Lacework Cloud Security
Overview
The Lacework Cloud Security provides continuous cloud security monitoring and automated threat detection, safeguarding cloud environments with real-time insights and compliance enforcement.
- Vendor: Lacework
- Supported environment: SaaS
- Detection based on: Alert, Telemetry
- Supported application or feature:
Prerequisites
To create API keys, you must have the account admin role or otherwise have write permissions for API keys in the Lacework Console.
Step-by-Step Configuration Procedure
Instructions on the 3rd Party Solution
Create Lacework Credentials
Create a service user
In the lacework console:
-
Go to
Settings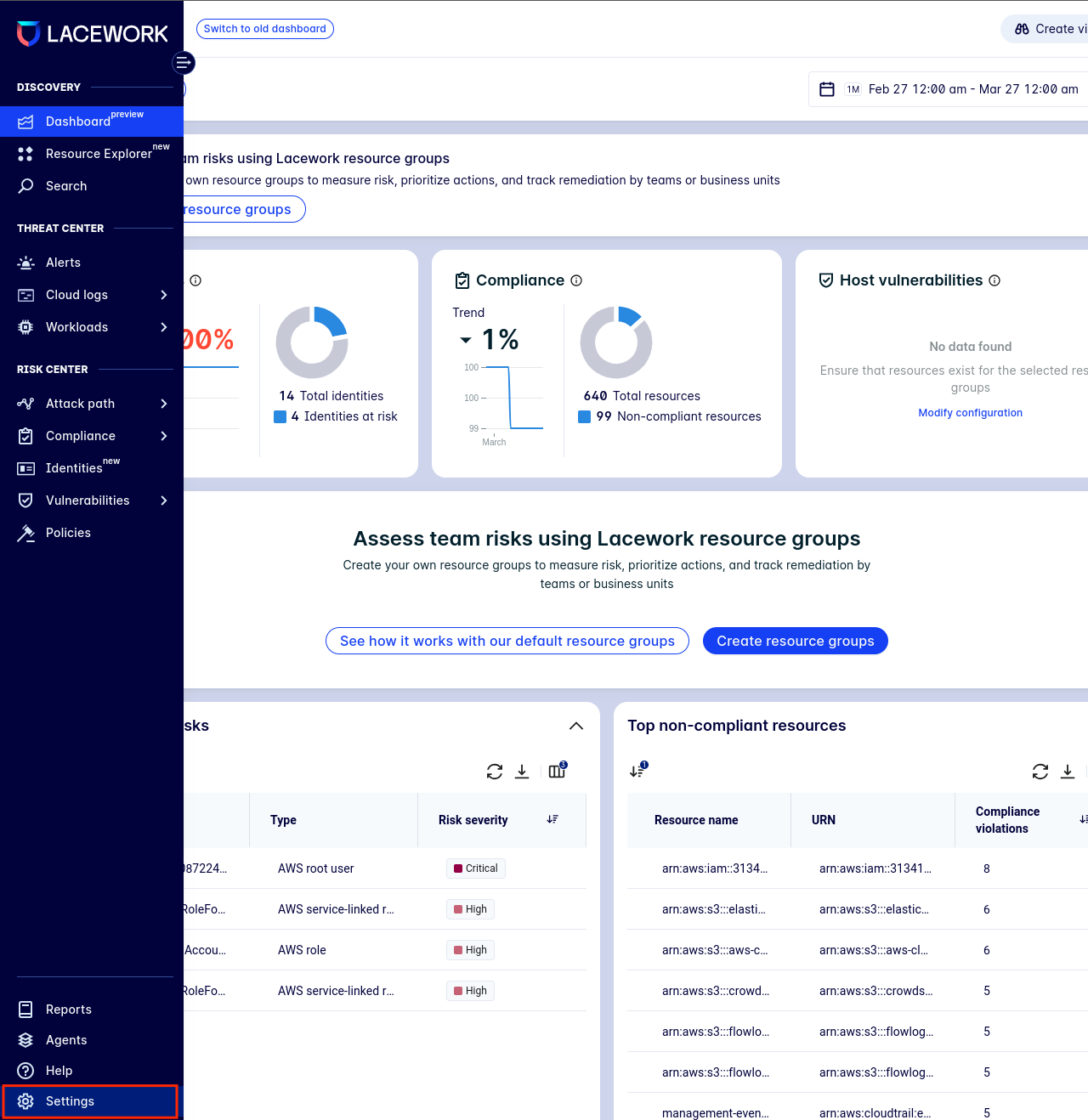
-
In the settings, go to
Access Control>Users>Account leveland click+ Add New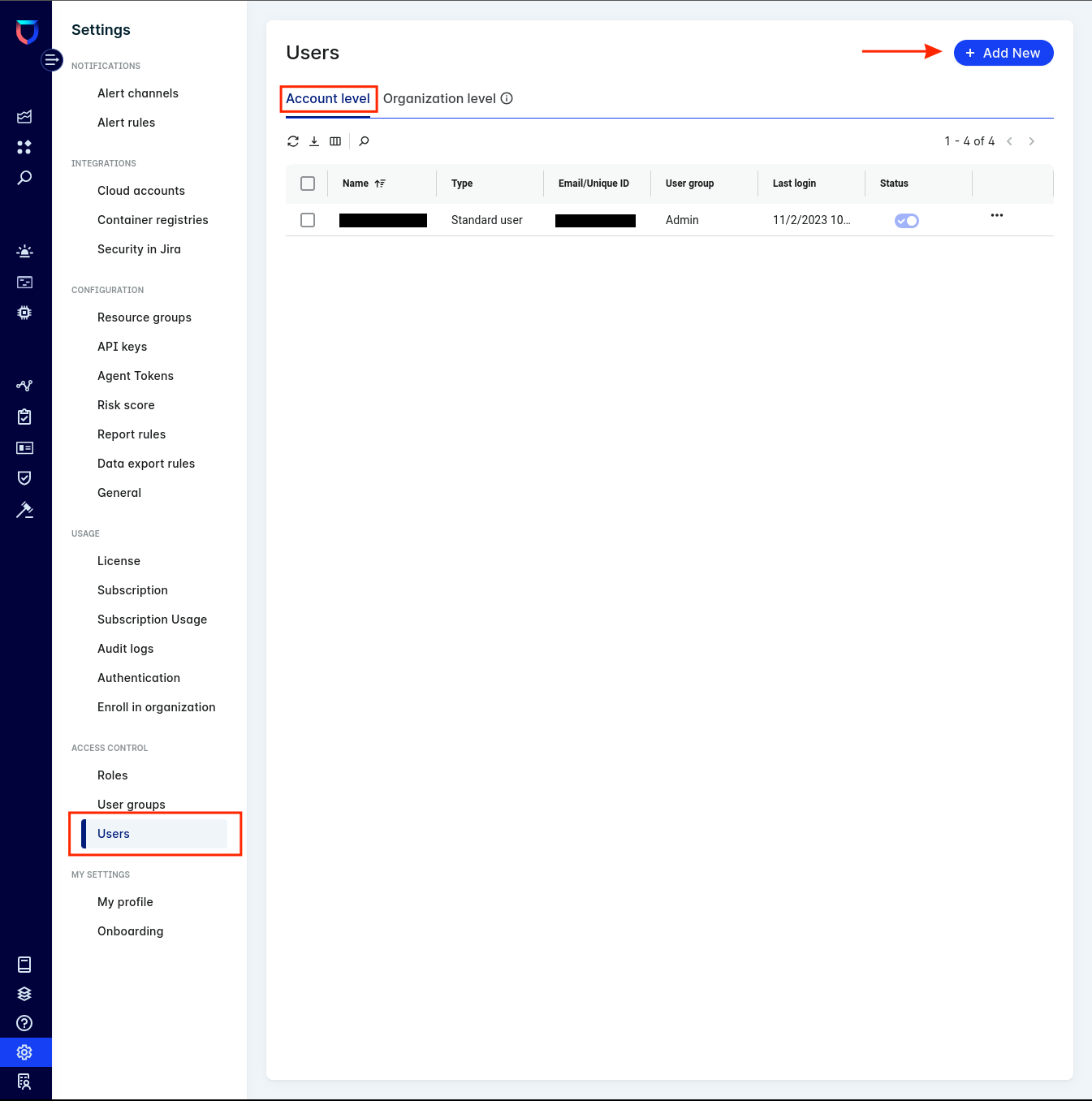
-
To create a service user:
- Select
Service useras user type - Give the user a name and an optional description
-
Click
Next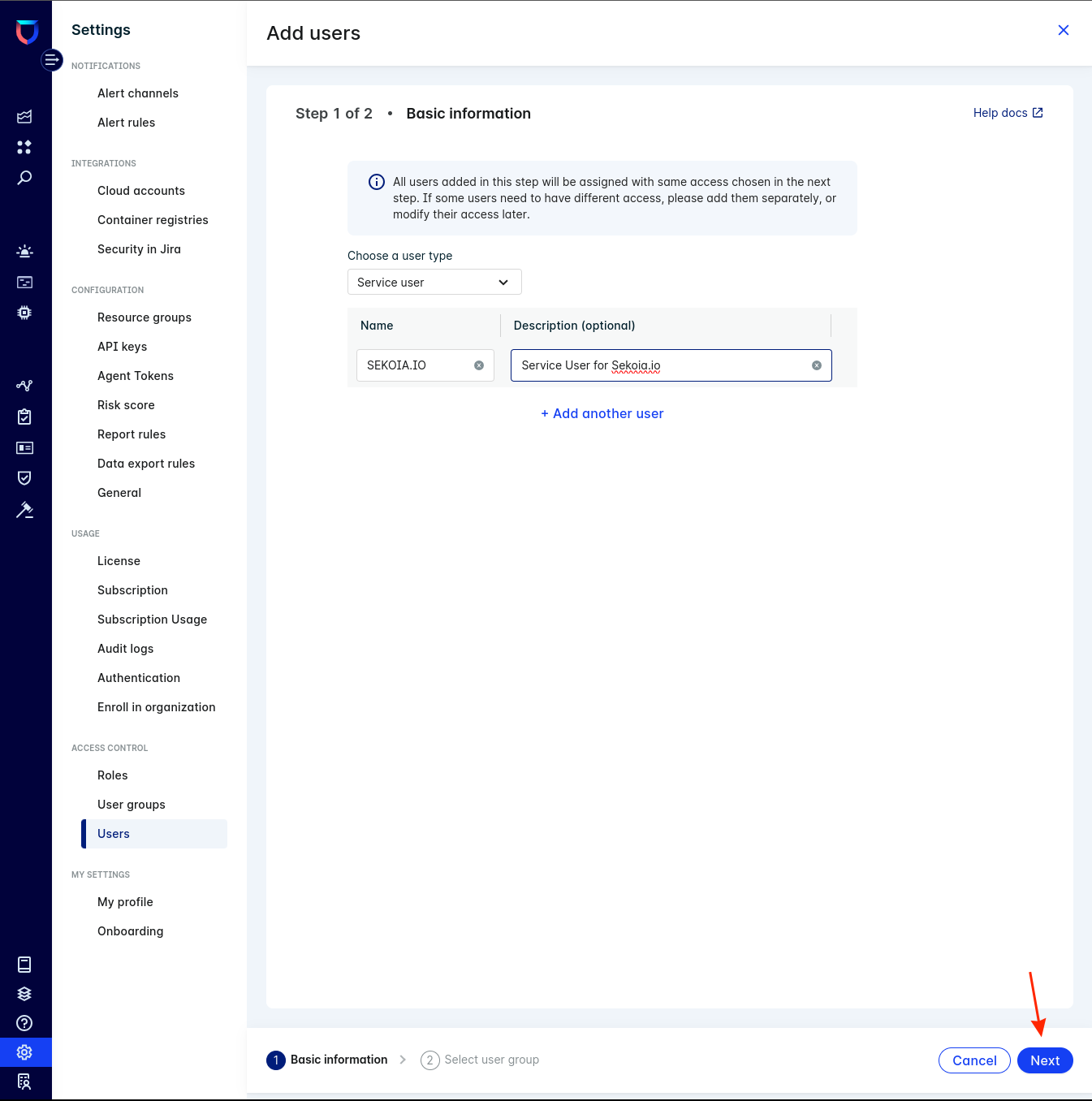
-
Select
Read-Only Useras user group -
Click
Save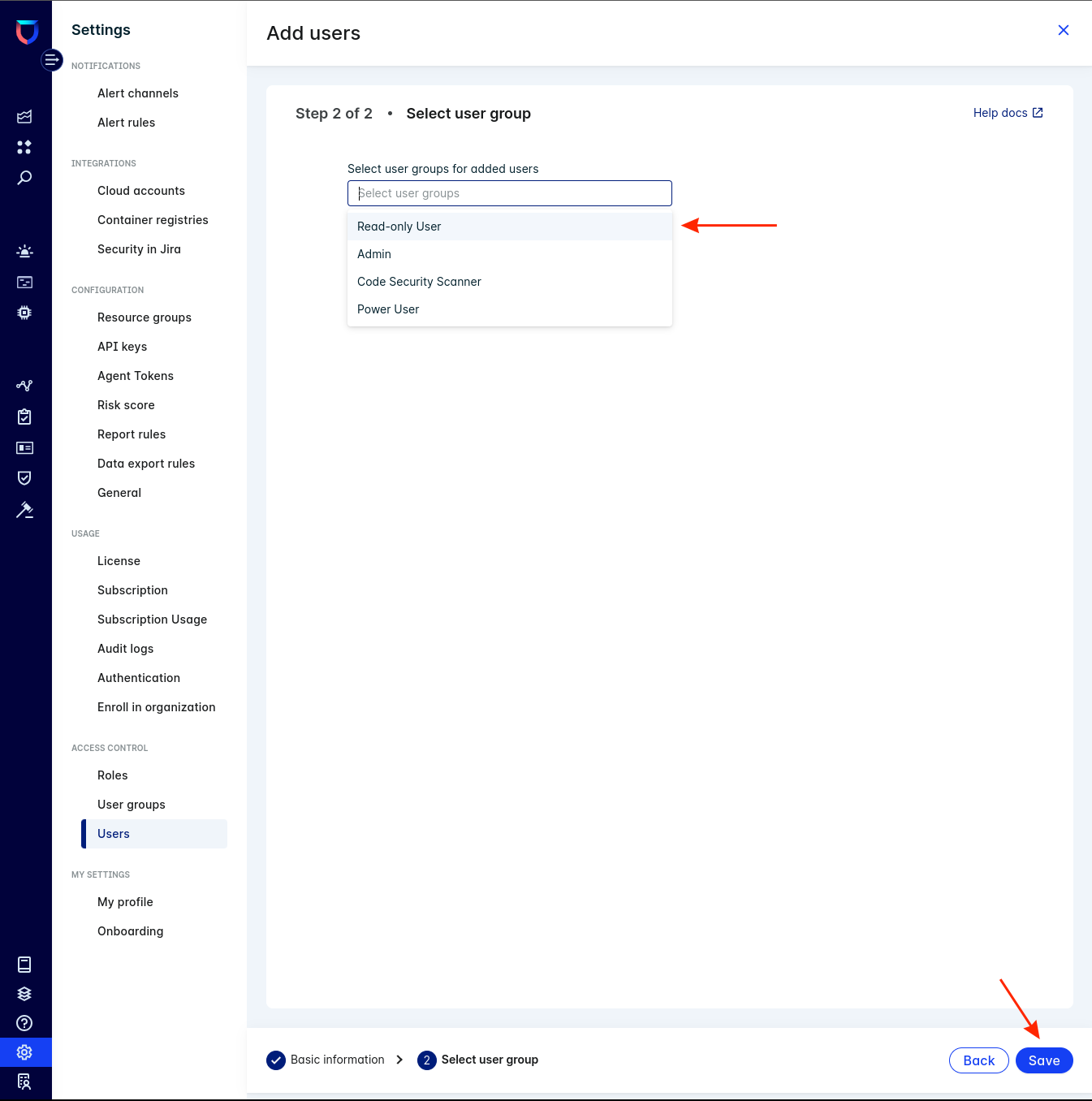
- Select
Create API keys
In the Lacework console:
-
In the
Settings, go toConfiguration>API keys>Service User API Keysand click+ Add New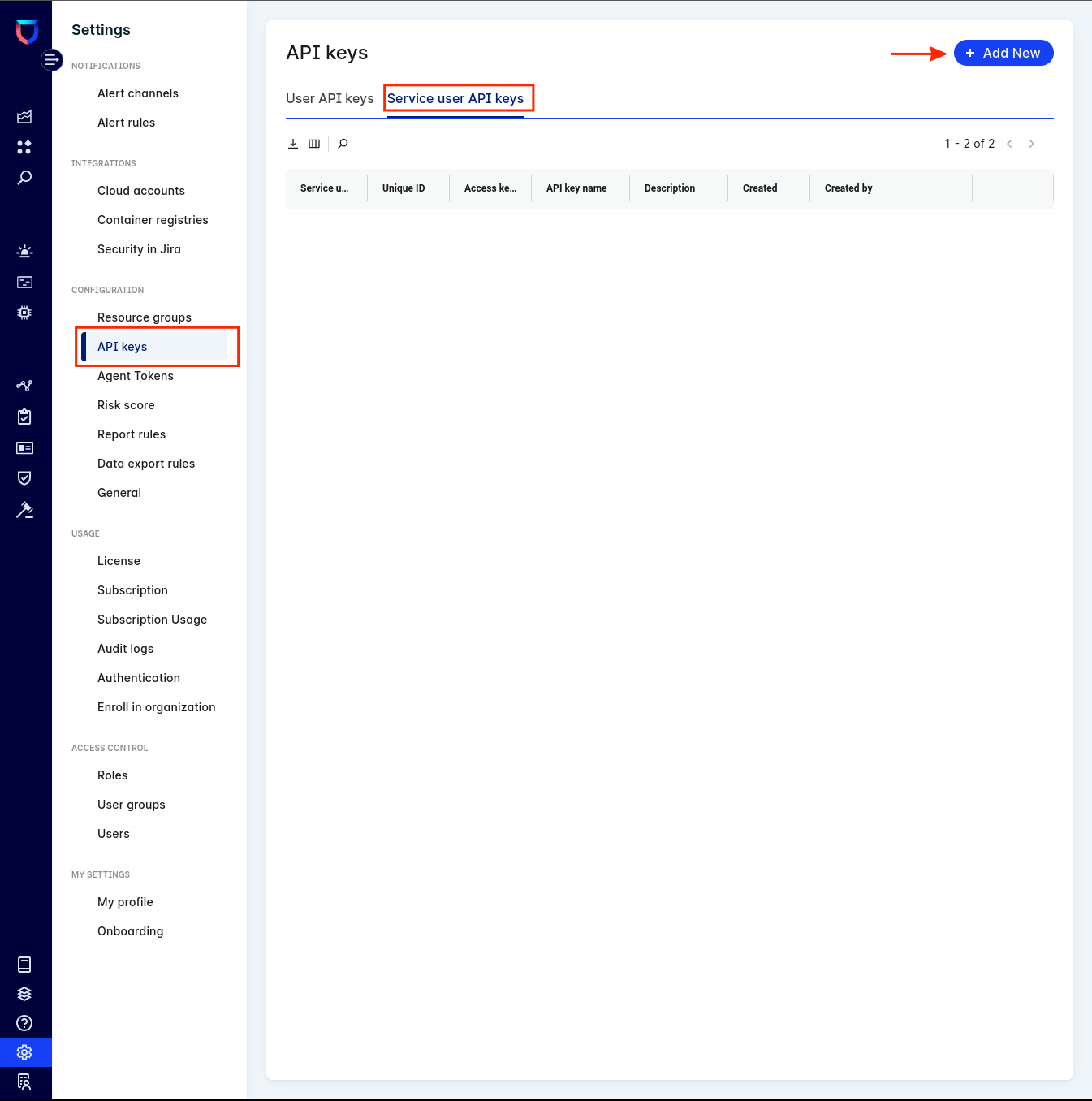
-
To create an API Key:
- Give the key a name and an optional description.
