Security Scorecard Vunerability Assessment Scanner
Overview
SecurityScorecard's Vulnerability Assessment Scanner is a tool designed to identify and assess vulnerabilities in an organization's digital infrastructure, offering real-time insights and prioritized recommendations to strengthen security measures and reduce cyber risk.
- Vendor: SecurityScorecard
- Supported environment: SaaS
- Detection based on: Alert
- Supported application or feature: Application logs
Configure
This setup guide will show you how to provide an integration between Security Scorecard Vunerability Assessment Scanner events and Sekoia.io.
Create an intake
Go to the intake page and create a new intake from the format Security Scorecard VAS. Copy the intake key.
Configure Security Scorecard
-
Login to admin panel and go to
Rule Buildertab.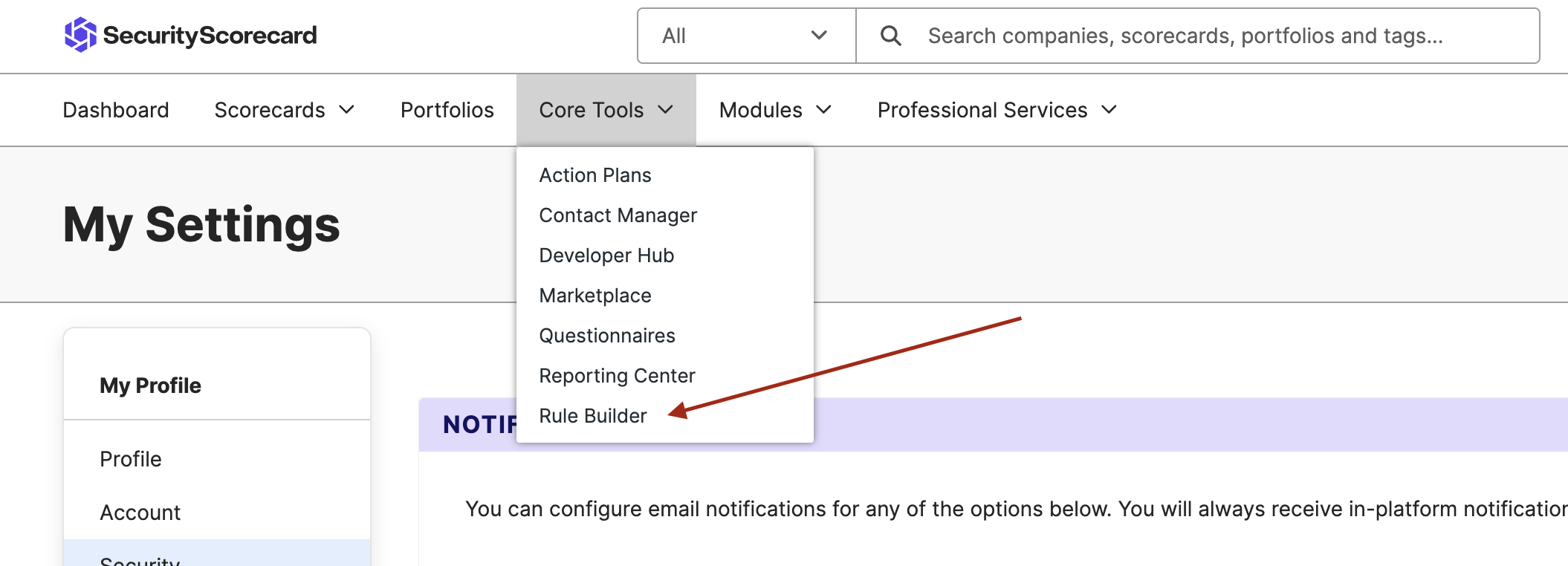
-
Click
Create Rulebutton.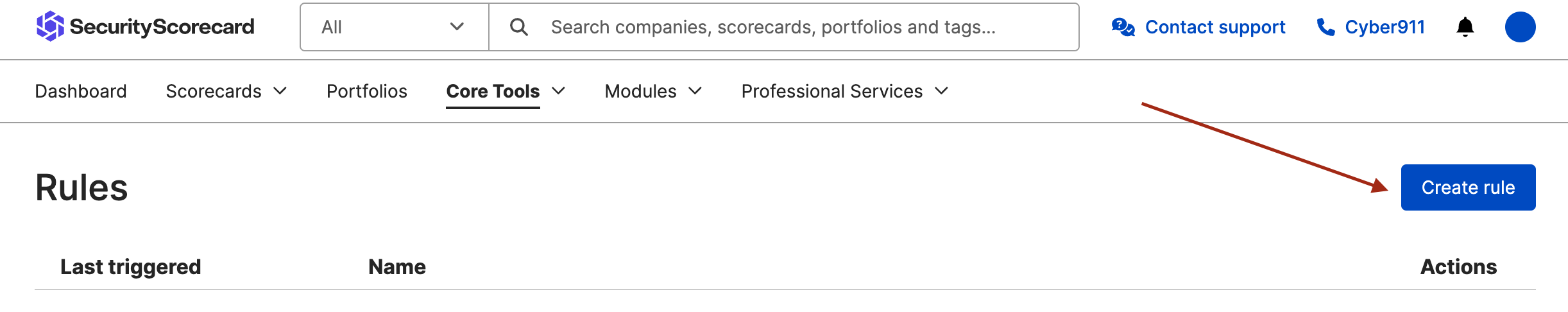
-
In the forms that you see please feel all the fields with correct values and use
Send web request toas action. Set the destination url tohttps://intake.sekoia.io/plain?intake_key=<intake_key>with value from previous steps.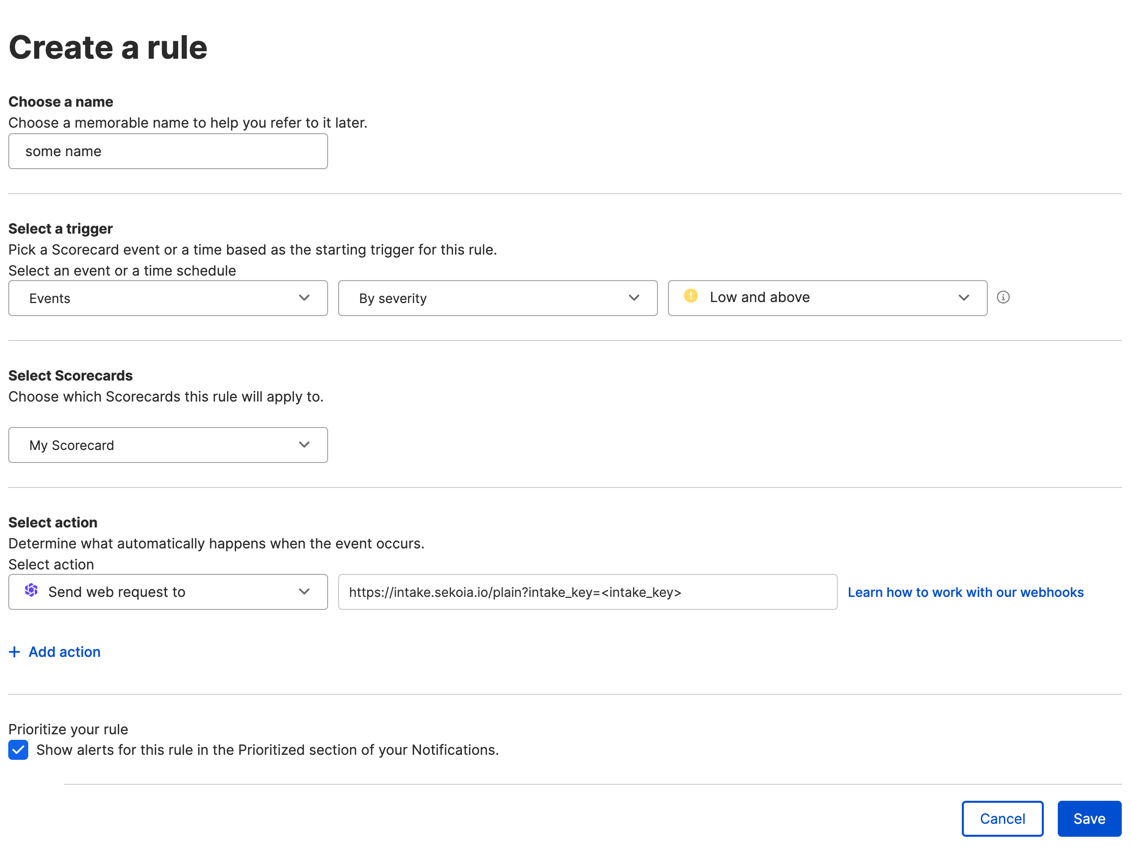
-
Save the configuration and enjoy your events
Raw Events Samples
In this section, you will find examples of raw logs as generated natively by the source. These examples are provided to help integrators understand the data format before ingestion into Sekoia.io. It is crucial for setting up the correct parsing stages and ensuring that all relevant information is captured.
