identity\",\"vendor_name\":\"SentinelOne\"},\"version\":\"1.1.0-dev\"},\"remediation\":{\"result_id\":2},\"resources\":[{\"name\":\"name_test\",\"owner\":{\"domain\":\"domain.name\",\"name\":\"name_test\",\"org\":{\"name\":\"domain\"}},\"type\":\"identity::users_and_groups::ad_user\",\"uid\":\"33333333-3333-3333-3333-333333333333\",\"s1_metadata\":{\"group_name\":\"Default Group\",\"account_id\":\"1234567890123456789\",\"account_name\":\"Account Name\",\"group_id\":\"5555555555555555555\",\"mgmt_id\":19789,\"scope_id\":\"5555555555555555555\",\"scope_level\":\"Group\",\"site_id\":\"6666666666666666666\",\"site_name\":\"Default site\"},\"internal_uid\":\"aaaaaaaaaaaaaaaaaaaaaaaaaa\"}],\"severity_id\":3,\"status_id\":1,\"time\":\"1743691396805\",\"type_uid\":\"1111111101\",\"evidences\":[{\"actor\":{\"user\":{\"domain\":\"domain.name\",\"name\":\"name_test\",\"uid\":\"33333333-3333-3333-3333-333333333333\"}}}],\"verdict_id\":0,\"attack_surface_ids\":[4],\"s1_classification_id\":0,\"verdict_detail_id\":0,\"verdict_fidelity_id\":0}}",
"event": {
"category": "intrusion_detection",
"kind": "alert",
"provider": "Identity",
"reason": "Current passwords of your users are exposed in a public breach database or are banned in your network. If left unchanged, attackers can use these passwords to start Dictionary, Password Spray, and Credential Stuffing attacks.",
"type": "info"
},
"@timestamp": "2025-04-03T14:43:16.805000Z",
"host": {
"name": "name_test"
},
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"organization": {
"id": "1234567890123456789",
"name": "Account Name"
},
"related": {
"user": [
"name_test"
]
},
"sentinelone": {
"identity": {
"analystVerdict": "UNDEFINED",
"analyticsCategory": "BreachDetect",
"attackSurfaces": [
"IDENTITY"
],
"classification": "UNKNOWN",
"id": "11111111-1111-1111-1111-111111111111",
"name": "Compromised Password Detected",
"result": "UNMITIGATED",
"siteId": "6666666666666666666",
"siteName": "Default site",
"status": "NEW"
}
},
"user": {
"domain": "domain.name",
"name": "name_test"
}
}
{
"message": "{\n \"analystVerdict\": \"UNDEFINED\",\n \"analytics\": {\n \"category\": \"ADSecure-DC\"\n },\n \"asset\": {\n \"agentUuid\": \"123123123123123\",\n \"agentVersion\": \"AgentVersion1\",\n \"category\": \"Server\",\n \"name\": \"VM0001.LAB\",\n \"osType\": \"UNKNOWN\",\n \"osVersion\": \"1.1\",\n \"subcategory\": \"Other Server\",\n \"type\": \"UNKNOWN\"\n },\n \"assignee\": null,\n \"attackSurfaces\": [\n \"IDENTITY\"\n ],\n \"classification\": \"UNKNOWN\",\n \"confidenceLevel\": \"MALICIOUS\",\n \"description\": \"This event is generated when a DCSync attack is detected.\",\n \"detectedAt\": \"2024-12-11T13:11:48.487Z\",\n \"detectionSource\": {\n \"product\": \"Identity\"\n },\n \"firstSeenAt\": \"2024-12-11T13:11:48.487Z\",\n \"id\": \"19b5cab4-9fdc-49f9-9641-dae9ed9b1c3b\",\n \"lastSeenAt\": \"2024-12-11T13:11:48.487Z\",\n \"name\": \"DCSync Attack Detected\",\n \"process\": null,\n \"rawData\": {\n \"activity_id\": 2,\n \"activity_name\": \"Update\",\n \"attack_surface_ids\": [\n 4\n ],\n \"category_uid\": 2,\n \"class_uid\": 99602001,\n \"confidence_id\": 3,\n \"evidences\": [\n {\n \"actor\": {\n \"user\": {\n\"name\":\"test_user\", \"domain\": \"LAB\"\n }\n },\n \"dst_endpoint\": {\n \"hostname\": \"VM0001\",\n \"ip\": \"5.6.7.8\",\n \"uid\": \"xxxxx-xxxxx-xxxxx-xxxxxxxxxxx\"\n },\n \"src_endpoint\": {\n \"hostname\":\"tes.test\", \"ip\": \"1.2.3.4\"\n }\n }\n ],\n \"finding_info\": {\n \"analytic\": {\n \"category\": \"ADSecure-DC\",\n \"type_id\": 1,\n \"uid\": \"ADSecure-DC\"\n },\n \"attacks\": [\n {\n \"tactics\": [\n {\n \"name\": \"Credential Access\",\n \"uid\": \"TA006\"\n }\n ],\n \"technique\": {\n \"name\": \"OS Credential Dumping\",\n \"uid\": \"T1003\"\n },\n \"version\": \"ATT&CK v11\"\n }\n ],\n \"desc\": \"This event is generated when a DCSync attack is detected.