-
Click
Save.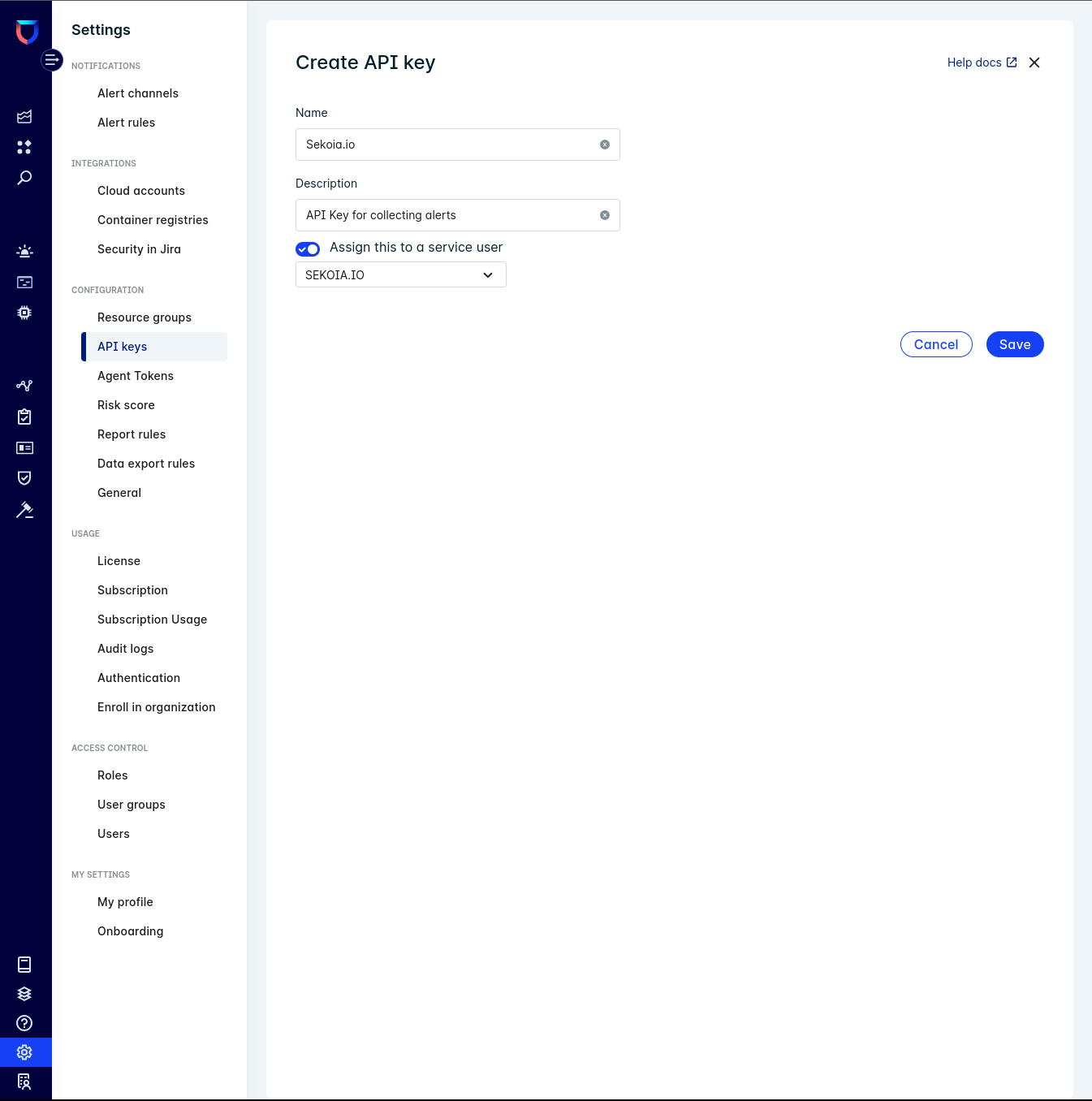
Download the generated API key file and open it in an editor to view and use the key ID and generated secret in your API requests. You can create up to 20 API keys.
Instruction on Sekoia
Create an intake
- Go to the intake page and create a new intake from the
Lacework Cloud Securityformat. - Set the intake account configuration with the account, the keyId and the secret of your API Key.
Raw Events Samples
In this section, you will find examples of raw logs as generated natively by the source. These examples are provided to help integrators understand the data format before ingestion into Sekoia.io. It is crucial for setting up the correct parsing stages and ensuring that all relevant information is captured.
{
"alertId": 813628,
"startTime": "2022-06-30T00:00:00.000Z",
"alertType": "CloudActivityLogIngestionFailed",
"severity": "High",
"endTime": "2022-06-30T01:00:00.000Z",
"lastUserUpdatedTime": "",
"status": "Open",
"alertName": "Clone of Cloud Activity log ingestion failure detected",
"alertInfo": {
"subject": "Clone of Cloud Activity log ingestion failure detected: `azure-al-india-dnd` (and `3` more) is failing for data ingestion into Lacework",
"description": "New integration failure detected for azure-al-india-dnd (and 3 more)",
"supportingFacts": [
{
"supportingFactText": "Container Escape",
"subElements": [
{
"supportingFactText": "Use of known container privilege escalation and exploit tools 6 time(s) on host(s) ip-172-18-0-240"
}
]
}
]
},
"entityMap": {
"API": "{object}",
"CT_User": "{object}",
"CT_RawTime": "{object}",
"Region": "{object}",
"Resource": "{object}",
"RulesTriggered": "{object}",
"SourceIpAddress": "{object}"
}
}
{
"alertId": 205,
"alertName": "Usage of Root Account",
"startTime": "2024-02-13T17:00:00.000Z",
"alertType": "UsageOfRootAccount",
"severity": "Info",
"internetExposure": "UnknownInternetExposure",
"reachability": "UnknownReachability",
"derivedFields": {
"category": "Policy",
"sub_category": "Cloud Activity",
"source": "AWS"
},
"endTime": "2024-02-13T18:00:00.000Z",
"lastUserUpdatedTime": "",
"status": "Open",
"alertInfo": {
"description": " For account: 0123456789 : Root account was successfully used 96 times by user 0123456789 ",
"subject": "Usage of Root Account: For account: 0123456789 : Root account was successfully used 96 times by user 0123456789 ",
"customerCount": 0,
"isExpectedLWBehavior": false
},
"policyId": "lacework-global-8",
"evolvingAlert": false,
"tagMetadata": []
}
{
"alertId": 206,
"alertName": "Unauthorized API Call",
"startTime": "2024-02-13T18:00:00.000Z",
"alertType": "UnauthorizedAPICall",
"severity": "Medium",
"internetExposure": "UnknownInternetExposure",
"reachability": "UnknownReachability",
"derivedFields": {
"category": "Policy",
"sub_category": "Cloud Activity",
"source": "AWS"
},
"endTime": "2024-02-13T19:00:00.000Z",
"lastUserUpdatedTime": "",
"status": "Open",
"alertInfo": {
"description": " For account: 0123456789 : Unauthorized API call was attempted 18 times by user AROAUR6F6MOZQBRKBX6RG:3e0ac0bf-fa18-4e70-8aa4-44debb525a10 ",
"subject": "Unauthorized API Call: For account: 0123456789 : Unauthorized API call was attempted 18 times by user AROAUR6F6MOZQBRKBX6RG:3e0ac0bf-fa18-4e70-8aa4-44debb525a10 ",
"customerCount": 0,
"isExpectedLWBehavior": false
},
"policyId": "lacework-global-29",
"evolvingAlert": false,
"tagMetadata": []
}
{
"alertId": 207,
"alertName": "Unauthorized API Call",
"startTime": "2024-02-13T19:00:00.000Z",
"alertType": "UnauthorizedAPICall",
"severity": "Low",
"internetExposure": "UnknownInternetExposure",
"reachability": "UnknownReachability",
"derivedFields": {
"category": "Policy",
"sub_category": "Cloud Activity",
"source": "AWS"
},
"endTime": "2024-02-13T20:00:00.000Z",
"lastUserUpdatedTime": "",
"status": "Open",
"alertInfo": {
"description": " For account: 0123456789 : Unauthorized API call was attempted 99 times by user AROAUR6F6MOZ7YRJNRFJB:LACEWORK-CFG-external ",
"subject": "Unauthorized API Call: For account: 0123456789 : Unauthorized API call was attempted 99 times by user AROAUR6F6MOZ7YRJNRFJB:LACEWORK-CFG-external ",
"customerCount": 0,
"isExpectedLWBehavior": false
},
"policyId": "lacework-global-29",
"evolvingAlert": false,
"tagMetadata": []
}
{
"alertId": 208,
"alertName": "Unauthorized API Call",
"startTime": "2024-02-14T03:00:00.000Z",
"alertType": "UnauthorizedAPICall",
"severity": "Medium",
"internetExposure": "UnknownInternetExposure",
"reachability": "UnknownReachability",
"derivedFields": {
"category": "Policy",
"sub_category": "Cloud Activity",
"source": "AWS"
},
"endTime": "2024-02-14T04:00:00.000Z",
"lastUserUpdatedTime": "",
"status": "Open",
"alertInfo": {
"description": " For account: 0123456789 : Unauthorized API call was attempted 18 times by user AROAUR6F6MOZQBRKBX6RG:a7913090-862e-4cfa-ad11-80508825167e ",
"subject": "Unauthorized API Call: For account: 0123456789 : Unauthorized API call was attempted 18 times by user AROAUR6F6MOZQBRKBX6RG:a7913090-862e-4cfa-ad11-80508825167e ",
"customerCount": 0,
"isExpectedLWBehavior": false
},
"policyId": "lacework-global-29",
"evolvingAlert": false,
"tagMetadata": []
}
{
"alertId": 209,
"alertName": "Usage of Root Account",
"startTime": "2024-02-14T10:00:00.000Z",
"alertType": "UsageOfRootAccount",
"severity": "Info",
"internetExposure": "UnknownInternetExposure",
"reachability": "UnknownReachability",
"derivedFields": {
"category": "Policy",
"sub_category": "Cloud Activity",
"source": "AWS"
},
"endTime": "2024-02-14T11:00:00.000Z",
"lastUserUpdatedTime": "",
"status": "Open",
"alertInfo": {
"description": " For account: 0123456789 : Root account was successfully used 83 times by user 0123456789 ",
"subject": "Usage of Root Account: For account: 0123456789 : Root account was successfully used 83 times by user 0123456789 ",
"customerCount": 0,
"isExpectedLWBehavior": false
},
"policyId": "lacework-global-8",
"evolvingAlert": false,
"tagMetadata": []
}
{
"alertId": 210,
"alertName": "Usage of Root Account",
"startTime": "2024-02-14T11:00:00.000Z",
"alertType": "UsageOfRootAccount",
"severity": "Info",
"internetExposure": "UnknownInternetExposure",
"reachability": "UnknownReachability",
"derivedFields": {
"category": "Policy",
"sub_category": "Cloud Activity",
"source": "AWS"
},
"endTime": "2024-02-14T12:00:00.000Z",
"lastUserUpdatedTime": "",
"status": "Open",
"alertInfo": {
"description": " For account: 0123456789 : Root account was successfully used 8 times by user 0123456789 ",
"subject": "Usage of Root Account: For account: 0123456789 : Root account was successfully used 8 times by user 0123456789 ",
"customerCount": 0,
"isExpectedLWBehavior": false
},
"policyId": "lacework-global-8",
"evolvingAlert": false,
"tagMetadata": []
}
{
"alertId": 202634,
"alertName": "New Grant Added to Key Management Service (KMS) Key",
"startTime": "2025-08-11T14:07:51.000Z",
"alertType": "New Grant Added to Key Management Service (KMS) Key",
"severity": "Info",
"derivedFields": {
"category": "Policy",
"sub_category": "Cloud Activity",
"source": "AWS"
},
"endTime": "2025-08-11T14:27:58.000Z",
"lastUserUpdatedTime": "",
"status": "Open",
"alertInfo": {
"description": " For account: 12345678 : new grant(s) added to a Customer Master Key by user JOHNDOE:1234 ",
"subject": "New Grant Added to Key Management Service (KMS) Key: For account: 12345678 : new grant(s) added to a Customer Master Key by user JOHNDOE:1234 ",
"customerCount": 0,
"isExpectedLWBehavior": false
},
"policyId": "lacework-global-19",
"evolvingAlert": true,
"tagMetadata": [],
"internetExposure": "UnknownInternetExposure",
"reachability": "UnknownReachability",
