AWS CloudTrail
Overview
AWS CloudTrail is a service that enables governance, compliance, and operational and risk auditing of your AWS account. With CloudTrail, you can log, continuously monitor, and retain account activity related to actions across your AWS infrastructure. CloudTrail provides the event history of your AWS account activity, including actions taken through the AWS Management Console, AWS SDKs, command line tools, and other AWS services (source: AWS CloudTrail Overview).
- Vendor: AWS
- Supported environment: SaaS
- Detection based on: Telemetry
- Supported application or feature: AWS CloudTrail logs, Services
Configure
Deploying the Data Collection Architecture
This section will guide you through creating all the AWS resources needed to collect AWS logs. If you already have existing resources that you want to use, you may do so, but any potential issues or incompatibilities with this tutorial will be your responsibility.
Prerequisites
In order to set up the AWS architecture, you need an administrator access to the Amazon console with the permissions to create and manage S3 buckets, SQS queues, S3 notifications and users.
Ensure that the IAM user dedicated to accessing the S3 bucket and SQS Queue has the following permissions:
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"sqs:ReceiveMessage", "sqs:DeleteMessage", "sqs:GetQueueUrl"
],
"Principal": {
"AWS": "arn:aws:iam::XXXXXXXXXXXX:user/USERNAME_HERE"
},
"Effect": "Allow",
"Resource": "arn:aws:sqs:REGION_HERE:XXXXXXXXXXXX:NAME_HERE"
},
{
"Action": [
"s3:GetObject"
],
"Principal": {
"AWS": "arn:aws:iam::XXXXXXXXXXXX:user/USERNAME_HERE"
},
"Effect": "Allow",
"Resource": "arn:aws:s3:REGION_HERE:XXXXXXXXXXXX:NAME_HERE/*"
},
]
}
Info
If you want to use SNS queue between S3 and SQS, to allow it you must add the option raw message delivery in your SNS configuration. Otherwise, the SQS queue will not be able to receive messages from the SNS topic and you will not receive any logs in Sekoia.io.
To get started, click on the button below and fill the form on AWS to set up the required environment for Sekoia 
You need to fill 4 inputs:
- Stack name - Name of the stack in CloudFormation (Name of the template)
- BucketName - Name of the S3 Bucket
- IAMUserName - Name of the dedicated user to access the S3 and SQS queue
- SQSName - Name of the SQS queue
Read the different pages and click on Next, then click on Submit.
You can follow the creation in the Events tab (it can take few minutes).
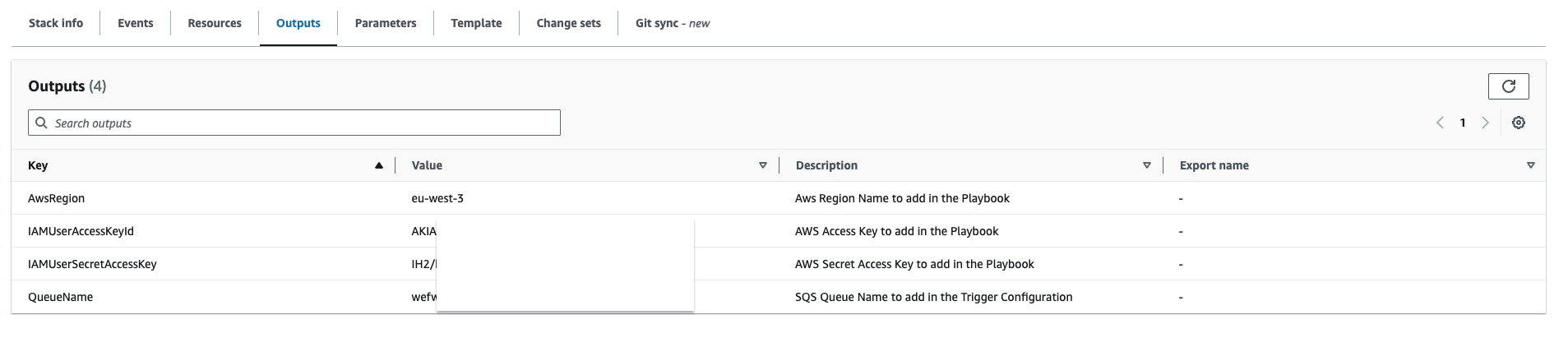
Once finished, it should be displayed on the left CREATE_COMPLETE. Click on the Outputs tab in order to retrieve the information needed for Sekoia playbook.
Create a S3 Bucket
Please refer to this guide to create a S3 Bucket.
Create a SQS queue
The collect will rely on S3 Event Notifications (SQS) to get new S3 objects.
- Create a queue in the SQS service by following this guide
- In the Access Policy step, choose the advanced configuration and adapt this configuration sample with your own SQS Amazon Resource Name (ARN) (the main change is the Service directive allowing S3 bucket access):
{ "Version": "2008-10-17", "Id": "__default_policy_ID", "Statement": [ { "Sid": "__owner_statement", "Effect": "Allow", "Principal": { "Service": "s3.amazonaws.com" }, "Action": "SQS:SendMessage", "Resource": "arn:aws:sqs:XXX:XXX" } ] }
Important
Keep in mind that you have to create the SQS queue in the same region as the S3 bucket you want to watch.
Info
No need to add a prefix in the notification configuration and you can select all S3 events
** Create a S3 Event Notification **
Use the following guide to create S3 Event Notification. Once created:
- Select the notification for object creation in the Event type section
- As the destination, choose the SQS service
- Select the queue you created in the previous section
Send CloudTrail trail to an AWS S3 bucket
To allow Cloudtrail to store logs in S3, you have to create an AWS S3 Policy. Follow this guide to edit your S3 Bucket.
For CloudTrail to record activities across your desired AWS services, you need an active CloudTrail trail.
To configure your trail:
- In the AWS console, navigate to:
Services > CloudTrail > Trails. -
Activate the specific events you want to log:
-
Management events: provide visibility into management operations that are performed on resources in your AWS account.
- Insights events: help AWS users identify and respond to unusual activity associated with write API calls by continuously analyzing CloudTrail management events. Insights events are logged when CloudTrail detects unusual write management API activity in your account.
- Data events: provide visibility into the resource operations performed on or within a resource.
Activate the logging on the trail through the switch button (On/Off) located at the top right corner of the trail page.
Configure Your Intake
This section will guide you through creating the intake object in Sekoia, which provides a unique identifier called the "Intake key." The Intake key is essential for later configuration, as it references the Community, Entity, and Parser (Intake Format) used when receiving raw events on Sekoia.
- Go to the Sekoia Intake page.
- Click on the
+ New Intakebutton at the top right of the page. - Search for your Intake by the product name in the search bar.
- Give it a Name and associate it with an Entity (and a Community if using multi-tenant mode).
- Click on
Create.
Note
For more details on how to use the Intake page and to find the Intake key you just created, refer to this documentation.
Pull events
Create your intake
- Go to the intake page and create a new intake from the
AWS CloudTrail. - Set up the intake account configuration with the AWS Access Key, the secret key and the region name. Set up the intake configuration with the name of the SQS queue
Important
In the "intake configuration" settings, we recommend using the following configuration by default: chunk_size = 10000, frequency = 10 and tick the box "delete_consumed_messages" that will delete S3 notifications of your Amazon Simple Queue Service to avoid duplicates.
Start the playbook and enjoy your events.
Raw Events Samples
In this section, you will find examples of raw logs as generated natively by the source. These examples are provided to help integrators understand the data format before ingestion into Sekoia.io. It is crucial for setting up the correct parsing stages and ensuring that all relevant information is captured.
{
"eventVersion": "1.08",
"userIdentity": {
"type": "Root",
"principalId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"accountId": "1111111111",
"accessKeyId": "ASIA1111111111111",
"sessionContext": {
"sessionIssuer": {},
"webIdFederationData": {},
"attributes": {
"creationDate": "2022-08-31T07:20:10Z",
"mfaAuthenticated": "true"
}
}
},
"eventTime": "2022-08-31T09:48:47Z",
"eventSource": "ec2.amazonaws.com",
"eventName": "ModifyInstanceAttribute",
"awsRegion": "eu-west-3",
"sourceIPAddress": "aws.internal",
"userAgent": "aws.internal",
"requestParameters": {
"instanceId": "i-00000000000000000",
"userData": "<sensitiveDataRemoved>"
},
"responseElements": {
"requestId": "5fcae0f1-790c-4a86-85aa-0b3fd120e341",
"_return": true
},
"requestID": "5fcae0f1-790c-4a86-85aa-0b3fd120e341",
"eventID": "8311ce18-5d58-40f1-a4b3-a757df7cbe47",
"readOnly": false,
"eventType": "AwsApiCall",
"managementEvent": true,
"recipientAccountId": "1111111111",
"eventCategory": "Management",
"sessionCredentialFromConsole": "true"
}
{
"awsRegion": "eu-west-3",
"eventID": "6ffb6978-7b42-47d1-9aa1-1838ec08b514",
"eventName": "LookupEvents",
"eventSource": "cloudtrail.amazonaws.com",
"eventTime": "2020-08-12T12:26:51Z",
"eventType": "AwsApiCall",
"eventVersion": "1.05",
"readOnly": true,
"recipientAccountId": "1111111111",
"requestID": "5b8387cf-59e8-4e6e-ba6d-5fe417820c13",
"requestParameters": {
"eventCategory": "insight",
"maxResults": 50
},
"responseElements": null,
"sourceIPAddress": "1.2.3.4",
"userAgent": "console.amazonaws.com",
"userIdentity": {
"accessKeyId": "ASIA1111111111111",
"accountId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"principalId": "1111111111",
"sessionContext": {
"attributes": {
"creationDate": "2020-08-12T07:04:40Z",
"mfaAuthenticated": "false"
},
"sessionIssuer": {},
"webIdFederationData": {}
},
"type": "Root"
}
}
{
"eventVersion": "1.08",
"userIdentity": {
"type": "IAMUser",
"principalId": "demo",
"arn": "arn:aws:iam::0:user/demo",
"accountId": "00000",
"accessKeyId": "AAAAAAAAA",
"userName": "AAAAAAAAAAAA"
},
"eventTime": "2023-09-29T15:06:45Z",
"eventSource": "ecs.amazonaws.com",
"eventName": "PutClusterCapacityProviders",
"awsRegion": "eu-west-1",
"sourceIPAddress": "00.000.000.00",
"userAgent": "APN/1.0 HashiCorp/1.0 Terraform/1.4.7 (+https://www.terraform.io) terraform-provider-aws/4.59.0 (+https://registry.terraform.io/providers/hashicorp/aws) aws-sdk-go/1.44.221 (go1.19.6; linux; amd64)",
"requestParameters": {
"cluster": "cluster_name",
"capacityProviders": [
"DEMO"
],
"defaultCapacityProviderStrategy": [
{
"capacityProvider": "DEMO",
"weight": 0,
"base": 0
}
]
},
"responseElements": {
"cluster": {
"clusterArn": "arn:aws:ecs:eu-west-1:00000000:cluster/cluster_name",
"clusterName": "cluster_name",
"configuration": {
"executeCommandConfiguration": {
"logging": "OVERRIDE",
"logConfiguration": {
"cloudWatchLogGroupName": "/ecs/cluster/cluster_name",
"cloudWatchEncryptionEnabled": true,
"s3EncryptionEnabled": false
}
}
},
"status": "ACTIVE",
"registeredContainerInstancesCount": 0,
"runningTasksCount": 0,
"pendingTasksCount": 0,
"activeServicesCount": 0,
"statistics": [],
"tags": [],
"settings": [
{
"name": "containerInsights",
"value": "enabled"
}
],
"capacityProviders": [
"DEMO"
],
"defaultCapacityProviderStrategy": [
{
"capacityProvider": "DEMO",
"weight": 0,
"base": 0
}
],
"attachments": [],
"attachmentsStatus": "UPDATE_IN_PROGRESS"
}
},
"readOnly": false,
"eventType": "AwsApiCall",
"managementEvent": true,
"recipientAccountId": "007",
"eventCategory": "Management",
"tlsDetails": {
"tlsVersion": "TLSv1.3",
"cipherSuite": "TLS_AES_128_GCM_SHA256",
"clientProvidedHostHeader": "sekoia.eu-west-1.amazonaws.com"
}
}
{
"eventVersion": "1.05",
"userIdentity": {
"type": "Root",
"principalId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"accountId": "1111111111",
"accessKeyId": "AKIA1111111111"
},
"eventTime": "2020-09-22T15:05:22Z",
"eventSource": "ec2.amazonaws.com",
"eventName": "CreateInstanceExportTask",
"awsRegion": "eu-west-3",
"sourceIPAddress": "1.2.3.4",
"userAgent": "aws-cli/1.18.87 Python/3.7.3 Linux/4.19.0-6-amd64 botocore/1.17.30",
"errorCode": "Client.AuthFailure",
"errorMessage": "vm-import-export@amazon.com must have WRITE and READ_ACL permission on the S3 bucket.",
"requestParameters": {
"instanceId": "i-00000000000000",
"targetEnvironment": "vmware",
"exportToS3": {
"diskImageFormat": "VMDK",
"containerFormat": "ova",
"s3Bucket": "qbo-export-instance-bucket",
"s3Prefix": "vms"
}
},
"responseElements": null,
"requestID": "5d1c2af1-f216-4771-9922-5a032e2826f5",
"eventID": "249e3b13-41d4-4007-8f04-ef4b4f4341ed",