{
"trigger": {
"type": "breach_reported",
"breach": {
"domain": "example.com",
"root_cause": "hacked",
"company_name": "Example Company",
"records_lost": 10000,
"date_discovered": 0,
"type_of_breach": "",
"description": "Company was breached, exposing authentication details of senior employees. An insider is believed to have helped."
}
},
"created_at": "2022-08-09T16:36:42.397Z",
"execution_id": "87b786f3-76c9-4a2e-a44b-985be679ef80",
"scorecard_id": "8e21f4aa-ee49-5f6d-be70-366b95ecc586",
"domain": "example.com"
}
{
"trigger": {
"type": "new_issues",
"issues": {
"csp_no_policy_v2": {
"active": {
"count": 26
},
"departed": {
"count": 3
},
"resolved": {
"count": 2
}
},
"domain_missing_https_v2": {
"active": {
"count": 15
}
}
},
"selected": "by_severity",
"severity": "low"
},
"created_at": "2022-08-10T19:49:46.029Z",
"execution_id": "ee08b90e-98fe-45e1-9261-91eb0a80275d",
"scorecard_id": "8e21f4aa-ee49-5f6d-be70-366b95ecc586",
"domain": "example.com"
}
{
"trigger": {
"type": "new_issues",
"issues": {
"tls_weak_protocol": {
"departed": {
"count": 1
},
"active": {
"count": 1
}
},
"tls_weak_cipher": {
"departed": {
"count": 2
},
"active": {
"count": 2
}
}
},
"selected": "by_severity",
"severity": "low"
},
"created_at": "2024-07-12T04:54:27.941Z",
"execution_id": "8a1be922-6698-4407-ba70-0515943d323e",
"scorecard_id": "56f0fca6-f6e0-55fd-9fce-b75ba65db80e",
"domain": "example.com",
"previous": {
"score": 90,
"factors": {}
},
"current": {
"score": 90,
"factors": {}
},
"platform_score_date": 20240710
}
{
"trigger": {
"type": "new_issues",
"issues": {
"tlscert_excessive_expiration": {
"active": {
"count": 1
}
},
"tlscert_no_revocation": {
"active": {
"count": 1
}
},
"csp_no_policy_v2": {
"active": {
"count": 1
}
},
"insecure_https_redirect_pattern_v2": {
"active": {
"count": 3
}
},
"redirect_chain_contains_http_v2": {
"active": {
"count": 9
}
},
"tls_weak_protocol": {
"departed": {
"count": 1
},
"active": {
"count": 1
}
},
"tls_weak_cipher": {
"active": {
"count": 1
}
},
"unsafe_sri_v2": {
"active": {
"count": 1
}
},
"hsts_incorrect_v2": {
"active": {
"count": 1
}
},
"x_content_type_options_incorrect_v2": {
"active": {
"count": 1
}
}
},
"selected": "by_severity",
"severity": "low"
},
"created_at": "2024-07-11T07:47:17.165Z",
"execution_id": "4c5395cc-0161-402f-896f-477966c2386d",
"scorecard_id": "d332f6dd-ec0e-57bf-9086-31ddd68095c9",
"domain": "example.com",
"previous": {
"score": 88,
"factors": {
"application_security": 85,
"network_security": 85
}
},
"current": {
"score": 88,
"factors": {
"application_security": 84,
"network_security": 84
}
},
"platform_score_date": 20240709
}
Detection section
The following section provides information for those who wish to learn more about the detection capabilities enabled by collecting this intake. It includes details about the built-in rule catalog, event categories, and ECS fields extracted from raw events. This is essential for users aiming to create custom detection rules, perform hunting activities, or pivot in the events page.
Related Built-in Rules
The following Sekoia.io built-in rules match the intake SecurityScorecard Vulnerability Assessment Scanner. This documentation is updated automatically and is based solely on the fields used by the intake which are checked against our rules. This means that some rules will be listed but might not be relevant with the intake.
SEKOIA.IO x SecurityScorecard Vulnerability Assessment Scanner on ATT&CK Navigator
SecurityScorecard Vulnerability Assessment Scanner New Issues
Raises an alert when SecurityScorecard Vulnerability Assessment Scanner find new issues.