"report": "FALSE"
}
{
"alertId": 202467,
"alertName": "Virtual Private Cloud (VPC) Change",
"startTime": "2025-08-11T04:16:39.000Z",
"alertType": "Virtual Private Cloud (VPC) Change",
"severity": "Info",
"derivedFields": {
"category": "Policy",
"sub_category": "Cloud Activity",
"source": "AWS"
},
"endTime": "2025-08-11T04:19:25.000Z",
"lastUserUpdatedTime": "",
"status": "Open",
"alertInfo": {
"description": " For account: 123456789 : 5 new VPC(s) created, deleted or changed by user USER01:john.doe@domain.com ",
"subject": "Virtual Private Cloud (VPC) Change: For account: 123456789 : 5 new VPC(s) created, deleted or changed by user USER01:john.doe@domain.com ",
"customerCount": 0,
"isExpectedLWBehavior": false
},
"policyId": "lacework-global-1",
"evolvingAlert": false,
"tagMetadata": [],
"internetExposure": "UnknownInternetExposure",
"reachability": "UnknownReachability",
"report": "FALSE"
}
{
"alertId": 202655,
"alertName": "New AWS user",
"startTime": "2025-08-11T14:00:00.000Z",
"alertType": "NewAwsUser",
"severity": "Low",
"derivedFields": {
"category": "Anomaly",
"sub_category": "Cloud Activity",
"source": "AWS"
},
"endTime": "2025-08-11T15:00:00.000Z",
"lastUserUpdatedTime": "",
"status": "Open",
"alertInfo": {
"description": "For account: 12345678 : User AssumedRole/12345678:AWSServiceRoleForAmazonGuardDuty using Aws for the first time",
"subject": "New AWS user: For account: 12345678 : User AssumedRole/12345678:AWSServiceRoleForAmazonGuardDuty using Aws for the first time",
"customerCount": 0,
"isExpectedLWBehavior": false
},
"evolvingAlert": false,
"tagMetadata": [],
"internetExposure": "UnknownInternetExposure",
"reachability": "UnknownReachability",
"report": "FALSE"
}
{
"alertId": 233783,
"alertName": "AWS account accessed from a new geolocation",
"startTime": "2024-08-05T07:00:00.000Z",
"alertType": "LoginFromSourceUsingCalltype",
"severity": "Low",
"derivedFields": {
"category": "Anomaly",
"sub_category": "Cloud Activity",
"source": "AWS"
},
"endTime": "2024-08-05T08:00:00.000Z",
"lastUserUpdatedTime": "",
"status": "Open",
"alertInfo": {
"description": "For account: 123456789 (company) : Unknown/123456789:john.doe@company.com logged in from an IP address 1.2.3.4 in a new location Rennes,Bretagne,France using the AWS event type AwsServiceEvent . This is the first time this AWS account has been accessed from this location.",
"subject": "AWS account accessed from a new geolocation: For account: 123456789 (company) : Unknown/123456789:john.doe@company.com logged in from an IP address 1.2.3.4 in a new location Rennes,Bretagne,France using the AWS event type AwsServiceEvent . This is the first time this AWS account has been accessed from this location.",
"customerCount": 0,
"isExpectedLWBehavior": false
},
"evolvingAlert": false,
"tagMetadata": [],
"internetExposure": "UnknownInternetExposure",
"reachability": "UnknownReachability"
}
{
"alertId": 233849,
"alertName": "GCP user logged in from new source",
"startTime": "2024-08-05T11:00:00.000Z",
"alertType": "GcpUserLoggedInFromSource",
"severity": "Low",
"derivedFields": {
"category": "Anomaly",
"sub_category": "Cloud Activity",
"source": "GCP"
},
"endTime": "2024-08-05T12:00:00.000Z",
"lastUserUpdatedTime": "",
"status": "Open",
"alertInfo": {
"description": " john.doe@company.com logged in from a new source Rennes,Bretagne,France for the first time ",
"subject": "GCP user logged in from new source: john.doe@company.com logged in from a new source Rennes,Bretagne,France for the first time ",
"customerCount": 0,
"isExpectedLWBehavior": false
},
"policyId": "203135697",
"evolvingAlert": false,
"tagMetadata": [],
"internetExposure": "UnknownInternetExposure",
"reachability": "UnknownReachability"
}
{
"alertId": 233782,
"alertName": "New GCP service",
"startTime": "2024-08-05T07:00:00.000Z",
"alertType": "NewGcpService",
"severity": "Medium",
"derivedFields": {
"category": "Anomaly",
"sub_category": "Cloud Activity",
"source": "GCP"
},
"endTime": "2024-08-05T08:00:00.000Z",
"lastUserUpdatedTime": "",
"status": "Open",
"alertInfo": {
"description": "For project: project-001 (test-projects) : A new service service.apis.com was used for the first time (by user john.doe@company.com)",
"subject": "New GCP service: For project: project-001 (test-projects) : A new service service.apis.com was used for the first time (by user john.doe@company.com)",
"customerCount": 0,
"isExpectedLWBehavior": false
},
"policyId": "203101916",
"evolvingAlert": false,
"tagMetadata": [],
"internetExposure": "UnknownInternetExposure",
"reachability": "UnknownReachability"
}
{
"alertId": 233726,
"alertName": "New GCP source",
"startTime": "2024-08-05T00:00:00.000Z",
"alertType": "NewGcpSource",
"severity": "Low",
"derivedFields": {
"category": "Anomaly",
"sub_category": "Cloud Activity",
"source": "GCP"
},
"endTime": "2024-08-05T01:00:00.000Z",
"lastUserUpdatedTime": "",
"status": "Open",
"alertInfo": {
"description": " A user (john.doe@company.com) logged in from a new source Rennes,Bretagne,France for the first time",
"subject": "New GCP source: A user (john.doe@company.com) logged in from a new source Rennes,Bretagne,France for the first time",
"customerCount": 0,
"isExpectedLWBehavior": false
},
"policyId": "203059776",
"evolvingAlert": false,
"tagMetadata": [],
"internetExposure": "UnknownInternetExposure",
"reachability": "UnknownReachability"
}
{
"alertId": 233825,
"alertName": "New GCP user",
"startTime": "2024-08-05T10:00:00.000Z",
"alertType": "NewGcpUser",
"severity": "Info",
"derivedFields": {
"category": "Anomaly",
"sub_category": "Cloud Activity",
"source": "GCP"
},
"endTime": "2024-08-05T11:00:00.000Z",
"lastUserUpdatedTime": "",
"status": "Open",
"alertInfo": {
"description": " User john.doe@company.com using GCP for the first time",
"subject": "New GCP user: User john.doe@company.com using GCP for the first time",
"customerCount": 0,
"isExpectedLWBehavior": false
},
"policyId": "203126334",
"evolvingAlert": false,
"tagMetadata": [],
"internetExposure": "UnknownInternetExposure",
"reachability": "UnknownReachability"
}
{
"alertId": 233808,
"alertName": "Security Group Change",
"startTime": "2024-08-05T09:00:00.000Z",
"alertType": "SecurityGroupChange",
"severity": "Info",
"derivedFields": {
"category": "Policy",
"sub_category": "Cloud Activity",
"source": "AWS"
},
"endTime": "2024-08-05T10:00:00.000Z",
"lastUserUpdatedTime": "",
"status": "Open",
"alertInfo": {
"description": " For account: 1234567890 (company) : SecurityGroup sg-012345 created/deleted/changed 5 times by user USER01:john.doe@company.com ",
"subject": "Security Group Change: For account: 1234567890 (company) : SecurityGroup sg-012345 created/deleted/changed 5 times by user USER01:john.doe@company.com ",
"customerCount": 0,
"isExpectedLWBehavior": false
},
"policyId": "lacework-global-2",
"evolvingAlert": false,
"tagMetadata": [],
"internetExposure": "UnknownInternetExposure",
"reachability": "UnknownReachability"
}
Detection section
The following section provides information for those who wish to learn more about the detection capabilities enabled by collecting this intake. It includes details about the built-in rule catalog, event categories, and ECS fields extracted from raw events. This is essential for users aiming to create custom detection rules, perform hunting activities, or pivot in the events page.
Related Built-in Rules
The following Sekoia.io built-in rules match the intake Lacework Cloud Security. This documentation is updated automatically and is based solely on the fields used by the intake which are checked against our rules. This means that some rules will be listed but might not be relevant with the intake.
