External Integrations: Splunk
Sekoia is providing an application for Splunk to detect threats in your logs based on Sekoia.io CTI feed.
Prerequisites
- An operational Splunk instance with administrator privileges (Enterprise for OnPrem or Cloud for the SaaS version)
- An active Sekoia.io license with access to the CTI
- An access to Sekoia.io User Center with the role that contains the permission to create an API key (e.g. Built-in Analyst Role or create a custom role with ic_viewer permissions
Note
This following guide is for Splunk solutions (Enterprise (OnPrem) or Splunk Cloud (Cloud)).
1. Connect to Splunk Enterprise
- In a Web browser, type the following and replace
server_ipandportby their values: http://server_ip:port
!!!note For Cloud version, only the next step is required
- Enter your login and password of your Splunk Enterprise instance
2. Install and configure your Sekoia application for Splunk
-
Go to Application Setup Page by clicking on
Apps>Find more Apps
-
Search for
Sekoia.ioapplication and install it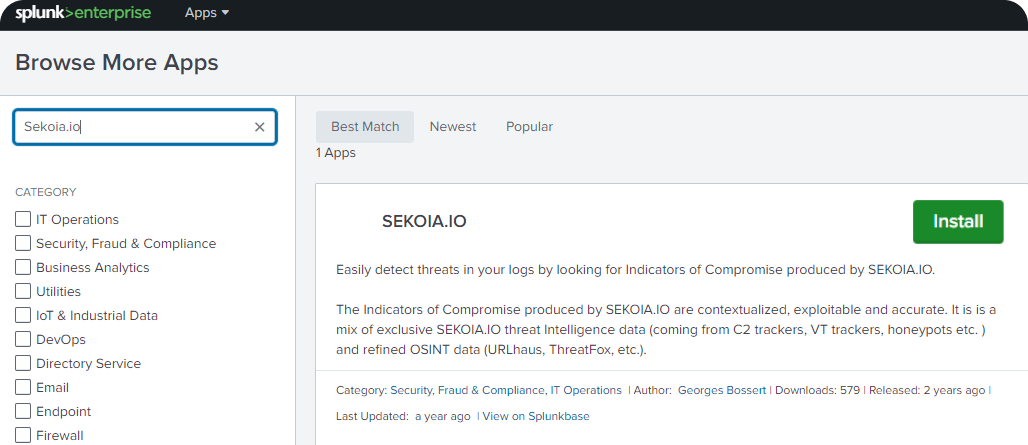
-
Configure your Sekoia application for Splunk by completing fields
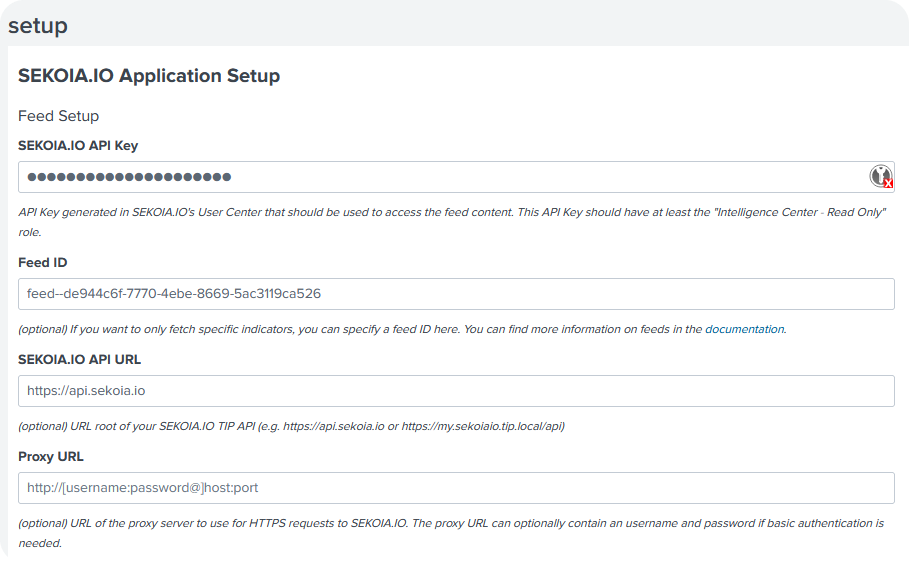
Please find below the explanation of the fields to be configured
Required
SEKOIA.IO API Key: Sekoia API Key to be created as stated in the Prerequisites
Optional
Sekoia API url: the default url is https://api.sekoia.ioFeed ID: default feed is used by default. For custom feed, add the feed ID. Please find more information on this documentationProxy URL- Here are 2 ways to configure a proxy:- If you need the Sekoia application for Splunk to connect directly through a proxy, this field needs to be filled on the installation page (To connect, in a Web browser, type and replace
username,password,hostandportby their values: http://[username:password@]host:port) - If you don't want to distinguish the Sekoia application for Splunk network configuration from the configuration of your Splunk instance, the Sekoia application for Splunk takes into account the global Splunk proxy configuration provided by means of the
HTTP_PROXYandHTTPS_PROXYenvironment variables.
