Nozomi Vantage
Overview
Nozomi Vantage is a comprehensive SaaS-based platform that delivers real-time visibility, threat detection, and incident response for industrial environments. Designed for operational technology (OT) security, it enables organizations to monitor critical infrastructure and IoT devices effectively. With advanced analytics and intuitive dashboards, Nozomi Vantage helps ensure the safety and resilience of connected systems against cyber threats.
Warning
Important note - This format is currently in beta. We highly value your feedback to improve its performance.
- Vendor: Nozomi Networks
- Supported environment: SaaS
- Detection based on: Alerts, Telemetry
- Supported application or feature:
- Alerts
- Assets
- Vulnerabilities
- Wireless Networks
Configure
Create an API key
- Log into Vantage.
- In the top navigation bar, select
Profile. - Select
API Keys. -
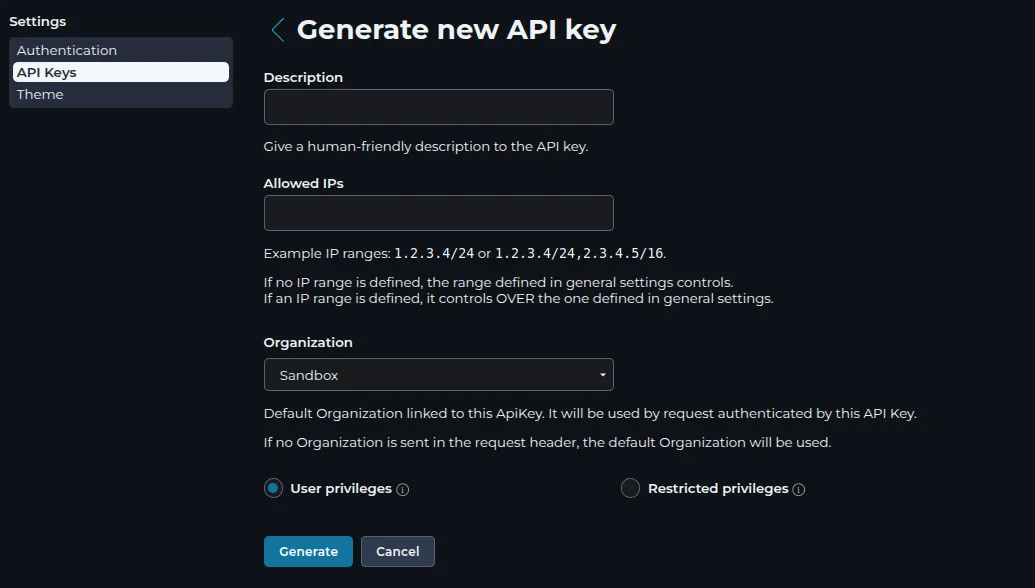
To generate a new API key, select
Add, fill the form and clickGenerate.
More details you can find in the Nozomi documentation: Generate an API key.
Create your intake
Go to the intake page and create a new intake from the Nozomi Vantage
Raw Events Samples
In this section, you will find examples of raw logs as generated natively by the source. These examples are provided to help integrators understand the data format before ingestion into Sekoia.io. It is crucial for setting up the correct parsing stages and ensuring that all relevant information is captured.
{
"event_type": "alerts",
"id": "111111-111111-11111111",
"ack": false,
"_can": {
"trace_requests": true,
"close_learn_alerts": false,
"security_control_panel.tuning": true
},
"name": "Program change",
"note": null,
"time": 1750085403336,
"id_dst": "1.2.3.125",
"id_src": "1.2.3.58",
"ip_dst": "1.2.3.125",
"ip_src": "1.2.3.58",
"status": "open",
"counter": 1,
"mac_dst": "f4:22:11:33:44:55",
"mac_src": "00:11:22:33:44:be",
"parents": [],
"uid_dst": "222222-222222-22222-22222",
"uid_src": "333333-33333-333333-33333",
"port_dst": 44818,
"port_src": 58679,
"protocol": "ethernetip",
"severity": 10,
"zone_dst": "Production_B",
"zone_src": "Production_B",
"dst_roles": "producer",
"label_dst": null,
"label_src": null,
"src_roles": "consumer, engineering_station",
"ti_source": "",
"type_name": "Program change",
"types_dst": [
"OT_device"
],
"types_src": [
"computer"
],
"alert_info": {},
"bpf_filter": "(ip host 1.2.3.58 and ip host 1.2.3.125 and tcp port 58679 and tcp port 44818) or (vlan and ip host 1.2.3.58 and ip host 1.2.3.125 and tcp port 58679 and tcp port 44818)",
"levels_dst": [
"2"
],
"levels_src": [
"2"
],
"properties": {
"to_id": "1.2.3.125",
"from_id": "1.2.3.58",
"base_risk": 6,
"raised_by": "n2os_ids",
"n2os_version": "25.1.0-05290909_263B4",
"is_dst_public": false,
"is_src_public": false,
"is_dst_node_learned": true,
"is_src_node_learned": true,
"mitre_attack_for_ics": {
"source": {
"types": [
"Engineering Workstation"
],
"levels": [
"2"
]
},
"destination": {
"types": [
"Field Controller/RTU/PLC/IED"
],
"levels": [
"2"
]
}
},
"is_dst_reputation_bad": false,
"is_src_reputation_bad": false
},
"closed_time": 0,
"description": "Online edits have been made on the PLC with IP 1.2.3.125. The following steps were executed:\n[1]- Changed Controller [ C1_1756 ] to Run Mode\n[2]- Changed Controller [ C1_1756 ] to Program Mode\n[3]- Downloaded project [ C:\\USERS\\NOZOMI\\DESKTOP\\LADDERBOMB\\PLC_LOGIC_CHALLENGE2\\challenge2changed.ACD ] to [ \\AB_ETHIP-1\\1.2.3.125\\C1_1756 ]\n[4]- Changed Controller [ C1_1756 ] to Run Mode\n[5]- Changed Controller [ C1_1756 ] to Program Mode\n[6]- Downloaded project [ C:\\USERS\\NOZOMI\\DESKTOP\\LADDERBOMB\\PLC_LOGIC_CHALLENGE2\\challenge2changed.ACD ] to [ \\AB_ETHIP-1\\1.2.3.125\\C1_1756 ]\n[7]- Changed Controller [ C1_1756 ] to Run Mode\n[8]- Changed Controller [ C1_1756 ] to Program Mode\n[9]- Downloaded project [ C:\\USERS\\NOZOMI\\DESKTOP\\LADDERBOMB\\PLC_LOGIC_CHALLENGE2\\challenge2changed.ACD ] to [ \\AB_ETHIP-1\\1.2.3.125\\C1_1756 ]\n[10]- Changed Controller [ C1_1756 ] to Run Mode\n",
"is_incident": false,
"is_security": true,
"threat_name": "",
"created_time": 1750085403336,
"trigger_type": null,
"incident_keys": [],
"appliance_host": "Sandbox-TAE-Guardian3",
"capture_device": "base.pcap",
"physical_links": null,
"grouped_visible": true,
"assertion_source": "",
"custom_fields_dst": {},
"custom_fields_src": {},
"playbook_contents": null,
"transport_protocol": "tcp",
"sec_profile_visible": true,
"mitre_attack_tactics": null,
"additional_description": {},
"mitre_attack_techniques": null,
"edge_id": "111111-111111-11111111",
"risk": 6,
"trace_status": null,
"trace_sha1": null,
"record_created_at": 1750085573483,
"type_id": "SIGN:PROGRAM:CHANGE",
"trigger_id": null
}
{
"event_type": "assets",
"ip": [
"1.2.3.4"
],
"os": "Windows",
"name": "Desktop/Laptop Computer",
"time": 1750088529631,
"type": "computer",
"level": "1",
"nodes": [
"1.2.3.4"
],
"roles": [
"other"
],
"zones": [
"Substation"
],
"fields": {},
"vendor": "Dell",
"os:info": {
"source": "passive"
},
"lifecycle": "",
"protocols": [
"http",
"keyence"
],
"type:info": {
"source": "passive"
},
"created_at": 1724888822747,
"mac_vendor": [
"Test mac vendor"
],
"nodes_uids": [
"111111111-111111-1111111"
],
"properties": {
"1.2.3.4": {
"_type.passive": "computer",
"_type.enrichment": "computer",
"_vendor.enrichment": "Dell",
"_type.passive.unknown": "computer",
"_product_name.enrichment": "Desktop/Laptop Computer",
"_type.enrichment.unknown": "computer",
"http.last_client_version": "Chrome 91.0.4472.124",
"_vendor.enrichment.unknown": "Dell",
"_product_name.enrichment.unknown": "Desktop/Laptop Computer"
}
},
"arc_version": "",
"mac_address": [
"00:11:22:33:44:55"
],
"vendor:info": {
"source": "enrichment",
"confidence": "low",
"granularity": "generic"
},
"product_name": "Desktop/Laptop Computer",
"custom_fields": {},
"serial_number": "",
"capture_device": "base.pcap",
"is_ai_enriched": true,
"is_sp_enriched": false,
"is_ti_enriched": true,
"lifecycle:info": {