"eventType": "AwsApiCall",
"recipientAccountId": "1111111111"
}
{
"eventVersion": "1.08",
"userIdentity": {
"type": "Root",
"principalId": "111111111111",
"arn": "arn:aws:iam::111111111111:root",
"accountId": "111111111111",
"accessKeyId": "ASI00000000000000000",
"sessionContext": {
"sessionIssuer": {},
"webIdFederationData": {},
"attributes": {
"creationDate": "2022-09-01T06:46:50Z",
"mfaAuthenticated": "true"
}
}
},
"eventTime": "2022-09-01T13:09:23Z",
"eventSource": "ec2.amazonaws.com",
"eventName": "ModifyInstanceAttribute",
"awsRegion": "eu-west-3",
"sourceIPAddress": "AWS Internal",
"userAgent": "AWS Internal",
"requestParameters": {
"instanceId": "i-00000000000000000",
"userData": "<sensitiveDataRemoved>"
},
"responseElements": {
"requestId": "190dc310-2b3e-41bc-ad3f-970f95f24c1b",
"_return": true
},
"requestID": "190dc310-2b3e-41bc-ad3f-970f95f24c1b",
"eventID": "f832abd6-9496-4f3e-9112-796f64b786e3",
"readOnly": false,
"eventType": "AwsApiCall",
"managementEvent": true,
"recipientAccountId": "111111111111",
"eventCategory": "Management",
"sessionCredentialFromConsole": "true"
}
{
"awsRegion": "us-east-1",
"eventID": "76a4c7d1-1f00-4ceb-b7ad-3d355a3515cd",
"eventName": "CreateUser",
"eventSource": "iam.amazonaws.com",
"eventTime": "2020-08-12T12:16:24Z",
"eventType": "AwsApiCall",
"eventVersion": "1.05",
"recipientAccountId": "1111111111",
"requestID": "4ba495c6-03b8-4eb9-a812-95f89835f68c",
"requestParameters": {
"userName": "user"
},
"responseElements": {
"user": {
"arn": "arn:aws:iam::1111111111:user/user",
"createDate": "Aug 12, 2020 12:16:24 PM",
"path": "/",
"userId": "AIDA11111111111111",
"userName": "user"
}
},
"sourceIPAddress": "1.2.3.4",
"userAgent": "aws-cli/1.18.87 Python/3.7.3 Linux/4.19.0-6-amd64 botocore/1.17.30",
"userIdentity": {
"accessKeyId": "AKIA11111111111111",
"accountId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"principalId": "1111111111",
"type": "Root"
}
}
{
"awsRegion": "eu-west-3",
"eventID": "6a957c22-7dd9-4d2e-a9ba-7c869d726293",
"eventName": "Decrypt",
"eventSource": "kms.amazonaws.com",
"eventTime": "2020-08-12T12:48:09Z",
"eventType": "AwsApiCall",
"eventVersion": "1.05",
"readOnly": true,
"recipientAccountId": "1111111111",
"requestID": "3d03af66-1431-4911-b809-ab08b9bd604a",
"requestParameters": {
"encryptionAlgorithm": "SYMMETRIC_DEFAULT",
"encryptionContext": {
"aws:lambda:FunctionArn": "arn:aws:lambda:eu-west-3:1111111111:function:ctstreamer-dev-s3"
}
},
"resources": [
{
"ARN": "arn:aws:kms:eu-west-3:1111111111:key/14eb3a8a-ffec-4b0e-a6da-e901d5e6ee9c",
"accountId": "1111111111",
"type": "AWS::KMS::Key"
}
],
"responseElements": null,
"sourceIPAddress": "1.2.3.4",
"userAgent": "aws-internal/3 aws-sdk-java/1.11.802 Linux/4.14.181-108.257.amzn1.x86_64 OpenJDK_64-Bit_Server_VM/11.0.7+10-LTS java/11.0.7 vendor/Amazon.com_Inc.",
"userIdentity": {
"accessKeyId": "ASIA11111111111111",
"accountId": "1111111111",
"arn": "arn:aws:sts::1111111111:assumed-role/user/ctstreamer-dev-s3",
"principalId": "AROA11111111111111:ctstreamer-dev-s3",
"sessionContext": {
"attributes": {
"creationDate": "2020-08-12T12:03:12Z",
"mfaAuthenticated": "false"
},
"sessionIssuer": {
"accountId": "1111111111",
"arn": "arn:aws:iam::1111111111:role/user",
"principalId": "AROA11111111111111",
"type": "Role",
"userName": "user"
},
"webIdFederationData": {}
},
"type": "AssumedRole"
}
}
{
"eventVersion": "1.08",
"userIdentity": {
"type": "Root",
"principalId": "111111111111",
"arn": "arn:aws:iam::111111111111:root",
"accountId": "111111111111",
"accessKeyId": "ASI00000000000000000",
"sessionContext": {
"sessionIssuer": {},
"webIdFederationData": {},
"attributes": {
"creationDate": "2022-09-01T06:46:50Z",
"mfaAuthenticated": "true"
}
}
},
"eventTime": "2022-09-01T14:13:11Z",
"eventSource": "rds.amazonaws.com",
"eventName": "ModifyDBInstance",
"awsRegion": "eu-west-3",
"sourceIPAddress": "AWS Internal",
"userAgent": "AWS Internal",
"requestParameters": {
"dBInstanceIdentifier": "database-1",
"applyImmediately": true,
"masterUserPassword": "****",
"allowMajorVersionUpgrade": false,
"maxAllocatedStorage": 1000
},
"responseElements": {
"dBInstanceIdentifier": "database-1",
"dBInstanceClass": "db.m6g.large",
"engine": "postgres",
"dBInstanceStatus": "available",
"masterUsername": "postgres",
"endpoint": {
"address": "x.rds.amazonaws.com",
"port": 5432,
"hostedZoneId": "ZMESEXB7ZGGQ3"
},
"allocatedStorage": 100,
"instanceCreateTime": "Sep 1, 2022 12:47:35 PM",
"preferredBackupWindow": "10:10-10:40",
"backupRetentionPeriod": 7,
"dBSecurityGroups": [],
"vpcSecurityGroups": [
{
"vpcSecurityGroupId": "sg-00000000000000000",
"status": "active"
}
],
"dBParameterGroups": [
{
"dBParameterGroupName": "default.postgres13",
"parameterApplyStatus": "in-sync"
}
],
"availabilityZone": "eu-west-3b",
"dBSubnetGroup": {
"dBSubnetGroupName": "default-vpc-00000000000000000",
"dBSubnetGroupDescription": "Created from the RDS Management Console",
"vpcId": "vpc-00000000000000000",
"subnetGroupStatus": "Complete",
"subnets": [
{
"subnetIdentifier": "subnet-00000000000000000",
"subnetAvailabilityZone": {
"name": "eu-west-3a"
},
"subnetOutpost": {},
"subnetStatus": "Active"
}
]
},
"preferredMaintenanceWindow": "thu:04:33-thu:05:03",
"pendingModifiedValues": {
"masterUserPassword": "****"
},
"latestRestorableTime": "Sep 1, 2022 2:07:11 PM",
"multiAZ": true,
"engineVersion": "13.7",
"autoMinorVersionUpgrade": true,
"readReplicaDBInstanceIdentifiers": [],
"licenseModel": "postgresql-license",
"iops": 3000,
"storageThroughput": 0,
"optionGroupMemberships": [
{
"optionGroupName": "default:postgres-13",
"status": "in-sync"
}
],
"secondaryAvailabilityZone": "eu-west-3c",
"publiclyAccessible": false,
"storageType": "io1",
"dbInstancePort": 0,
"storageEncrypted": true,
"kmsKeyId": "arn:aws:kms:eu-west-3:111111111111:key/a7dce59f-5b3c-4178-90e1-91103a32b26d",
"dbiResourceId": "db-00000000000000000000000000",
"cACertificateIdentifier": "rds-ca-2019",
"domainMemberships": [],
"copyTagsToSnapshot": true,
"monitoringInterval": 60,
"enhancedMonitoringResourceArn": "arn:aws:logs:eu-west-3:111111111111:group:schema:stream:db-00000000000000000000000000",
"monitoringRoleArn": "arn:aws:iam::111111111111:role/role",
"dBInstanceArn": "arn:aws:rds:eu-west-3:111111111111:db:database-1",
"iAMDatabaseAuthenticationEnabled": false,
"performanceInsightsEnabled": true,
"performanceInsightsKMSKeyId": "arn:aws:kms:eu-west-3:111111111111:key/a7dce59f-5b3c-4178-90e1-91103a32b26d",
"performanceInsightsRetentionPeriod": 7,
"deletionProtection": true,
"associatedRoles": [],
"httpEndpointEnabled": false,
"maxAllocatedStorage": 1000,
"tagList": [],
"customerOwnedIpEnabled": false,
"networkType": "IPV4",
"backupTarget": "region"
},
"requestID": "fc070739-07b9-4533-9652-eec872b5ad3d",
"eventID": "eee4217d-4a93-4ad3-89ff-108b25c4c9ab",
"readOnly": false,
"eventType": "AwsApiCall",
"managementEvent": true,
"recipientAccountId": "111111111111",
"eventCategory": "Management",
"sessionCredentialFromConsole": "true"
}
{
"awsRegion": "eu-west-3",
"eventID": "bcf6f457-76bc-4e8c-8a7b-8a2451481675",
"eventName": "AssumeRole",
"eventSource": "sts.amazonaws.com",
"eventTime": "2020-08-12T12:03:12Z",
"eventType": "AwsApiCall",
"eventVersion": "1.05",
"recipientAccountId": "1111111111",
"requestID": "34c3d58a-83f5-42cc-9e4d-1beeb85f809c",
"requestParameters": {
"roleArn": "arn:aws:iam::1111111111:role/user",
"roleSessionName": "session-name"
},
"resources": [
{
"ARN": "arn:aws:iam::1111111111:role/user",
"accountId": "1111111111",
"type": "AWS::IAM::Role"
}
],
"responseElements": {
"credentials": {
"accessKeyId": "ASIA11111111111111",
"expiration": "Aug 13, 2020, 12:03:12 AM",
"sessionToken": "11111111111111111111111111111111111111111"
}
},
"sharedEventID": "e0b224e9-a818-452c-87e3-a1d4078bb102",
"sourceIPAddress": "lambda.amazonaws.com",
"userAgent": "lambda.amazonaws.com",
"userIdentity": {
"invokedBy": "lambda.amazonaws.com",
"type": "AWSService"
}
}
{
"additionalEventData": {
"LoginTo": "https://console.aws.amazon.com/billing/home?region=eu-west-3&state=hashArgs%23%2F&isauthcode=true",
"MFAUsed": "No",
"MobileVersion": "No"
},
"awsRegion": "us-east-1",
"eventID": "9d4ca355-a7d3-4422-96ae-dbe2c3431609",
"eventName": "ConsoleLogin",
"eventSource": "signin.amazonaws.com",
"eventTime": "2020-08-19T15:33:43Z",
"eventType": "AwsConsoleSignIn",
"eventVersion": "1.05",
"recipientAccountId": "1111111111",
"requestParameters": null,
"responseElements": {
"ConsoleLogin": "Success"
},
"sourceIPAddress": "1.2.3.4",
"userAgent": "Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0",
"userIdentity": {
"accessKeyId": "",
"accountId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"principalId": "1111111111",
"type": "Root"
}
}
{
"awsRegion": "eu-west-3",
"eventID": "bcf6f457-76bc-4e8c-8a7b-8a2451481675",
"eventName": "AssumeRole",
"eventSource": "sts.amazonaws.com",
"eventTime": "2020-08-12T12:03:12Z",
"eventType": "AwsApiCall",
"eventVersion": "1.05",
"recipientAccountId": "1111111111",
"requestID": "34c3d58a-83f5-42cc-9e4d-1beeb85f809c",
"requestParameters": {
"roleArn": "arn:aws:iam::1111111111:role/user",
"roleSessionName": "session-name"
},
"resources": [
{
"ARN": "arn:aws:iam::1111111111:role/user",
"accountId": "1111111111",
"type": "AWS::IAM::Role"
}
],
"responseElements": {
"credentials": {
"accessKeyId": "ASIA11111111111111",
"expiration": "Aug 13, 2020, 12:03:12 AM",
"sessionToken": "1111111111111111111111111111111111111111111111111111111111111111111111111"
}
},
"sharedEventID": "e0b224e9-a818-452c-87e3-a1d4078bb102",
"sourceIPAddress": "lambda.amazonaws.com",
"userAgent": "lambda.amazonaws.com",
"userIdentity": {
"invokedBy": "lambda.amazonaws.com",
"type": "AWSService"
}
}
{
"eventVersion": "1.09",
"userIdentity": {
"accessKeyId": "ASIA1111111111111",
"accountId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"principalId": "1111111111",
"sessionContext": {
"attributes": {
"creationDate": "2020-08-12T07:04:40Z",
"mfaAuthenticated": "false"
},
"sessionIssuer": {},
"webIdFederationData": {}
},
"type": "Root"
},
"eventTime": "2025-07-25T04:25:16Z",
"eventSource": "connect.amazonaws.com",
"eventName": "ListRealtimeContactAnalysisSegmentsV2",
"awsRegion": "eu-west-3",
"sourceIPAddress": "connect.amazonaws.com",
"userAgent": "connect.amazonaws.com",
"requestParameters": {
"InstanceId": "arn%3Aaws%3Aconnect%3Aeu-west-3%3A111111111111%3Ainstance%2F1d9a8bf6-5051-477e-b1c2-e5834a4a34b5",
"SegmentTypes": [
"Transcript",
"Issues",
"Event",
"Attachments",
"Categories"
],
"ContactId": "1d3e6813-0fa5-487e-9c48-0d93abb06241",
"OutputType": "Raw"
},
"responseElements": {
"Status": "COMPLETED",
"Segments": [
{
"Transcript": {
"Id": "cfa1f07b-41c9-433c-a913-3a64987038a1",
"ParticipantId": "8aaadd53-1a04-4f37-986d-690bca5b0a4a",
"ParticipantRole": "CUSTOMER",
"DisplayName": "JDOE",
"ContentType": "text/plain",
"Time": {
"AbsoluteTime": "2025-07-25T04:18:43.097Z"
},
"Sentiment": "NEUTRAL",
"Content": "\uc548\ub155\ud558\uc138\uc694 \uace0\uac1d\ub2d8,\n\n\ud83e\udd16 \ubcf8 \ucc44\ub110\uc740 \ucc57\ubd07\uc744 \ud1b5\ud574 \uc790\ub3d9\uc73c\ub85c \uc751\ub2f5\ub4dc\ub9ac\uace0 \uc788\uc2b5\ub2c8\ub2e4."