- If you need the Sekoia application for Splunk to connect directly through a proxy, this field needs to be filled on the installation page (To connect, in a Web browser, type and replace
Note
After the launch of Sekoia application for Splunk, only valid IOCs of these types will be downloaded and updated on Splunk from current date.
3. Sekoia Intelligence in Splunk
In the following section, here are the Sekoia IOC types available in Splunk:
| IOC type | Meaning |
|---|---|
| domain | Domain name |
| url | Url website |
| ipv4 | Internet Protocol version 4 (32-bit number e.g. 111.111.1.11 ) |
| md5 | Cryptographic hash function that results in a 128-bit hash value |
| sha1 | Hash function which takes an input and produces a 160-bit (20-byte) |
| sha256 | Secure Hash Algorithm 256-bit |
An IOC is an observable that represents a malicious activity. For more information, please consult this page.
Note
Only these Sekoia Indicator types will be updated.
Update is scheduled every night to ensure that valid IOCs are used to detect threats.
4. Search Sekoia Intelligence and match with IOCs in Splunk
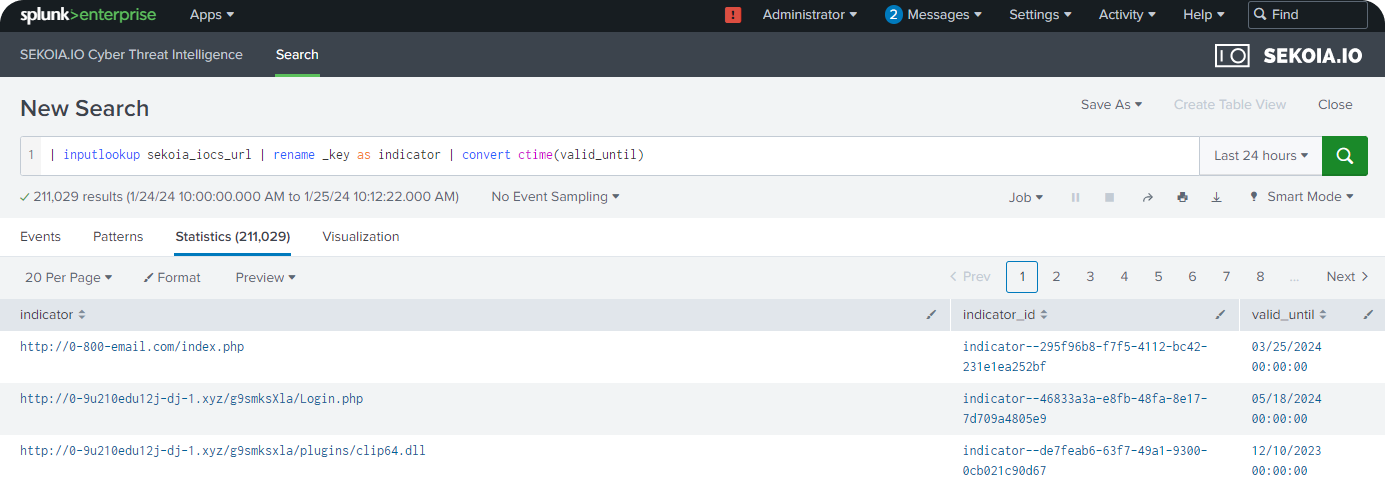
Search existing Sekoia IOCs in Splunk with expiry date
- Go to Application Setup Page by clicking on
Apps>Sekoia.io - In the search tab, query on
| inputlookup sekoia_iocs_url | rename _key as indicator | convert ctime(valid_until)
Search and compare Sekoia IOCs with logs in Splunk
Note
Logs have to be collected in Splunk. Please consult Splunk documentation.
-
Setup a lookup table
A typical query would be
index=* sourcetype=<YOUR_SOURCETYPE>(<YOUR_SOURCETYPE>is to be replaced by the Sekoia IOCs types listed above).When installing Sekoia application for Splunk, a message will be displayed requesting to configure the lookup table.