"source": "none"
},
"os_or_firmware": "Windows",
"appliance_hosts": [
"Sandbox-TAE-Guardian1"
],
"is_arc_enriched": false,
"end_of_sale_date": 0,
"firmware_version": "",
"mac_address_level": {
"00:11:22:33:44:55": "unconfirmed"
},
"product_name:info": {
"source": "enrichment",
"confidence": "low",
"granularity": "generic"
},
"last_activity_time": 1750088403014,
"serial_number:info": {
"source": "none"
},
"end_of_support_date": 0,
"os_or_firmware:info": {
"source": "passive"
},
"technology_category": "IT",
"end_of_sale_date:info": {
"source": "none"
},
"firmware_version:info": {
"source": "none"
},
"end_of_support_date:info": {
"source": "none"
},
"edge_id": "222222-2222222-22222222-222222",
"risk": 9,
"record_created_at": 1741874120458,
"mobility:info": {},
"mobility": null,
"mobility_votes": {
"asset-kb": "unknown"
},
"risk_configuration": {
"type_weight": 0.5,
"ai_risk_weight": 1,
"lifecycle_weight": 0.5,
"asset_criticality": 25,
"alerts_risk_weight": 0.5,
"device_risk_weight": 0.5,
"open_alerts_weight": 0.5,
"compensating_control": 0,
"high_risk_alert_level": 7,
"unsafe_countries_list": [
"china",
"russia",
"north korea",
"ukraine",
"vietnam",
"indonesia"
],
"unsafe_protocols_list": [
"ftp",
"http",
"imap",
"llmnr",
"ntlm",
"nfs",
"pop3",
"rdp",
"smb",
"snmp",
"smtp",
"sip",
"telnet"
],
"connection_type_weight": 0.5,
"risk_mitigation_factor": 0,
"high_risk_alerts_weight": 0.5,
"network_activity_weight": 0.5,
"unsafe_countries_weight": 0.5,
"unsafe_protocols_weight": 0.5,
"asset_criticality_factor": 0,
"asset_criticality_weight": 0.5,
"internet_exposure_weight": 0.5,
"communication_risk_weight": 0.5,
"technology_category_weight": 0.5,
"compensating_control_weight": 0.2,
"open_vulnerabilities_weight": 0.5,
"vulnerabilities_risk_weight": 0.5,
"suboptimal_management_weight": 0.5,
"critical_vulnerabilities_weight": 0.5,
"high_risk_vulnerabilities_level": 7,
"open_vulnerabilities_likelihood": 0.7,
"exploitable_vulnerabilities_weight": 0.5,
"exploitable_vulnerabilities_epss_score": 0.2
},
"nozomi_risk": 9,
"activity_times": {
"1749400200000": 12,
"1749403800000": 11,
"1749407400000": 11,
"1749411000000": 12,
"1749414600000": 10,
"1749418200000": 10,
"1749421800000": 8,
"1749425400000": 12,
"1749429000000": 12,
"1749432600000": 10,
"1749436200000": 11,
"1749439800000": 8,
"1749443400000": 12,
"1749447000000": 10,
"1749450600000": 12,
"1749454200000": 8,
"1749457800000": 12,
"1749461400000": 11,
"1749465000000": 12,
"1749468600000": 12,
"1749472200000": 12,
"1749475800000": 12,
"1749479400000": 12,
"1749483000000": 12,
"1749486600000": 12,
"1749490200000": 12,
"1749493800000": 12,
"1749497400000": 12,
"1749501000000": 12,
"1749504600000": 12,
"1749508200000": 12,
"1749511800000": 12,
"1749515400000": 12,
"1749519000000": 11,
"1749522600000": 12,
"1749526200000": 11,
"1749529800000": 10,
"1749533400000": 11,
"1749537000000": 11,
"1749540600000": 12,
"1749544200000": 12,
"1749547800000": 12,
"1749551400000": 10,
"1749555000000": 9,
"1749558600000": 10,
"1749562200000": 12,
"1749565800000": 12,
"1749569400000": 11,
"1749573000000": 12,
"1749576600000": 12,
"1749580200000": 12,
"1749583800000": 12,
"1749587400000": 12,
"1749591000000": 12,
"1749594600000": 12,
"1749598200000": 12,
"1749601800000": 12,
"1749605400000": 12,
"1749609000000": 12,
"1749612600000": 12,
"1749616200000": 12,
"1749619800000": 12,
"1749623400000": 12,
"1749627000000": 12,
"1749630600000": 12,
"1749634200000": 12,
"1749637800000": 12,
"1749641400000": 12,
"1749645000000": 12,
"1749648600000": 12,
"1749652200000": 12,
"1749655800000": 12,
"1749659400000": 12,
"1749663000000": 12,
"1749666600000": 12,
"1749670200000": 12,
"1749673800000": 12,
"1749677400000": 12,
"1749681000000": 12,
"1749684600000": 12,
"1749688200000": 12,
"1749691800000": 12,
"1749695400000": 12,
"1749699000000": 12,
"1749702600000": 12,
"1749706200000": 12,
"1749709800000": 12,
"1749713400000": 12,
"1749717000000": 12,
"1749720600000": 12,
"1749724200000": 12,
"1749727800000": 12,
"1749731400000": 12,
"1749735000000": 12,
"1749738600000": 12,
"1749742200000": 12,
"1749745800000": 12,
"1749749400000": 12,
"1749753000000": 12,
"1749756600000": 12,
"1749760200000": 12,
"1749763800000": 12,
"1749767400000": 12,
"1749771000000": 12,
"1749774600000": 12,
"1749778200000": 12,
"1749781800000": 12,
"1749785400000": 12,
"1749789000000": 12,
"1749792600000": 12,
"1749796200000": 12,
"1749799800000": 12,
"1749803400000": 12,
"1749807000000": 12,
"1749810600000": 12,
"1749814200000": 12,
"1749817800000": 12,
"1749821400000": 12,
"1749825000000": 12,
"1749828600000": 12,
"1749832200000": 12,
"1749835800000": 12,
"1749839400000": 12,
"1749843000000": 12,
"1749846600000": 12,
"1749850200000": 12,
"1749853800000": 12,
"1749857400000": 12,
"1749861000000": 12,
"1749864600000": 12,
"1749868200000": 12,
"1749871800000": 12,
"1749875400000": 12,
"1749879000000": 12,
"1749882600000": 12,
"1749886200000": 12,
"1749889800000": 12,
"1749893400000": 12,
"1749897000000": 12,
"1749900600000": 12,
"1749904200000": 9,
"1749907800000": 12,
"1749911400000": 12,
"1749915000000": 12,
"1749918600000": 12,
"1749922200000": 12,
"1749925800000": 12,
"1749929400000": 12,
"1749933000000": 12,
"1749936600000": 12,
"1749940200000": 12,
"1749943800000": 12,
"1749947400000": 12,
"1749951000000": 12,
"1749954600000": 12,
"1749958200000": 12,
"1749961800000": 12,
"1749965400000": 12,
"1749969000000": 12,
"1749972600000": 12,
"1749976200000": 12,
"1749979800000": 12,
"1749983400000": 12,
"1749987000000": 12,
"1749990600000": 12,
"1749994200000": 12,
"1749997800000": 12,
"1750001400000": 12,
"1750005000000": 12,
"1750008600000": 12,
"1750012200000": 12,
"1750015800000": 12,
"1750019400000": 12,
"1750023000000": 12,
"1750026600000": 12,
"1750030200000": 12,
"1750033800000": 12,
"1750037400000": 12,
"1750041000000": 12,
"1750044600000": 12,
"1750048200000": 12,
"1750051800000": 12,
"1750055400000": 12,
"1750059000000": 12,
"1750062600000": 12,
"1750066200000": 12,
"1750069800000": 12,
"1750073400000": 11,
"1750077000000": 4,