\",\n \"first_seen_time\": \"1733922708487\",\n \"internal_uid\": \"d2dfca23-c7c7-409d-840c-cc0702ef7eb7\",\n \"kill_chain\": [\n {\n \"phase_id\": 2\n }\n ],\n \"last_seen_time\": \"1733922708487\",\n \"related_events\": [\n {\n \"message\": \"An authorized session has been detected with a certain privilege which could be result of an privilege escalation.\",\n \"severity_id\": 5,\n \"time\": \"1733922708487\",\n \"type\": \"Authorize Session: Other\",\n \"uid\": \"xxxxx-xxxxx-xxxxx-xxxxxxxxxxx\"\n }\n ],\n \"title\": \"DCSync Attack Detected\",\n \"uid\": \"xxxxx-xxxxx-xxxxx-xxxxxxxxxxx\"\n },\n \"message\": \"This event is generated when a DCSync attack is detected.\",\n \"metadata\": {\n \"extension\": {\n \"name\": \"s1\",\n \"uid\": \"996\",\n \"version\": \"0.1.0\"\n },\n \"product\": {\n \"name\": \"Identity\",\n \"vendor_name\": \"SentinelOne\"\n },\n \"uid\": \"xxxxx-xxxxx-xxxxx-xxxxxxxxxxx\",\n \"version\": \"1.1.0-dev\"\n },\n \"raw_data\": \"5001802:Attacker IP=1.2.3.4 Source Port=49970 Target IP=5.6.7.8 Target Port=49155 Severity=14 Domain=LAB userName=john.doe dc_host=VM00001 CA_STATUS=ALERT client_id=xxxxxxx-xxxxxx-xxxx-xxxxxxx subscriberId:6666\",\n \"resources\": [\n {\n \"internal_uid\": \"11111111111111111111111111\",\n \"name\": \"VM0001.LAB\",\n \"s1_metadata\": {\n \"account_id\": \"123123123123123123\",\n \"account_name\": \"EXAMPLE CORP\",\n \"group_id\": \"1234567890\",\n \"group_name\": \"Default Group\",\n \"mgmt_id\": 123123,\n \"scope_id\": \"1234567890\",\n \"scope_level\": \"Group\",\n \"site_id\": \"1234567890\",\n \"site_name\": \"Sekoia.io\"\n },\n \"type\": \"server::other_server::windows_server\",\n \"uid\": \"xxxxx-xxxxx-xxxxx-xxxxxxxxxxx\",\n \"version\": \"Microsoft Windows Server 2012 R2 Standard 64-bit\"\n }\n ],\n \"s1_classification_id\": 0,\n \"severity_id\": 5,\n \"status_id\": 1,\n \"time\": \"1733922708487\",\n \"type_name\": \"\",\n \"type_uid\": \"9960200101\",\n \"unmapped\": {},\n \"verdict_detail_id\": 0,\n \"verdict_id\": 0\n },\n \"result\": null,\n \"status\": \"NEW\",\n \"storylineId\": null\n}",
"event": {
"category": "intrusion_detection",
"end": "2024-12-11T13:11:48.487000Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is generated when a DCSync attack is detected.",
"start": "2024-12-11T13:11:48.487000Z",
"type": "info"
},
"@timestamp": "2024-12-11T13:11:48.487000Z",
"agent": {
"id": "123123123123123",
"version": "AgentVersion1"
},
"destination": {
"address": "VM0001",
"domain": "VM0001",
"ip": "5.6.7.8"
},
"host": {
"name": "VM0001.LAB",
"os": {
"family": "UNKNOWN",
"version": "1.1"
}
},
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"organization": {
"id": "123123123123123123",
"name": "EXAMPLE CORP"
},
"related": {
"hosts": [
"VM0001",
"tes.test"
],
"ip": [
"1.2.3.4",
"5.6.7.8"
],
"user": [
"test_user"
]
},
"sentinelone": {
"identity": {
"analystVerdict": "UNDEFINED",
"analyticsCategory": "ADSecure-DC",
"attackSurfaces": [
"IDENTITY"
],
"classification": "UNKNOWN",
"confidenceLevel": "MALICIOUS",
"id": "19b5cab4-9fdc-49f9-9641-dae9ed9b1c3b",
"name": "DCSync Attack Detected",
"siteId": "1234567890",
"siteName": "Sekoia.io",
"status": "NEW"
}
},
"source": {
"address": "tes.test",
"domain": "tes.test",
"ip": "1.2.3.4",
"subdomain": "tes"