- Effort: master
Event Categories
The following table lists the data source offered by this integration.
| Data Source | Description |
|---|---|
Application logs |
collect activities from the source |
In details, the following table denotes the type of events produced by this integration.
| Name | Values |
|---|---|
| Kind | alert |
| Category | intrusion_detection, vulnerability |
| Type | info |
Transformed Events Samples after Ingestion
This section demonstrates how the raw logs will be transformed by our parsers. It shows the extracted fields that will be available for use in the built-in detection rules and hunting activities in the events page. Understanding these transformations is essential for analysts to create effective detection mechanisms with custom detection rules and to leverage the full potential of the collected data.
{
"message": "{\"trigger\":{\"type\":\"breach_reported\",\"breach\":{\"domain\":\"example.com\",\"root_cause\":\"hacked\",\"company_name\":\"Example Company\",\"records_lost\":10000,\"date_discovered\":0,\"type_of_breach\":\"\",\"description\":\"Company was breached, exposing authentication details of senior employees. An insider is believed to have helped.\"}},\"created_at\":\"2022-08-09T16:36:42.397Z\",\"execution_id\":\"87b786f3-76c9-4a2e-a44b-985be679ef80\",\"scorecard_id\":\"8e21f4aa-ee49-5f6d-be70-366b95ecc586\",\"domain\":\"example.com\"}",
"event": {
"action": "breach_reported",
"category": [
"intrusion_detection"
],
"dataset": "breach",
"kind": "alert",
"reason": "Company was breached, exposing authentication details of senior employees. An insider is believed to have helped.",
"type": [
"info"
]
},
"@timestamp": "2022-08-09T16:36:42.397000Z",
"cloud": {
"account": {
"name": "example.com"
}
},
"observer": {
"product": "Vulnerability Assessment Scanner",
"vendor": "SecurityScorecard"
},
"organization": {
"name": "Example Company"
},
"securityscorecard": {
"vas": {
"breach": {
"root_cause": "hacked"
},
"id": "8e21f4aa-ee49-5f6d-be70-366b95ecc586",
"type": "breach_reported"
}
}
}
{
"message": "{\"trigger\":{\"type\":\"new_issues\",\"issues\":{\"csp_no_policy_v2\":{\"active\":{\"count\":26},\"departed\":{\"count\":3},\"resolved\":{\"count\":2}},\"domain_missing_https_v2\":{\"active\":{\"count\":15}}},\"selected\":\"by_severity\",\"severity\":\"low\"},\"created_at\":\"2022-08-10T19:49:46.029Z\",\"execution_id\":\"ee08b90e-98fe-45e1-9261-91eb0a80275d\",\"scorecard_id\":\"8e21f4aa-ee49-5f6d-be70-366b95ecc586\",\"domain\":\"example.com\"}",
"event": {
"action": "new_issues",
"category": [
"vulnerability"
],
"dataset": "issue",
"type": [
"info"
]
},
"@timestamp": "2022-08-10T19:49:46.029000Z",
"cloud": {
"account": {
"name": "example.com"
}
},
"observer": {
"product": "Vulnerability Assessment Scanner",
"vendor": "SecurityScorecard"
},
"securityscorecard": {
"vas": {
"id": "8e21f4aa-ee49-5f6d-be70-366b95ecc586",
"selected": "by_severity",
"severity": "low",
"type": "new_issues"
}
}
}
{
"message": "{\n \"trigger\": {\n \"type\": \"new_issues\",\n \"issues\": {\n \"tls_weak_protocol\": {\n \"departed\": { \"count\": 1 },\n \"active\": { \"count\": 1 }\n },\n \"tls_weak_cipher\": {\n \"departed\": { \"count\": 2 },\n \"active\": { \"count\": 2 }\n }\n },\n \"selected\": \"by_severity\",\n \"severity\": \"low\"\n },\n \"created_at\": \"2024-07-12T04:54:27.941Z\",\n \"execution_id\": \"8a1be922-6698-4407-ba70-0515943d323e\",\n \"scorecard_id\": \"56f0fca6-f6e0-55fd-9fce-b75ba65db80e\",\n \"domain\": \"example.com\",\n \"previous\": { \"score\": 90, \"factors\": {} },\n \"current\": { \"score\": 90, \"factors\": {} },\n \"platform_score_date\": 20240710\n}",
"event": {
"action": "new_issues",
"category": [
"vulnerability"
],
"dataset": "issue",
"type": [
"info"
]
},