"1750080600000": 4,
"1750084200000": 12,
"1750087800000": 9
},
"remediations_signatures": [
"stop_using_http"
],
"has_remediations": true,
"latitude": null,
"longitude": null,
"location:info": {},
"location_source": null,
"_asset_kb_id": "",
"device_id": "3333333-33333333-3333333-3333333",
"vlan_id": []
}
{
"id": "000000000000-7143-4670-95da-7fe6e3735e6c",
"event_type": "assets",
"ip": [],
"os": "",
"name": "TEST_TEST-00000000",
"risk": 4.0,
"tags": [],
"time": 1753286752148,
"type": "sensor",
"level": "0",
"nodes": [
"TEST_TEST-00000000"
],
"roles": [
"other"
],
"zones": [
"Layer2"
],
"vendor": "",
"os:info": {
"source": "none"
},
"mobility": "static",
"lifecycle": "",
"protocols": [],
"type:info": {
"source": "passive"
},
"created_at": 1718016000000,
"mac_vendor": [],
"properties": {
"TEST_TEST-00000000": {
"_type.passive": "sensor",
"wireless_network": "lora_The Things Network",
"wireless_protocol": "lora",
"wireless_signal_snr": "9",
"wireless_signal_rssi": "-111",
"wireless_signal_noise": "-128",
"_wireless_mobility_info": "static",
"wireless_network_region": "World",
"wireless_signal_channel": "5",
"wireless_network_activation": "Over-The-Air Activation"
}
},
"mac_address": [],
"vendor:info": {
"source": "none"
},
"product_name": "",
"custom_fields": {},
"mobility:info": {
"source": "guardian-air",
"confidence": "high"
},
"serial_number": "",
"capture_device": "demo",
"is_ai_enriched": false,
"is_sp_enriched": false,
"is_ti_enriched": false,
"lifecycle:info": {
"source": "none"
},
"mobility_votes": {
"asset-kb": "static",
"guardian-air": "static"
},
"os_or_firmware": "",
"appliance_hosts": [
"Test test 000000000"
],
"is_arc_enriched": false,
"end_of_sale_date": "0",
"firmware_version": "",
"mac_address_level": {},
"product_name:info": {
"source": "none"
},
"record_created_at": 1753286752553,
"last_activity_time": 1753285200000,
"risk_configuration": {
"type_weight": 0.5,
"ai_risk_weight": 1,
"lifecycle_weight": 0.5,
"asset_criticality": 25,
"alerts_risk_weight": 0.5,
"device_risk_weight": 0.5,
"open_alerts_weight": 0.5,
"compensating_control": 0,
"high_risk_alert_level": 7,
"unsafe_countries_list": [
"china",
"russia",
"north korea",
"ukraine",
"vietnam",
"indonesia"
],
"unsafe_protocols_list": [
"ftp",
"http",
"imap",
"llmnr",
"ntlm",
"nfs",
"pop3",
"rdp",
"smb",
"snmp",
"smtp",
"sip",
"telnet"
],
"connection_type_weight": 0.5,
"risk_mitigation_factor": 0.0,
"high_risk_alerts_weight": 0.5,
"network_activity_weight": 0.5,
"unsafe_countries_weight": 0.5,
"unsafe_protocols_weight": 0.5,
"asset_criticality_factor": 0.0,
"asset_criticality_weight": 0.5,
"internet_exposure_weight": 0.5,
"communication_risk_weight": 0.5,
"technology_category_weight": 0.5,
"compensating_control_weight": 0.2,
"open_vulnerabilities_weight": 0.5,
"vulnerabilities_risk_weight": 0.5,
"suboptimal_management_weight": 0.5,
"critical_vulnerabilities_weight": 0.5,
"high_risk_vulnerabilities_level": 7,
"open_vulnerabilities_likelihood": 0.7,
"exploitable_vulnerabilities_weight": 0.5,
"exploitable_vulnerabilities_epss_score": 0.2
},
"serial_number:info": {
"source": "none"
},
"end_of_support_date": "0",
"os_or_firmware:info": {
"source": "none"
},
"technology_category": "IoT",
"end_of_sale_date:info": {
"source": "none"
},
"firmware_version:info": {
"source": "none"
},
"end_of_support_date:info": {
"source": "none"
},
"edge_id": "000000000-e63d-53ae-8e8e-85a210f79295",
"nozomi_risk": 4.0,
"activity_times": {
"1753284600000": 1
},
"remediations_signatures": [],
"has_remediations": false,
"latitude": null,
"longitude": null,
"location:info": {},
"location_source": null,
"_asset_kb_id": null,
"device_id": null,
"vlan_id": []
}
{
"cve": "CVE-2019-1684",
"probability": "Confirmed",
"score": "6.5",
"time": 1741954841522,
"status": "open",
"closed_time": 0,
"likelihood": "1.0",
"minimum_hotfix": null,
"latest_hotfix": null,
"matching_cpes": [
"cpe:/h:cisco:ip_phone_8811:-:-:-"
],
"summary": "A vulnerability in the Cisco Discovery Protocol or Link Layer Discovery Protocol (LLDP) implementation for the Cisco IP Phone 7800 and 8800 Series could allow an unauthenticated, adjacent attacker to cause an affected phone to reload unexpectedly, resulting in a temporary denial of service (DoS) condition. The vulnerability is due to missing length validation of certain Cisco Discovery Protocol or LLDP packet header fields. An attacker could exploit this vulnerability by sending a malicious Cisco Discovery Protocol or LLDP packet to the targeted phone. A successful exploit could allow the attacker to cause the affected phone to reload unexpectedly, resulting in a temporary DoS condition. Versions prior to 12.6(1)MN80 are affected.",
"category": "Improper Restriction of Operations within the Bounds of a Memory Buffer",
"references": [
{
"url": "https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20190220-cdp-lldp-dos",
"name": "20190220 Cisco IP Phone 7800 and 8800 Series Cisco Discovery Protocol and Link Layer Discovery Protocol Denial of Service Vulnerability",
"source": "CISCO",
"reference_type": "Vendor Advisory"
}
],
"is_kev": false,
"creation_time": 1550780940000,
"update_time": 1742458289562,
"source": null,
"resolution_status": "",
"epss_score": 0.00145,
"event_type": "vulnerabilities"
}
{
"name": "default",
"tags": [],
"time": 1750149053976,
"avg_snr": null,
"enabled": true,
"avg_rssi": -75,
"protocol": "bluetooth",
"avg_noise": null,
"created_at": "2025-06-17T08:30:54.003Z",
"properties": null,
"updated_at": "2025-06-17T08:30:54.003Z",
"edge_id": "1111111-11111111-111111111/bluetooth_default",
"inspect_privacy_macs": false,
"event_type": "wireless_networks"
}
Detection section
The following section provides information for those who wish to learn more about the detection capabilities enabled by collecting this intake. It includes details about the built-in rule catalog, event categories, and ECS fields extracted from raw events. This is essential for users aiming to create custom detection rules, perform hunting activities, or pivot in the events page.