SEKOIA.IO x Lacework Cloud Security on ATT&CK Navigator
Account Added To A Security Enabled Group
Detection in order to investigate who has added a specific Domain User in Domain Admins or Group Policy Creator Owners (Security event 4728)
- Effort: master
Account Removed From A Security Enabled Group
Detection in order to investigate who has removed a specific Domain User in Domain Admins or Group Policy Creator Owners (Security event 4729)
- Effort: master
Computer Account Deleted
Detects computer account deletion.
- Effort: master
Cryptomining
Detection of domain names potentially related to cryptomining activities.
- Effort: master
Domain Trust Created Or Removed
A trust was created or removed to a domain. An attacker could perform that in order to do lateral movement easily between domains or shutdown the ability of two domains to communicate.
- Effort: advanced
Dynamic DNS Contacted
Detect communication with dynamic dns domain. This kind of domain is often used by attackers. This rule can trigger false positive in non-controlled environment because dynamic dns is not always malicious.
- Effort: master
Exfiltration Domain
Detects traffic toward a domain flagged as a possible exfiltration vector.
- Effort: master
Lacework Cloud Security Critical Severity Alert
Detects when a critical alert severity is raised by Lacework. This severity level might indicates a suspicious change in configuration or policy violation.
- Effort: master
Lacework Cloud Security High Severity Alert
Detects when a high alert severity is raised by Lacework. This severity level might indicates a suspicious change in configuration or policy violation.
- Effort: master
Lacework Cloud Security Low Severity Alert
Detects when a low alert severity is raised by Lacework. This severity level might indicates a change in configuration that could be malicious or not.
- Effort: master
Lacework Cloud Security Medium Severity Alert
Detects when a medium alert severity is raised by Lacework. This severity level might indicates a suspicious activity such as new source from user connection.
- Effort: master
Password Change On Directory Service Restore Mode (DSRM) Account
The Directory Service Restore Mode (DSRM) account is a local administrator account on Domain Controllers. Attackers may change the password to gain persistence.
- Effort: intermediate
Possible Replay Attack
This event can be a sign of Kerberos replay attack or, among other things, network device configuration or routing problems.
- Effort: master
Remote Access Tool Domain
Detects traffic toward a domain flagged as a Remote Administration Tool (RAT).
- Effort: master
SEKOIA.IO Intelligence Feed
Detect threats based on indicators of compromise (IOCs) collected by SEKOIA's Threat and Detection Research team.
- Effort: elementary
Sekoia.io EICAR Detection
Detects observables in Sekoia.io CTI tagged as EICAR, which are fake samples meant to test detection.
- Effort: master
TOR Usage Generic Rule
Detects TOR usage globally, whether the IP is a destination or source. TOR is short for The Onion Router, and it gets its name from how it works. TOR intercepts the network traffic from one or more apps on user’s computer, usually the user web browser, and shuffles it through a number of randomly-chosen computers before passing it on to its destination. This disguises user location, and makes it harder for servers to pick him/her out on repeat visits, or to tie together separate visits to different sites, this making tracking and surveillance more difficult. Before a network packet starts its journey, user’s computer chooses a random list of relays and repeatedly encrypts the data in multiple layers, like an onion. Each relay knows only enough to strip off the outermost layer of encryption, before passing what’s left on to the next relay in the list.
- Effort: master
User Account Created
Detects user creation on windows servers, which shouldn't happen in an Active Directory environment. Apply this on your windows server logs and not on your DC logs. One default account defaultuser0 is excluded as only used during Windows set-up. This detection use Security Event ID 4720.
- Effort: master
User Account Deleted
Detects local user deletion
- Effort: master
Event Categories
The following table lists the data source offered by this integration.
| Data Source | Description |
|---|---|
AWS CloudTrail logs |
Lacework leverages Amazon Web Services to process the data collected by the platform |
File monitoring |
The Lacework agent periodically scans system directories on a monitored system and generates hashes of the files located within directories |
Process monitoring |
The Lacework agent collects metadata information about the processes running on the system. |
Network intrusion detection system |
The Lacework agent collects metadata information about the network connections to and from the system. |
In details, the following table denotes the type of events produced by this integration.
| Name | Values |
|---|---|
| Kind | alert |
| Category | `` |
| Type | `` |
Transformed Events Samples after Ingestion
This section demonstrates how the raw logs will be transformed by our parsers. It shows the extracted fields that will be available for use in the built-in detection rules and hunting activities in the events page. Understanding these transformations is essential for analysts to create effective detection mechanisms with custom detection rules and to leverage the full potential of the collected data.
{
"message": "{\"alertId\": 813628, \"startTime\": \"2022-06-30T00:00:00.000Z\", \"alertType\": \"CloudActivityLogIngestionFailed\", \"severity\": \"High\", \"endTime\": \"2022-06-30T01:00:00.000Z\", \"lastUserUpdatedTime\": \"\", \"status\": \"Open\", \"alertName\": \"Clone of Cloud Activity log ingestion failure detected\", \"alertInfo\": {\"subject\": \"Clone of Cloud Activity log ingestion failure detected: `azure-al-india-dnd` (and `3` more) is failing for data ingestion into Lacework\", \"description\": \"New integration failure detected for azure-al-india-dnd (and 3 more)\", \"supportingFacts\": [{\"supportingFactText\": \"Container Escape\", \"subElements\": [{\"supportingFactText\": \"Use of known container privilege escalation and exploit tools 6 time(s) on host(s) ip-172-18-0-240\"}]}]}, \"entityMap\": {\"API\": \"{object}\", \"CT_User\": \"{object}\", \"CT_RawTime\": \"{object}\", \"Region\": \"{object}\", \"Resource\": \"{object}\", \"RulesTriggered\": \"{object}\", \"SourceIpAddress\": \"{object}\"}}",
"event": {
"code": "CloudActivityLogIngestionFailed",
"end": "2022-06-30T01:00:00Z",
"kind": "alert",
"reason": "Clone of Cloud Activity log ingestion failure detected",
"start": "2022-06-30T00:00:00Z"
},
"@timestamp": "2022-06-30T00:00:00Z",
"lacework": {
"cloud_security": {
"alert": {
"id": 813628,
"info": {
"description": "New integration failure detected for azure-al-india-dnd (and 3 more)",
"subject": "Clone of Cloud Activity log ingestion failure detected: `azure-al-india-dnd` (and `3` more) is failing for data ingestion into Lacework"
},
"severity": "High",
"status": "Open"
}
}
},
"observer": {
"product": "Lacework Cloud Security",
"vendor": "Lacework"
},
"related": {
"user": [
"{object}"
]
},
"rule": {
"name": "{object}"
},
"user": {
"name": "{object}"
}
}
{
"message": "{\"alertId\": 205, \"alertName\": \"Usage of Root Account\", \"startTime\": \"2024-02-13T17:00:00.000Z\", \"alertType\": \"UsageOfRootAccount\", \"severity\": \"Info\", \"internetExposure\": \"UnknownInternetExposure\", \"reachability\": \"UnknownReachability\", \"derivedFields\": {\"category\": \"Policy\", \"sub_category\": \"Cloud Activity\", \"source\": \"AWS\"}, \"endTime\": \"2024-02-13T18:00:00.000Z\", \"lastUserUpdatedTime\": \"\", \"status\": \"Open\", \"alertInfo\": {\"description\": \" For account: 0123456789 : Root account was successfully used 96 times by user 0123456789 \", \"subject\": \"Usage of Root Account: For account: 0123456789 : Root account was successfully used 96 times by user 0123456789 \", \"customerCount\": 0, \"isExpectedLWBehavior\": false}, \"policyId\": \"lacework-global-8\", \"evolvingAlert\": false, \"tagMetadata\": []}",
"event": {
"category": [
"configuration"
],
"code": "UsageOfRootAccount",
"end": "2024-02-13T18:00:00Z",
"kind": "alert",
"reason": "Usage of Root Account",
"start": "2024-02-13T17:00:00Z",
"type": [
"info"
]
},
"@timestamp": "2024-02-13T17:00:00Z",
"lacework": {
"cloud_security": {
"account": {
"name": "0123456789"
},
"alert": {
"id": 205,
"info": {