}
}
],
"Channel": "CHAT"
},
"requestID": "3e3d2004-23a7-4856-a680-af60f7a52b07",
"eventID": "18312058-5aae-41a9-9a72-9c47a50ece24",
"readOnly": false,
"eventType": "AwsApiCall",
"managementEvent": true,
"recipientAccountId": "111111111111",
"eventCategory": "Management"
}
{
"eventVersion": "1.08",
"eventTime": "2022-09-05T07:45:00Z",
"awsRegion": "eu-west-3",
"eventID": "7a9130fc-ca15-49d9-b4aa-685f7a0c182a",
"eventType": "AwsCloudTrailInsight",
"recipientAccountId": "1111111111",
"sharedEventID": "0a771801-c0cc-406d-a080-219de884f089",
"insightDetails": {
"state": "End",
"eventSource": "s3.amazonaws.com",
"eventName": "GetBucketPolicy",
"insightType": "ApiErrorRateInsight",
"errorCode": "NoSuchBucketPolicy",
"insightContext": {
"statistics": {
"baseline": {
"average": 0.0021817492
},
"insight": {
"average": 1.3333333333
},
"insightDuration": 3,
"baselineDuration": 10542
},
"attributions": [
{
"attribute": "userIdentityArn",
"insight": [
{
"value": "arn:aws:iam::1111111111:root",
"average": 1.3333333333
}
],
"baseline": [
{
"value": "arn:aws:iam::1111111111:root",
"average": 0.0020868905
},
{
"value": "arn:aws:sts::1111111111:assumed-role/AWSServiceRoleForConfig/AWSConfig-Describe",
"average": 9.48587e-05
}
]
},
{
"attribute": "userAgent",
"insight": [
{
"value": "[S3Console/0.4, aws-internal/3 aws-sdk-java/1.11.1030 Linux/5.4.204-124.362.amzn2int.x86_64 OpenJDK_64-Bit_Server_VM/25.302-b08 java/1.8.0_302 vendor/Oracle_Corporation cfg/retry-mode/standard]",
"average": 0.6666666667
},
{
"value": "[S3Console/0.4, aws-internal/3 aws-sdk-java/1.11.1030 Linux/5.4.207-126.363.amzn2int.x86_64 OpenJDK_64-Bit_Server_VM/25.302-b08 java/1.8.0_302 vendor/Oracle_Corporation cfg/retry-mode/standard]",
"average": 0.6666666667
}
],
"baseline": [
{
"value": "[S3Console/0.4, aws-internal/3 aws-sdk-java/1.11.1030 Linux/5.4.204-124.362.amzn2int.x86_64 OpenJDK_64-Bit_Server_VM/25.302-b08 java/1.8.0_302 vendor/Oracle_Corporation cfg/retry-mode/standard]",
"average": 0.0010434453
},
{
"value": "[S3Console/0.4, aws-internal/3 aws-sdk-java/1.11.1030 Linux/5.4.207-126.363.amzn2int.x86_64 OpenJDK_64-Bit_Server_VM/25.302-b08 java/1.8.0_302 vendor/Oracle_Corporation cfg/retry-mode/standard]",
"average": 0.0009485866
},
{
"value": "AWS Internal",
"average": 0.0001897173
}
]
}
]
}
},
"eventCategory": "Insight"
}
{
"eventVersion": "1.08",
"userIdentity": {
"type": "AssumedRole",
"principalId": "AR0000000000000000:1111111111111111111111111",
"arn": "arn:aws:sts::1111111111:assumed-role/role/1111111111111111111111111",
"accountId": "1111111111",
"accessKeyId": "AS000000000000000000",
"sessionContext": {
"sessionIssuer": {
"type": "Role",
"principalId": "AR0000000000000000",
"arn": "arn:aws:iam::1111111111:role/service-role/username",
"accountId": "1111111111",
"userName": "username"
},
"webIdFederationData": {},
"attributes": {
"creationDate": "2022-09-09T07:45:14Z",
"mfaAuthenticated": "false"
}
}
},
"eventTime": "2022-09-09T09:17:32Z",
"eventSource": "elasticfilesystem.amazonaws.com",
"eventName": "NewClientConnection",
"awsRegion": "eu-central-1",
"sourceIPAddress": "AWS Internal",
"userAgent": "elasticfilesystem",
"requestParameters": null,
"responseElements": null,
"eventID": "6ff7e265-b0b9-42c0-b4b5-ad140a7f1baa",
"readOnly": true,
"resources": [
{
"accountId": "1111111111",
"type": "AWS::EFS::FileSystem",
"ARN": "arn:aws:elasticfilesystem:eu-central-1:1111111111:file-system/fs-00000000"
},
{
"accountId": "1111111111",
"type": "AWS::EFS::AccessPoint",
"ARN": "arn:aws:elasticfilesystem:eu-central-1:1111111111:access-point/fsap-00000000000000000"
}
],
"eventType": "AwsServiceEvent",
"managementEvent": true,
"recipientAccountId": "1111111111",
"serviceEventDetails": {
"permissions": {
"ClientRootAccess": false,
"ClientMount": true,
"ClientWrite": true
},
"sourceIpAddress": "1.2.3.4"
},
"eventCategory": "Management"
}
{
"eventVersion": "1.08",
"userIdentity": {
"type": "AssumedRole",
"principalId": "A00000000000000000000:user@example.org",
"arn": "arn:aws:sts::111111111:assumed-role/role/user@example.org",
"accountId": "111111111"
},
"eventTime": "2022-09-08T15:01:59Z",
"eventSource": "signin.amazonaws.com",
"eventName": "ConsoleLogin",
"awsRegion": "us-east-1",
"sourceIPAddress": "1.2.3.4",
"userAgent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.0.0 Safari/537.36",
"requestParameters": null,
"responseElements": {
"ConsoleLogin": "Success"
},
"additionalEventData": {
"LoginTo": "https://console.aws.amazon.com/console/home",
"MobileVersion": "No",
"MFAUsed": "No",
"SamlProviderArn": "arn:aws:iam::111111111:saml-provider/provider-name"
},
"eventID": "e7dd6d97-2d3a-45dc-bb19-a3ea347091e3",
"readOnly": false,
"eventType": "AwsConsoleSignIn",
"managementEvent": true,
"recipientAccountId": "111111111",
"eventCategory": "Management",
"tlsDetails": {
"tlsVersion": "TLSv1.2",
"cipherSuite": "ECDHE-RSA-AES128-GCM-SHA256",
"clientProvidedHostHeader": "signin.aws.amazon.com"
}
}
Detection section
The following section provides information for those who wish to learn more about the detection capabilities enabled by collecting this intake. It includes details about the built-in rule catalog, event categories, and ECS fields extracted from raw events. This is essential for users aiming to create custom detection rules, perform hunting activities, or pivot in the events page.
Related Built-in Rules
The following Sekoia.io built-in rules match the intake AWS CloudTrail. This documentation is updated automatically and is based solely on the fields used by the intake which are checked against our rules. This means that some rules will be listed but might not be relevant with the intake.
SEKOIA.IO x AWS CloudTrail on ATT&CK Navigator
AWS CloudTrail Config DeleteConfigurationRecorder
Detects when the Configuration Recorder was deleted. The configuration recorder is used to detect changes in your resource configurations and capture these changes as configuration items.
- Effort: intermediate
AWS CloudTrail Config Disable Channel/Recorder
Detects AWS Config Service disabling channel or recorder
- Effort: elementary
AWS CloudTrail Disable MFA
Detects a user disabling the multi factor authentication mechanism for its account. It could be a sign of malicious activity.
- Effort: intermediate
AWS CloudTrail EC2 CreateKeyPair
Detects when a key pair is created. Usually, SendSSHPublicKey is used afterwards to push the created key to an EC2 instance in order to be able to establish a connection to that instance.
- Effort: advanced
AWS CloudTrail EC2 CreateVPC
Detects when a VPC is created.
- Effort: advanced
AWS CloudTrail EC2 DeleteKeyPair
Detects when a specific key pair is deleted. This means the public key was removed from EC2.
- Effort: advanced
AWS CloudTrail EC2 Enable Serial Console Access
Detects when the EC2 serial console access feature is enabled. This could abused by some attackers to avoid network detection when accessing to EC2 instances.
- Effort: intermediate
AWS CloudTrail EC2 Instance Connect SendSSHPublicKey
Detects when an attacker is pushing an SSH Public Key to an EC2 instance. Then he can establish a connection to the console using SSH.
- Effort: advanced
AWS CloudTrail EC2 Instance Connect SendSerialConsoleSSHPublicKey
Detects when an attacker is pushing an SSH Public Key to an EC2 instance. Then he can establish a serial connection to the console using SSH.
- Effort: advanced
AWS CloudTrail EC2 Security Group Modified
Detects when an AWS EC2 security group has been modified
- Effort: master
AWS CloudTrail EC2 Startup Script Changed
Detects changes to the EC2 instance startup script. The shell script will be executed as root/SYSTEM everytime the specific instances are booted up.
- Effort: intermediate
AWS CloudTrail EC2 Subnet Deleted
Detects when an attacker is destroying an EC2 subnet.
- Effort: master
AWS CloudTrail EC2 VM Export Failure
Detects attempt to export an AWS EC2 instance. A VM Export might indicate an attempt to extract information from an instance.
- Effort: intermediate
AWS CloudTrail ECS Cluster Deleted
Detects when an attacker is destroying an AWS ECS Cluster
- Effort: intermediate
AWS CloudTrail EventBridge Rule Disabled Or Deleted
Detects when an attacker is trying to evade defenses by deleting or disabling EventBridge rules
- Effort: master
AWS CloudTrail GuardDuty Detector Deleted
Detects when an attacker is trying to evade defenses by deleting a GuardDuty detector
- Effort: intermediate
AWS CloudTrail GuardDuty Detector Suspended
Detects the suspension of the GuardDuty service
- Effort: intermediate
AWS CloudTrail GuardDuty Disruption
Detects updates of the GuardDuty list of trusted IPs, perhaps to disable security alerts against malicious IPs
- Effort: intermediate
AWS CloudTrail IAM AWSCompromisedKeyQuarantineV2
Detects when AWS CloudTrail detected an AWS Access Key that was compromised, and then quarantined by AWS. This could indicate for instance that the private key was found on a GitHub public repository.
- Effort: elementary
AWS CloudTrail IAM AddClientIDToOpenIDConnectProvider
Detects the addition of a Client ID to an existing identity provider that supports OpenID Connect.
- Effort: intermediate
AWS CloudTrail IAM ChangePassword
Detects when an IAM user wants to change its password.
- Effort: advanced
AWS CloudTrail IAM CreateOpenIDConnectProvider
Detects the creation of an IAM entity to describe an identity provider that supports OpenID Connect.
- Effort: intermediate
AWS CloudTrail IAM CreateSAMLProvider
Detects when an IAM user creates a SAML provider, which could allow third-party connection and therefore could be used by attackers.
- Effort: intermediate
AWS CloudTrail IAM DeleteOpenIDConnectProvider
Detects the deletion of an IAM entity to describe an identity provider that supports OpenID Connect.
- Effort: intermediate
AWS CloudTrail IAM DeleteSAMLProvider
Detects when an IAM user deletes a SAML provider, which could be performed by attackers to cover their tracks.
- Effort: intermediate
AWS CloudTrail IAM Failed User Creation
Detects an attemp to create a user account where the result is an explicit denied.
- Effort: intermediate
AWS CloudTrail IAM Password Policy Updated
Detects an update to the password policy. This could be an attempt to lower accounts security level.
- Effort: intermediate
AWS CloudTrail IAM Policy Changed
Detects change on AWS IAM Policy
- Effort: master
AWS CloudTrail IAM RemoveClientIDFromOpenIDConnectProvider
Detects when a Client ID is removed from an identity provider that supports OpenID Connect. Could be used by attackers for sabotage or to cover their tracks.
- Effort: intermediate
AWS CloudTrail IAM UpdateOpenIDConnectProviderThumbprint
Detects the update of a ThumbPrint from an identity provider that supports OpenID Connect. This could be a sign of an attacker adding a trusted certificate.
- Effort: intermediate
AWS CloudTrail IAM UpdateSAMLProvider
Detects when an IAM user updates a SAML provider. Attackers could perform that to be stealthy by adding a third-party connection into an existing SAML provider.
- Effort: intermediate
AWS CloudTrail Important Change
Detects disabling, deleting and updating of a Trail source which could be done by some attackers trying to masquerade their activity.
- Effort: advanced
AWS CloudTrail KMS CMK Key Deleted
Detects when a CMK is deleted or scheduled for deletion
- Effort: advanced
AWS CloudTrail RDS Change Master Password
Detects the change of database master password. It may be a part of data exfiltration.
- Effort: intermediate
AWS CloudTrail RDS DB Cluster/Instance Deleted
Detects when an attacker is destroying a RDS Cluster or Instance
- Effort: advanced
AWS CloudTrail RDS Public DB Restore
Detects the recovery of a new public database instance from a snapshot. It may be a part of data exfiltration.
- Effort: intermediate
AWS CloudTrail Remove Flow logs
Detects when an attacker is removing Flow Logs to cover their tracks
- Effort: advanced
AWS CloudTrail Root ConsoleLogin
Detects a login with a root account on AWS portal. It is a best practice to avoid root account usage for daily tasks and to create an IAM admin user.
- Effort: intermediate
AWS CloudTrail Route 53 Domain Transfer Attempt
Detects when a request in success or failure is made to transfer a domain name to an other AWS account
- Effort: intermediate
AWS CloudTrail Route 53 Domain Transfer Lock Disabled
Detects when the transfer lock feature is disabled on a domain name handled by AWS Route 53 service.
- Effort: elementary
AWS CloudTrail S3 Bucket Replication
Detects a replication rule being enable for a given S3 bucket: it could provide an attacker a way to exfiltrate data.
- Effort: master
AWS Persistence By Creating KeyPair And SecurityGroup
Attackers can use AWS credentials to create a KeyPair and a SecurityGroup to have continuous access to the AWS account.
- Effort: master
AWS Suspicious Discovery Commands
Attackers often use discovery commands such as DescribeInstances or DescribeSecurityGroups, and many others, to find how an AWS tenant is configured.