Related Built-in Rules
The following Sekoia.io built-in rules match the intake Nozomi Vantage [BETA]. This documentation is updated automatically and is based solely on the fields used by the intake which are checked against our rules. This means that some rules will be listed but might not be relevant with the intake.
SEKOIA.IO x Nozomi Vantage [BETA] on ATT&CK Navigator
Cryptomining
Detection of domain names potentially related to cryptomining activities.
- Effort: master
Dynamic DNS Contacted
Detect communication with dynamic dns domain. This kind of domain is often used by attackers. This rule can trigger false positive in non-controlled environment because dynamic dns is not always malicious.
- Effort: master
Exfiltration Domain
Detects traffic toward a domain flagged as a possible exfiltration vector.
- Effort: master
Internet Scanner
Detects known scanner IP addresses. Alert is only raised when the scan hits an opened port, on TCP or UDP. This could be a very noisy rule, so be careful to check your detection perimeter before activation.
- Effort: master
Internet Scanner Target
Detects known scanner IP addresses. Alert is only raised when the scan hits an opened port, on TCP or UDP and group by target address. This could be a very noisy rule, so be careful to check your detection perimeter before activation.
- Effort: master
Remote Access Tool Domain
Detects traffic toward a domain flagged as a Remote Administration Tool (RAT).
- Effort: master
Remote Monitoring and Management Software - AnyDesk
Detect artifacts related to the installation or execution of the Remote Monitoring and Management tool AnyDesk.
- Effort: master
SEKOIA.IO Intelligence Feed
Detect threats based on indicators of compromise (IOCs) collected by SEKOIA's Threat and Detection Research team.
- Effort: elementary
Sekoia.io EICAR Detection
Detects observables in Sekoia.io CTI tagged as EICAR, which are fake samples meant to test detection.
- Effort: master
TOR Usage
Detects TOR usage, based on the IP address and the destination port (filtered on NTP). TOR is short for The Onion Router, and it gets its name from how it works. TOR intercepts the network traffic from one or more apps on user’s computer, usually the user web browser, and shuffles it through a number of randomly-chosen computers before passing it on to its destination. This disguises user location, and makes it harder for servers to pick him/her out on repeat visits, or to tie together separate visits to different sites, this making tracking and surveillance more difficult. Before a network packet starts its journey, user’s computer chooses a random list of relays and repeatedly encrypts the data in multiple layers, like an onion. Each relay knows only enough to strip off the outermost layer of encryption, before passing what’s left on to the next relay in the list.
- Effort: master
TOR Usage Generic Rule
Detects TOR usage globally, whether the IP is a destination or source. TOR is short for The Onion Router, and it gets its name from how it works. TOR intercepts the network traffic from one or more apps on user’s computer, usually the user web browser, and shuffles it through a number of randomly-chosen computers before passing it on to its destination. This disguises user location, and makes it harder for servers to pick him/her out on repeat visits, or to tie together separate visits to different sites, this making tracking and surveillance more difficult. Before a network packet starts its journey, user’s computer chooses a random list of relays and repeatedly encrypts the data in multiple layers, like an onion. Each relay knows only enough to strip off the outermost layer of encryption, before passing what’s left on to the next relay in the list.
- Effort: master
Event Categories
The following table lists the data source offered by this integration.
| Data Source | Description |
|---|---|
Network device logs |
None |
In details, the following table denotes the type of events produced by this integration.
| Name | Values |
|---|---|
| Kind | `` |
| Category | `` |
| Type | info |
Transformed Events Samples after Ingestion
This section demonstrates how the raw logs will be transformed by our parsers. It shows the extracted fields that will be available for use in the built-in detection rules and hunting activities in the events page. Understanding these transformations is essential for analysts to create effective detection mechanisms with custom detection rules and to leverage the full potential of the collected data.
{
"message": "{\"event_type\":\"alerts\",\"id\":\"111111-111111-11111111\",\"ack\":false,\"_can\":{\"trace_requests\":true,\"close_learn_alerts\":false,\"security_control_panel.tuning\":true},\"name\":\"Program change\",\"note\":null,\"time\":1750085403336,\"id_dst\":\"1.2.3.125\",\"id_src\":\"1.2.3.58\",\"ip_dst\":\"1.2.3.125\",\"ip_src\":\"1.2.3.58\",\"status\":\"open\",\"counter\":1,\"mac_dst\":\"f4:22:11:33:44:55\",\"mac_src\":\"00:11:22:33:44:be\",\"parents\":[],\"uid_dst\":\"222222-222222-22222-22222\",\"uid_src\":\"333333-33333-333333-33333\",\"port_dst\":44818,\"port_src\":58679,\"protocol\":\"ethernetip\",\"severity\":10,\"zone_dst\":\"Production_B\",\"zone_src\":\"Production_B\",\"dst_roles\":\"producer\",\"label_dst\":null,\"label_src\":null,\"src_roles\":\"consumer, engineering_station\",\"ti_source\":\"\",\"type_name\":\"Program change\",\"types_dst\":[\"OT_device\"],\"types_src\":[\"computer\"],\"alert_info\":{},\"bpf_filter\":\"(ip host 1.2.3.58 and ip host 1.2.3.125 and tcp port 58679 and tcp port 44818) or (vlan and ip host 1.2.3.58 and ip host 1.2.3.125 and tcp port 58679 and tcp port 44818)\",\"levels_dst\":[\"2\"],\"levels_src\":[\"2\"],\"properties\":{\"to_id\":\"1.2.3.125\",\"from_id\":\"1.2.3.58\",\"base_risk\":6,\"raised_by\":\"n2os_ids\",\"n2os_version\":\"25.1.0-05290909_263B4\",\"is_dst_public\":false,\"is_src_public\":false,\"is_dst_node_learned\":true,\"is_src_node_learned\":true,\"mitre_attack_for_ics\":{\"source\":{\"types\":[\"Engineering Workstation\"],\"levels\":[\"2\"]},\"destination\":{\"types\":[\"Field Controller/RTU/PLC/IED\"],\"levels\":[\"2\"]}},\"is_dst_reputation_bad\":false,\"is_src_reputation_bad\":false},\"closed_time\":0,\"description\":\"Online