},
"threat": {
"tactic": {
"id": [
"TA006"
],
"name": [
"Credential Access"
]
}
},
"user": {
"domain": "LAB",
"name": "test_user"
}
}
{
"message": "{\"id\": \"01935310-dc47-75de-8925-5f026bd5a705\", \"name\": \"LDAP Search Detected\", \"description\": \"This events is raised when a LDAP search Query is detected from the endpoint.\", \"detectedAt\": \"2024-11-22T08:45:50.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T08:45:50.000Z\", \"lastSeenAt\": \"2024-11-22T08:45:50.000Z\", \"process\": {\"cmdLine\": \"Sharphound.exe\", \"file\": {\"path\": \"c:\\\\users\\\\administrator\\\\desktop\\\\ad_recon\\\\sharphound.exe\", \"sha1\": null, \"sha256\": \"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T08:45:50Z",
"kind": "alert",
"provider": "Identity",
"reason": "This events is raised when a LDAP search Query is detected from the endpoint.",
"start": "2024-11-22T08:45:50Z",
"type": "info"
},
"@timestamp": "2024-11-22T08:45:50Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "Sharphound.exe",
"executable": "c:\\users\\administrator\\desktop\\ad_recon\\sharphound.exe",
"hash": {
"sha256": "61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
},
"name": "sharphound.exe"
},
"related": {
"hash": [
"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "01935310-dc47-75de-8925-5f026bd5a705",
"name": "LDAP Search Detected",
"status": "NEW"
}
}
}
{
"message": "{\n \"analystVerdict\": \"UNDEFINED\",\n \"analytics\": {\n \"category\": \"ThreatPath\"\n },\n \"asset\": {\n \"agentUuid\": null,\n \"agentVersion\": null,\n \"category\": \"Workstation\",\n \"name\": \"Unknown\",\n \"osType\": \"UNKNOWN\",\n \"osVersion\": \"\",\n \"subcategory\": \"Other Workstation\",\n \"type\": \"UNKNOWN\"\n },\n \"assignee\": null,\n \"attackSurfaces\": [\n \"IDENTITY\"\n ],\n \"classification\": \"UNKNOWN\",\n \"confidenceLevel\": \"MALICIOUS\",\n \"description\": \"This event is triggered when a new Privilege Account has been detected in the Active Directory.\",\n \"detectedAt\": \"2024-12-24T05:47:33.726Z\",\n \"detectionSource\": {\n \"product\": \"Identity\"\n },\n \"firstSeenAt\": \"2024-12-24T05:47:33.726Z\",\n \"id\": \"0193f734-d130-773a-815c-fbfe892a2635\",\n \"lastSeenAt\": \"2024-12-24T05:47:33.726Z\",\n \"name\": \"New AD Privilege Accounts Detected\",\n \"process\": null,\n \"rawData\": {\n \"activity_id\": 2,\n \"activity_name\": \"Update\",\n \"attack_surface_ids\": [\n 4\n ],\n \"category_uid\": 2,\n \"class_uid\": 99602001,\n \"confidence_id\": 3,\n \"evidences\": [\n {\n \"actor\": {\n \"user\": {}\n },\n \"dst_endpoint\": {},\n \"src_endpoint\": {}\n }\n ],\n \"finding_info\": {\n \"analytic\": {\n \"category\": \"ThreatPath\",\n \"type_id\": 1,\n \"uid\": \"ThreatPath\"\n },\n \"attacks\": [\n {\n \"tactics\": [\n {\n \"id\": \"xxx-xxx-xxxx\", \"name\": \"Credential Access\",\n \"uid\": \"TA006\"\n }\n ],\n \"technique\": {\n \"name\": \"Exploitation for Credential Access\",\n \"uid\": \"T1212\"\n },\n \"version\": \"ATT&CK v11\"\n }\n ],\n \"desc\": \"This event is triggered when a new Privilege Account has been detected in the Active Directory.\",\n \"first_seen_time\": \"1735026290990\",\n \"internal_uid\": \"316e8d31-9bc5-49b6-a0e2-49f9795bf9e9\",\n \"kill_chain\": [\n {\n \"phase_id\": 0\n }\n ],\n \"last_seen_time\": \"1735026290990\",\n \"title\": \"New AD Privilege Accounts Detected\",\n \"uid\": \"316e8d31-9bc5-49b6-a0e2-49f9795bf9e9\"\n },\n \"message\": \"This event is triggered when a new Privilege Account has been detected in the Active Directory.