"description": " For account: 0123456789 : Root account was successfully used 96 times by user 0123456789 ",
"subject": "Usage of Root Account: For account: 0123456789 : Root account was successfully used 96 times by user 0123456789 "
},
"severity": "Info",
"sight": 96,
"status": "Open"
}
}
},
"observer": {
"product": "Lacework Cloud Security",
"vendor": "Lacework"
},
"related": {
"user": [
"0123456789"
]
},
"user": {
"name": "0123456789"
}
}
{
"message": "{\"alertId\": 206, \"alertName\": \"Unauthorized API Call\", \"startTime\": \"2024-02-13T18:00:00.000Z\", \"alertType\": \"UnauthorizedAPICall\", \"severity\": \"Medium\", \"internetExposure\": \"UnknownInternetExposure\", \"reachability\": \"UnknownReachability\", \"derivedFields\": {\"category\": \"Policy\", \"sub_category\": \"Cloud Activity\", \"source\": \"AWS\"}, \"endTime\": \"2024-02-13T19:00:00.000Z\", \"lastUserUpdatedTime\": \"\", \"status\": \"Open\", \"alertInfo\": {\"description\": \" For account: 0123456789 : Unauthorized API call was attempted 18 times by user AROAUR6F6MOZQBRKBX6RG:3e0ac0bf-fa18-4e70-8aa4-44debb525a10 \", \"subject\": \"Unauthorized API Call: For account: 0123456789 : Unauthorized API call was attempted 18 times by user AROAUR6F6MOZQBRKBX6RG:3e0ac0bf-fa18-4e70-8aa4-44debb525a10 \", \"customerCount\": 0, \"isExpectedLWBehavior\": false}, \"policyId\": \"lacework-global-29\", \"evolvingAlert\": false, \"tagMetadata\": []}",
"event": {
"category": [
"configuration"
],
"code": "UnauthorizedAPICall",
"end": "2024-02-13T19:00:00Z",
"kind": "alert",
"reason": "Unauthorized API Call",
"start": "2024-02-13T18:00:00Z",
"type": [
"info"
]
},
"@timestamp": "2024-02-13T18:00:00Z",
"lacework": {
"cloud_security": {
"account": {
"name": "0123456789"
},
"alert": {
"id": 206,
"info": {
"description": " For account: 0123456789 : Unauthorized API call was attempted 18 times by user AROAUR6F6MOZQBRKBX6RG:3e0ac0bf-fa18-4e70-8aa4-44debb525a10 ",
"subject": "Unauthorized API Call: For account: 0123456789 : Unauthorized API call was attempted 18 times by user AROAUR6F6MOZQBRKBX6RG:3e0ac0bf-fa18-4e70-8aa4-44debb525a10 "
},
"severity": "Medium",
"sight": 18,
"status": "Open"
}
}
},
"observer": {
"product": "Lacework Cloud Security",
"vendor": "Lacework"
},
"related": {
"user": [
"AROAUR6F6MOZQBRKBX6RG"
]
},
"user": {
"id": "3e0ac0bf-fa18-4e70-8aa4-44debb525a10",
"name": "AROAUR6F6MOZQBRKBX6RG"
}
}
{
"message": "{\"alertId\": 207, \"alertName\": \"Unauthorized API Call\", \"startTime\": \"2024-02-13T19:00:00.000Z\", \"alertType\": \"UnauthorizedAPICall\", \"severity\": \"Low\", \"internetExposure\": \"UnknownInternetExposure\", \"reachability\": \"UnknownReachability\", \"derivedFields\": {\"category\": \"Policy\", \"sub_category\": \"Cloud Activity\", \"source\": \"AWS\"}, \"endTime\": \"2024-02-13T20:00:00.000Z\", \"lastUserUpdatedTime\": \"\", \"status\": \"Open\", \"alertInfo\": {\"description\": \" For account: 0123456789 : Unauthorized API call was attempted 99 times by user AROAUR6F6MOZ7YRJNRFJB:LACEWORK-CFG-external \", \"subject\": \"Unauthorized API Call: For account: 0123456789 : Unauthorized API call was attempted 99 times by user AROAUR6F6MOZ7YRJNRFJB:LACEWORK-CFG-external \", \"customerCount\": 0, \"isExpectedLWBehavior\": false}, \"policyId\": \"lacework-global-29\", \"evolvingAlert\": false, \"tagMetadata\": []}",
"event": {
"category": [
"configuration"
],
"code": "UnauthorizedAPICall",
"end": "2024-02-13T20:00:00Z",
"kind": "alert",
"reason": "Unauthorized API Call",
"start": "2024-02-13T19:00:00Z",
"type": [
"info"
]
},
"@timestamp": "2024-02-13T19:00:00Z",
"lacework": {
"cloud_security": {
"account": {
"name": "0123456789"
},
"alert": {
"id": 207,
"info": {
"description": " For account: 0123456789 : Unauthorized API call was attempted 99 times by user AROAUR6F6MOZ7YRJNRFJB:LACEWORK-CFG-external ",
"subject": "Unauthorized API Call: For account: 0123456789 : Unauthorized API call was attempted 99 times by user AROAUR6F6MOZ7YRJNRFJB:LACEWORK-CFG-external "
},
"severity": "Low",
"sight": 99,
"status": "Open"
}
}
},
"observer": {
"product": "Lacework Cloud Security",
"vendor": "Lacework"
},
"related": {
"user": [
"AROAUR6F6MOZ7YRJNRFJB"
]
},
"user": {
"name": "AROAUR6F6MOZ7YRJNRFJB"
}
}
{
"message": "{\"alertId\": 208, \"alertName\": \"Unauthorized API Call\", \"startTime\": \"2024-02-14T03:00:00.000Z\", \"alertType\": \"UnauthorizedAPICall\", \"severity\": \"Medium\", \"internetExposure\": \"UnknownInternetExposure\", \"reachability\": \"UnknownReachability\", \"derivedFields\": {\"category\": \"Policy\", \"sub_category\": \"Cloud Activity\", \"source\": \"AWS\"}, \"endTime\": \"2024-02-14T04:00:00.000Z\", \"lastUserUpdatedTime\": \"\", \"status\": \"Open\", \"alertInfo\": {\"description\": \" For account: 0123456789 : Unauthorized API call was attempted 18 times by user AROAUR6F6MOZQBRKBX6RG:a7913090-862e-4cfa-ad11-80508825167e \", \"subject\": \"Unauthorized API Call: For account: 0123456789 : Unauthorized API call was attempted 18 times by user AROAUR6F6MOZQBRKBX6RG:a7913090-862e-4cfa-ad11-80508825167e \", \"customerCount\": 0, \"isExpectedLWBehavior\": false}, \"policyId\": \"lacework-global-29\", \"evolvingAlert\": false, \"tagMetadata\": []}",
"event": {
"category": [
"configuration"
],
"code": "UnauthorizedAPICall",
"end": "2024-02-14T04:00:00Z",
"kind": "alert",
"reason": "Unauthorized API Call",
"start": "2024-02-14T03:00:00Z",
"type": [
"info"
]
},
"@timestamp": "2024-02-14T03:00:00Z",
"lacework": {
"cloud_security": {
"account": {
"name": "0123456789"
},
"alert": {
"id": 208,
"info": {
"description": " For account: 0123456789 : Unauthorized API call was attempted 18 times by user AROAUR6F6MOZQBRKBX6RG:a7913090-862e-4cfa-ad11-80508825167e ",
"subject": "Unauthorized API Call: For account: 0123456789 : Unauthorized API call was attempted 18 times by user AROAUR6F6MOZQBRKBX6RG:a7913090-862e-4cfa-ad11-80508825167e "
},
"severity": "Medium",
"sight": 18,
"status": "Open"
}
}
},
"observer": {
"product": "Lacework Cloud Security",
"vendor": "Lacework"
},
"related": {
"user": [
"AROAUR6F6MOZQBRKBX6RG"
]
},
"user": {
"id": "a7913090-862e-4cfa-ad11-80508825167e",
"name": "AROAUR6F6MOZQBRKBX6RG"
}
}
{
"message": "{\"alertId\": 209, \"alertName\": \"Usage of Root Account\", \"startTime\": \"2024-02-14T10:00:00.000Z\", \"alertType\": \"UsageOfRootAccount\", \"severity\": \"Info\", \"internetExposure\": \"UnknownInternetExposure\", \"reachability\": \"UnknownReachability\", \"derivedFields\": {\"category\": \"Policy\", \"sub_category\": \"Cloud Activity\", \"source\": \"AWS\"}, \"endTime\": \"2024-02-14T11:00:00.000Z\", \"lastUserUpdatedTime\": \"\", \"status\": \"Open\", \"alertInfo\": {\"description\": \" For account: 0123456789 : Root account was successfully used 83 times by user 0123456789 \", \"subject\": \"Usage of Root Account: For account: 0123456789 : Root account was successfully used 83 times by user 0123456789 \", \"customerCount\": 0, \"isExpectedLWBehavior\": false}, \"policyId\": \"lacework-global-8\", \"evolvingAlert\": false, \"tagMetadata\": []}",
"event": {
"category": [
"configuration"
],
"code": "UsageOfRootAccount",
"end": "2024-02-14T11:00:00Z",
"kind": "alert",
"reason": "Usage of Root Account",
"start": "2024-02-14T10:00:00Z",
"type": [
"info"
]
},
"@timestamp": "2024-02-14T10:00:00Z",
"lacework": {
"cloud_security": {
"account": {
"name": "0123456789"
},
"alert": {
"id": 209,
"info": {
"description": " For account: 0123456789 : Root account was successfully used 83 times by user 0123456789 ",
"subject": "Usage of Root Account: For account: 0123456789 : Root account was successfully used 83 times by user 0123456789 "
},
"severity": "Info",
"sight": 83,
"status": "Open"
}
}
},
"observer": {
"product": "Lacework Cloud Security",
"vendor": "Lacework"
},
"related": {
"user": [
"0123456789"
]
},
"user": {
"name": "0123456789"
}
}
{
"message": "{\"alertId\": 210, \"alertName\": \"Usage of Root Account\", \"startTime\": \"2024-02-14T11:00:00.000Z\", \"alertType\": \"UsageOfRootAccount\", \"severity\": \"Info\", \"internetExposure\": \"UnknownInternetExposure\", \"reachability\": \"UnknownReachability\", \"derivedFields\": {\"category\": \"Policy\", \"sub_category\": \"Cloud Activity\", \"source\": \"AWS\"}, \"endTime\": \"2024-02-14T12:00:00.000Z\", \"lastUserUpdatedTime\": \"\", \"status\": \"Open\", \"alertInfo\": {\"description\": \" For account: 0123456789 : Root account was successfully used 8 times by user 0123456789 \", \"subject\": \"Usage of Root Account: For account: 0123456789 : Root account was successfully used 8 times by user 0123456789 \", \"customerCount\": 0, \"isExpectedLWBehavior\": false}, \"policyId\": \"lacework-global-8\", \"evolvingAlert\": false, \"tagMetadata\": []}",