- Effort: master
Account Added To A Security Enabled Group
Detection in order to investigate who has added a specific Domain User in Domain Admins or Group Policy Creator Owners (Security event 4728)
- Effort: master
Account Removed From A Security Enabled Group
Detection in order to investigate who has removed a specific Domain User in Domain Admins or Group Policy Creator Owners (Security event 4729)
- Effort: master
Backup Catalog Deleted
The rule detects when the Backup Catalog has been deleted. It means the administrators will not be able to access any backups that were created earlier to perform recoveries. This is often being done using the wbadmin.exe tool.
- Effort: intermediate
Computer Account Deleted
Detects computer account deletion.
- Effort: master
Cryptomining
Detection of domain names potentially related to cryptomining activities.
- Effort: master
DHCP Server Error Failed Loading the CallOut DLL
This rule detects a DHCP server error in which a specified Callout DLL (in registry) could not be loaded.
- Effort: intermediate
DHCP Server Loaded the CallOut DLL
This rule detects a DHCP server in which a specified Callout DLL (in registry) was loaded. This would indicate a succesful attack against DHCP service allowing to disrupt the service or alter the integrity of the responses.
- Effort: intermediate
DNS Server Error Failed Loading The ServerLevelPluginDLL
This rule detects a DNS server error in which a specified plugin DLL (in registry) could not be loaded. This requires the dedicated Windows event provider Microsoft-Windows-DNS-Server-Service.
- Effort: master
Domain Trust Created Or Removed
A trust was created or removed to a domain. An attacker could perform that in order to do lateral movement easily between domains or shutdown the ability of two domains to communicate.
- Effort: advanced
Dynamic DNS Contacted
Detect communication with dynamic dns domain. This kind of domain is often used by attackers. This rule can trigger false positive in non-controlled environment because dynamic dns is not always malicious.
- Effort: master
Exfiltration Domain
Detects traffic toward a domain flagged as a possible exfiltration vector.
- Effort: master
Login Brute-Force Successful On SentinelOne EDR Management Console
A user has attempted to login several times (brute-force) on the SentinelOne EDR Management Console and succeeded to login.
- Effort: master
Microsoft Defender Antivirus History Deleted
Windows Defender history has been deleted. Could be an attempt by an attacker to remove its traces.
- Effort: master
Microsoft Defender Antivirus Tampering Detected
Detection of Windows Defender Tampering, from definitions' deletion to deactivation of parts or all of Defender.
- Effort: advanced
Microsoft Defender Antivirus Threat Detected
Detection of a windows defender alert indicating the presence of potential malware
- Effort: advanced
Nimbo-C2 User Agent
Nimbo-C2 Uses an unusual User-Agent format in its implants.
- Effort: intermediate
Password Change On Directory Service Restore Mode (DSRM) Account
The Directory Service Restore Mode (DSRM) account is a local administrator account on Domain Controllers. Attackers may change the password to gain persistence.
- Effort: intermediate
Possible Replay Attack
This event can be a sign of Kerberos replay attack or, among other things, network device configuration or routing problems.
- Effort: master
Potential Bazar Loader User-Agents
Detects potential Bazar loader communications through the user-agent
- Effort: elementary
Potential Lemon Duck User-Agent
Detects LemonDuck user agent. The format used two sets of alphabetical characters separated by dashes, for example "User-Agent: Lemon-Duck-[A-Z]-[A-Z]".
- Effort: elementary
Potential RDP Connection To Non-Domain Host
Detects logons using NTLM to hosts that are potentially not part of the domain using RDP (TermSrv). Event ID 8001 corresponds to outgoing NTLM authentication traffic and TermSrv stands for RDP Terminal Services Server. Check if the contacted host is legitimate. To use this detection rule, enable logging of outbound NTLM authentications on all domain controllers, using the following Group Policy (GPO) - Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options > Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers -> Define this policy setting: Audit all.
- Effort: master
Remote Access Tool Domain
Detects traffic toward a domain flagged as a Remote Administration Tool (RAT).
- Effort: master
Remote Monitoring and Management Software - AnyDesk
Detect artifacts related to the installation or execution of the Remote Monitoring and Management tool AnyDesk.
- Effort: master
SEKOIA.IO Intelligence Feed
Detect threats based on indicators of compromise (IOCs) collected by SEKOIA's Threat and Detection Research team.
- Effort: elementary
Sekoia.io EICAR Detection
Detects observables in Sekoia.io CTI tagged as EICAR, which are fake samples meant to test detection.
- Effort: master
TOR Usage Generic Rule
Detects TOR usage globally, whether the IP is a destination or source. TOR is short for The Onion Router, and it gets its name from how it works. TOR intercepts the network traffic from one or more apps on user’s computer, usually the user web browser, and shuffles it through a number of randomly-chosen computers before passing it on to its destination. This disguises user location, and makes it harder for servers to pick him/her out on repeat visits, or to tie together separate visits to different sites, this making tracking and surveillance more difficult. Before a network packet starts its journey, user’s computer chooses a random list of relays and repeatedly encrypts the data in multiple layers, like an onion. Each relay knows only enough to strip off the outermost layer of encryption, before passing what’s left on to the next relay in the list.
- Effort: master
User Account Created
Detects user creation on windows servers, which shouldn't happen in an Active Directory environment. Apply this on your windows server logs and not on your DC logs. One default account defaultuser0 is excluded as only used during Windows set-up. This detection use Security Event ID 4720.
- Effort: master
User Account Deleted
Detects local user deletion
- Effort: master
Event Categories
The following table lists the data source offered by this integration.
| Data Source | Description |
|---|---|
AWS CloudTrail logs |
Cloudtrail events are analyzed in detail |
Services |
CloudTrail logs activities from all AWS Services |
In details, the following table denotes the type of events produced by this integration.
| Name | Values |
|---|---|
| Kind | `` |
| Category | authentication, iam, network |
| Type | access, change |
Transformed Events Samples after Ingestion
This section demonstrates how the raw logs will be transformed by our parsers. It shows the extracted fields that will be available for use in the built-in detection rules and hunting activities in the events page. Understanding these transformations is essential for analysts to create effective detection mechanisms with custom detection rules and to leverage the full potential of the collected data.
{
"message": "{\"eventVersion\":\"1.08\",\"userIdentity\":{\"type\":\"Root\",\"principalId\":\"1111111111\",\"arn\":\"arn:aws:iam::1111111111:root\",\"accountId\":\"1111111111\",\"accessKeyId\":\"ASIA1111111111111\",\"sessionContext\":{\"sessionIssuer\":{},\"webIdFederationData\":{},\"attributes\":{\"creationDate\":\"2022-08-31T07:20:10Z\",\"mfaAuthenticated\":\"true\"}}},\"eventTime\":\"2022-08-31T09:48:47Z\",\"eventSource\":\"ec2.amazonaws.com\",\"eventName\":\"ModifyInstanceAttribute\",\"awsRegion\":\"eu-west-3\",\"sourceIPAddress\":\"aws.internal\",\"userAgent\":\"aws.internal\",\"requestParameters\":{\"instanceId\":\"i-00000000000000000\",\"userData\":\"<sensitiveDataRemoved>\"},\"responseElements\":{\"requestId\":\"5fcae0f1-790c-4a86-85aa-0b3fd120e341\",\"_return\":true},\"requestID\":\"5fcae0f1-790c-4a86-85aa-0b3fd120e341\",\"eventID\":\"8311ce18-5d58-40f1-a4b3-a757df7cbe47\",\"readOnly\":false,\"eventType\":\"AwsApiCall\",\"managementEvent\":true,\"recipientAccountId\":\"1111111111\",\"eventCategory\":\"Management\",\"sessionCredentialFromConsole\":\"true\"}",
"event": {
"action": "ModifyInstanceAttribute",
"category": [
"network"
],
"outcome": "success",
"provider": "ec2.amazonaws.com",
"type": [
"access"
]
},
"@timestamp": "2022-08-31T09:48:47Z",
"action": {
"name": "ModifyInstanceAttribute",
"outcome": "success",
"properties": {
"recipientAccountId": "1111111111",
"requestParameters": {
"userData": "<sensitiveDataRemoved>"
},
"userIdentity": {
"accountId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"principalId": "1111111111",
"sessionContext": {
"attributes": {
"mfaAuthenticated": "true"
}
},
"type": "Root"
}
},
"target": "network-traffic",
"type": "AwsApiCall"
},
"aws": {
"cloudtrail": {
"flattened": {
"request_parameters": "{\"instanceId\":\"i-00000000000000000\",\"userData\":\"<sensitiveDataRemoved>\"}",
"response_elements": "{\"requestId\":\"5fcae0f1-790c-4a86-85aa-0b3fd120e341\",\"_return\":true}"
},
"user_identity": {
"accessKeyId": "ASIA1111111111111",
"accountId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"principalId": "1111111111",
"type": "Root"
}
}
},
"cloud": {
"account": {
"id": "1111111111"
},
"instance": {
"id": "i-00000000000000000"
},
"provider": "aws",
"region": "eu-west-3",
"service": {
"name": "cloudtrail"
}
},
"related": {
"hosts": [
"aws.internal"
]
},
"source": {
"address": "aws.internal",
"domain": "aws.internal",
"subdomain": "aws"
},
"user": {
"id": "1111111111"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Other",
"original": "aws.internal",
"os": {
"name": "Other"
}
}
}
{
"message": "{\"awsRegion\":\"eu-west-3\",\"eventID\":\"6ffb6978-7b42-47d1-9aa1-1838ec08b514\",\"eventName\":\"LookupEvents\",\"eventSource\":\"cloudtrail.amazonaws.com\",\"eventTime\":\"2020-08-12T12:26:51Z\",\"eventType\":\"AwsApiCall\",\"eventVersion\":\"1.05\",\"readOnly\":true,\"recipientAccountId\":\"1111111111\",\"requestID\":\"5b8387cf-59e8-4e6e-ba6d-5fe417820c13\",\"requestParameters\":{\"eventCategory\":\"insight\",\"maxResults\":50},\"responseElements\":null,\"sourceIPAddress\":\"1.2.3.4\",\"userAgent\":\"console.amazonaws.com\",\"userIdentity\":{\"accessKeyId\":\"ASIA1111111111111\",\"accountId\":\"1111111111\",\"arn\":\"arn:aws:iam::1111111111:root\",\"principalId\":\"1111111111\",\"sessionContext\":{\"attributes\":{\"creationDate\":\"2020-08-12T07:04:40Z\",\"mfaAuthenticated\":\"false\"},\"sessionIssuer\":{},\"webIdFederationData\":{}},\"type\":\"Root\"}}",
"event": {
"action": "LookupEvents",
"category": [
"network"
],
"outcome": "success",
"provider": "cloudtrail.amazonaws.com",
"type": [
"access"
]
},
"@timestamp": "2020-08-12T12:26:51Z",
"action": {
"name": "LookupEvents",
"outcome": "success",
"properties": {
"recipientAccountId": "1111111111",
"userIdentity": {
"accountId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"principalId": "1111111111",
"sessionContext": {
"attributes": {
"mfaAuthenticated": "false"
}
},
"type": "Root"
}
},
"target": "network-traffic",
"type": "AwsApiCall"
},
"aws": {
"cloudtrail": {
"flattened": {
"request_parameters": "{\"eventCategory\":\"insight\",\"maxResults\":50}"
},
"user_identity": {
"accessKeyId": "ASIA1111111111111",
"accountId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"principalId": "1111111111",
"type": "Root"
}
}
},
"cloud": {