\",\n \"metadata\": {\n \"extension\": {\n \"name\": \"s1\",\n \"uid\": \"996\",\n \"version\": \"0.1.0\"\n },\n \"product\": {\n \"name\": \"Identity\",\n \"vendor_name\": \"SentinelOne\"\n },\n \"uid\": \"316e8d31-9bc5-49b6-a0e2-49f9795bf9e9\",\n \"version\": \"1.1.0-dev\"\n },\n \"raw_data\": \"5006406:AD Privilege Accounts credentials(S1-Local-Admin) detected in domain:LAB, ip:vm00001.lab at timestamp:1733309067716 of severity:8 subscriberId:6666\",\n \"resources\": [\n {\n \"internal_uid\": \"11111111111111111111111111\",\n \"name\": \"VM0001.LAB\",\n \"s1_metadata\": {\n \"account_id\": \"617755838952421242\",\n \"account_name\": \"EXAMPLE CORP\",\n \"group_id\": \"1107851598374945694\",\n \"group_name\": \"Default Group\",\n \"mgmt_id\": 86061,\n \"scope_id\": \"1107851598374945694\",\n \"scope_level\": \"Group\",\n \"site_id\": \"1107851598374945694\",\n \"site_name\": \"Sekoia.io\"\n },\n \"type\": \"server::other_server::windows_server\",\n \"uid\": \"70629f7d-e514-4a71-b88d-28a466d0fa02VM0001\",\n \"version\": \"Microsoft Windows Server 2012 R2 Standard 64-bit\"\n }\n ],\n \"s1_classification_id\": 0,\n \"severity_id\": 3,\n \"status_id\": 1,\n \"time\": \"1735026290990\",\n \"type_name\": \"\",\n \"type_uid\": \"9960200101\",\n \"unmapped\": {},\n \"verdict_detail_id\": 0,\n \"verdict_id\": 0\n },\n \"result\": null,\n \"status\": \"NEW\",\n \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-12-24T05:47:33.726000Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is triggered when a new Privilege Account has been detected in the Active Directory.",
"start": "2024-12-24T05:47:33.726000Z",
"type": "info"
},
"@timestamp": "2024-12-24T05:47:33.726000Z",
"host": {
"name": "VM0001.LAB",
"os": {
"family": "UNKNOWN"
}
},
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"organization": {
"id": "617755838952421242",
"name": "EXAMPLE CORP"
},
"sentinelone": {
"identity": {
"analystVerdict": "UNDEFINED",
"analyticsCategory": "ThreatPath",
"attackSurfaces": [
"IDENTITY"
],
"classification": "UNKNOWN",
"confidenceLevel": "MALICIOUS",
"id": "0193f734-d130-773a-815c-fbfe892a2635",
"name": "New AD Privilege Accounts Detected",
"siteId": "1107851598374945694",
"siteName": "Sekoia.io",
"status": "NEW"
}
},
"threat": {
"tactic": {
"id": [
"TA006"
],
"name": [
"Credential Access"
]
}
}
}
{
"message": "{\"id\": \"01935359-3eda-7903-93fc-af6a0e5d0a8f\", \"name\": \"Brute force attack - Mass Account Lockout\", \"description\": \"This event is raised when ADAssessor detects lockout of multiple accounts, which could be due to brute-force attempts or a password spray.\", \"detectedAt\": \"2024-11-22T10:09:37.779Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"UNKNOWN\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T10:09:37.779Z\", \"lastSeenAt\": \"2024-11-22T10:09:37.779Z\", \"process\": null, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T10:09:37.779000Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when ADAssessor detects lockout of multiple accounts, which could be due to brute-force attempts or a password spray.",
"start": "2024-11-22T10:09:37.779000Z",
"type": "info"
},
"@timestamp": "2024-11-22T10:09:37.779000Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "UNKNOWN",
"confidenceLevel": "MALICIOUS",
"id": "01935359-3eda-7903-93fc-af6a0e5d0a8f",