edits have been made on the PLC with IP 1.2.3.125. The following steps were executed:\\n[1]- Changed Controller [ C1_1756 ] to Run Mode\\n[2]- Changed Controller [ C1_1756 ] to Program Mode\\n[3]- Downloaded project [ C:\\\\USERS\\\\NOZOMI\\\\DESKTOP\\\\LADDERBOMB\\\\PLC_LOGIC_CHALLENGE2\\\\challenge2changed.ACD ] to [ \\\\AB_ETHIP-1\\\\1.2.3.125\\\\C1_1756 ]\\n[4]- Changed Controller [ C1_1756 ] to Run Mode\\n[5]- Changed Controller [ C1_1756 ] to Program Mode\\n[6]- Downloaded project [ C:\\\\USERS\\\\NOZOMI\\\\DESKTOP\\\\LADDERBOMB\\\\PLC_LOGIC_CHALLENGE2\\\\challenge2changed.ACD ] to [ \\\\AB_ETHIP-1\\\\1.2.3.125\\\\C1_1756 ]\\n[7]- Changed Controller [ C1_1756 ] to Run Mode\\n[8]- Changed Controller [ C1_1756 ] to Program Mode\\n[9]- Downloaded project [ C:\\\\USERS\\\\NOZOMI\\\\DESKTOP\\\\LADDERBOMB\\\\PLC_LOGIC_CHALLENGE2\\\\challenge2changed.ACD ] to [ \\\\AB_ETHIP-1\\\\1.2.3.125\\\\C1_1756 ]\\n[10]- Changed Controller [ C1_1756 ] to Run Mode\\n\",\"is_incident\":false,\"is_security\":true,\"threat_name\":\"\",\"created_time\":1750085403336,\"trigger_type\":null,\"incident_keys\":[],\"appliance_host\":\"Sandbox-TAE-Guardian3\",\"capture_device\":\"base.pcap\",\"physical_links\":null,\"grouped_visible\":true,\"assertion_source\":\"\",\"custom_fields_dst\":{},\"custom_fields_src\":{},\"playbook_contents\":null,\"transport_protocol\":\"tcp\",\"sec_profile_visible\":true,\"mitre_attack_tactics\":null,\"additional_description\":{},\"mitre_attack_techniques\":null,\"edge_id\":\"111111-111111-11111111\",\"risk\":6,\"trace_status\":null,\"trace_sha1\":null,\"record_created_at\":1750085573483,\"type_id\":\"SIGN:PROGRAM:CHANGE\",\"trigger_id\":null}",
"event": {
"action": "Program change",
"dataset": "alerts",
"kind": "alert",
"reason": "Online edits have been made on the PLC with IP 1.2.3.125. The following steps were executed:\n[1]- Changed Controller [ C1_1756 ] to Run Mode\n[2]- Changed Controller [ C1_1756 ] to Program Mode\n[3]- Downloaded project [ C:\\USERS\\NOZOMI\\DESKTOP\\LADDERBOMB\\PLC_LOGIC_CHALLENGE2\\challenge2changed.ACD ] to [ \\AB_ETHIP-1\\1.2.3.125\\C1_1756 ]\n[4]- Changed Controller [ C1_1756 ] to Run Mode\n[5]- Changed Controller [ C1_1756 ] to Program Mode\n[6]- Downloaded project [ C:\\USERS\\NOZOMI\\DESKTOP\\LADDERBOMB\\PLC_LOGIC_CHALLENGE2\\challenge2changed.ACD ] to [ \\AB_ETHIP-1\\1.2.3.125\\C1_1756 ]\n[7]- Changed Controller [ C1_1756 ] to Run Mode\n[8]- Changed Controller [ C1_1756 ] to Program Mode\n[9]- Downloaded project [ C:\\USERS\\NOZOMI\\DESKTOP\\LADDERBOMB\\PLC_LOGIC_CHALLENGE2\\challenge2changed.ACD ] to [ \\AB_ETHIP-1\\1.2.3.125\\C1_1756 ]\n[10]- Changed Controller [ C1_1756 ] to Run Mode\n",
"severity": 10,
"type": [
"info"
]
},
"@timestamp": "2025-06-16T14:50:03.336000Z",
"destination": {
"address": "1.2.3.125",
"geo": {
"name": "Production_B"
},
"ip": "1.2.3.125",
"mac": "f4:22:11:33:44:55",
"port": 44818
},
"network": {
"protocol": "ethernetip",
"transport": "tcp"
},
"nozomi": {
"vantage": {
"alert": {
"ack": false,
"bpf_filter": "(ip host 1.2.3.58 and ip host 1.2.3.125 and tcp port 58679 and tcp port 44818) or (vlan and ip host 1.2.3.58 and ip host 1.2.3.125 and tcp port 58679 and tcp port 44818)",
"destination": {
"is_node_learned": true,
"is_public": false,
"is_reputation_bad": false,
"levels": [
"2"
],
"roles": [
"producer"
],
"types": [
"OT_device"
],
"uuid": "222222-222222-22222-22222"
},
"edge_id": "111111-111111-11111111",
"is_incident": false,
"is_security": true,
"source": {
"is_node_learned": true,
"is_public": false,
"is_reputation_bad": false,
"levels": [
"2"
],
"roles": [
"consumer",
"engineering_station"
],
"types": [
"computer"
],
"uuid": "333333-33333-333333-33333"
},
"status": "open",
"type": "SIGN:PROGRAM:CHANGE"
}
}
},
"observer": {
"name": "Sandbox-TAE-Guardian3"
},
"related": {
"ip": [
"1.2.3.125",
"1.2.3.58"
]
},
"source": {
"address": "1.2.3.58",
"geo": {
"name": "Production_B"
},
"ip": "1.2.3.58",
"mac": "00:11:22:33:44:be",
"port": 58679
},
"threat": {
"indicator": {
"description": "Online edits have been made on the PLC with IP 1.2.3.125. The following steps were executed:\n[1]- Changed Controller [ C1_1756 ] to Run Mode\n[2]- Changed Controller [ C1_1756 ] to Program Mode\n[3]- Downloaded project [ C:\\USERS\\NOZOMI\\DESKTOP\\LADDERBOMB\\PLC_LOGIC_CHALLENGE2\\challenge2changed.ACD ] to [ \\AB_ETHIP-1\\1.2.3.125\\C1_1756 ]\n[4]- Changed Controller [ C1_1756 ] to Run Mode\n[5]- Changed Controller [ C1_1756 ] to Program Mode\n[6]- Downloaded project [ C:\\USERS\\NOZOMI\\DESKTOP\\LADDERBOMB\\PLC_LOGIC_CHALLENGE2\\challenge2changed.ACD ] to [ \\AB_ETHIP-1\\1.2.3.125\\C1_1756 ]\n[7]- Changed Controller [ C1_1756 ] to Run Mode\n[8]- Changed Controller [ C1_1756 ] to Program Mode\n[9]- Downloaded project [ C:\\USERS\\NOZOMI\\DESKTOP\\LADDERBOMB\\PLC_LOGIC_CHALLENGE2\\challenge2changed.ACD ] to [ \\AB_ETHIP-1\\1.2.3.125\\C1_1756 ]\n[10]- Changed Controller [ C1_1756 ] to Run Mode\n"
}
}
}
{
"message": "{\"event_type\": \"assets\",\"ip\":[\"1.2.3.4\"],\"os\":\"Windows\",\"name\":\"Desktop/Laptop Computer\",\"time\":1750088529631,\"type\":\"computer\",\"level\":\"1\",\"nodes\":[\"1.2.3.4\"],\"roles\":[\"other\"],\"zones\":[\"Substation\"],\"fields\":{},\"vendor\":\"Dell\",\"os:info\":{\"source\":\"passive\"},\"lifecycle\":\"\",\"protocols\":[\"http\",\"keyence\"],\"type:info\":{\"source\":\"passive\"},\"created_at\":1724888822747,\"mac_vendor\":[\"Test mac vendor\"],\"nodes_uids\":[\"111111111-111111-1111111\"],\"properties\":{\"1.2.3.4\":{\"_type.passive\":\"computer\",\"_type.enrichment\":\"computer\",\"_vendor.enrichment\":\"Dell\",\"_type.passive.unknown\":\"computer\",\"_product_name.enrichment\":\"Desktop/Laptop Computer\",\"_type.enrichment.unknown\":\"computer\",\"http.last_client_version\":\"Chrome 91.0.4472.124\",\"_vendor.enrichment.unknown\":\"Dell\",\"_product_name.enrichment.unknown\":\"Desktop/Laptop Computer\"}},\"arc_version\":\"\",\"mac_address\":[\"00:11:22:33:44:55\"],\"vendor:info\":{\"source\":\"enrichment\",\"confidence\":\"low\",\"granularity\":\"generic\"},\"product_name\":\"Desktop/Laptop