"account": {
"id": "1111111111"
},
"provider": "aws",
"region": "eu-west-3",
"service": {
"name": "cloudtrail"
}
},
"related": {
"ip": [
"1.2.3.4"
]
},
"source": {
"address": "1.2.3.4",
"ip": "1.2.3.4"
},
"user": {
"id": "1111111111"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Other",
"original": "console.amazonaws.com",
"os": {
"name": "Other"
}
}
}
{
"message": "{\n \"eventVersion\": \"1.08\",\n \"userIdentity\": {\n \"type\": \"IAMUser\",\n \"principalId\": \"demo\",\n \"arn\": \"arn:aws:iam::0:user/demo\",\n \"accountId\": \"00000\",\n \"accessKeyId\": \"AAAAAAAAA\",\n \"userName\": \"AAAAAAAAAAAA\"\n },\n \"eventTime\": \"2023-09-29T15:06:45Z\",\n \"eventSource\": \"ecs.amazonaws.com\",\n \"eventName\": \"PutClusterCapacityProviders\",\n \"awsRegion\": \"eu-west-1\",\n \"sourceIPAddress\": \"00.000.000.00\",\n \"userAgent\": \"APN/1.0 HashiCorp/1.0 Terraform/1.4.7 (+https://www.terraform.io) terraform-provider-aws/4.59.0 (+https://registry.terraform.io/providers/hashicorp/aws) aws-sdk-go/1.44.221 (go1.19.6; linux; amd64)\",\n \"requestParameters\": {\n \"cluster\": \"cluster_name\",\n \"capacityProviders\": [\n \"DEMO\"\n ],\n \"defaultCapacityProviderStrategy\": [\n {\n \"capacityProvider\": \"DEMO\",\n \"weight\": 0,\n \"base\": 0\n }\n ]\n },\n \"responseElements\": {\n \"cluster\": {\n \"clusterArn\": \"arn:aws:ecs:eu-west-1:00000000:cluster/cluster_name\",\n \"clusterName\": \"cluster_name\",\n \"configuration\": {\n \"executeCommandConfiguration\": {\n \"logging\": \"OVERRIDE\",\n \"logConfiguration\": {\n \"cloudWatchLogGroupName\": \"/ecs/cluster/cluster_name\",\n \"cloudWatchEncryptionEnabled\": true,\n \"s3EncryptionEnabled\": false\n }\n }\n },\n \"status\": \"ACTIVE\",\n \"registeredContainerInstancesCount\": 0,\n \"runningTasksCount\": 0,\n \"pendingTasksCount\": 0,\n \"activeServicesCount\": 0,\n \"statistics\": [],\n \"tags\": [],\n \"settings\": [\n {\n \"name\": \"containerInsights\",\n \"value\": \"enabled\"\n }\n ],\n \"capacityProviders\": [\n \"DEMO\"\n ],\n \"defaultCapacityProviderStrategy\": [\n {\n \"capacityProvider\": \"DEMO\",\n \"weight\": 0,\n \"base\": 0\n }\n ],\n \"attachments\": [],\n \"attachmentsStatus\": \"UPDATE_IN_PROGRESS\"\n }\n },\n \"readOnly\": false,\n \"eventType\": \"AwsApiCall\",\n \"managementEvent\": true,\n \"recipientAccountId\": \"007\",\n \"eventCategory\": \"Management\",\n \"tlsDetails\": {\n \"tlsVersion\": \"TLSv1.3\",\n \"cipherSuite\": \"TLS_AES_128_GCM_SHA256\",\n \"clientProvidedHostHeader\": \"sekoia.eu-west-1.amazonaws.com\"\n }\n}",
"event": {
"action": "PutClusterCapacityProviders",
"category": [
"network"
],
"outcome": "success",
"provider": "ecs.amazonaws.com",
"type": [
"access"
]
},
"@timestamp": "2023-09-29T15:06:45Z",
"action": {
"name": "PutClusterCapacityProviders",
"outcome": "success",
"properties": {
"recipientAccountId": "007",
"userIdentity": {
"accountId": "00000",
"arn": "arn:aws:iam::0:user/demo",
"principalId": "demo",
"type": "IAMUser",
"userName": "AAAAAAAAAAAA"
}
},
"target": "network-traffic",
"type": "AwsApiCall"
},
"aws": {
"cloudtrail": {
"cluster_name": "cluster_name",
"flattened": {
"request_parameters": "{\"capacityProviders\":[\"DEMO\"],\"cluster\":\"cluster_name\",\"defaultCapacityProviderStrategy\":[{\"base\":0,\"capacityProvider\":\"DEMO\",\"weight\":0}]}",
"response_elements": "{\"cluster\":{\"clusterArn\":\"arn:aws:ecs:eu-west-1:00000000:cluster/cluster_name\",\"clusterName\":\"cluster_name\",\"configuration\":{\"executeCommandConfiguration\":{\"logging\":\"OVERRIDE\",\"logConfiguration\":{\"cloudWatchLogGroupName\":\"/ecs/cluster/cluster_name\",\"cloudWatchEncryptionEnabled\":true,\"s3EncryptionEnabled\":false}}},\"status\":\"ACTIVE\",\"registeredContainerInstancesCount\":0,\"runningTasksCount\":0,\"pendingTasksCount\":0,\"activeServicesCount\":0,\"statistics\":[],\"tags\":[],\"settings\":[{\"name\":\"containerInsights\",\"value\":\"enabled\"}],\"capacityProviders\":[\"DEMO\"],\"defaultCapacityProviderStrategy\":[{\"capacityProvider\":\"DEMO\",\"weight\":0,\"base\":0}],\"attachments\":[],\"attachmentsStatus\":\"UPDATE_IN_PROGRESS\"}}"
},
"user_identity": {
"accessKeyId": "AAAAAAAAA",
"accountId": "00000",
"arn": "arn:aws:iam::0:user/demo",
"principalId": "demo",
"type": "IAMUser"
}
}
},
"cloud": {
"account": {
"id": "00000"
},
"provider": "aws",
"region": "eu-west-1",
"service": {
"name": "cloudtrail"
}
},
"tls": {
"cipher": "TLS_AES_128_GCM_SHA256",
"version": "TLSv1.3"
},
"user": {
"id": "00000"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "aws-sdk-go",
"original": "APN/1.0 HashiCorp/1.0 Terraform/1.4.7 (+https://www.terraform.io) terraform-provider-aws/4.59.0 (+https://registry.terraform.io/providers/hashicorp/aws) aws-sdk-go/1.44.221 (go1.19.6; linux; amd64)",
"os": {
"name": "Linux"
},
"version": "1.44.221"
}
}
{
"message": "{\"eventVersion\": \"1.05\", \"userIdentity\": {\"type\": \"Root\", \"principalId\": \"1111111111\", \"arn\": \"arn:aws:iam::1111111111:root\", \"accountId\": \"1111111111\", \"accessKeyId\": \"AKIA1111111111\"}, \"eventTime\": \"2020-09-22T15:05:22Z\", \"eventSource\": \"ec2.amazonaws.com\", \"eventName\": \"CreateInstanceExportTask\", \"awsRegion\": \"eu-west-3\", \"sourceIPAddress\": \"1.2.3.4\", \"userAgent\": \"aws-cli/1.18.87 Python/3.7.3 Linux/4.19.0-6-amd64 botocore/1.17.30\", \"errorCode\": \"Client.AuthFailure\", \"errorMessage\": \"vm-import-export@amazon.com must have WRITE and READ_ACL permission on the S3 bucket.\", \"requestParameters\": {\"instanceId\": \"i-00000000000000\", \"targetEnvironment\": \"vmware\", \"exportToS3\": {\"diskImageFormat\": \"VMDK\", \"containerFormat\": \"ova\", \"s3Bucket\": \"qbo-export-instance-bucket\", \"s3Prefix\": \"vms\"}}, \"responseElements\": null, \"requestID\": \"5d1c2af1-f216-4771-9922-5a032e2826f5\", \"eventID\": \"249e3b13-41d4-4007-8f04-ef4b4f4341ed\", \"eventType\": \"AwsApiCall\", \"recipientAccountId\": \"1111111111\"}",
"event": {
"action": "CreateInstanceExportTask",
"category": [
"network"
],
"code": "Client.AuthFailure",
"outcome": "success",
"provider": "ec2.amazonaws.com",
"reason": "vm-import-export@amazon.com must have WRITE and READ_ACL permission on the S3 bucket.",
"type": [
"access"
]
},
"@timestamp": "2020-09-22T15:05:22Z",
"action": {
"name": "CreateInstanceExportTask",
"outcome": "success",
"properties": {
"errorCode": "Client.AuthFailure",
"errorMessage": "vm-import-export@amazon.com must have WRITE and READ_ACL permission on the S3 bucket.",
"recipientAccountId": "1111111111",
"userIdentity": {
"accountId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"principalId": "1111111111",
"type": "Root"
}
},
"target": "network-traffic",
"type": "AwsApiCall"
},
"aws": {
"cloudtrail": {
"flattened": {
"request_parameters": "{\"exportToS3\":{\"containerFormat\":\"ova\",\"diskImageFormat\":\"VMDK\",\"s3Bucket\":\"qbo-export-instance-bucket\",\"s3Prefix\":\"vms\"},\"instanceId\":\"i-00000000000000\",\"targetEnvironment\":\"vmware\"}"
},
"user_identity": {
"accessKeyId": "AKIA1111111111",
"accountId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"principalId": "1111111111",
"type": "Root"
}
}
},
"cloud": {
"account": {
"id": "1111111111"
},
"instance": {
"id": "i-00000000000000"
},
"provider": "aws",
"region": "eu-west-3",
"service": {
"name": "cloudtrail"
}
},
"related": {
"ip": [
"1.2.3.4"
]
},
"source": {
"address": "1.2.3.4",
"ip": "1.2.3.4"
},
"user": {
"id": "1111111111"
},
"user_agent": {
"device": {
"name": "Spider"
},
"name": "aws-cli",
"original": "aws-cli/1.18.87 Python/3.7.3 Linux/4.19.0-6-amd64 botocore/1.17.30",
"os": {
"name": "Linux",
"version": "4.19.0"
},
"version": "1.18.87"
}
}
{
"message": "{\"eventVersion\":\"1.08\",\"userIdentity\":{\"type\":\"Root\",\"principalId\":\"111111111111\",\"arn\":\"arn:aws:iam::111111111111:root\",\"accountId\":\"111111111111\",\"accessKeyId\":\"ASI00000000000000000\",\"sessionContext\":{\"sessionIssuer\":{},\"webIdFederationData\":{},\"attributes\":{\"creationDate\":\"2022-09-01T06:46:50Z\",\"mfaAuthenticated\":\"true\"}}},\"eventTime\":\"2022-09-01T13:09:23Z\",\"eventSource\":\"ec2.amazonaws.com\",\"eventName\":\"ModifyInstanceAttribute\",\"awsRegion\":\"eu-west-3\",\"sourceIPAddress\":\"AWS Internal\",\"userAgent\":\"AWS Internal\",\"requestParameters\":{\"instanceId\":\"i-00000000000000000\",\"userData\":\"<sensitiveDataRemoved>\"},\"responseElements\":{\"requestId\":\"190dc310-2b3e-41bc-ad3f-970f95f24c1b\",\"_return\":true},\"requestID\":\"190dc310-2b3e-41bc-ad3f-970f95f24c1b\",\"eventID\":\"f832abd6-9496-4f3e-9112-796f64b786e3\",\"readOnly\":false,\"eventType\":\"AwsApiCall\",\"managementEvent\":true,\"recipientAccountId\":\"111111111111\",\"eventCategory\":\"Management\",\"sessionCredentialFromConsole\":\"true\"}\n",
"event": {
"action": "ModifyInstanceAttribute",
"category": [
"network"
],
"outcome": "success",
"provider": "ec2.amazonaws.com",
"type": [
"access"
]
},
"@timestamp": "2022-09-01T13:09:23Z",
"action": {
"name": "ModifyInstanceAttribute",
"outcome": "success",
"properties": {
"recipientAccountId": "111111111111",
"requestParameters": {
"userData": "<sensitiveDataRemoved>"
},
"userIdentity": {
"accountId": "111111111111",
"arn": "arn:aws:iam::111111111111:root",
"principalId": "111111111111",
"sessionContext": {
"attributes": {
"mfaAuthenticated": "true"
}
},
"type": "Root"
}
},
"target": "network-traffic",
"type": "AwsApiCall"
},
"aws": {
"cloudtrail": {
"flattened": {
"request_parameters": "{\"instanceId\":\"i-00000000000000000\",\"userData\":\"<sensitiveDataRemoved>\"}",
"response_elements": "{\"requestId\":\"190dc310-2b3e-41bc-ad3f-970f95f24c1b\",\"_return\":true}"
},
"user_identity": {
"accessKeyId": "ASI00000000000000000",
"accountId": "111111111111",
"arn": "arn:aws:iam::111111111111:root",
"principalId": "111111111111",
"type": "Root"
}
}
},
"cloud": {
"account": {
"id": "111111111111"
},
"instance": {
"id": "i-00000000000000000"
},
"provider": "aws",
"region": "eu-west-3",
"service": {
"name": "cloudtrail"
}
},
"user": {
"id": "111111111111"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Other",
"original": "AWS Internal",
"os": {
"name": "Other"
}
}
}
{
"message": "{\"awsRegion\":\"us-east-1\",\"eventID\":\"76a4c7d1-1f00-4ceb-b7ad-3d355a3515cd\",\"eventName\":\"CreateUser\",\"eventSource\":\"iam.amazonaws.com\",\"eventTime\":\"2020-08-12T12:16:24Z\",\"eventType\":\"AwsApiCall\",\"eventVersion\":\"1.05\",\"recipientAccountId\":\"1111111111\",\"requestID\":\"4ba495c6-03b8-4eb9-a812-95f89835f68c\",\"requestParameters\":{\"userName\":\"user\"},\"responseElements\":{\"user\":{\"arn\":\"arn:aws:iam::1111111111:user/user\",\"createDate\":\"Aug 12, 2020 12:16:24 PM\",\"path\":\"/\",\"userId\":\"AIDA11111111111111\",\"userName\":\"user\"}},\"sourceIPAddress\":\"1.2.3.4\",\"userAgent\":\"aws-cli/1.18.87 Python/3.7.3 Linux/4.19.0-6-amd64 botocore/1.17.30\",\"userIdentity\":{\"accessKeyId\":\"AKIA11111111111111\",\"accountId\":\"1111111111\",\"arn\":\"arn:aws:iam::1111111111:root\",\"principalId\":\"1111111111\",\"type\":\"Root\"}}",
"event": {
"action": "CreateUser",
"category": [
"network"
],
"outcome": "success",
"provider": "iam.amazonaws.com",
"type": [
"access"
]
},
"@timestamp": "2020-08-12T12:16:24Z",
"action": {
"name": "CreateUser",
"outcome": "success",
"properties": {
"recipientAccountId": "1111111111",
"userIdentity": {
"accountId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"principalId": "1111111111",
"type": "Root"
}
},
"target": "network-traffic",