"name": "Brute force attack - Mass Account Lockout",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935358-ee81-7eb7-b57f-022c6f0019a9\", \"name\": \"Brute force attack - Mass Account Lockout\", \"description\": \"This event is raised when ADAssessor detects lockout of multiple accounts, which could be due to brute-force attempts or a password spray.\", \"detectedAt\": \"2024-11-22T10:09:17.184Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"UNKNOWN\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T10:09:17.184Z\", \"lastSeenAt\": \"2024-11-22T10:09:17.184Z\", \"process\": null, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T10:09:17.184000Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when ADAssessor detects lockout of multiple accounts, which could be due to brute-force attempts or a password spray.",
"start": "2024-11-22T10:09:17.184000Z",
"type": "info"
},
"@timestamp": "2024-11-22T10:09:17.184000Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "UNKNOWN",
"confidenceLevel": "MALICIOUS",
"id": "01935358-ee81-7eb7-b57f-022c6f0019a9",
"name": "Brute force attack - Mass Account Lockout",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"0193534d-63c1-7497-b854-b883425af3f5\", \"name\": \"Domain Controller Discovery Detected\", \"description\": \"This event is raised when there is a query from an endpoint to find the domain controllers or AD Servers in the Active Directory Domain.\", \"detectedAt\": \"2024-11-22T09:54:58.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T09:54:58.000Z\", \"lastSeenAt\": \"2024-11-22T09:54:58.000Z\", \"process\": {\"cmdLine\": \"\\\"C:\\\\Windows\\\\system32\\\\cmd.exe\\\"\", \"file\": {\"path\": \"c:\\\\windows\\\\system32\\\\cmd.exe\", \"sha1\": null, \"sha256\": \"4D89FC34D5F0F9BABD022271C585A9477BF41E834E46B991DEAA0530FDB25E22\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T09:54:58Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when there is a query from an endpoint to find the domain controllers or AD Servers in the Active Directory Domain.",
"start": "2024-11-22T09:54:58Z",
"type": "info"
},
"@timestamp": "2024-11-22T09:54:58Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "\"C:\\Windows\\system32\\cmd.exe\"",
"executable": "c:\\windows\\system32\\cmd.exe",
"hash": {
"sha256": "4D89FC34D5F0F9BABD022271C585A9477BF41E834E46B991DEAA0530FDB25E22"
},
"name": "cmd.exe"
},
"related": {
"hash": [
"4D89FC34D5F0F9BABD022271C585A9477BF41E834E46B991DEAA0530FDB25E22"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "0193534d-63c1-7497-b854-b883425af3f5",
"name": "Domain Controller Discovery Detected",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935347-abf7-7457-8467-e3443470e6f3\", \"name\": \"AD Domain Computer Enumeration Detected\", \"description\": \"This event is raised when there is a query from an endpoint to dump all the computers in the Active Directory Domain.\", \"detectedAt\": \"2024-11-22T09:45:51.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T09:45:51.000Z\", \"lastSeenAt\": \"2024-11-22T09:45:51.000Z\", \"process\": {\"cmdLine\": \"Sharphound.exe\", \"file\": {\"path\": \"c:\\\\users\\\\administrator\\\\desktop\\\\ad_recon\\\\sharphound.exe\", \"sha1\": null, \"sha256\": \"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T09:45:51Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when there is a query from an endpoint to dump all the computers in the Active Directory Domain.",
"start": "2024-11-22T09:45:51Z",
"type": "info"
},
"@timestamp": "2024-11-22T09:45:51Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "Sharphound.exe",
"executable": "c:\\users\\administrator\\desktop\\ad_recon\\sharphound.exe",
"hash": {
"sha256": "61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
},
"name": "sharphound.exe"
},
"related": {
"hash": [