Computer\",\"custom_fields\":{},\"serial_number\":\"\",\"capture_device\":\"base.pcap\",\"is_ai_enriched\":true,\"is_sp_enriched\":false,\"is_ti_enriched\":true,\"lifecycle:info\":{\"source\":\"none\"},\"os_or_firmware\":\"Windows\",\"appliance_hosts\":[\"Sandbox-TAE-Guardian1\"],\"is_arc_enriched\":false,\"end_of_sale_date\":0,\"firmware_version\":\"\",\"mac_address_level\":{\"00:11:22:33:44:55\":\"unconfirmed\"},\"product_name:info\":{\"source\":\"enrichment\",\"confidence\":\"low\",\"granularity\":\"generic\"},\"last_activity_time\":1750088403014,\"serial_number:info\":{\"source\":\"none\"},\"end_of_support_date\":0,\"os_or_firmware:info\":{\"source\":\"passive\"},\"technology_category\":\"IT\",\"end_of_sale_date:info\":{\"source\":\"none\"},\"firmware_version:info\":{\"source\":\"none\"},\"end_of_support_date:info\":{\"source\":\"none\"},\"edge_id\":\"222222-2222222-22222222-222222\",\"risk\":9,\"record_created_at\":1741874120458,\"mobility:info\":{},\"mobility\":null,\"mobility_votes\":{\"asset-kb\":\"unknown\"},\"risk_configuration\":{\"type_weight\":0.5,\"ai_risk_weight\":1,\"lifecycle_weight\":0.5,\"asset_criticality\":25,\"alerts_risk_weight\":0.5,\"device_risk_weight\":0.5,\"open_alerts_weight\":0.5,\"compensating_control\":0,\"high_risk_alert_level\":7,\"unsafe_countries_list\":[\"china\",\"russia\",\"north korea\",\"ukraine\",\"vietnam\",\"indonesia\"],\"unsafe_protocols_list\":[\"ftp\",\"http\",\"imap\",\"llmnr\",\"ntlm\",\"nfs\",\"pop3\",\"rdp\",\"smb\",\"snmp\",\"smtp\",\"sip\",\"telnet\"],\"connection_type_weight\":0.5,\"risk_mitigation_factor\":0,\"high_risk_alerts_weight\":0.5,\"network_activity_weight\":0.5,\"unsafe_countries_weight\":0.5,\"unsafe_protocols_weight\":0.5,\"asset_criticality_factor\":0,\"asset_criticality_weight\":0.5,\"internet_exposure_weight\":0.5,\"communication_risk_weight\":0.5,\"technology_category_weight\":0.5,\"compensating_control_weight\":0.2,\"open_vulnerabilities_weight\":0.5,\"vulnerabilities_risk_weight\":0.5,\"suboptimal_management_weight\":0.5,\"critical_vulnerabilities_weight\":0.5,\"high_risk_vulnerabilities_level\":7,\"open_vulnerabilities_likelihood\":0.7,\"exploitable_vulnerabilities_weight\":0.5,\"exploitable_vulnerabilities_epss_score\":0.2},\"nozomi_risk\":9,\"activity_times\":{\"1749400200000\":12,\"1749403800000\":11,\"1749407400000\":11,\"1749411000000\":12,\"1749414600000\":10,\"1749418200000\":10,\"1749421800000\":8,\"1749425400000\":12,\"1749429000000\":12,\"1749432600000\":10,\"1749436200000\":11,\"1749439800000\":8,\"1749443400000\":12,\"1749447000000\":10,\"1749450600000\":12,\"1749454200000\":8,\"1749457800000\":12,\"1749461400000\":11,\"1749465000000\":12,\"1749468600000\":12,\"1749472200000\":12,\"1749475800000\":12,\"1749479400000\":12,\"1749483000000\":12,\"1749486600000\":12,\"1749490200000\":12,\"1749493800000\":12,\"1749497400000\":12,\"1749501000000\":12,\"1749504600000\":12,\"1749508200000\":12,\"1749511800000\":12,\"1749515400000\":12,\"1749519000000\":11,\"1749522600000\":12,\"1749526200000\":11,\"1749529800000\":10,\"1749533400000\":11,\"1749537000000\":11,\"1749540600000\":12,\"1749544200000\":12,\"1749547800000\":12,\"1749551400000\":10,\"1749555000000\":9,\"1749558600000\":10,\"1749562200000\":12,\"1749565800000\":12,\"1749569400000\":11,\"1749573000000\":12,\"1749576600000\":12,\"1749580200000\":12,\"1749583800000\":12,\"1749587400000\":12,\"1749591000000\":12,\"1749594600000\":12,\"1749598200000\":12,\"1749601800000\":12,\"1749605400000\":12,\"1749609000000\":12,\"1749612600000\":12,\"1749616200000\":12,\"1749619800000\":12,\"1749623400000\":12,\"1749627000000\":12,\"1749630600000\":12,\"1749634200000\":12,\"1749637800000\":12,\"1749641400000\":12,\"1749645000000\":12,\"1749648600000\":12,\"1749652200000\":12,\"1749655800000\":12,\"1749659400000\":12,\"1749663000000\":12,\"1749666600000\":12,\"1749670200000\":12,\"1749673800000\":12,\"1749677400000\":12,\"1749681000000\":12,\"1749684600000\":12,\"1749688200000\":12,\"1749691800000\":12,\"1749695400000\":12,\"1749699000000\":12,\"1749702600000\":12,\"1749706200000\":12,\"1749709800000\":12,\"1749713400000\":12,\"1749717000000\":12,\"1749720600000\":12,\"1749724200000\":12,\"1749727800000\":12,\"1749731400000\":12,\"1749735000000\":12,\"1749738600000\":12,\"1749742200000\":12,\"1749745800000\":12,\"1749749400000\":12,\"1749753000000\":12,\"1749756600000\":12,\"1749760200000\":12,\"1749763800000\":12,\"1749767400000\":12,\"1749771000000\":12,\"1749774600000\":12,\"1749778200000\":12,\"1749781800000\":12,\"1749785400000\":12,\"1749789000000\":12,\"1749792600000\":12,\"1749796200000\":12,\"1749799800000\":12,\"1749803400000\":12,\"1749807000000\":12,\"1749810600000\":12,\"1749814200000\":12,\"1749817800000\":12,\"1749821400000\":12,\"1749825000000\":12,\"1749828600000\":12,\"1749832200000\":12,\"1749835800000\":12,\"1749839400000\":12,\"1749843000000\":12,\"1749846600000\":12,\"1749850200000\":12,\"1749853800000\":12,\"1749857400000\":12,\"1749861000000\":12,\"1749864600000\":12,\"1749868200000\":12,\"1749871800000\":12,\"1749875400000\":12,\"1749879000000\":12,\"1749882600000\":12,\"1749886200000\":12,\"1749889800000\":12,\"1749893400000\":12,\"1749897000000\":12,\"1749900600000\":12,\"1749904200000\":9,\"1749907800000\":12,\"1749911400000\":12,\"1749915000000\":12,\"1749918600000\":12,\"1749922200000\":12,\"1749925800000\":12,\"1749929400000\":12,\"1749933000000\":12,\"1749936600000\":12,\"1749940200000\":12,\"1749943800000\":12,\"1749947400000\":12,\"1749951000000\":12,\"1749954600000\":12,\"1749958200000\":12,\"1749961800000\":12,\"1749965400000\":12,\"1749969000000\":12,\"1749972600000\":12,\"1749976200000\":12,\"1749979800000\":12,\"1749983400000\":12,\"1749987000000\":12,\"1749990600000\":12,\"1749994200000\":12,\"1749997800000\":12,\"1750001400000\":12,\"1750005000000\":12,\"1750008600000\":12,\"1750012200000\":12,\"1750015800000\":12,\"1750019400000\":12,\"1750023000000\":12,\"1750026600000\":12,\"1750030200000\":12,\"1750033800000\":12,\"1750037400000\":12,\"1750041000000\":12,\"1750044600000\":12,\"1750048200000\":12,\"1750051800000\":12,\"1750055400000\":12,\"1750059000000\":12,\"1750062600000\":12,\"1750066200000\":12,\"1750069800000\":12,\"1750073400000\":11,\"1750077000000\":4,\"1750080600000\":4,\"1750084200000\":12,\"1750087800000\":9},\"remediations_signatures\":[\"stop_using_http\"],\"has_remediations\":true,\"latitude\":null,\"longitude\":null,\"location:info\":{},\"location_source\":null,\"_asset_kb_id\":\"\",\"device_id\":\"3333333-33333333-3333333-3333333\",\"vlan_id\":[]}",