"type": "AwsApiCall"
},
"aws": {
"cloudtrail": {
"flattened": {
"request_parameters": "{\"userName\":\"user\"}",
"response_elements": "{\"user\":{\"arn\":\"arn:aws:iam::1111111111:user/user\",\"createDate\":\"Aug 12, 2020 12:16:24 PM\",\"path\":\"/\",\"userId\":\"AIDA11111111111111\",\"userName\":\"user\"}}"
},
"response_elements": {
"user": {
"userName": "user"
}
},
"user_identity": {
"accessKeyId": "AKIA11111111111111",
"accountId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"principalId": "1111111111",
"type": "Root"
}
}
},
"cloud": {
"account": {
"id": "1111111111"
},
"provider": "aws",
"region": "us-east-1",
"service": {
"name": "cloudtrail"
}
},
"related": {
"ip": [
"1.2.3.4"
],
"user": [
"AIDA11111111111111"
]
},
"source": {
"address": "1.2.3.4",
"ip": "1.2.3.4"
},
"user": {
"id": "1111111111",
"name": "AIDA11111111111111"
},
"user_agent": {
"device": {
"name": "Spider"
},
"name": "aws-cli",
"original": "aws-cli/1.18.87 Python/3.7.3 Linux/4.19.0-6-amd64 botocore/1.17.30",
"os": {
"name": "Linux",
"version": "4.19.0"
},
"version": "1.18.87"
}
}
{
"message": "{\"awsRegion\":\"eu-west-3\",\"eventID\":\"6a957c22-7dd9-4d2e-a9ba-7c869d726293\",\"eventName\":\"Decrypt\",\"eventSource\":\"kms.amazonaws.com\",\"eventTime\":\"2020-08-12T12:48:09Z\",\"eventType\":\"AwsApiCall\",\"eventVersion\":\"1.05\",\"readOnly\":true,\"recipientAccountId\":\"1111111111\",\"requestID\":\"3d03af66-1431-4911-b809-ab08b9bd604a\",\"requestParameters\":{\"encryptionAlgorithm\":\"SYMMETRIC_DEFAULT\",\"encryptionContext\":{\"aws:lambda:FunctionArn\":\"arn:aws:lambda:eu-west-3:1111111111:function:ctstreamer-dev-s3\"}},\"resources\":[{\"ARN\":\"arn:aws:kms:eu-west-3:1111111111:key/14eb3a8a-ffec-4b0e-a6da-e901d5e6ee9c\",\"accountId\":\"1111111111\",\"type\":\"AWS::KMS::Key\"}],\"responseElements\":null,\"sourceIPAddress\":\"1.2.3.4\",\"userAgent\":\"aws-internal/3 aws-sdk-java/1.11.802 Linux/4.14.181-108.257.amzn1.x86_64 OpenJDK_64-Bit_Server_VM/11.0.7+10-LTS java/11.0.7 vendor/Amazon.com_Inc.\",\"userIdentity\":{\"accessKeyId\":\"ASIA11111111111111\",\"accountId\":\"1111111111\",\"arn\":\"arn:aws:sts::1111111111:assumed-role/user/ctstreamer-dev-s3\",\"principalId\":\"AROA11111111111111:ctstreamer-dev-s3\",\"sessionContext\":{\"attributes\":{\"creationDate\":\"2020-08-12T12:03:12Z\",\"mfaAuthenticated\":\"false\"},\"sessionIssuer\":{\"accountId\":\"1111111111\",\"arn\":\"arn:aws:iam::1111111111:role/user\",\"principalId\":\"AROA11111111111111\",\"type\":\"Role\",\"userName\":\"user\"},\"webIdFederationData\":{}},\"type\":\"AssumedRole\"}}",
"event": {
"action": "Decrypt",
"category": [
"network"
],
"outcome": "success",
"provider": "kms.amazonaws.com",
"type": [
"access"
]
},
"@timestamp": "2020-08-12T12:48:09Z",
"action": {
"name": "Decrypt",
"outcome": "success",
"properties": {
"recipientAccountId": "1111111111",
"resources": [
{
"ARN": "arn:aws:kms:eu-west-3:1111111111:key/14eb3a8a-ffec-4b0e-a6da-e901d5e6ee9c"
}
],
"userIdentity": {
"accountId": "1111111111",
"arn": "arn:aws:sts::1111111111:assumed-role/user/ctstreamer-dev-s3",
"principalId": "AROA11111111111111:ctstreamer-dev-s3",
"sessionContext": {
"attributes": {
"mfaAuthenticated": "false"
},
"sessionIssuer": {
"arn": "arn:aws:iam::1111111111:role/user",
"type": "Role",
"userName": "user"
}
},
"type": "AssumedRole"
}
},
"target": "network-traffic",
"type": "AwsApiCall"
},
"aws": {
"cloudtrail": {
"flattened": {
"request_parameters": "{\"encryptionAlgorithm\":\"SYMMETRIC_DEFAULT\",\"encryptionContext\":{\"aws:lambda:FunctionArn\":\"arn:aws:lambda:eu-west-3:1111111111:function:ctstreamer-dev-s3\"}}"
},
"user_identity": {
"accessKeyId": "ASIA11111111111111",
"accountId": "1111111111",
"arn": "arn:aws:sts::1111111111:assumed-role/user/ctstreamer-dev-s3",
"principalId": "AROA11111111111111:ctstreamer-dev-s3",
"sessionContext": {
"sessionIssuer": {
"arn": "arn:aws:iam::1111111111:role/user",
"userName": "user"
}
},
"type": "AssumedRole"
}
}
},
"cloud": {
"account": {
"id": "1111111111"
},
"provider": "aws",
"region": "eu-west-3",
"service": {
"name": "cloudtrail"
}
},
"related": {
"ip": [
"1.2.3.4"
]
},
"source": {
"address": "1.2.3.4",
"ip": "1.2.3.4"
},
"user": {
"id": "1111111111"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "aws-sdk-java",
"original": "aws-internal/3 aws-sdk-java/1.11.802 Linux/4.14.181-108.257.amzn1.x86_64 OpenJDK_64-Bit_Server_VM/11.0.7+10-LTS java/11.0.7 vendor/Amazon.com_Inc.",
"os": {
"name": "Linux",
"version": "4.14.181"
},
"version": "1.11.802"
}
}
{
"message": "{\"eventVersion\":\"1.08\",\"userIdentity\":{\"type\":\"Root\",\"principalId\":\"111111111111\",\"arn\":\"arn:aws:iam::111111111111:root\",\"accountId\":\"111111111111\",\"accessKeyId\":\"ASI00000000000000000\",\"sessionContext\":{\"sessionIssuer\":{},\"webIdFederationData\":{},\"attributes\":{\"creationDate\":\"2022-09-01T06:46:50Z\",\"mfaAuthenticated\":\"true\"}}},\"eventTime\":\"2022-09-01T14:13:11Z\",\"eventSource\":\"rds.amazonaws.com\",\"eventName\":\"ModifyDBInstance\",\"awsRegion\":\"eu-west-3\",\"sourceIPAddress\":\"AWS Internal\",\"userAgent\":\"AWS Internal\",\"requestParameters\":{\"dBInstanceIdentifier\":\"database-1\",\"applyImmediately\":true,\"masterUserPassword\":\"****\",\"allowMajorVersionUpgrade\":false,\"maxAllocatedStorage\":1000},\"responseElements\":{\"dBInstanceIdentifier\":\"database-1\",\"dBInstanceClass\":\"db.m6g.large\",\"engine\":\"postgres\",\"dBInstanceStatus\":\"available\",\"masterUsername\":\"postgres\",\"endpoint\":{\"address\":\"x.rds.amazonaws.com\",\"port\":5432,\"hostedZoneId\":\"ZMESEXB7ZGGQ3\"},\"allocatedStorage\":100,\"instanceCreateTime\":\"Sep 1, 2022 12:47:35 PM\",\"preferredBackupWindow\":\"10:10-10:40\",\"backupRetentionPeriod\":7,\"dBSecurityGroups\":[],\"vpcSecurityGroups\":[{\"vpcSecurityGroupId\":\"sg-00000000000000000\",\"status\":\"active\"}],\"dBParameterGroups\":[{\"dBParameterGroupName\":\"default.postgres13\",\"parameterApplyStatus\":\"in-sync\"}],\"availabilityZone\":\"eu-west-3b\",\"dBSubnetGroup\":{\"dBSubnetGroupName\":\"default-vpc-00000000000000000\",\"dBSubnetGroupDescription\":\"Created from the RDS Management Console\",\"vpcId\":\"vpc-00000000000000000\",\"subnetGroupStatus\":\"Complete\",\"subnets\":[{\"subnetIdentifier\":\"subnet-00000000000000000\",\"subnetAvailabilityZone\":{\"name\":\"eu-west-3a\"},\"subnetOutpost\":{},\"subnetStatus\":\"Active\"}]},\"preferredMaintenanceWindow\":\"thu:04:33-thu:05:03\",\"pendingModifiedValues\":{\"masterUserPassword\":\"****\"},\"latestRestorableTime\":\"Sep 1, 2022 2:07:11 PM\",\"multiAZ\":true,\"engineVersion\":\"13.7\",\"autoMinorVersionUpgrade\":true,\"readReplicaDBInstanceIdentifiers\":[],\"licenseModel\":\"postgresql-license\",\"iops\":3000,\"storageThroughput\":0,\"optionGroupMemberships\":[{\"optionGroupName\":\"default:postgres-13\",\"status\":\"in-sync\"}],\"secondaryAvailabilityZone\":\"eu-west-3c\",\"publiclyAccessible\":false,\"storageType\":\"io1\",\"dbInstancePort\":0,\"storageEncrypted\":true,\"kmsKeyId\":\"arn:aws:kms:eu-west-3:111111111111:key/a7dce59f-5b3c-4178-90e1-91103a32b26d\",\"dbiResourceId\":\"db-00000000000000000000000000\",\"cACertificateIdentifier\":\"rds-ca-2019\",\"domainMemberships\":[],\"copyTagsToSnapshot\":true,\"monitoringInterval\":60,\"enhancedMonitoringResourceArn\":\"arn:aws:logs:eu-west-3:111111111111:group:schema:stream:db-00000000000000000000000000\",\"monitoringRoleArn\":\"arn:aws:iam::111111111111:role/role\",\"dBInstanceArn\":\"arn:aws:rds:eu-west-3:111111111111:db:database-1\",\"iAMDatabaseAuthenticationEnabled\":false,\"performanceInsightsEnabled\":true,\"performanceInsightsKMSKeyId\":\"arn:aws:kms:eu-west-3:111111111111:key/a7dce59f-5b3c-4178-90e1-91103a32b26d\",\"performanceInsightsRetentionPeriod\":7,\"deletionProtection\":true,\"associatedRoles\":[],\"httpEndpointEnabled\":false,\"maxAllocatedStorage\":1000,\"tagList\":[],\"customerOwnedIpEnabled\":false,\"networkType\":\"IPV4\",\"backupTarget\":\"region\"},\"requestID\":\"fc070739-07b9-4533-9652-eec872b5ad3d\",\"eventID\":\"eee4217d-4a93-4ad3-89ff-108b25c4c9ab\",\"readOnly\":false,\"eventType\":\"AwsApiCall\",\"managementEvent\":true,\"recipientAccountId\":\"111111111111\",\"eventCategory\":\"Management\",\"sessionCredentialFromConsole\":\"true\"}\n",
"event": {
"action": "ModifyDBInstance",
"category": [
"network"
],
"outcome": "success",
"provider": "rds.amazonaws.com",
"type": [
"access"
]
},
"@timestamp": "2022-09-01T14:13:11Z",
"action": {
"name": "ModifyDBInstance",
"outcome": "success",
"properties": {
"recipientAccountId": "111111111111",
"responseElements": {
"publiclyAccessible": false
},
"userIdentity": {
"accountId": "111111111111",
"arn": "arn:aws:iam::111111111111:root",
"principalId": "111111111111",
"sessionContext": {
"attributes": {
"mfaAuthenticated": "true"
}
},
"type": "Root"
}
},
"target": "network-traffic",
"type": "AwsApiCall"
},
"aws": {
"cloudtrail": {
"flattened": {
"request_parameters": "{\"dBInstanceIdentifier\":\"database-1\",\"applyImmediately\":true,\"masterUserPassword\":\"****\",\"allowMajorVersionUpgrade\":false,\"maxAllocatedStorage\":1000}",
"response_elements": "{\"dBInstanceIdentifier\":\"database-1\",\"dBInstanceClass\":\"db.m6g.large\",\"engine\":\"postgres\",\"dBInstanceStatus\":\"available\",\"masterUsername\":\"postgres\",\"endpoint\":{\"address\":\"x.rds.amazonaws.com\",\"port\":5432,\"hostedZoneId\":\"ZMESEXB7ZGGQ3\"},\"allocatedStorage\":100,\"instanceCreateTime\":\"Sep 1, 2022 12:47:35 PM\",\"preferredBackupWindow\":\"10:10-10:40\",\"backupRetentionPeriod\":7,\"dBSecurityGroups\":[],\"vpcSecurityGroups\":[{\"vpcSecurityGroupId\":\"sg-00000000000000000\",\"status\":\"active\"}],\"dBParameterGroups\":[{\"dBParameterGroupName\":\"default.postgres13\",\"parameterApplyStatus\":\"in-sync\"}],\"availabilityZone\":\"eu-west-3b\",\"dBSubnetGroup\":{\"dBSubnetGroupName\":\"default-vpc-00000000000000000\",\"dBSubnetGroupDescription\":\"Created from the RDS Management Console\",\"vpcId\":\"vpc-00000000000000000\",\"subnetGroupStatus\":\"Complete\",\"subnets\":[{\"subnetIdentifier\":\"subnet-00000000000000000\",\"subnetAvailabilityZone\":{\"name\":\"eu-west-3a\"},\"subnetOutpost\":{},\"subnetStatus\":\"Active\"}]},\"preferredMaintenanceWindow\":\"thu:04:33-thu:05:03\",\"pendingModifiedValues\":{\"masterUserPassword\":\"****\"},\"latestRestorableTime\":\"Sep 1, 2022 2:07:11 PM\",\"multiAZ\":true,\"engineVersion\":\"13.7\",\"autoMinorVersionUpgrade\":true,\"readReplicaDBInstanceIdentifiers\":[],\"licenseModel\":\"postgresql-license\",\"iops\":3000,\"storageThroughput\":0,\"optionGroupMemberships\":[{\"optionGroupName\":\"default:postgres-13\",\"status\":\"in-sync\"}],\"secondaryAvailabilityZone\":\"eu-west-3c\",\"publiclyAccessible\":false,\"storageType\":\"io1\",\"dbInstancePort\":0,\"storageEncrypted\":true,\"kmsKeyId\":\"arn:aws:kms:eu-west-3:111111111111:key/a7dce59f-5b3c-4178-90e1-91103a32b26d\",\"dbiResourceId\":\"db-00000000000000000000000000\",\"cACertificateIdentifier\":\"rds-ca-2019\",\"domainMemberships\":[],\"copyTagsToSnapshot\":true,\"monitoringInterval\":60,\"enhancedMonitoringResourceArn\":\"arn:aws:logs:eu-west-3:111111111111:group:schema:stream:db-00000000000000000000000000\",\"monitoringRoleArn\":\"arn:aws:iam::111111111111:role/role\",\"dBInstanceArn\":\"arn:aws:rds:eu-west-3:111111111111:db:database-1\",\"iAMDatabaseAuthenticationEnabled\":false,\"performanceInsightsEnabled\":true,\"performanceInsightsKMSKeyId\":\"arn:aws:kms:eu-west-3:111111111111:key/a7dce59f-5b3c-4178-90e1-91103a32b26d\",\"performanceInsightsRetentionPeriod\":7,\"deletionProtection\":true,\"associatedRoles\":[],\"httpEndpointEnabled\":false,\"maxAllocatedStorage\":1000,\"tagList\":[],\"customerOwnedIpEnabled\":false,\"networkType\":\"IPV4\",\"backupTarget\":\"region\"}"