"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "01935347-abf7-7457-8467-e3443470e6f3",
"name": "AD Domain Computer Enumeration Detected",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935347-b05a-7d28-a929-5294ee16628a\", \"name\": \"Domain Controller Discovery Detected\", \"description\": \"This event is raised when there is a query from an endpoint to find the domain controllers or AD Servers in the Active Directory Domain.\", \"detectedAt\": \"2024-11-22T09:45:51.000Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"ENUMERATION\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T09:45:51.000Z\", \"lastSeenAt\": \"2024-11-22T09:45:51.000Z\", \"process\": {\"cmdLine\": \"Sharphound.exe\", \"file\": {\"path\": \"c:\\\\users\\\\administrator\\\\desktop\\\\ad_recon\\\\sharphound.exe\", \"sha1\": null, \"sha256\": \"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863\", \"md5\": null}, \"parentName\": null}, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T09:45:51Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when there is a query from an endpoint to find the domain controllers or AD Servers in the Active Directory Domain.",
"start": "2024-11-22T09:45:51Z",
"type": "info"
},
"@timestamp": "2024-11-22T09:45:51Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"process": {
"command_line": "Sharphound.exe",
"executable": "c:\\users\\administrator\\desktop\\ad_recon\\sharphound.exe",
"hash": {
"sha256": "61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
},
"name": "sharphound.exe"
},
"related": {
"hash": [
"61F897ED69646E0509F6802FB2D7C5E88C3E3B93C4CA86942E24D203AA878863"
]
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "ENUMERATION",
"confidenceLevel": "MALICIOUS",
"id": "01935347-b05a-7d28-a929-5294ee16628a",
"name": "Domain Controller Discovery Detected",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935342-d073-7ed0-8c5e-2373fc013310\", \"name\": \"Default Admin Account Usage\", \"description\": \"This event is raised for default administrator account logon anywhere in the domain.\", \"detectedAt\": \"2024-11-22T09:45:07.655Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"UNKNOWN\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T09:45:07.655Z\", \"lastSeenAt\": \"2024-11-22T09:45:07.655Z\", \"process\": null, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T09:45:07.655000Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised for default administrator account logon anywhere in the domain.",
"start": "2024-11-22T09:45:07.655000Z",
"type": "info"
},
"@timestamp": "2024-11-22T09:45:07.655000Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "UNKNOWN",
"confidenceLevel": "MALICIOUS",
"id": "01935342-d073-7ed0-8c5e-2373fc013310",
"name": "Default Admin Account Usage",
"status": "NEW"
}
}
}
{
"message": "{\"id\": \"01935322-cc3a-76cc-890b-a1c2d1b815d4\", \"name\": \"Brute force attack - Mass Account Lockout\", \"description\": \"This event is raised when ADAssessor detects lockout of multiple accounts, which could be due to brute-force attempts or a password spray.\", \"detectedAt\": \"2024-11-22T09:10:09.467Z\", \"attackSurfaces\": [\"IDENTITY\"], \"detectionSource\": {\"product\": \"Identity\"}, \"status\": \"NEW\", \"assignee\": null, \"classification\": \"UNKNOWN\", \"confidenceLevel\": \"MALICIOUS\", \"firstSeenAt\": \"2024-11-22T09:10:09.467Z\", \"lastSeenAt\": \"2024-11-22T09:10:09.467Z\", \"process\": null, \"result\": null, \"storylineId\": null}",
"event": {
"category": "intrusion_detection",
"end": "2024-11-22T09:10:09.467000Z",
"kind": "alert",
"provider": "Identity",