"event": {
"category": [
"configuration"
],
"code": "UsageOfRootAccount",
"end": "2024-02-14T12:00:00Z",
"kind": "alert",
"reason": "Usage of Root Account",
"start": "2024-02-14T11:00:00Z",
"type": [
"info"
]
},
"@timestamp": "2024-02-14T11:00:00Z",
"lacework": {
"cloud_security": {
"account": {
"name": "0123456789"
},
"alert": {
"id": 210,
"info": {
"description": " For account: 0123456789 : Root account was successfully used 8 times by user 0123456789 ",
"subject": "Usage of Root Account: For account: 0123456789 : Root account was successfully used 8 times by user 0123456789 "
},
"severity": "Info",
"sight": 8,
"status": "Open"
}
}
},
"observer": {
"product": "Lacework Cloud Security",
"vendor": "Lacework"
},
"related": {
"user": [
"0123456789"
]
},
"user": {
"name": "0123456789"
}
}
{
"message": "{\"alertId\":202634,\"alertName\":\"New Grant Added to Key Management Service (KMS) Key\",\"startTime\":\"2025-08-11T14:07:51.000Z\",\"alertType\":\"New Grant Added to Key Management Service (KMS) Key\",\"severity\":\"Info\",\"derivedFields\":{\"category\":\"Policy\",\"sub_category\":\"Cloud Activity\",\"source\":\"AWS\"},\"endTime\":\"2025-08-11T14:27:58.000Z\",\"lastUserUpdatedTime\":\"\",\"status\":\"Open\",\"alertInfo\":{\"description\":\" For account: 12345678 : new grant(s) added to a Customer Master Key by user JOHNDOE:1234 \",\"subject\":\"New Grant Added to Key Management Service (KMS) Key: For account: 12345678 : new grant(s) added to a Customer Master Key by user JOHNDOE:1234 \",\"customerCount\":0,\"isExpectedLWBehavior\":false},\"policyId\":\"lacework-global-19\",\"evolvingAlert\":true,\"tagMetadata\":[],\"internetExposure\":\"UnknownInternetExposure\",\"reachability\":\"UnknownReachability\",\"report\":\"FALSE\"}",
"event": {
"category": [
"configuration"
],
"code": "New Grant Added to Key Management Service (KMS) Key",
"end": "2025-08-11T14:27:58Z",
"kind": "alert",
"reason": "New Grant Added to Key Management Service (KMS) Key",
"start": "2025-08-11T14:07:51Z",
"type": [
"info"
]
},
"@timestamp": "2025-08-11T14:07:51Z",
"lacework": {
"cloud_security": {
"account": {
"name": "12345678"
},
"alert": {
"id": 202634,
"info": {
"description": " For account: 12345678 : new grant(s) added to a Customer Master Key by user JOHNDOE:1234 ",
"subject": "New Grant Added to Key Management Service (KMS) Key: For account: 12345678 : new grant(s) added to a Customer Master Key by user JOHNDOE:1234 "
},
"severity": "Info",
"sight": 1,
"status": "Open"
}
}
},
"observer": {
"product": "Lacework Cloud Security",
"vendor": "Lacework"
},
"related": {
"user": [
"JOHNDOE"
]
},
"user": {
"name": "JOHNDOE"
}
}
{
"message": "{\"alertId\":202467,\"alertName\":\"Virtual Private Cloud (VPC) Change\",\"startTime\":\"2025-08-11T04:16:39.000Z\",\"alertType\":\"Virtual Private Cloud (VPC) Change\",\"severity\":\"Info\",\"derivedFields\":{\"category\":\"Policy\",\"sub_category\":\"Cloud Activity\",\"source\":\"AWS\"},\"endTime\":\"2025-08-11T04:19:25.000Z\",\"lastUserUpdatedTime\":\"\",\"status\":\"Open\",\"alertInfo\":{\"description\":\" For account: 123456789 : 5 new VPC(s) created, deleted or changed by user USER01:john.doe@domain.com \",\"subject\":\"Virtual Private Cloud (VPC) Change: For account: 123456789 : 5 new VPC(s) created, deleted or changed by user USER01:john.doe@domain.com \",\"customerCount\":0,\"isExpectedLWBehavior\":false},\"policyId\":\"lacework-global-1\",\"evolvingAlert\":false,\"tagMetadata\":[],\"internetExposure\":\"UnknownInternetExposure\",\"reachability\":\"UnknownReachability\",\"report\":\"FALSE\"}",
"event": {
"category": [
"configuration"
],
"code": "Virtual Private Cloud (VPC) Change",
"end": "2025-08-11T04:19:25Z",
"kind": "alert",
"reason": "Virtual Private Cloud (VPC) Change",
"start": "2025-08-11T04:16:39Z",
"type": [
"info"
]
},
"@timestamp": "2025-08-11T04:16:39Z",
"lacework": {
"cloud_security": {
"account": {
"name": "123456789"
},
"alert": {
"id": 202467,
"info": {
"description": " For account: 123456789 : 5 new VPC(s) created, deleted or changed by user USER01:john.doe@domain.com ",
"subject": "Virtual Private Cloud (VPC) Change: For account: 123456789 : 5 new VPC(s) created, deleted or changed by user USER01:john.doe@domain.com "
},
"severity": "Info",
"sight": 1,
"status": "Open"
}
}
},
"observer": {
"product": "Lacework Cloud Security",
"vendor": "Lacework"
},
"related": {
"user": [
"USER01"
]
},
"user": {
"email": "john.doe@domain.com",
"name": "USER01"
}
}
{
"message": "{\"alertId\":202655,\"alertName\":\"New AWS user\",\"startTime\":\"2025-08-11T14:00:00.000Z\",\"alertType\":\"NewAwsUser\",\"severity\":\"Low\",\"derivedFields\":{\"category\":\"Anomaly\",\"sub_category\":\"Cloud Activity\",\"source\":\"AWS\"},\"endTime\":\"2025-08-11T15:00:00.000Z\",\"lastUserUpdatedTime\":\"\",\"status\":\"Open\",\"alertInfo\":{\"description\":\"For account: 12345678 : User AssumedRole/12345678:AWSServiceRoleForAmazonGuardDuty using Aws for the first time\",\"subject\":\"New AWS user: For account: 12345678 : User AssumedRole/12345678:AWSServiceRoleForAmazonGuardDuty using Aws for the first time\",\"customerCount\":0,\"isExpectedLWBehavior\":false},\"evolvingAlert\":false,\"tagMetadata\":[],\"internetExposure\":\"UnknownInternetExposure\",\"reachability\":\"UnknownReachability\",\"report\":\"FALSE\"}",
"event": {
"category": [
"configuration"
],
"code": "NewAwsUser",
"end": "2025-08-11T15:00:00Z",
"kind": "alert",
"reason": "New AWS user",
"start": "2025-08-11T14:00:00Z",
"type": [
"info"
]
},
"@timestamp": "2025-08-11T14:00:00Z",
"lacework": {
"cloud_security": {
"account": {
"name": "12345678"
},
"alert": {
"id": 202655,
"info": {
"description": "For account: 12345678 : User AssumedRole/12345678:AWSServiceRoleForAmazonGuardDuty using Aws for the first time",
"subject": "New AWS user: For account: 12345678 : User AssumedRole/12345678:AWSServiceRoleForAmazonGuardDuty using Aws for the first time"
},
"severity": "Low",
"sight": 1,
"status": "Open"
}
}
},
"observer": {
"product": "Lacework Cloud Security",
"vendor": "Lacework"
},
"related": {
"user": [
"AWSServiceRoleForAmazonGuardDuty"
]
},
"user": {
"name": "AWSServiceRoleForAmazonGuardDuty"
}
}
{
"message": "{\"alertId\":233783,\"alertName\":\"AWS account accessed from a new geolocation\",\"startTime\":\"2024-08-05T07:00:00.000Z\",\"alertType\":\"LoginFromSourceUsingCalltype\",\"severity\":\"Low\",\"derivedFields\":{\"category\":\"Anomaly\",\"sub_category\":\"Cloud Activity\",\"source\":\"AWS\"},\"endTime\":\"2024-08-05T08:00:00.000Z\",\"lastUserUpdatedTime\":\"\",\"status\":\"Open\",\"alertInfo\":{\"description\":\"For account: 123456789 (company) : Unknown/123456789:john.doe@company.com logged in from an IP address 1.2.3.4 in a new location Rennes,Bretagne,France using the AWS event type AwsServiceEvent . This is the first time this AWS account has been accessed from this location.\",\"subject\":\"AWS account accessed from a new geolocation: For account: 123456789 (company) : Unknown/123456789:john.doe@company.com logged in from an IP address 1.2.3.4 in a new location Rennes,Bretagne,France using the AWS event type AwsServiceEvent . This is the first time this AWS account has been accessed from this location.\",\"customerCount\":0,\"isExpectedLWBehavior\":false},\"evolvingAlert\":false,\"tagMetadata\":[],\"internetExposure\":\"UnknownInternetExposure\",\"reachability\":\"UnknownReachability\"}",
"event": {
"category": [
"configuration"
],
"code": "LoginFromSourceUsingCalltype",
"end": "2024-08-05T08:00:00Z",
"kind": "alert",
"reason": "AWS account accessed from a new geolocation",
"start": "2024-08-05T07:00:00Z",
"type": [
"info"
]
},
"@timestamp": "2024-08-05T07:00:00Z",
"lacework": {
"cloud_security": {
"account": {
"name": "123456789"
},
"alert": {
"id": 233783,
"info": {
"description": "For account: 123456789 (company) : Unknown/123456789:john.doe@company.com logged in from an IP address 1.2.3.4 in a new location Rennes,Bretagne,France using the AWS event type AwsServiceEvent . This is the first time this AWS account has been accessed from this location.",
"subject": "AWS account accessed from a new geolocation: For account: 123456789 (company) : Unknown/123456789:john.doe@company.com logged in from an IP address 1.2.3.4 in a new location Rennes,Bretagne,France using the AWS event type AwsServiceEvent . This is the first time this AWS account has been accessed from this location."