},
"response_elements": {
"pendingModifiedValues": {
"masterUserPassword": "****"
}
},
"user_identity": {
"accessKeyId": "ASI00000000000000000",
"accountId": "111111111111",
"arn": "arn:aws:iam::111111111111:root",
"principalId": "111111111111",
"type": "Root"
}
}
},
"cloud": {
"account": {
"id": "111111111111"
},
"provider": "aws",
"region": "eu-west-3",
"service": {
"name": "cloudtrail"
}
},
"user": {
"id": "111111111111"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Other",
"original": "AWS Internal",
"os": {
"name": "Other"
}
}
}
{
"message": "{\"awsRegion\":\"eu-west-3\",\"eventID\":\"bcf6f457-76bc-4e8c-8a7b-8a2451481675\",\"eventName\":\"AssumeRole\",\"eventSource\":\"sts.amazonaws.com\",\"eventTime\":\"2020-08-12T12:03:12Z\",\"eventType\":\"AwsApiCall\",\"eventVersion\":\"1.05\",\"recipientAccountId\":\"1111111111\",\"requestID\":\"34c3d58a-83f5-42cc-9e4d-1beeb85f809c\",\"requestParameters\":{\"roleArn\":\"arn:aws:iam::1111111111:role/user\",\"roleSessionName\":\"session-name\"},\"resources\":[{\"ARN\":\"arn:aws:iam::1111111111:role/user\",\"accountId\":\"1111111111\",\"type\":\"AWS::IAM::Role\"}],\"responseElements\":{\"credentials\":{\"accessKeyId\":\"ASIA11111111111111\",\"expiration\":\"Aug 13, 2020, 12:03:12 AM\",\"sessionToken\":\"11111111111111111111111111111111111111111\"}},\"sharedEventID\":\"e0b224e9-a818-452c-87e3-a1d4078bb102\",\"sourceIPAddress\":\"lambda.amazonaws.com\",\"userAgent\":\"lambda.amazonaws.com\",\"userIdentity\":{\"invokedBy\":\"lambda.amazonaws.com\",\"type\":\"AWSService\"}}",
"event": {
"action": "AssumeRole",
"category": [
"network"
],
"outcome": "success",
"provider": "sts.amazonaws.com",
"type": [
"access"
]
},
"@timestamp": "2020-08-12T12:03:12Z",
"action": {
"name": "AssumeRole",
"outcome": "success",
"properties": {
"recipientAccountId": "1111111111",
"resources": [
{
"ARN": "arn:aws:iam::1111111111:role/user"
}
],
"userIdentity": {
"invokedBy": "lambda.amazonaws.com",
"type": "AWSService"
}
},
"target": "network-traffic",
"type": "AwsApiCall"
},
"aws": {
"cloudtrail": {
"flattened": {
"request_parameters": "{\"roleArn\":\"arn:aws:iam::1111111111:role/user\",\"roleSessionName\":\"session-name\"}",
"response_elements": "{\"credentials\":{\"accessKeyId\":\"ASIA11111111111111\",\"expiration\":\"Aug 13, 2020, 12:03:12 AM\",\"sessionToken\":\"11111111111111111111111111111111111111111\"}}"
},
"user_identity": {
"type": "AWSService"
}
}
},
"cloud": {
"provider": "aws",
"region": "eu-west-3",
"service": {
"name": "cloudtrail"
}
},
"related": {
"hosts": [
"lambda.amazonaws.com"
]
},
"source": {
"address": "lambda.amazonaws.com",
"domain": "lambda.amazonaws.com",
"registered_domain": "amazonaws.com",
"subdomain": "lambda",
"top_level_domain": "com"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Other",
"original": "lambda.amazonaws.com",
"os": {
"name": "Other"
}
}
}
{
"message": "{\"additionalEventData\":{\"LoginTo\":\"https://console.aws.amazon.com/billing/home?region=eu-west-3&state=hashArgs%23%2F&isauthcode=true\",\"MFAUsed\":\"No\",\"MobileVersion\":\"No\"},\"awsRegion\":\"us-east-1\",\"eventID\":\"9d4ca355-a7d3-4422-96ae-dbe2c3431609\",\"eventName\":\"ConsoleLogin\",\"eventSource\":\"signin.amazonaws.com\",\"eventTime\":\"2020-08-19T15:33:43Z\",\"eventType\":\"AwsConsoleSignIn\",\"eventVersion\":\"1.05\",\"recipientAccountId\":\"1111111111\",\"requestParameters\":null,\"responseElements\":{\"ConsoleLogin\":\"Success\"},\"sourceIPAddress\":\"1.2.3.4\",\"userAgent\":\"Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0\",\"userIdentity\":{\"accessKeyId\":\"\",\"accountId\":\"1111111111\",\"arn\":\"arn:aws:iam::1111111111:root\",\"principalId\":\"1111111111\",\"type\":\"Root\"}}",
"event": {
"action": "ConsoleLogin",
"category": [
"authentication"
],
"outcome": "success",
"provider": "signin.amazonaws.com",
"type": [
"allowed"
]
},
"@timestamp": "2020-08-19T15:33:43Z",
"action": {
"name": "ConsoleLogin",
"outcome": "success",
"properties": {
"recipientAccountId": "1111111111",
"userIdentity": {
"accountId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"principalId": "1111111111",
"type": "Root"
}
},
"target": "network-traffic",
"type": "AwsConsoleSignIn"
},
"aws": {
"cloudtrail": {
"flattened": {
"response_elements": "{\"ConsoleLogin\":\"Success\"}"
},
"user_identity": {
"accountId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"principalId": "1111111111",
"type": "Root"
}
}
},
"cloud": {
"account": {
"id": "1111111111"
},
"provider": "aws",
"region": "us-east-1",
"service": {
"name": "cloudtrail"
}
},
"related": {
"ip": [
"1.2.3.4"
]
},
"source": {
"address": "1.2.3.4",
"ip": "1.2.3.4"
},
"user": {
"id": "1111111111"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Firefox",
"original": "Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0",
"os": {
"name": "Linux"
},
"version": "68.0"
}
}
{
"message": "{\"awsRegion\":\"eu-west-3\",\"eventID\":\"bcf6f457-76bc-4e8c-8a7b-8a2451481675\",\"eventName\":\"AssumeRole\",\"eventSource\":\"sts.amazonaws.com\",\"eventTime\":\"2020-08-12T12:03:12Z\",\"eventType\":\"AwsApiCall\",\"eventVersion\":\"1.05\",\"recipientAccountId\":\"1111111111\",\"requestID\":\"34c3d58a-83f5-42cc-9e4d-1beeb85f809c\",\"requestParameters\":{\"roleArn\":\"arn:aws:iam::1111111111:role/user\",\"roleSessionName\":\"session-name\"},\"resources\":[{\"ARN\":\"arn:aws:iam::1111111111:role/user\",\"accountId\":\"1111111111\",\"type\":\"AWS::IAM::Role\"}],\"responseElements\":{\"credentials\":{\"accessKeyId\":\"ASIA11111111111111\",\"expiration\":\"Aug 13, 2020, 12:03:12 AM\",\"sessionToken\":\"1111111111111111111111111111111111111111111111111111111111111111111111111\"}},\"sharedEventID\":\"e0b224e9-a818-452c-87e3-a1d4078bb102\",\"sourceIPAddress\":\"lambda.amazonaws.com\",\"userAgent\":\"lambda.amazonaws.com\",\"userIdentity\":{\"invokedBy\":\"lambda.amazonaws.com\",\"type\":\"AWSService\"}}",
"event": {
"action": "AssumeRole",
"category": [
"network"
],
"outcome": "success",
"provider": "sts.amazonaws.com",
"type": [
"access"
]
},
"@timestamp": "2020-08-12T12:03:12Z",
"action": {
"name": "AssumeRole",
"outcome": "success",
"properties": {
"recipientAccountId": "1111111111",
"resources": [
{
"ARN": "arn:aws:iam::1111111111:role/user"
}
],
"userIdentity": {
"invokedBy": "lambda.amazonaws.com",
"type": "AWSService"
}
},
"target": "network-traffic",
"type": "AwsApiCall"
},
"aws": {
"cloudtrail": {
"flattened": {
"request_parameters": "{\"roleArn\":\"arn:aws:iam::1111111111:role/user\",\"roleSessionName\":\"session-name\"}",
"response_elements": "{\"credentials\":{\"accessKeyId\":\"ASIA11111111111111\",\"expiration\":\"Aug 13, 2020, 12:03:12 AM\",\"sessionToken\":\"1111111111111111111111111111111111111111111111111111111111111111111111111\"}}"
},
"user_identity": {
"type": "AWSService"
}
}
},
"cloud": {
"provider": "aws",
"region": "eu-west-3",
"service": {
"name": "cloudtrail"
}
},
"related": {
"hosts": [
"lambda.amazonaws.com"
]
},
"source": {
"address": "lambda.amazonaws.com",
"domain": "lambda.amazonaws.com",
"registered_domain": "amazonaws.com",
"subdomain": "lambda",
"top_level_domain": "com"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Other",
"original": "lambda.amazonaws.com",
"os": {
"name": "Other"
}
}
}
{
"message": "{\"eventVersion\":\"1.09\",\"userIdentity\":{\"accessKeyId\":\"ASIA1111111111111\",\"accountId\":\"1111111111\",\"arn\":\"arn:aws:iam::1111111111:root\",\"principalId\":\"1111111111\",\"sessionContext\":{\"attributes\":{\"creationDate\":\"2020-08-12T07:04:40Z\",\"mfaAuthenticated\":\"false\"},\"sessionIssuer\":{},\"webIdFederationData\":{}},\"type\":\"Root\"},\"eventTime\":\"2025-07-25T04:25:16Z\",\"eventSource\":\"connect.amazonaws.com\",\"eventName\":\"ListRealtimeContactAnalysisSegmentsV2\",\"awsRegion\":\"eu-west-3\",\"sourceIPAddress\":\"connect.amazonaws.com\",\"userAgent\":\"connect.amazonaws.com\",\"requestParameters\":{\"InstanceId\":\"arn%3Aaws%3Aconnect%3Aeu-west-3%3A111111111111%3Ainstance%2F1d9a8bf6-5051-477e-b1c2-e5834a4a34b5\",\"SegmentTypes\":[\"Transcript\",\"Issues\",\"Event\",\"Attachments\",\"Categories\"],\"ContactId\":\"1d3e6813-0fa5-487e-9c48-0d93abb06241\",\"OutputType\":\"Raw\"},\"responseElements\":{\"Status\":\"COMPLETED\",\"Segments\":[{\"Transcript\":{\"Id\":\"cfa1f07b-41c9-433c-a913-3a64987038a1\",\"ParticipantId\":\"8aaadd53-1a04-4f37-986d-690bca5b0a4a\",\"ParticipantRole\":\"CUSTOMER\",\"DisplayName\":\"JDOE\",\"ContentType\":\"text/plain\",\"Time\":{\"AbsoluteTime\":\"2025-07-25T04:18:43.097Z\"},\"Sentiment\":\"NEUTRAL\",\"Content\":\"\uc548\ub155\ud558\uc138\uc694 \uace0\uac1d\ub2d8,\\n\\n\ud83e\udd16 \ubcf8 \ucc44\ub110\uc740 \ucc57\ubd07\uc744 \ud1b5\ud574 \uc790\ub3d9\uc73c\ub85c \uc751\ub2f5\ub4dc\ub9ac\uace0 \uc788\uc2b5\ub2c8\ub2e4.\"}}],\"Channel\":\"CHAT\"},\"requestID\":\"3e3d2004-23a7-4856-a680-af60f7a52b07\",\"eventID\":\"18312058-5aae-41a9-9a72-9c47a50ece24\",\"readOnly\":false,\"eventType\":\"AwsApiCall\",\"managementEvent\":true,\"recipientAccountId\":\"111111111111\",\"eventCategory\":\"Management\"}\n",
"event": {
"action": "ListRealtimeContactAnalysisSegmentsV2",
"category": [
"network"
],
"outcome": "success",
"provider": "connect.amazonaws.com",
"type": [
"access"
]
},
"@timestamp": "2025-07-25T04:25:16Z",
"action": {
"name": "ListRealtimeContactAnalysisSegmentsV2",
"outcome": "success",
"properties": {
"recipientAccountId": "111111111111",
"userIdentity": {
"accountId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"principalId": "1111111111",
"sessionContext": {
"attributes": {
"mfaAuthenticated": "false"
}
},
"type": "Root"
}
},
"target": "network-traffic",
"type": "AwsApiCall"
},
"aws": {
"cloudtrail": {
"flattened": {
"request_parameters": "{\"ContactId\":\"1d3e6813-0fa5-487e-9c48-0d93abb06241\",\"InstanceId\":\"arn%3Aaws%3Aconnect%3Aeu-west-3%3A111111111111%3Ainstance%2F1d9a8bf6-5051-477e-b1c2-e5834a4a34b5\",\"OutputType\":\"Raw\",\"SegmentTypes\":[\"Transcript\",\"Issues\",\"Event\",\"Attachments\",\"Categories\"]}",
"response_elements": "{\"Channel\":\"CHAT\",\"Segments\":[{\"Transcript\":{\"Content\":\"\uc548\ub155\ud558\uc138\uc694 \uace0\uac1d\ub2d8,\\n\\n\ud83e\udd16 \ubcf8 \ucc44\ub110\uc740 \ucc57\ubd07\uc744 \ud1b5\ud574 \uc790\ub3d9\uc73c\ub85c \uc751\ub2f5\ub4dc\ub9ac\uace0 \uc788\uc2b5\ub2c8\ub2e4.\",\"ContentType\":\"text/plain\",\"DisplayName\":\"JDOE\",\"Id\":\"cfa1f07b-41c9-433c-a913-3a64987038a1\",\"ParticipantId\":\"8aaadd53-1a04-4f37-986d-690bca5b0a4a\",\"ParticipantRole\":\"CUSTOMER\",\"Sentiment\":\"NEUTRAL\",\"Time\":{\"AbsoluteTime\":\"2025-07-25T04:18:43.097Z\"}}}],\"Status\":\"COMPLETED\"}"
},
"user_identity": {
"accessKeyId": "ASIA1111111111111",
"accountId": "1111111111",
"arn": "arn:aws:iam::1111111111:root",
"principalId": "1111111111",
"type": "Root"
}
}
},
"cloud": {
"account": {
"id": "1111111111"
},
"provider": "aws",
"region": "eu-west-3",
"service": {
"name": "cloudtrail"
}
},
"related": {
"hosts": [
"connect.amazonaws.com"
]
},
"source": {
"address": "connect.amazonaws.com",
"domain": "connect.amazonaws.com",
"registered_domain": "amazonaws.com",
"subdomain": "connect",
"top_level_domain": "com"
},
"user": {
"id": "1111111111"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Other",
"original": "connect.amazonaws.com",