"reason": "This event is raised when ADAssessor detects lockout of multiple accounts, which could be due to brute-force attempts or a password spray.",
"start": "2024-11-22T09:10:09.467000Z",
"type": "info"
},
"@timestamp": "2024-11-22T09:10:09.467000Z",
"observer": {
"product": "Singularity Identity",
"vendor": "SentinelOne"
},
"sentinelone": {
"identity": {
"attackSurfaces": [
"IDENTITY"
],
"classification": "UNKNOWN",
"confidenceLevel": "MALICIOUS",
"id": "01935322-cc3a-76cc-890b-a1c2d1b815d4",
"name": "Brute force attack - Mass Account Lockout",
"status": "NEW"
}
}
}
Extracted Fields
The following table lists the fields that are extracted, normalized under the ECS format, analyzed and indexed by the parser. It should be noted that infered fields are not listed.
| Name | Type | Description |
|---|---|---|
@timestamp |
date |
Date/time when the event originated. |
agent.id |
keyword |
Unique identifier of this agent. |
agent.version |
keyword |
Version of the agent. |
destination.domain |
keyword |
The domain name of the destination. |
destination.ip |
ip |
IP address of the destination. |
event.category |
keyword |
Event category. The second categorization field in the hierarchy. |
event.end |
date |
event.end contains the date when the event ended or when the activity was last observed. |
event.kind |
keyword |
The kind of the event. The highest categorization field in the hierarchy. |
event.provider |
keyword |
Source of the event. |
event.reason |
keyword |
Reason why this event happened, according to the source |
event.start |
date |
event.start contains the date when the event started or when the activity was first observed. |
event.type |
keyword |
Event type. The third categorization field in the hierarchy. |
host.name |
keyword |
Name of the host. |
host.os.family |
keyword |
OS family (such as redhat, debian, freebsd, windows). |
host.os.version |
keyword |
Operating system version as a raw string. |
observer.product |
keyword |
The product name of the observer. |
observer.vendor |
keyword |
Vendor name of the observer. |
organization.id |
keyword |
Unique identifier for the organization. |
organization.name |
keyword |
Organization name. |
process.command_line |
wildcard |
Full command line that started the process. |
process.executable |
keyword |
Absolute path to the process executable. |
process.hash.md5 |
keyword |
MD5 hash. |
process.hash.sha1 |
keyword |
SHA1 hash. |
process.hash.sha256 |
keyword |
SHA256 hash. |
process.name |
keyword |
Process name. |
process.parent.name |
keyword |
Process name. |
sentinelone.identity.analystVerdict |
keyword |
|
sentinelone.identity.analyticsCategory |
keyword |
|
sentinelone.identity.attackSurfaces |
keyword |
|
sentinelone.identity.classification |
keyword |
|
sentinelone.identity.confidenceLevel |
keyword |
|
sentinelone.identity.id |
keyword |
|
sentinelone.identity.name |
keyword |
|
sentinelone.identity.result |
keyword |
|
sentinelone.identity.siteId |
keyword |
|
sentinelone.identity.siteName |
keyword |
|
sentinelone.identity.status |
keyword |
|
sentinelone.identity.storyLineId |
keyword |
|
source.domain |
keyword |
The domain name of the source. |
source.ip |
ip |
IP address of the source. |
threat.tactic.id |
keyword |
Threat tactic id. |
threat.tactic.name |
keyword |
Threat tactic. |
user.domain |
keyword |
Name of the directory the user is a member of. |
user.name |
keyword |
Short name or login of the user. |
For more information on the Intake Format, please find the code of the Parser, Smart Descriptions, and Supported Events here.