},
"severity": "Low",
"sight": 1,
"status": "Open"
},
"company": {
"name": "company"
}
}
},
"observer": {
"product": "Lacework Cloud Security",
"vendor": "Lacework"
},
"related": {
"ip": [
"1.2.3.4"
]
},
"source": {
"address": "1.2.3.4",
"ip": "1.2.3.4"
},
"user": {
"email": "john.doe@company.com"
}
}
{
"message": "{\"alertId\":233849,\"alertName\":\"GCP user logged in from new source\",\"startTime\":\"2024-08-05T11:00:00.000Z\",\"alertType\":\"GcpUserLoggedInFromSource\",\"severity\":\"Low\",\"derivedFields\":{\"category\":\"Anomaly\",\"sub_category\":\"Cloud Activity\",\"source\":\"GCP\"},\"endTime\":\"2024-08-05T12:00:00.000Z\",\"lastUserUpdatedTime\":\"\",\"status\":\"Open\",\"alertInfo\":{\"description\":\" john.doe@company.com logged in from a new source Rennes,Bretagne,France for the first time \",\"subject\":\"GCP user logged in from new source: john.doe@company.com logged in from a new source Rennes,Bretagne,France for the first time \",\"customerCount\":0,\"isExpectedLWBehavior\":false},\"policyId\":\"203135697\",\"evolvingAlert\":false,\"tagMetadata\":[],\"internetExposure\":\"UnknownInternetExposure\",\"reachability\":\"UnknownReachability\"}",
"event": {
"category": [
"configuration"
],
"code": "GcpUserLoggedInFromSource",
"end": "2024-08-05T12:00:00Z",
"kind": "alert",
"reason": "GCP user logged in from new source",
"start": "2024-08-05T11:00:00Z",
"type": [
"info"
]
},
"@timestamp": "2024-08-05T11:00:00Z",
"lacework": {
"cloud_security": {
"alert": {
"id": 233849,
"info": {
"description": " john.doe@company.com logged in from a new source Rennes,Bretagne,France for the first time ",
"subject": "GCP user logged in from new source: john.doe@company.com logged in from a new source Rennes,Bretagne,France for the first time "
},
"severity": "Low",
"sight": 1,
"status": "Open"
}
}
},
"observer": {
"product": "Lacework Cloud Security",
"vendor": "Lacework"
},
"user": {
"email": "john.doe@company.com"
}
}
{
"message": "{\"alertId\":233782,\"alertName\":\"New GCP service\",\"startTime\":\"2024-08-05T07:00:00.000Z\",\"alertType\":\"NewGcpService\",\"severity\":\"Medium\",\"derivedFields\":{\"category\":\"Anomaly\",\"sub_category\":\"Cloud Activity\",\"source\":\"GCP\"},\"endTime\":\"2024-08-05T08:00:00.000Z\",\"lastUserUpdatedTime\":\"\",\"status\":\"Open\",\"alertInfo\":{\"description\":\"For project: project-001 (test-projects) : A new service service.apis.com was used for the first time (by user john.doe@company.com)\",\"subject\":\"New GCP service: For project: project-001 (test-projects) : A new service service.apis.com was used for the first time (by user john.doe@company.com)\",\"customerCount\":0,\"isExpectedLWBehavior\":false},\"policyId\":\"203101916\",\"evolvingAlert\":false,\"tagMetadata\":[],\"internetExposure\":\"UnknownInternetExposure\",\"reachability\":\"UnknownReachability\"}",
"event": {
"category": [
"configuration"
],
"code": "NewGcpService",
"end": "2024-08-05T08:00:00Z",
"kind": "alert",
"reason": "New GCP service",
"start": "2024-08-05T07:00:00Z",
"type": [
"info"
]
},
"@timestamp": "2024-08-05T07:00:00Z",
"lacework": {
"cloud_security": {
"alert": {
"id": 233782,
"info": {
"description": "For project: project-001 (test-projects) : A new service service.apis.com was used for the first time (by user john.doe@company.com)",
"subject": "New GCP service: For project: project-001 (test-projects) : A new service service.apis.com was used for the first time (by user john.doe@company.com)"
},
"severity": "Medium",
"sight": 1,
"status": "Open"
}
}
},
"observer": {
"product": "Lacework Cloud Security",
"vendor": "Lacework"
},
"service": {
"name": "service.apis.com"
},
"user": {
"email": "john.doe@company.com"
}
}
{
"message": "{\"alertId\":233726,\"alertName\":\"New GCP source\",\"startTime\":\"2024-08-05T00:00:00.000Z\",\"alertType\":\"NewGcpSource\",\"severity\":\"Low\",\"derivedFields\":{\"category\":\"Anomaly\",\"sub_category\":\"Cloud Activity\",\"source\":\"GCP\"},\"endTime\":\"2024-08-05T01:00:00.000Z\",\"lastUserUpdatedTime\":\"\",\"status\":\"Open\",\"alertInfo\":{\"description\":\" A user (john.doe@company.com) logged in from a new source Rennes,Bretagne,France for the first time\",\"subject\":\"New GCP source: A user (john.doe@company.com) logged in from a new source Rennes,Bretagne,France for the first time\",\"customerCount\":0,\"isExpectedLWBehavior\":false},\"policyId\":\"203059776\",\"evolvingAlert\":false,\"tagMetadata\":[],\"internetExposure\":\"UnknownInternetExposure\",\"reachability\":\"UnknownReachability\"}",
"event": {
"category": [
"configuration"
],
"code": "NewGcpSource",
"end": "2024-08-05T01:00:00Z",
"kind": "alert",
"reason": "New GCP source",
"start": "2024-08-05T00:00:00Z",
"type": [
"info"
]
},
"@timestamp": "2024-08-05T00:00:00Z",
"lacework": {
"cloud_security": {
"alert": {
"id": 233726,
"info": {
"description": " A user (john.doe@company.com) logged in from a new source Rennes,Bretagne,France for the first time",
"subject": "New GCP source: A user (john.doe@company.com) logged in from a new source Rennes,Bretagne,France for the first time"
},
"severity": "Low",
"sight": 1,
"status": "Open"
}
}
},
"observer": {
"product": "Lacework Cloud Security",
"vendor": "Lacework"
},
"user": {
"email": "john.doe@company.com"
}
}
{
"message": "{\"alertId\":233825,\"alertName\":\"New GCP user\",\"startTime\":\"2024-08-05T10:00:00.000Z\",\"alertType\":\"NewGcpUser\",\"severity\":\"Info\",\"derivedFields\":{\"category\":\"Anomaly\",\"sub_category\":\"Cloud Activity\",\"source\":\"GCP\"},\"endTime\":\"2024-08-05T11:00:00.000Z\",\"lastUserUpdatedTime\":\"\",\"status\":\"Open\",\"alertInfo\":{\"description\":\" User john.doe@company.com using GCP for the first time\",\"subject\":\"New GCP user: User john.doe@company.com using GCP for the first time\",\"customerCount\":0,\"isExpectedLWBehavior\":false},\"policyId\":\"203126334\",\"evolvingAlert\":false,\"tagMetadata\":[],\"internetExposure\":\"UnknownInternetExposure\",\"reachability\":\"UnknownReachability\"}",
"event": {
"category": [
"configuration"
],
"code": "NewGcpUser",
"end": "2024-08-05T11:00:00Z",
"kind": "alert",
"reason": "New GCP user",
"start": "2024-08-05T10:00:00Z",
"type": [
"info"
]
},
"@timestamp": "2024-08-05T10:00:00Z",
"lacework": {
"cloud_security": {
"alert": {
"id": 233825,
"info": {
"description": " User john.doe@company.com using GCP for the first time",
"subject": "New GCP user: User john.doe@company.com using GCP for the first time"
},
"severity": "Info",
"sight": 1,
"status": "Open"
}
}
},
"observer": {
"product": "Lacework Cloud Security",
"vendor": "Lacework"
},
"user": {
"email": "john.doe@company.com"
}
}
{
"message": "{\"alertId\":233808,\"alertName\":\"Security Group Change\",\"startTime\":\"2024-08-05T09:00:00.000Z\",\"alertType\":\"SecurityGroupChange\",\"severity\":\"Info\",\"derivedFields\":{\"category\":\"Policy\",\"sub_category\":\"Cloud Activity\",\"source\":\"AWS\"},\"endTime\":\"2024-08-05T10:00:00.000Z\",\"lastUserUpdatedTime\":\"\",\"status\":\"Open\",\"alertInfo\":{\"description\":\" For account: 1234567890 (company) : SecurityGroup sg-012345 created/deleted/changed 5 times by user USER01:john.doe@company.com \",\"subject\":\"Security Group Change: For account: 1234567890 (company) : SecurityGroup sg-012345 created/deleted/changed 5 times by user USER01:john.doe@company.com \",\"customerCount\":0,\"isExpectedLWBehavior\":false},\"policyId\":\"lacework-global-2\",\"evolvingAlert\":false,\"tagMetadata\":[],\"internetExposure\":\"UnknownInternetExposure\",\"reachability\":\"UnknownReachability\"}",
"event": {
"category": [
"configuration"
],
"code": "SecurityGroupChange",
"end": "2024-08-05T10:00:00Z",
"kind": "alert",
"reason": "Security Group Change",
"start": "2024-08-05T09:00:00Z",
"type": [
"info"
]
},
"@timestamp": "2024-08-05T09:00:00Z",
"lacework": {
"cloud_security": {
"account": {
"name": "1234567890"
},
"alert": {
"id": 233808,
"info": {
"description": " For account: 1234567890 (company) : SecurityGroup sg-012345 created/deleted/changed 5 times by user USER01:john.doe@company.com ",
"subject": "Security Group Change: For account: 1234567890 (company) : SecurityGroup sg-012345 created/deleted/changed 5 times by user USER01:john.doe@company.com "
},
"severity": "Info",
"sight": 5,
"status": "Open"
},
"company": {
"name": "company"
}
}
},
"observer": {
"product": "Lacework Cloud Security",
"vendor": "Lacework"
},
"related": {
"user": [
"USER01"
]
},
"user": {
"email": "john.doe@company.com",
"name": "USER01"
}
}
Extracted Fields
The following table lists the fields that are extracted, normalized under the ECS format, analyzed and indexed by the parser. It should be noted that infered fields are not listed.
| Name | Type | Description |
|---|---|---|
@timestamp |
date |
Date/time when the event originated. |
event.category |
keyword |
Event category. The second categorization field in the hierarchy. |
event.code |
keyword |
Identification code for this event. |
event.end |
date |
event.end contains the date when the event ended or when the activity was last observed. |
event.kind |
keyword |
The kind of the event. The highest categorization field in the hierarchy. |
event.reason |
keyword |
Reason why this event happened, according to the source |
event.start |
date |
event.start contains the date when the event started or when the activity was first observed. |
event.type |
keyword |
Event type. The third categorization field in the hierarchy. |
lacework.cloud_security.account.name |
keyword |
Account name |
lacework.cloud_security.alert.id |
long |
Lacework alert ID |
lacework.cloud_security.alert.info.description |
keyword |
Alert info description |
lacework.cloud_security.alert.info.subject |
keyword |
Alert info subject |
lacework.cloud_security.alert.severity |
keyword |
Alert severity |
lacework.cloud_security.alert.sight |
long |
Number of times an alert have been seen |
lacework.cloud_security.alert.status |
keyword |
Alert status |
lacework.cloud_security.company.name |
keyword |
Company name |
observer.product |
keyword |
The product name of the observer. |
observer.vendor |
keyword |
Vendor name of the observer. |
rule.name |
keyword |
Rule name |
service.name |
keyword |
Name of the service. |
source.ip |
ip |
IP address of the source. |
user.email |
keyword |
User email address. |
user.id |
keyword |
Unique identifier of the user. |
user.name |
keyword |
Short name or login of the user. |
For more information on the Intake Format, please find the code of the Parser, Smart Descriptions, and Supported Events here.