"os": {
"name": "Other"
}
}
}
{
"message": "{\"eventVersion\":\"1.08\",\"eventTime\":\"2022-09-05T07:45:00Z\",\"awsRegion\":\"eu-west-3\",\"eventID\":\"7a9130fc-ca15-49d9-b4aa-685f7a0c182a\",\"eventType\":\"AwsCloudTrailInsight\",\"recipientAccountId\":\"1111111111\",\"sharedEventID\":\"0a771801-c0cc-406d-a080-219de884f089\",\"insightDetails\":{\"state\":\"End\",\"eventSource\":\"s3.amazonaws.com\",\"eventName\":\"GetBucketPolicy\",\"insightType\":\"ApiErrorRateInsight\",\"errorCode\":\"NoSuchBucketPolicy\",\"insightContext\":{\"statistics\":{\"baseline\":{\"average\":0.0021817492},\"insight\":{\"average\":1.3333333333},\"insightDuration\":3,\"baselineDuration\":10542},\"attributions\":[{\"attribute\":\"userIdentityArn\",\"insight\":[{\"value\":\"arn:aws:iam::1111111111:root\",\"average\":1.3333333333}],\"baseline\":[{\"value\":\"arn:aws:iam::1111111111:root\",\"average\":0.0020868905},{\"value\":\"arn:aws:sts::1111111111:assumed-role/AWSServiceRoleForConfig/AWSConfig-Describe\",\"average\":9.48587e-05}]},{\"attribute\":\"userAgent\",\"insight\":[{\"value\":\"[S3Console/0.4, aws-internal/3 aws-sdk-java/1.11.1030 Linux/5.4.204-124.362.amzn2int.x86_64 OpenJDK_64-Bit_Server_VM/25.302-b08 java/1.8.0_302 vendor/Oracle_Corporation cfg/retry-mode/standard]\",\"average\":0.6666666667},{\"value\":\"[S3Console/0.4, aws-internal/3 aws-sdk-java/1.11.1030 Linux/5.4.207-126.363.amzn2int.x86_64 OpenJDK_64-Bit_Server_VM/25.302-b08 java/1.8.0_302 vendor/Oracle_Corporation cfg/retry-mode/standard]\",\"average\":0.6666666667}],\"baseline\":[{\"value\":\"[S3Console/0.4, aws-internal/3 aws-sdk-java/1.11.1030 Linux/5.4.204-124.362.amzn2int.x86_64 OpenJDK_64-Bit_Server_VM/25.302-b08 java/1.8.0_302 vendor/Oracle_Corporation cfg/retry-mode/standard]\",\"average\":0.0010434453},{\"value\":\"[S3Console/0.4, aws-internal/3 aws-sdk-java/1.11.1030 Linux/5.4.207-126.363.amzn2int.x86_64 OpenJDK_64-Bit_Server_VM/25.302-b08 java/1.8.0_302 vendor/Oracle_Corporation cfg/retry-mode/standard]\",\"average\":0.0009485866},{\"value\":\"AWS Internal\",\"average\":0.0001897173}]}]}},\"eventCategory\":\"Insight\"}\n",
"event": {
"action": "GetBucketPolicy",
"category": [
"network"
],
"code": "NoSuchBucketPolicy",
"outcome": "success",
"provider": "s3.amazonaws.com",
"type": [
"access"
]
},
"@timestamp": "2022-09-05T07:45:00Z",
"action": {
"outcome": "success",
"properties": {
"recipientAccountId": "1111111111"
},
"target": "network-traffic",
"type": "AwsCloudTrailInsight"
},
"cloud": {
"provider": "aws",
"region": "eu-west-3",
"service": {
"name": "cloudtrail"
}
}
}
{
"message": "{\"eventVersion\":\"1.08\",\"userIdentity\":{\"type\":\"AssumedRole\",\"principalId\":\"AR0000000000000000:1111111111111111111111111\",\"arn\":\"arn:aws:sts::1111111111:assumed-role/role/1111111111111111111111111\",\"accountId\":\"1111111111\",\"accessKeyId\":\"AS000000000000000000\",\"sessionContext\":{\"sessionIssuer\":{\"type\":\"Role\",\"principalId\":\"AR0000000000000000\",\"arn\":\"arn:aws:iam::1111111111:role/service-role/username\",\"accountId\":\"1111111111\",\"userName\":\"username\"},\"webIdFederationData\":{},\"attributes\":{\"creationDate\":\"2022-09-09T07:45:14Z\",\"mfaAuthenticated\":\"false\"}}},\"eventTime\":\"2022-09-09T09:17:32Z\",\"eventSource\":\"elasticfilesystem.amazonaws.com\",\"eventName\":\"NewClientConnection\",\"awsRegion\":\"eu-central-1\",\"sourceIPAddress\":\"AWS Internal\",\"userAgent\":\"elasticfilesystem\",\"requestParameters\":null,\"responseElements\":null,\"eventID\":\"6ff7e265-b0b9-42c0-b4b5-ad140a7f1baa\",\"readOnly\":true,\"resources\":[{\"accountId\":\"1111111111\",\"type\":\"AWS::EFS::FileSystem\",\"ARN\":\"arn:aws:elasticfilesystem:eu-central-1:1111111111:file-system/fs-00000000\"},{\"accountId\":\"1111111111\",\"type\":\"AWS::EFS::AccessPoint\",\"ARN\":\"arn:aws:elasticfilesystem:eu-central-1:1111111111:access-point/fsap-00000000000000000\"}],\"eventType\":\"AwsServiceEvent\",\"managementEvent\":true,\"recipientAccountId\":\"1111111111\",\"serviceEventDetails\":{\"permissions\":{\"ClientRootAccess\":false,\"ClientMount\":true,\"ClientWrite\":true},\"sourceIpAddress\":\"1.2.3.4\"},\"eventCategory\":\"Management\"}\n",
"event": {
"action": "NewClientConnection",
"category": [
"network"
],
"outcome": "success",
"provider": "elasticfilesystem.amazonaws.com",
"type": [
"access"
]
},
"@timestamp": "2022-09-09T09:17:32Z",
"action": {
"name": "NewClientConnection",
"outcome": "success",
"properties": {
"recipientAccountId": "1111111111",
"resources": [
{
"ARN": "arn:aws:elasticfilesystem:eu-central-1:1111111111:file-system/fs-00000000"
},
{
"ARN": "arn:aws:elasticfilesystem:eu-central-1:1111111111:access-point/fsap-00000000000000000"
}
],
"userIdentity": {
"accountId": "1111111111",
"arn": "arn:aws:sts::1111111111:assumed-role/role/1111111111111111111111111",
"principalId": "AR0000000000000000:1111111111111111111111111",
"sessionContext": {
"attributes": {
"mfaAuthenticated": "false"
},
"sessionIssuer": {
"arn": "arn:aws:iam::1111111111:role/service-role/username",
"type": "Role",
"userName": "username"
}
},
"type": "AssumedRole"
}
},
"target": "network-traffic",
"type": "AwsServiceEvent"
},
"aws": {
"cloudtrail": {
"user_identity": {
"accessKeyId": "AS000000000000000000",
"accountId": "1111111111",
"arn": "arn:aws:sts::1111111111:assumed-role/role/1111111111111111111111111",
"principalId": "AR0000000000000000:1111111111111111111111111",
"sessionContext": {
"sessionIssuer": {
"arn": "arn:aws:iam::1111111111:role/service-role/username",
"userName": "username"
}
},
"type": "AssumedRole"
}
}
},
"cloud": {
"account": {
"id": "1111111111"
},
"provider": "aws",
"region": "eu-central-1",
"service": {
"name": "cloudtrail"
}
},
"user": {
"id": "1111111111"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Other",
"original": "elasticfilesystem",
"os": {
"name": "Other"
}
}
}
{
"message": "{\"eventVersion\":\"1.08\",\"userIdentity\":{\"type\":\"AssumedRole\",\"principalId\":\"A00000000000000000000:user@example.org\",\"arn\":\"arn:aws:sts::111111111:assumed-role/role/user@example.org\",\"accountId\":\"111111111\"},\"eventTime\":\"2022-09-08T15:01:59Z\",\"eventSource\":\"signin.amazonaws.com\",\"eventName\":\"ConsoleLogin\",\"awsRegion\":\"us-east-1\",\"sourceIPAddress\":\"1.2.3.4\",\"userAgent\":\"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.0.0 Safari/537.36\",\"requestParameters\":null,\"responseElements\":{\"ConsoleLogin\":\"Success\"},\"additionalEventData\":{\"LoginTo\":\"https://console.aws.amazon.com/console/home\",\"MobileVersion\":\"No\",\"MFAUsed\":\"No\",\"SamlProviderArn\":\"arn:aws:iam::111111111:saml-provider/provider-name\"},\"eventID\":\"e7dd6d97-2d3a-45dc-bb19-a3ea347091e3\",\"readOnly\":false,\"eventType\":\"AwsConsoleSignIn\",\"managementEvent\":true,\"recipientAccountId\":\"111111111\",\"eventCategory\":\"Management\",\"tlsDetails\":{\"tlsVersion\":\"TLSv1.2\",\"cipherSuite\":\"ECDHE-RSA-AES128-GCM-SHA256\",\"clientProvidedHostHeader\":\"signin.aws.amazon.com\"}}\n",
"event": {
"action": "ConsoleLogin",
"category": [
"authentication"
],
"outcome": "success",
"provider": "signin.amazonaws.com",
"type": [
"allowed"
]
},
"@timestamp": "2022-09-08T15:01:59Z",
"action": {
"name": "ConsoleLogin",
"outcome": "success",
"properties": {
"recipientAccountId": "111111111",
"userIdentity": {
"accountId": "111111111",
"arn": "arn:aws:sts::111111111:assumed-role/role/user@example.org",
"principalId": "A00000000000000000000:user@example.org",
"type": "AssumedRole"
}
},
"target": "network-traffic",
"type": "AwsConsoleSignIn"
},
"aws": {
"cloudtrail": {
"flattened": {
"response_elements": "{\"ConsoleLogin\":\"Success\"}"
},
"user_identity": {
"accountId": "111111111",
"arn": "arn:aws:sts::111111111:assumed-role/role/user@example.org",
"principalId": "A00000000000000000000:user@example.org",
"type": "AssumedRole"
}
}
},
"cloud": {
"account": {
"id": "111111111"
},
"provider": "aws",
"region": "us-east-1",
"service": {
"name": "cloudtrail"
}
},
"related": {
"ip": [
"1.2.3.4"
]
},
"source": {
"address": "1.2.3.4",
"ip": "1.2.3.4"
},
"tls": {
"cipher": "ECDHE-RSA-AES128-GCM-SHA256",
"version": "TLSv1.2"
},
"user": {
"id": "111111111"
},
"user_agent": {
"device": {
"name": "Other"
},
"name": "Chrome",
"original": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.0.0 Safari/537.36",
"os": {
"name": "Windows",
"version": "10"
},
"version": "105.0.0"
}
}
Extracted Fields
The following table lists the fields that are extracted, normalized under the ECS format, analyzed and indexed by the parser. It should be noted that infered fields are not listed.
| Name | Type | Description |
|---|---|---|
@timestamp |
date |
Date/time when the event originated. |
action.properties.errorCode |
keyword |
The code of the error associated to the request |
action.properties.errorMessage |
keyword |
The message of the error associated to the request |
action.properties.recipientAccountId |
keyword |
The account ID that received the event |
action.properties.requestParameters.userData |
keyword |
The userData parameters sent with the request |
action.properties.responseElements.publiclyAccessible |
boolean |
Whether the requested ressource was public |
action.target |
keyword |
The target of the action |
aws.cloudtrail.cluster_name |
keyword |
The name of the cluster |
aws.cloudtrail.flattened.request_parameters |
keyword |
The flattened version of the field requestParameters |
aws.cloudtrail.flattened.response_elements |
keyword |
The flattened version of the field responseElements |
aws.cloudtrail.response_elements.pendingModifiedValues.masterUserPassword |
keyword |
The new master password for the RDS instance |
aws.cloudtrail.response_elements.policy.arn |
keyword |
provides information about the queried policy arn |
aws.cloudtrail.response_elements.policy.policyId |
keyword |
provides information about the queried policyId |
aws.cloudtrail.response_elements.policy.policyName |
keyword |
provides information about the queried policyName |
aws.cloudtrail.response_elements.user.userName |
keyword |
The name of the user in the response |
cloud.account.id |
keyword |
The cloud account or organization id. |
cloud.instance.id |
keyword |
Instance ID of the host machine. |
cloud.provider |
keyword |
Name of the cloud provider. |
cloud.region |
keyword |
Region in which this host, resource, or service is located. |
cloud.service.name |
keyword |
The cloud service name. |
event.action |
keyword |
The action captured by the event. |
event.category |
keyword |
Event category. The second categorization field in the hierarchy. |
event.code |
keyword |
Identification code for this event. |
event.provider |
keyword |
Source of the event. |
event.reason |
keyword |
Reason why this event happened, according to the source |
event.type |
keyword |
Event type. The third categorization field in the hierarchy. |
source.address |
keyword |
Source network address. |
source.domain |
keyword |
The domain name of the source. |
source.ip |
ip |
IP address of the source. |
tls.cipher |
keyword |
String indicating the cipher used during the current connection. |
tls.version |
keyword |
Numeric part of the version parsed from the original string. |
user.id |
keyword |
Unique identifier of the user. |
user.name |
keyword |
Short name or login of the user. |
user_agent.original |
keyword |
Unparsed user_agent string. |
For more information on the Intake Format, please find the code of the Parser, Smart Descriptions, and Supported Events here.