"event": {
"category": [
"host"
],
"dataset": "assets",
"kind": "asset",
"type": [
"info"
]
},
"@timestamp": "2025-06-16T15:42:09.631000Z",
"device": {
"id": "3333333-33333333-3333333-3333333",
"manufacturer": "Dell",
"model": {
"name": "Desktop/Laptop Computer"
}
},
"host": {
"ip": [
"1.2.3.4"
],
"mac": [
"00:11:22:33:44:55"
],
"name": "Desktop/Laptop Computer",
"os": {
"platform": "windows"
},
"type": "computer"
},
"related": {
"ip": [
"1.2.3.4"
]
}
}
{
"message": "{\"id\":\"000000000000-7143-4670-95da-7fe6e3735e6c\",\"event_type\":\"assets\",\"ip\":[],\"os\":\"\",\"name\":\"TEST_TEST-00000000\",\"risk\":4.0,\"tags\":[],\"time\":1753286752148,\"type\":\"sensor\",\"level\":\"0\",\"nodes\":[\"TEST_TEST-00000000\"],\"roles\":[\"other\"],\"zones\":[\"Layer2\"],\"vendor\":\"\",\"os:info\":{\"source\":\"none\"},\"mobility\":\"static\",\"lifecycle\":\"\",\"protocols\":[],\"type:info\":{\"source\":\"passive\"},\"created_at\":1718016000000,\"mac_vendor\":[],\"properties\":{\"TEST_TEST-00000000\":{\"_type.passive\":\"sensor\",\"wireless_network\":\"lora_The Things Network\",\"wireless_protocol\":\"lora\",\"wireless_signal_snr\":\"9\",\"wireless_signal_rssi\":\"-111\",\"wireless_signal_noise\":\"-128\",\"_wireless_mobility_info\":\"static\",\"wireless_network_region\":\"World\",\"wireless_signal_channel\":\"5\",\"wireless_network_activation\":\"Over-The-Air Activation\"}},\"mac_address\":[],\"vendor:info\":{\"source\":\"none\"},\"product_name\":\"\",\"custom_fields\":{},\"mobility:info\":{\"source\":\"guardian-air\",\"confidence\":\"high\"},\"serial_number\":\"\",\"capture_device\":\"demo\",\"is_ai_enriched\":false,\"is_sp_enriched\":false,\"is_ti_enriched\":false,\"lifecycle:info\":{\"source\":\"none\"},\"mobility_votes\":{\"asset-kb\":\"static\",\"guardian-air\":\"static\"},\"os_or_firmware\":\"\",\"appliance_hosts\":[\"Test test 000000000\"],\"is_arc_enriched\":false,\"end_of_sale_date\":\"0\",\"firmware_version\":\"\",\"mac_address_level\":{},\"product_name:info\":{\"source\":\"none\"},\"record_created_at\":1753286752553,\"last_activity_time\":1753285200000,\"risk_configuration\":{\"type_weight\":0.5,\"ai_risk_weight\":1,\"lifecycle_weight\":0.5,\"asset_criticality\":25,\"alerts_risk_weight\":0.5,\"device_risk_weight\":0.5,\"open_alerts_weight\":0.5,\"compensating_control\":0,\"high_risk_alert_level\":7,\"unsafe_countries_list\":[\"china\",\"russia\",\"north korea\",\"ukraine\",\"vietnam\",\"indonesia\"],\"unsafe_protocols_list\":[\"ftp\",\"http\",\"imap\",\"llmnr\",\"ntlm\",\"nfs\",\"pop3\",\"rdp\",\"smb\",\"snmp\",\"smtp\",\"sip\",\"telnet\"],\"connection_type_weight\":0.5,\"risk_mitigation_factor\":0.0,\"high_risk_alerts_weight\":0.5,\"network_activity_weight\":0.5,\"unsafe_countries_weight\":0.5,\"unsafe_protocols_weight\":0.5,\"asset_criticality_factor\":0.0,\"asset_criticality_weight\":0.5,\"internet_exposure_weight\":0.5,\"communication_risk_weight\":0.5,\"technology_category_weight\":0.5,\"compensating_control_weight\":0.2,\"open_vulnerabilities_weight\":0.5,\"vulnerabilities_risk_weight\":0.5,\"suboptimal_management_weight\":0.5,\"critical_vulnerabilities_weight\":0.5,\"high_risk_vulnerabilities_level\":7,\"open_vulnerabilities_likelihood\":0.7,\"exploitable_vulnerabilities_weight\":0.5,\"exploitable_vulnerabilities_epss_score\":0.2},\"serial_number:info\":{\"source\":\"none\"},\"end_of_support_date\":\"0\",\"os_or_firmware:info\":{\"source\":\"none\"},\"technology_category\":\"IoT\",\"end_of_sale_date:info\":{\"source\":\"none\"},\"firmware_version:info\":{\"source\":\"none\"},\"end_of_support_date:info\":{\"source\":\"none\"},\"edge_id\":\"000000000-e63d-53ae-8e8e-85a210f79295\",\"nozomi_risk\":4.0,\"activity_times\":{\"1753284600000\":1},\"remediations_signatures\":[],\"has_remediations\":false,\"latitude\":null,\"longitude\":null,\"location:info\":{},\"location_source\":null,\"_asset_kb_id\":null,\"device_id\":null,\"vlan_id\":[]}",
"event": {
"category": [
"host"
],
"dataset": "assets",
"kind": "asset",
"type": [
"info"
]
},
"@timestamp": "2025-07-23T16:05:52.148000Z",
"host": {
"name": "TEST_TEST-00000000",
"type": "sensor"
}
}
{
"message": "{\n\"cve\": \"CVE-2019-1684\",\n\"probability\": \"Confirmed\",\n\"score\": \"6.5\",\n\"time\": 1741954841522,\n\"status\": \"open\",\n\"closed_time\": 0,\n\"likelihood\": \"1.0\",\n\"minimum_hotfix\": null,\n\"latest_hotfix\": null,\n\"matching_cpes\": [\n\"cpe:/h:cisco:ip_phone_8811:-:-:-\"\n],\n\"summary\": \"A vulnerability in the Cisco Discovery Protocol or Link Layer Discovery Protocol (LLDP) implementation for the Cisco IP Phone 7800 and 8800 Series could allow an unauthenticated, adjacent attacker to cause an affected phone to reload unexpectedly, resulting in a temporary denial of service (DoS) condition. The vulnerability is due to missing length validation of certain Cisco Discovery Protocol or LLDP packet header fields. An attacker could exploit this vulnerability by sending a malicious Cisco Discovery Protocol or LLDP packet to the targeted phone. A successful exploit could allow the attacker to cause the affected phone to reload unexpectedly, resulting in a temporary DoS condition. Versions prior to 12.6(1)MN80 are affected.\",\n\"category\": \"Improper Restriction of Operations within the Bounds of a Memory Buffer\",\n\"references\": [\n{\n\"url\": \"https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20190220-cdp-lldp-dos\",\n\"name\": \"20190220 Cisco IP Phone 7800 and 8800 Series Cisco Discovery Protocol and Link Layer Discovery Protocol Denial of Service Vulnerability\",\n\"source\": \"CISCO\",\n\"reference_type\": \"Vendor Advisory\"\n}\n],\n\"is_kev\": false,\n\"creation_time\": 1550780940000,\n\"update_time\": 1742458289562,\n\"source\": null,\n\"resolution_status\": \"\",\n\"epss_score\": 0.00145,\"event_type\": \"vulnerabilities\"}",
"event": {
"category": [
"vulnerability"
],
"dataset": "vulnerabilities",
"reason": "Improper Restriction of Operations within the Bounds of a Memory Buffer",
"type": [
"info"
]
},
"@timestamp": "2025-03-14T12:20:41.522000Z",