"@timestamp": "2024-07-12T04:54:27.941000Z",
"cloud": {
"account": {
"name": "example.com"
}
},
"observer": {
"product": "Vulnerability Assessment Scanner",
"vendor": "SecurityScorecard"
},
"securityscorecard": {
"vas": {
"current_score": 90,
"id": "56f0fca6-f6e0-55fd-9fce-b75ba65db80e",
"previous_score": 90,
"selected": "by_severity",
"severity": "low",
"type": "new_issues"
}
}
}
{
"message": "{\n \"trigger\": {\n \"type\": \"new_issues\",\n \"issues\": {\n \"tlscert_excessive_expiration\": { \"active\": { \"count\": 1 } },\n \"tlscert_no_revocation\": { \"active\": { \"count\": 1 } },\n \"csp_no_policy_v2\": { \"active\": { \"count\": 1 } },\n \"insecure_https_redirect_pattern_v2\": { \"active\": { \"count\": 3 } },\n \"redirect_chain_contains_http_v2\": { \"active\": { \"count\": 9 } },\n \"tls_weak_protocol\": {\n \"departed\": { \"count\": 1 },\n \"active\": { \"count\": 1 }\n },\n \"tls_weak_cipher\": { \"active\": { \"count\": 1 } },\n \"unsafe_sri_v2\": { \"active\": { \"count\": 1 } },\n \"hsts_incorrect_v2\": { \"active\": { \"count\": 1 } },\n \"x_content_type_options_incorrect_v2\": { \"active\": { \"count\": 1 } }\n },\n \"selected\": \"by_severity\",\n \"severity\": \"low\"\n },\n \"created_at\": \"2024-07-11T07:47:17.165Z\",\n \"execution_id\": \"4c5395cc-0161-402f-896f-477966c2386d\",\n \"scorecard_id\": \"d332f6dd-ec0e-57bf-9086-31ddd68095c9\",\n \"domain\": \"example.com\",\n \"previous\": {\n \"score\": 88,\n \"factors\": { \"application_security\": 85, \"network_security\": 85 }\n },\n \"current\": {\n \"score\": 88,\n \"factors\": { \"application_security\": 84, \"network_security\": 84 }\n },\n \"platform_score_date\": 20240709\n}",
"event": {
"action": "new_issues",
"category": [
"vulnerability"
],
"dataset": "issue",
"type": [
"info"
]
},
"@timestamp": "2024-07-11T07:47:17.165000Z",
"cloud": {
"account": {
"name": "example.com"
}
},
"observer": {
"product": "Vulnerability Assessment Scanner",
"vendor": "SecurityScorecard"
},
"securityscorecard": {
"vas": {
"current_score": 88,
"id": "d332f6dd-ec0e-57bf-9086-31ddd68095c9",
"previous_score": 88,
"selected": "by_severity",
"severity": "low",
"type": "new_issues"
}
}
}
Extracted Fields
The following table lists the fields that are extracted, normalized under the ECS format, analyzed and indexed by the parser. It should be noted that infered fields are not listed.
| Name | Type | Description |
|---|---|---|
@timestamp |
date |
Date/time when the event originated. |
cloud.account.name |
keyword |
The cloud account name. |
event.action |
keyword |
The action captured by the event. |
event.category |
keyword |
Event category. The second categorization field in the hierarchy. |
event.dataset |
keyword |
Name of the dataset. |
event.kind |
keyword |
The kind of the event. The highest categorization field in the hierarchy. |
event.reason |
keyword |
Reason why this event happened, according to the source |
event.type |
keyword |
Event type. The third categorization field in the hierarchy. |
observer.product |
keyword |
The product name of the observer. |
observer.vendor |
keyword |
Vendor name of the observer. |
organization.name |
keyword |
Organization name. |
securityscorecard.vas.breach.root_cause |
keyword |
Scorecard breach root cause |
securityscorecard.vas.current_score |
number |
Scorecard current score |
securityscorecard.vas.id |
keyword |
Scorecard event id |
securityscorecard.vas.previous_score |
number |
Scorecard previous score |
securityscorecard.vas.selected |
keyword |
Scorecard event selected |
securityscorecard.vas.severity |
keyword |
Scorecard event severity |
securityscorecard.vas.type |
keyword |
Scorecard event type |
For more information on the Intake Format, please find the code of the Parser, Smart Descriptions, and Supported Events here.