-
Sightings will be displayed on a section
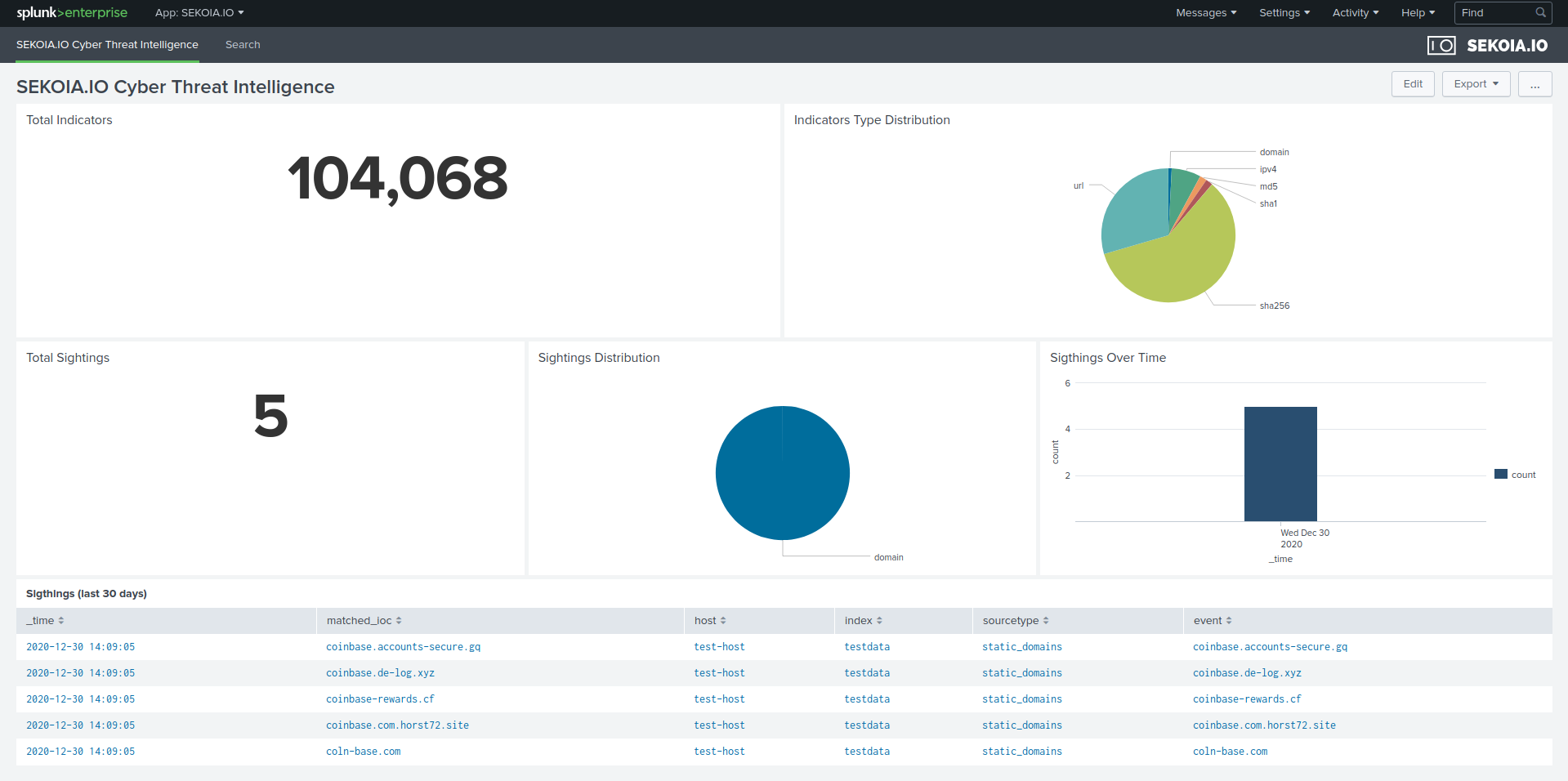
Please refer to our documentation to search IOCs in Intelligence page for more information.
5. Troubleshoot
1. False positive
Compare Sekoia IOCs valid date in Sekoia Intelligence.
2. Splunk issues
Search in the Internal logs for errors. Please consult Splunk documentation for more information.
6. Other resources
- Sekoia.io App for Splunk
https://github.com/SEKOIA-IO/SEKOIA.IO-for-Splunk
- Splunk official documentation
https://splunkbase.splunk.com/app/6327
https://community.splunk.com/t5/Installation/bd-p/installation
https://docs.splunk.com/Documentation/SplunkCloud/9.1.2308/SearchTutorial/InstallSplunk
https://docs.splunk.com/Documentation/SplunkCloud/9.1.2308/SearchTutorial/NavigatingSplunk