"nozomi": {
"vantage": {
"vulnerability": {
"cpes": [
"cpe:/h:cisco:ip_phone_8811:-:-:-"
],
"created": "1550780940000",
"epss_score": 0.00145,
"is_kev": false,
"probability": "Confirmed",
"status": "open",
"updated": "2025-03-20T08:11:29.562000Z"
}
}
},
"vulnerability": {
"description": "A vulnerability in the Cisco Discovery Protocol or Link Layer Discovery Protocol (LLDP) implementation for the Cisco IP Phone 7800 and 8800 Series could allow an unauthenticated, adjacent attacker to cause an affected phone to reload unexpectedly, resulting in a temporary denial of service (DoS) condition. The vulnerability is due to missing length validation of certain Cisco Discovery Protocol or LLDP packet header fields. An attacker could exploit this vulnerability by sending a malicious Cisco Discovery Protocol or LLDP packet to the targeted phone. A successful exploit could allow the attacker to cause the affected phone to reload unexpectedly, resulting in a temporary DoS condition. Versions prior to 12.6(1)MN80 are affected.",
"enumeration": "CVE",
"id": "CVE-2019-1684",
"reference": "https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20190220-cdp-lldp-dos",
"score": {
"environmental": 6.5
}
}
}
{
"message": "{\n\"name\": \"default\",\n\"tags\": [],\n\"time\": 1750149053976,\n\"avg_snr\": null,\n\"enabled\": true,\n\"avg_rssi\": -75,\n\"protocol\": \"bluetooth\",\n\"avg_noise\": null,\n\"created_at\": \"2025-06-17T08:30:54.003Z\",\n\"properties\": null,\n\"updated_at\": \"2025-06-17T08:30:54.003Z\",\n\"edge_id\": \"1111111-11111111-111111111/bluetooth_default\",\n\"inspect_privacy_macs\": false, \"event_type\": \"wireless_networks\"}",
"event": {
"category": [
"network"
],
"dataset": "wireless_networks",
"type": [
"info"
]
},
"@timestamp": "2025-06-17T08:30:53.976000Z",
"network": {
"name": "default",
"protocol": "bluetooth"
},
"nozomi": {
"vantage": {
"wireless": {
"average_rssi": "-75",
"created": "2025-06-17T08:30:54.003Z",
"edge_id": "1111111-11111111-111111111/bluetooth_default",
"enabled": true,
"inspect_privacy_macs": false,
"updated": "2025-06-17T08:30:54.003Z"
}
}
}
}
Extracted Fields
The following table lists the fields that are extracted, normalized under the ECS format, analyzed and indexed by the parser. It should be noted that infered fields are not listed.
| Name | Type | Description |
|---|---|---|
@timestamp |
date |
Date/time when the event originated. |
destination.geo.name |
keyword |
User-defined description of a location. |
destination.ip |
ip |
IP address of the destination. |
destination.mac |
keyword |
MAC address of the destination. |
destination.port |
long |
Port of the destination. |
event.action |
keyword |
The action captured by the event. |
event.dataset |
keyword |
Name of the dataset. |
event.reason |
keyword |
Reason why this event happened, according to the source |
event.severity |
long |
Numeric severity of the event. |
event.type |
keyword |
Event type. The third categorization field in the hierarchy. |
host.ip |
ip |
Host ip addresses. |
host.mac |
keyword |
Host MAC addresses. |
host.name |
keyword |
Name of the host. |
host.os.platform |
keyword |
Operating system platform (such centos, ubuntu, windows). |
host.type |
keyword |
Type of host. |
network.name |
keyword |
Name given by operators to sections of their network. |
network.protocol |
keyword |
Application protocol name. |
network.transport |
keyword |
Protocol Name corresponding to the field iana_number. |
nozomi.vantage.alert.ack |
boolean |
|
nozomi.vantage.alert.bpf_filter |
keyword |
|
nozomi.vantage.alert.destination.is_node_learned |
boolean |
|
nozomi.vantage.alert.destination.is_public |
boolean |
|
nozomi.vantage.alert.destination.is_reputation_bad |
boolean |
|
nozomi.vantage.alert.destination.label |
keyword |
|
nozomi.vantage.alert.destination.levels |
array |
|
nozomi.vantage.alert.destination.roles |
array |
|
nozomi.vantage.alert.destination.types |
array |
|
nozomi.vantage.alert.destination.uuid |
keyword |
|
nozomi.vantage.alert.edge_id |
keyword |
|
nozomi.vantage.alert.is_incident |
boolean |
|
nozomi.vantage.alert.is_security |
boolean |
|
nozomi.vantage.alert.source.is_node_learned |
boolean |
|
nozomi.vantage.alert.source.is_public |
boolean |
|
nozomi.vantage.alert.source.is_reputation_bad |
boolean |
|
nozomi.vantage.alert.source.label |
keyword |
|
nozomi.vantage.alert.source.levels |
array |
|
nozomi.vantage.alert.source.roles |
array |
|
nozomi.vantage.alert.source.types |
array |
|
nozomi.vantage.alert.source.uuid |
keyword |
|
nozomi.vantage.alert.status |
keyword |
|
nozomi.vantage.alert.type |
keyword |
|
nozomi.vantage.vulnerability.cpes |
array |
|
nozomi.vantage.vulnerability.created |
keyword |
|
nozomi.vantage.vulnerability.epss_score |
float |
|
nozomi.vantage.vulnerability.is_kev |
boolean |
|
nozomi.vantage.vulnerability.probability |
keyword |
|
nozomi.vantage.vulnerability.status |
keyword |
|
nozomi.vantage.vulnerability.updated |
keyword |
|
nozomi.vantage.wireless.average_noise |
keyword |
|
nozomi.vantage.wireless.average_rssi |
keyword |
|
nozomi.vantage.wireless.average_snr |
keyword |
|
nozomi.vantage.wireless.created |
keyword |
|
nozomi.vantage.wireless.edge_id |
keyword |
|
nozomi.vantage.wireless.enabled |
boolean |
|
nozomi.vantage.wireless.inspect_privacy_macs |
boolean |
|
nozomi.vantage.wireless.properties |
keyword |
|
nozomi.vantage.wireless.updated |
keyword |
|
observer.name |
keyword |
Custom name of the observer. |
source.geo.name |
keyword |
User-defined description of a location. |
source.ip |
ip |
IP address of the source. |
source.mac |
keyword |
MAC address of the source. |
source.port |
long |
Port of the source. |
threat.indicator.description |
keyword |
Indicator description |
vulnerability.description |
keyword |
Description of the vulnerability. |
vulnerability.enumeration |
keyword |
Identifier of the vulnerability. |
vulnerability.id |
keyword |
ID of the vulnerability. |
vulnerability.reference |
keyword |
Reference of the vulnerability. |
vulnerability.score.environmental |
float |
Vulnerability Environmental score. |
For more information on the Intake Format, please find the code of the Parser, Smart Descriptions, and Supported Events here.